2024-7-20 00:23:11 Author: www.uptycs.com(查看原文) 阅读量:21 收藏
CVE-2024-27348 is a critical remote code execution (RCE) vulnerability in Apache HugeGraph-Server. HugeGraph is a convenient, efficient, and adaptable graph database compatible with the Apache TinkerPop3 framework and the Gremlin query language. It is the first graph database project in Apache. This flaw enables unauthenticated attackers to execute arbitrary OS commands, potentially leading to unauthorized access, data manipulation, and full system compromise. The vulnerability impacts versions from 1.0.0 before 1.3.0 of Apache HugeGraph-Server running on Java8 and Java11. The root cause of CVE-2024-27348 lies in the way Apache HugeGraph-Server handles user inputs in Gremlin queries. The vulnerability allows attackers to send specially crafted Gremlin queries that exploit the GremlinGroovyScriptEngine class to execute arbitrary OS commands. The Gremlin script execution process involves the following steps: An attacker can craft a Gremlin query that utilizes the Runtime class to execute system commands. For Instance: This query should typically trigger a SecurityException due to the restrictions imposed by the SecurityManager. However, in vulnerable versions, the security checks can be bypassed, allowing the execution of arbitrary commands. The Shadowserver Foundation has published that they have observed in the wild exploitation attempts of this high severity vulnerability. We exploited the vulnerability in our lab to execute Coinminer and other types of malware. Uptycs detects the malicious activity. When blocking mode is enabled, all execution attempts are blocked at exploitation stage by Uptycs XDR as seen below. Uptycs XDR detects the vulnerable instance of Apache HugeGraph-Server running on a host/container. UApache HugeGraph is widely used across industries such as finance and healthcare. The discovery of CVE-2024-27348 and its active exploitation highlights the urgency for users to apply updates promptly. There is a critical need for robust security practices and proactive actions to stay protected from online threats.Affected Versions
Vulnerability Description
Gremlin Script Execution
Exploitation Path

 Fig. 1 - In the Wild exploitation reported
Fig. 1 - In the Wild exploitation reportedExploitation Detection using Uptycs XDR
 Fig. 2 - Detection of malicious activity (Detect-only mode) by Uptycs XDR
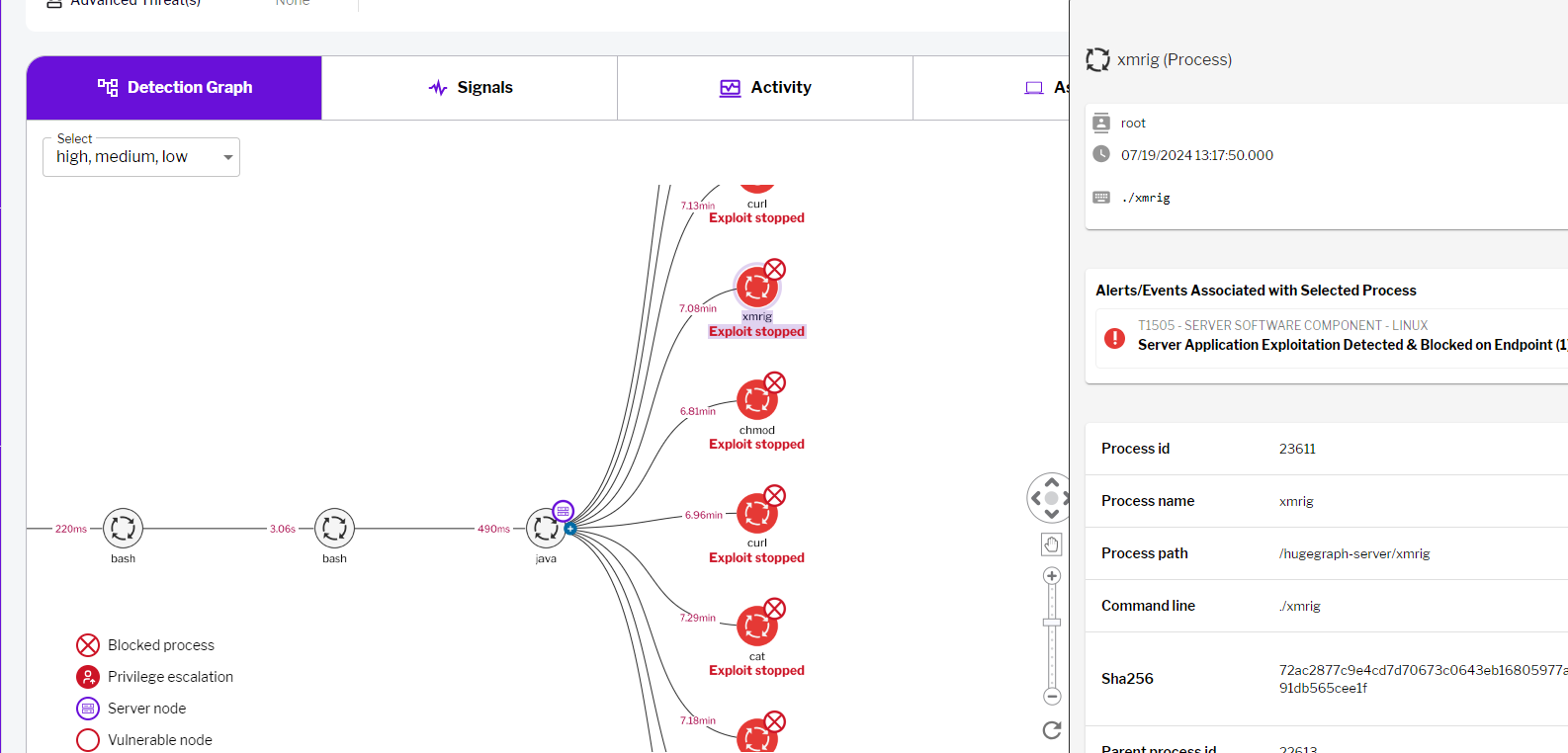
Fig. 2 - Detection of malicious activity (Detect-only mode) by Uptycs XDR Fig. 3 - Uptycs XDR killing the exploitation activities (Block mode)
Fig. 3 - Uptycs XDR killing the exploitation activities (Block mode)Vulnerability Detection using Uptycs XDR
 Fig. 4 - Vulnerability Detection by Uptycs XDR
Fig. 4 - Vulnerability Detection by Uptycs XDRConclusion
如有侵权请联系:admin#unsafe.sh