2024-7-18 19:17:6 Author: www.netcraft.com(查看原文) 阅读量:0 收藏
For the past year, Netcraft researchers have been tracking a threat actor using generative AI to assist in the creation of 17,000+ phishing and lure sites. These sites operate as infrastructure for phishing attacks that target more than 30 major crypto brands, including Coinbase, Crypto.com, Metamask, Trezor, and others.
These sites form part of a sophisticated, multi-step attack. The attack utilizes lure sites to hook victims, phishing sites to capture details, and a Traffic Distribution System (TDS) used to mask the relationships between attack infrastructure. With advanced deception techniques, like the ability to capture 2-factor authentication codes, this campaign highlights several of the most innovative capabilities of modern multi-channel phishing threats.
As phishing attacks become more complex than ever, recent advancements in generative AI further enhance these attacks by enabling threat actors to rapidly automate the creation of unique content that convincingly impersonates a wide variety of targets. The use of gen AI is also evident in other forms of cybercrime, such as donation scams and Advance Fee Fraud.
Interestingly, many of these AI-generated lure sites do not link to a phishing website, which appears deliberate. These are likely not designed for victims but instead suggest an attempt to flood the Web with similar content, making it harder to find the malicious needles in an AI-generated haystack. Without gen-AI, this new deception technique would be impossible for criminals, even criminal groups, to deploy at scale. For those combatting these threats, utilizing AI, ML, and automated techniques to detect and monitor threats is paramount in identifying and disrupting these nefarious techniques at any scale.
Anatomy of the attack
The attack starts with the victim visiting an AI-generated lure site. Lure sites hook unsuspecting victims into a scam and encourage them to complete an action, such as visiting another site, downloading a file, or sending an email. Commonly, lures are shared through various channels like email, SMS, social media, and SEO hacking. One widespread method used by this threat actor is distributing these links in the comment section of legitimate websites.
hxxp[://]forum[.]technikboard[.]net/index[.]php?page=UserBlogEntry&entryID=8
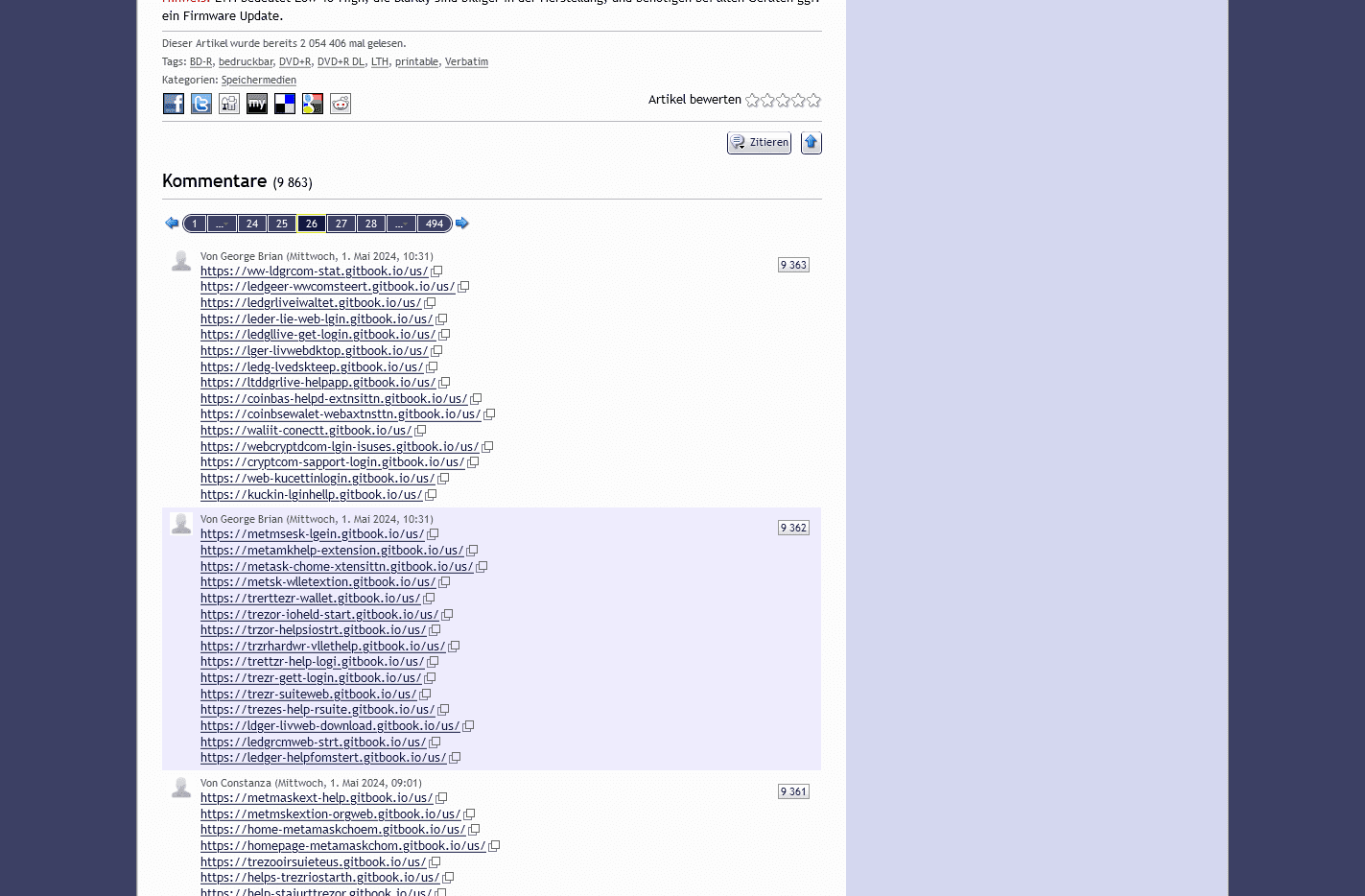
These lure sites are hosted on Gitbook, a documentation platform that targets software developers and offers a free tier requiring only an email address to sign up. Supported by vast amounts of content to increase credibility, the lure sites entice the victim by claiming to offer advice and tutorials for products from a wide range of brands in the crypto industry.
Example of an AI-generated lure site on hxxps[://]helpstrezorhardwrewallet[.]gitbook[.]io/us
Most sites contain a call-to-action link, which directs the user to a redirect URL on one of many [.]com domains. These URLs contain a Universally Unique Identifier (UUID) in the path to track which brand or lure site the victim visited. All these domains appear to be purpose-registered with Key Systems and hosted by Amazon.
Formatted extract from hxxps[://]helps-trezorhardwrewallet[.]gitbook[.]io/us
These redirect URLs use advanced Traffic Distribution Systems (TDSes), which can choose the redirect destination based on various factors. For example, if the TDS thinks the visitor is a victim, it will redirect them to a phishing site. When the TDS detects that the visitor is a security researcher, it will instead redirect them to the target brand’s legitimate site, attempting to cloak the existence of the phishing attack.
Visiting hxxps[://]shotheatsgnovel[.]com/1479dd91-86b0-4518-9970-ca644964c5e7 from an IP address the TDS classified as a security researcher (left) and an IP address classified as a victim (right)
The end phishing sites in this campaign aim to obtain one of two sets of credentials: the victim’s login details for the cryptocurrency platform or the seed recovery phrase for the victim’s wallet. If required by the platform, these phishing sites can even exfiltrate the victim’s 2-factor authentication codes, undermining the protection from this trusted layer of security.
Left hxxps[://]trazeorwalllet[.]azurewebsites[.]net/, right hxxps[://]bitmartesnc[.]azurewebsites[.]net/.
With either set of credentials, the threat actor can steal all the victim’s funds or sell the credentials on an underground marketplace for another criminal to do so. The pseudo-anonymous nature of cryptocurrency payments offers the threat actor a high degree of anonymity, making it highly desirable for cybercriminals. Even after accounts are drained, they are still valuable to criminals since they have already passed Know Your Customer (KYC) requirements and could be used to launder money.
This campaign’s lure and phishing sites are hosted on Microsoft Azure’s App Service platform (azurewebsites[.]net). As seen in previous attacks, such as the Phishception attack we uncovered targeting SendGrid, cloud services like Azure are attractive to fraudsters for their free tiers and credits.
Hedging their bets – Creating moving targets with phishing infrastructure
Since Netcraft researchers first discovered these attacks, we have performed countermeasures against them by first blocking these sites for users of Netcraft’s Apps and Extensions and then initiating takedowns against the sites of Netcraft customers using Netcraft’s Takedown platform. In response to those countermeasures, this criminal group has continued to evolve campaign strategies.
During this period, the threat actor tweaked and experimented with parts of their attack chain, likely to hedge their bets and keep their infrastructure available. One example is shifting traffic to phishing sites using much less sophisticated lures hosted on Webflow (webflow.io). These lures use a simple screenshot of the target brand’s homepage, redirecting to the TDS when clicking on the image. Many of these screenshots only include the page above the fold of the browser, meaning potential victims cannot scroll down. Some sites also include AI-generated text at the bottom of the webpage, which is likely to assist with SEO hacking.
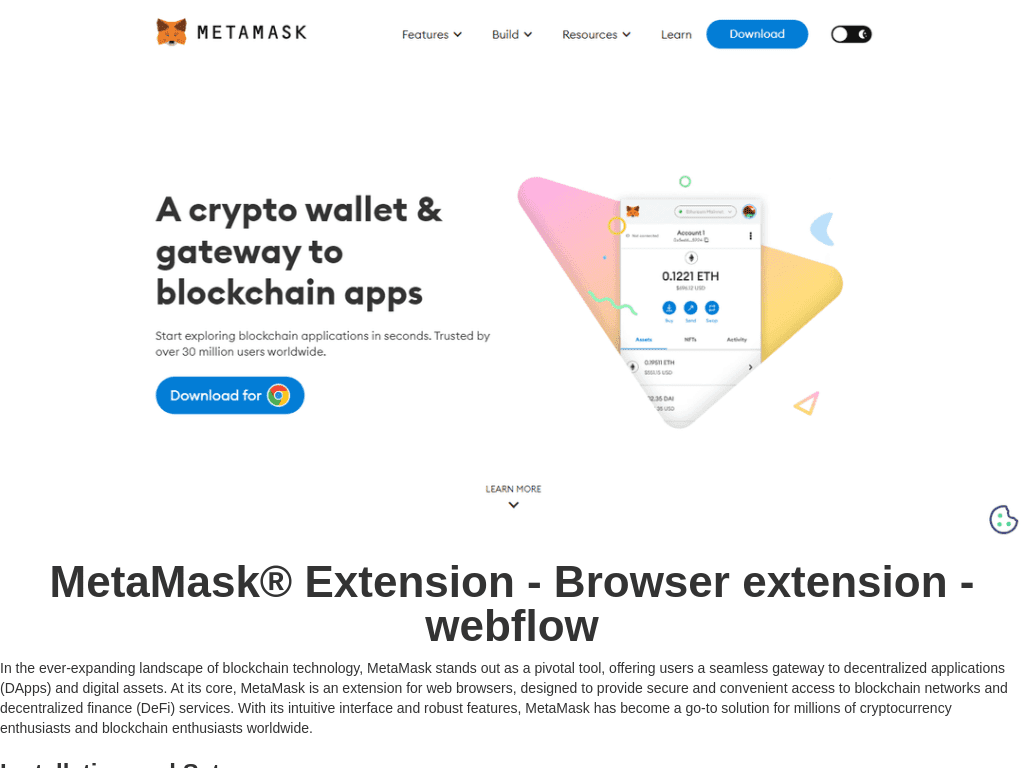
hxxps[://]metamaskeaxtenssion[.]webflow[.]io/
We also observed the threat actor replacing some of their [.]com TDS URLs with a legitimate link shortener platform, Geo Targetly (gtly.io). Doing this allows them to use many of the same functions as their traditional TDS, but with less work required to create new URLs. Reducing the complexity allows criminals to quickly create new URLs when many of the campaign’s [.]com domains were taken down.
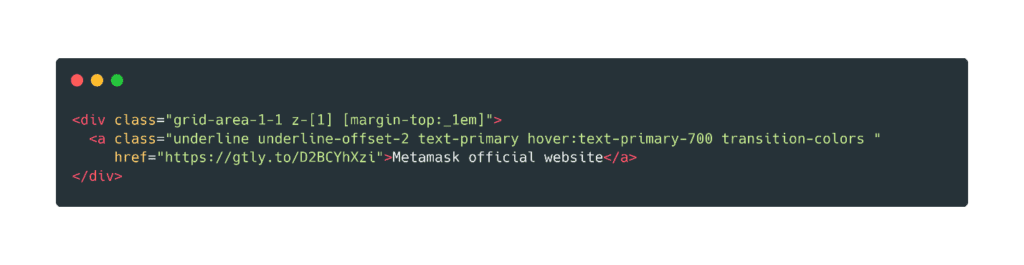
Formatted extract from hxxps[://]help-metamask-walletextension[.]gitbook[.]io/us
hxxps[://]help-metamask-walletextension[.]gitbook[.]io/us linking to hxxps://metamaskunb[.]azurewebsites[.]net/ via Geo Targetly
AI-generated lures raise the bar
Traditionally, one of the hardest parts of setting up a scam website is creating content that looks believable to potential victims. Due to the required manual effort, this is difficult for criminals to accomplish at scale, and poor-quality content has often been a key indicator of phishing infrastructure.
However, the recent surge in powerful and free-to-use LLMs through platforms such as ChatGPT has unlocked this final piece of the puzzle for fraudsters. Netcraft continues to monitor this space, and this threat actor appears to be an early adopter using these tools at a large scale.
Many lures use LLM-generated text to enable the threat actor to create unique content for thousands of pages that span a wide range of target brands. Creating this content is simple and cheap to automate and is faster and better than a human could achieve for even a fraction of the volume.
We also see examples where LLM-generated content has produced erroneous artifacts that pollute the output of the final text. These don’t appear to have been caught by the threat actor, which suggests high levels of automation to generate these lures. One LLM output even included a warning about the risks of phishing attacks!
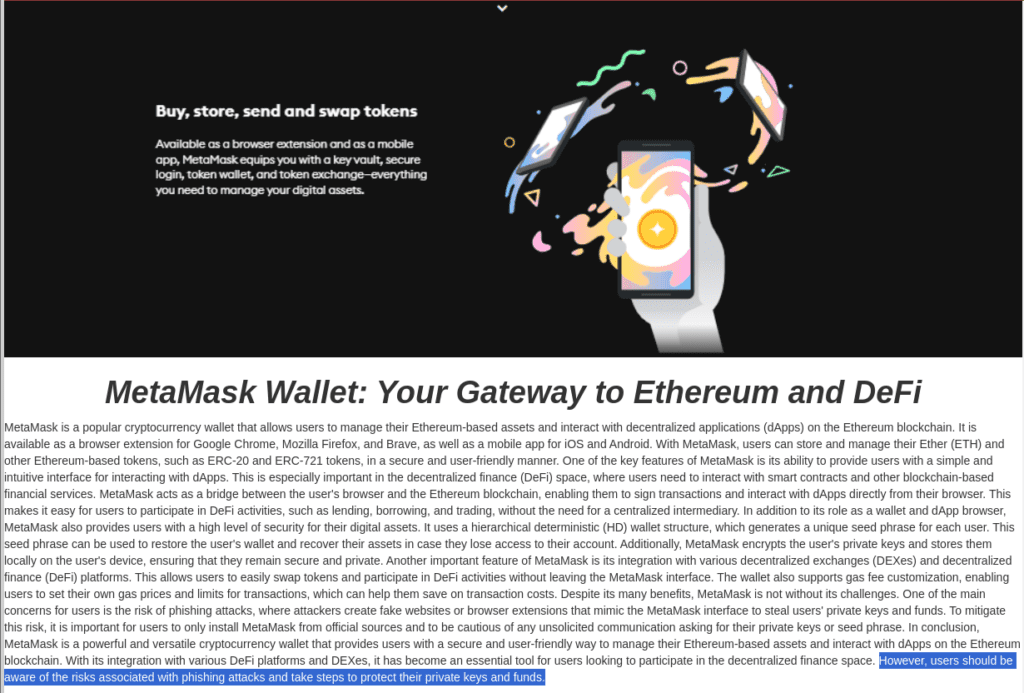
hxxps[://]metamaskwalletiis[.]webflow[.]io/ warning users about phishing attacks
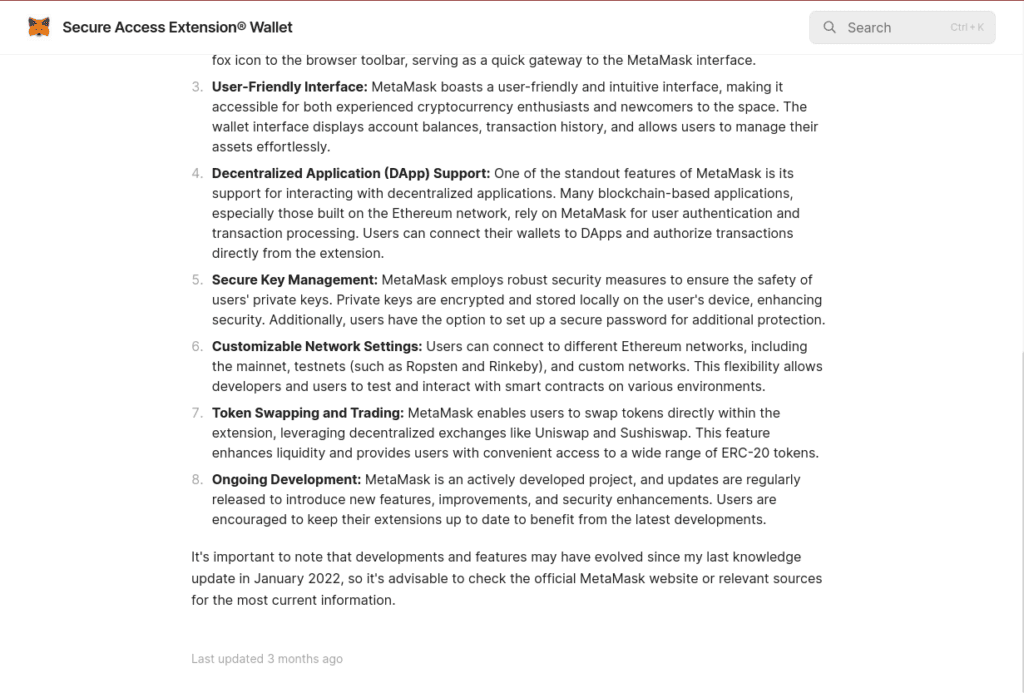
hxxps[://]mettemaskcchromextensionfs[.]gitbook[.]io/us, including the LLM warning about knowledge updates
As mentioned previously, many of these lure sites do not link to a phishing site – suggesting that the threat actor is attempting to flood the internet with content to make it more difficult to sort through and identify malicious needles in an LLM-generated haystack.
Crypto attacks on the rise
This attack follows a recent trend of threats observed by Netcraft; from crypto drainers, IPFS, pig butchering, and fake investment platforms to the Trump 2024 election campaign and YouTube channel hijacking, threats targeting the crypto industry range widely. The crypto industry is very enticing for threat actors due to lower traceability. Most recently, Netcraft researchers observed over $45 million in cryptocurrency payments transferred to scammers hidden in peer-to-peer messaging platform scams.
How Netcraft can help
Netcraft provides cybercrime detection, disruption, and takedown services to organizations worldwide, including 17 of the top 50 global banks and several of the largest cryptocurrency exchanges.
Netcraft provides cybercrime detection, disruption, and takedown services to organizations worldwide, including 17 of the top 50 global banks and many of the largest cryptocurrency exchanges in the world. While disrupting more than 100 unique attack types, Netcraft teams and systems constantly monitor unique and innovative attacks like these crypto phishing campaigns.
Netcraft’s brand protection platform operates 24/7 to discover phishing, fraud, scams, and other cyber-attacks through best-in-class automation, AI, machine learning, and human insight. Our disruption and takedown service ensures malicious content is blocked and removed quickly and efficiently – typically within hours. If you’d like to learn more about how Netcraft can help, book a demo on the Netcraft website.
如有侵权请联系:admin#unsafe.sh