2024-7-25 18:20:55 Author: securityaffairs.com(查看原文) 阅读量:17 收藏
Hackers exploit Microsoft Defender SmartScreen bug CVE-2024-21412 to deliver ACR, Lumma, and Meduza Stealers

The CVE-2024-21412 flaw in the Microsoft Defender SmartScreen has been exploited to deliver information stealers such as ACR Stealer, Lumma, and Meduza.
Fortinet FortiGuard Labs researchers observed a malware campaign exploiting the vulnerability CVE-2024-21412 (CVSS score: 8.1) to spread information stealer, such as ACR Stealer, Lumma, and Meduza.
The CVE-2024-21412 is an Internet Shortcut Files Security Feature Bypass Vulnerability.
The flaw resides in Microsoft Windows SmartScreen and is caused by improper handling of maliciously crafted files. An unauthenticated attacker can trigger the flaw by sending the victim a specially crafted file that is designed to bypass displayed security checks. The attacker has to trick the victims into clicking the file link. The flaw was reported by:
- Peter Girnus (gothburz) of Trend Micro’s Zero Day Initiative with Trend Micro
- dwbzn with Aura Information Security
- Dima Lenz and Vlad Stolyarov of Google’s Threat Analysis Group
Microsoft addressed the flaw with the release of Patch Tuesday Security updates for February 2024. Fortinet reported that the stealer campaign targeted Spain, Thailand, and the U.S. with booby-trapped files.
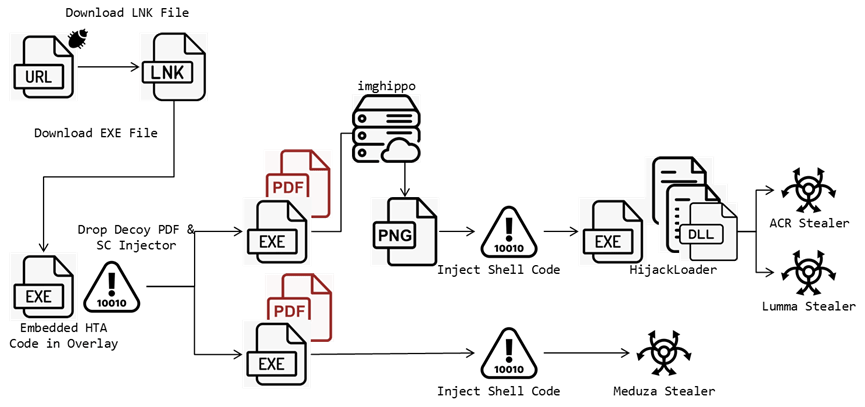
“FortiGuard Labs has observed a stealer campaign spreading multiple files that exploit CVE-2024-21412 to download malicious executable files. Initially, attackers lure victims into clicking a crafted link to a URL file designed to download an LNK file. The LNK file then downloads an executable file containing an HTA script. Once executed, the script decodes and decrypts PowerShell code to retrieve the final URLs, decoy PDF files, and a malicious shell code injector. These files aim to inject the final stealer into legitimate processes, initiating malicious activities and sending the stolen data back to a C2 server.” reads the report published by Fortinet. “The threat actors have designed different injectors to evade detection and use various PDF files to target specific regions, including North America, Spain, and Thailand.”

During the investigation, the researchers detected multiple LNK files that were used to download similar executables containing an embedded HTA script. The HTA script executed additional malicious code and downloads two files, a decoy PDF designed to divert the victim’s attention and an execution file that injects shell code for the subsequent stages of the attack.
The researchers identified two types of injectors. The first variant downloads a shell code from an image file hosted on Imghippo, which has low detection rates on VirusTotal. The shell code is extracted from the image pixels using the Windows API “GdipBitmapGetPixel” and then executed. This code retrieves necessary APIs, creates a folder, and drops files in the “%TEMP%” directory, including a HijackLoader, indicated by specific byte patterns in the data.
The second injector simply decrypts its code from a data section and uses several Windows API functions such as NtCreateSection, NtMapViewOfSection, and NtProtectVirtualMemory to inject the shell code into the system. This approach facilitates the execution of malicious payloads by manipulating memory sections and their protections.
Fortinet observed the threat actors spreading Meduza Stealer version 2.9, an ACR stealer delivered via HijackLoader that employs a “dead drop resolver” technique to hide the C2 server on a Steam community profile.
“To mitigate such threats, organizations must educate their users about the dangers of downloading and running files from unverified sources. Continuous innovation by threat actors necessitates a robust and proactive cybersecurity strategy to protect against sophisticated attack vectors.” concludes the report. “Proactive measures, user awareness, and stringent security protocols are vital components in safeguarding an organization’s digital assets.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CVE-2024-21412)
如有侵权请联系:admin#unsafe.sh