2024-7-30 23:44:27 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
TL;DR
- The cyber risk landscape and its respective management practices are constantly evolving, necessitating regular updates to cyber risk quantification models and platform capabilities.
- In this vein, Kovrr recently upgraded its CRQ platform and model calibration, ensuring customers have access to the features they need and the most accurate and precise quantification assessment outputs.
- Within the platform, Kovrr now equips users to map their relative control levels according to the ISO 27001:2022 maturity framework, ensuring broader organizational alignment.
- This international information security standard consists of 93 controls across organizational, people, physical, and technological security categories to help companies systematically improve their cybersecurity posture.
- By quantifying the potential contribution of ISO 27001 control levels to risk reduction, organizations can transform maturity assessments into actionable data, aiding in resource optimization and strategy development.
- Kovrr also recently updated its model calibration to ensure the data reflects the current cyber risk environment. The latest update noted a reduction in ransomware rates.
- These ongoing enhancements, both on the platform and model levels, ensure that Kovrr’s CRQ continues to provide accurate and practical data that helps cyber risk managers reduce exposure and achieve cyber resilience.
Continuously Evolving Cyber Risk Quantification (CRQ) Capabilities
One of the most simultaneously exciting and challenging aspects of working in the cybersecurity industry is that the risk landscape and management practices never stop evolving. Additional data is continuously being gathered, and new frameworks are constantly developed to help organizations better assess, measure, and secure themselves against threat actors poised to exploit system weaknesses.
Kovrr, keeping pace, is also always investing resources into adapting our on-demand cyber risk quantification solution to meet these market transformations, ensuring that our customers have access to the most accurate quantification outputs. In this vein, our team has both updated our model calibration and enhanced the platform so that it now offers organizations that leverage the ISO 27001:2022 maturity framework to quantify their relative control levels.
Transforming ISO 27001 Control Levels Into Actionable Insights
Chief information security officers (CISOs) across industries worldwide employ cybersecurity maturity frameworks to help them gauge the effectiveness of their organizations’ cyber programs. These frameworks illuminate those security areas in which progress has been made and which are in need of further investment. Yet, while the assessment criteria offer a basic road map on which mitigation strategies can be built, they lack the information necessary for prioritization, budget justification, and high-level communication.
By assessing the companies’ ISO 27001 maturity, cybersecurity leaders gain access to these important details. Control levels are transformed into actionable insights, influencing an organization’s forecasted likelihood of experiencing different cyber event loss scenarios, along with overall financial exposure. With this objective data, CISOs are equipped to optimize their limited resources and ensure they develop strategies that align with overall business goals.
What Is ISO 27001:2022?
ISO 27001 is an internationally recognized information security management standard that provides companies with precise instructions for “establishing, implementing, maintaining, and continuously improving” their cybersecurity practices. Adhering to this framework indicates that an organization has invested significant resources into securing data and assets from multiple angles. After implementing the specified controls, organizations can receive an official certification.
While the ISO 27001 certificate is an authorized third-party official recognition that information security leaders have implemented each of the controls to the highest degree, it is not a requirement. In fact, many organizations that adhere to the ISO 27001 standards decide not to undergo the final external audit. Instead, they leverage this maturity framework as a set of structured guidelines to level up their cybersecurity posture amid a landscape that’s overrun by threats.
ISO 27001:2022 is the latest iteration of this global information security management standard, which contains 93 controls.
What Are the Specific ISO 27001:2022 Controls?
The latest 93 ISO controls are broken down into four categories: organizational (Clause 5), people (Clause 6), physical (Clause 7), and technological (Clause 8). Each of these topic areas covers a crucial aspect of cybersecurity risk management, highlighting that this core business function should be approached holistically and integrated into overall operational processes.
Organizational Controls, Clause 5
The 37 organizational controls, all of which focus on a wide variety of topics, such as information security policies and documentation, access limitations, stakeholder responsibilities, proper data classification, and asset management. This controls section likewise highlights the importance of robust internal communication to help everyone stay aware of cyber threats. Organizational controls are intended to support business leaders in building robust defenses and maintaining high-level resilience.
People Controls, Clause 6
It’s commonly known that employees are some of the most vulnerable access points in the company’s system. This unfortunate reality is why Clause 6 emphasizes education, focusing on making people aware of their personal security responsibilities. ISO 27001:2022 stipulates that organizations should draw up confidentiality agreements and establish disciplinary processes to deter any violations. Ultimately, the eight ‘people’ controls intend to promote a security-conscious culture in which everyone takes accountability.
Physical Controls, Clause 7
While information security is typically associated with the cloud, there are also a considerable number of actions organizations can take to protect their data on the physical front. The ‘physical’ controls, of which there are 14, help to protect assets from unauthorized access and environmental threats.
For this category, cyber risk managers are meant to establish physical security perimeters and institute best practices, such as not leaving a laptop unlocked or unattended. These controls stress the importance of proper equipment maintenance and collectively support companies in safeguarding the integrity, confidentiality, and availability of physical assets and information.
Technological Controls, Clause 8
Finally, the ‘technological’ controls include measures to mitigate risks associated with device use and access, such as implementing multi-factor authentication. This set of controls also addresses protocols for malware protection and ensuring secure configuration management. In terms of operational resilience, CISOs should make sure that adequate backups and redundancy controls are in place in case an event occurs.
While this is by far not an exhaustive list of the 34 technological safeguards, the examples provided highlight their overall emphasis on building robust defenses against technological vulnerabilities.
Mapping ISO 27001 Control Levels Into Kovrr’s CRQ Platform
To more precisely and accurately quantify cyber risk exposure, Kovrr’s platform provides customers with the option to enter specific data pertaining to the organization’s technological profile, including which cybersecurity control framework they adhere to and the respective implementation control levels. With this latest update, in addition to the NIST CSF and CIS Security Control frameworks, the platform also allows for the selection of ISO 27001:2022.

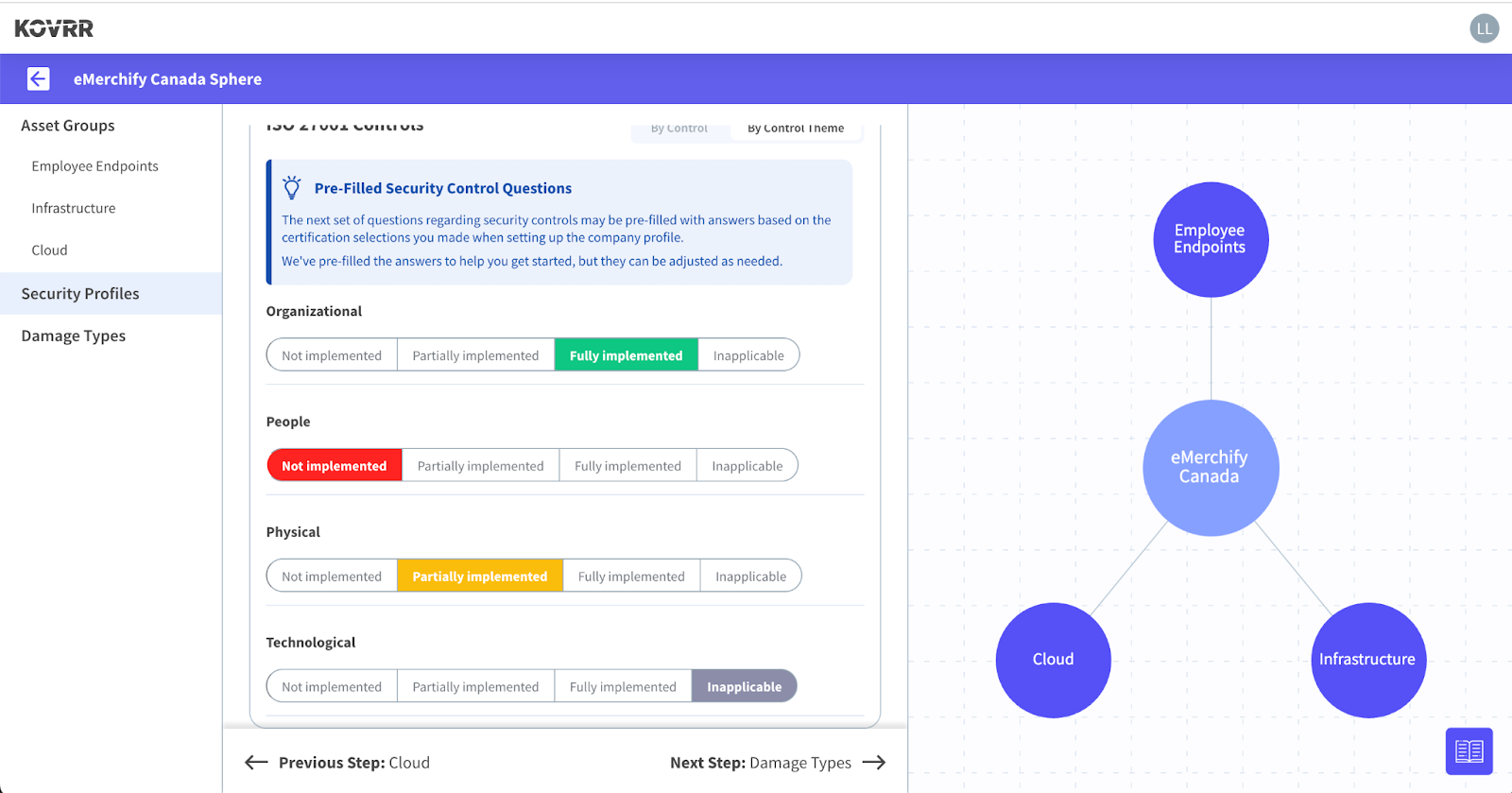
This new capability enables users to document the maturity of each of the specific controls within the four focus groups (organizational, people, physical, and technological). Each separate control can be ranked according to its implementation level, ranging from not implemented to fully implemented to ‘inapplicable.’ This ranking system allows for a more nuanced maturity evaluation, fostering sharper quantification outputs.
There is also the option to select ‘inapplicable’ when the specific controls are not relevant to the organization’s industry. ‘Inapplicable’ instructs the CRQ models to avoid taking these controls into account, likewise bolstering output accuracy. For instance, the organization eMerchify Canada has begun inputting their respective levels, and, as pictured above, the technological controls are inapplicable to them.
If certain details were previously provided or uploaded, or users specify that their organization has obtained various cybersecurity certificates, the Kovrr platform will automatically pre-fill various control maturity tiers accordingly. However, these inputs can always be adjusted as needed.
How Kovrr Quantifies ISO 27001 Control Levels
Mapping an organization’s maturity levels according to their respective cybersecurity frameworks provides a structured, targeted baseline for quantifying cyber risk. These levels, or implementation tiers as they’re sometimes known, help Kovrr’s CRQ models identify the strengths and weaknesses of the current cybersecurity posture. For example, if a company has a lower maturity status in ISO’s ‘People Controls,’ that is a signal that it is more likely to experience an event due to a phishing scam.
Kovrr’s similarly harnesses global loss intelligence collected from more than 100 external, objective sources that gather more than 1 million data points daily to inform our models. Kovrr also has privileged access to continuously evolving insurance loss intelligence datasets, providing us with loss data at various portfolio levels and illuminating hundreds of thousands of real-market financial impact data records.
Overall, the more mature a business’s cybersecurity practices are, the less likely it is to experience an event. Likewise, maturity has a direct impact on event severity levels. Contact us today to learn more about Kovrr’s methodology and how our models quantify cyber risk.
Upgrading Model Calibration to Reflect the Latest Cyber Risks
Because the cyber risk landscape is fiercely dynamic, with new threats, vulnerabilities, and technologies constantly emerging, Kovrr regularly updates its CRQ model calibration account for these changes. This ongoing enhancement is vital for maintaining accurate outputs and ensuring that risk likelihoods and relative severity forecasts reflect the organization’s current risk environment.
With access to dozens of data sources, many of which are augmented on a daily basis, the Kovrr models are constantly being re-educated and reinformed. The cybersecurity regulatory landscape likewise plays a significant role in the enhancement process as more information relating to fines and penalties for lack of compliance is released to the public. After enough new data has been accumulated, which typically occurs on a quarterly basis, although not always, Kovrr’s updated model calibrations are implemented.
Reduction in Ransomware Rates
In Kovrr’s latest update, after calibrating the data to match the current cyber risk landscape, there was a noticeable reduction in the rate of ransomware, with data breach rates remaining relatively constant. While this, by far, does not indicate that every organization across the market should expect to see a drop in their likelihood of experiencing a ransomware event, it does signify that, on average, ransomware events are becoming less common.
It is also important to note that these trends are likewise based on events that have yet to be reported and offer a quarterly projection based on the information already made available.
Staying Equipped With the Most Accurate Cyber Risk Forecasts
Cyber risk quantification’s ultimate purpose is to provide organizations with an objective, accurate understanding of their cyber risk posture by translating complex metrics into actionable insights. However, in order to maintain accuracy levels and ensure cyber risk managers can input the most customized data according to their unique technological profiles, CRQ models and platforms must always be evolving.
Considering its prominence throughout the cybersecurity industry, the ISO 27001 standard is now available to map within Kovrr’s CRQ solution, ensuring an organization’s security profile can directly reflect this framework and the respective maturity levels. At the same time, Kovrr also recently updated its model calibration, as it does on a regular basis, to reflect how the cyber risk landscape has transformed over the past few months.
To assess the specific outputs that Kovrr’s CRQ solution can offer your cybersecurity team and discover what Kovrr does to keep our customers equipped with the latest features and capabilities, schedule a free demo today or contact one of our experts.
如有侵权请联系:admin#unsafe.sh