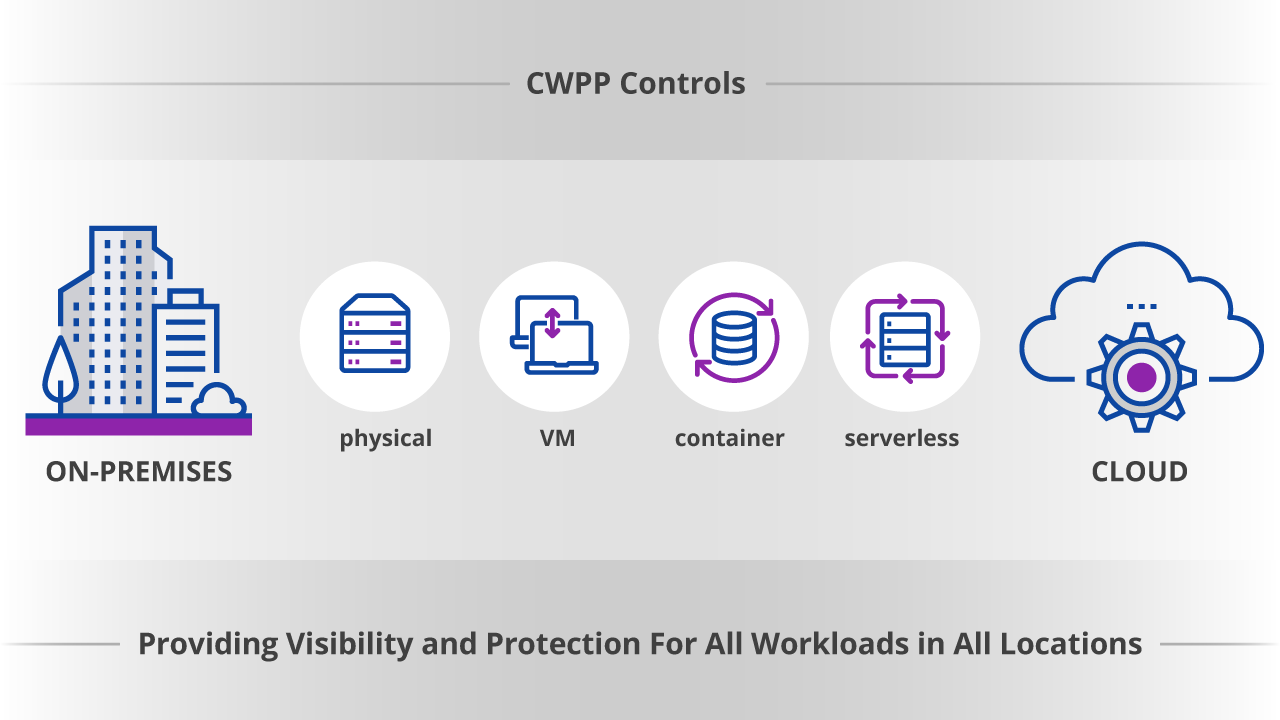
Organizations are accelerating their migrations to the cloud while continuing to use on-premises systems. This cloud/on-prem mix offers big upsides in flexibility and scalability, but it also makes it hard to protect an organization’s shifting attack surface. You can’t just take what worked in traditional data centers and port it to the cloud. Tools developed to secure on-premises workloads—such as heavyweight agents—weren’t designed to be deployed on the minimized, ephemeral workloads popular in the cloud. And with developers sometimes using sketchy open-source software libraries, cloud-native workflows require malware to be detected earlier in the development cycle rather than after code is deployed to production. These pressures have kickstarted a rethinking of workload visibility and security. One emerging approach to securing systems across an organization is the cloud workload protection platform (CWPP). According to Gartner, a CWPP is a workload-centric security tool that addresses the “unique protection requirements of server workloads in modern hybrid, multi-cloud data center architectures.” Cloud workload protection platforms provide visibility and protection for physical and virtual machines (VMs), containers, and serverless workloads in any location. The platform typically employs a combination of network segmentation, system integrity protection, application control, behavioral monitoring, host-based intrusion prevention, and anti-malware scanning. Designed to provide comprehensive and targeted protection for workloads on-prem or in the cloud, the system scans cloud environments for improperly configured security settings or ones that violate corporate security policies or regulatory compliance requirements. As one of the biggest advantages of the cloud is the ability to scale resources up and down on demand, CWPPs are cloud-based, enabling organizations to achieve the same level of flexibility with regard to application and workload security. Also referring to the amount of work (or load) that software imposes on the underlying computing resources, an application’s workload is related to the amount of time and computing resources required to perform a specific task or produce an output from inputs provided. First, let’s examine the eight layers of cloud workload protection platform controls as defined by Gartner. The core layers of cloud workload protection platforms controls are hardening, configuration, and vulnerability management; network firewalling, visibility, and microsegmentation; system integrity assurance; application control and allowlisting; and exploitation prevention and memory protection. The hardening, configuration, and vulnerability management layer is foundational for cloud workload protection platforms. At this layer, images are hardened based on industry standards. Information security teams ensure that systems are hardened and configured according to the organization’s guidelines, and systems are patched promptly. At the network firewalling, visibility, and micro-segmentation layer, the workload is secured through firewalling and segmentation of its communication with other resources. Micro-segmentation of east/west traffic in data centers and monitoring of the communication flows are supported. Some solutions offer encryption of network traffic. The system integrity assurance layer covers both pre-boot and post-boot. In the pre-boot phase, the tool measures the basic input/output system, unified extensible firmware interface, firmware, hypervisor, virtual machines, and container system images before they are loaded. In the post-boot phase, CWPP provides monitoring of workload integrity, including critical system files and configuration after the workloads are booted, as well as the integrity of the Windows registry, startup folders, drivers, and boot loader. At the application control/allowlisting layer, the tool uses application control to manage what executables are running on a server, enabling an organization to adopt a default deny security posture for executables. Malware that manifests as an executable file is blocked by default. Many tools offer built-in application control capabilities. The exploit prevention and memory protection capabilities from the operating system or supplemental functionality should be combined with application control to prevent attacks on vulnerabilities in an allowlisted application. These capabilities can also be used as mitigating features when patches are not available. The remaining three layers—server workload endpoint detection and response (EDR), behavioral monitoring, and threat detection/response; host-based IPS with vulnerability shielding; and anti-malware scanning—are important to CWPP but can be executed outside of the workload. While server workload EDR, behavioral monitoring, and threat detection/response should be mandatory for CWPP, they can be achieved using monitoring from outside the workload. For example, server EDR monitoring looks at network communications, processes launched, files opened, and log entries for behavior patterns that indicate malicious activity, including within containers. The server EDR function can also quickly scan systems for the presence of a specific file by name or hash in the event of an attack. Using host-based IPS with vulnerability shielding, the vendor inspects incoming network traffic for attacks against known bugs and thwarts those attacks. The inspection is executed at the host rather than at the network, which is better for preventing inter-VM or inter-container-based attacks. This layer is a valuable defense-in-depth control to prevent attacks on a zero-day bug until a patch is applied or the workload’s code is rebuilt from a patched image. Anti-malware scanning is an optional capability for a tool, but it should at least be performed on file repositories. Signature-based file scanning makes sense if the server workload is a general-purpose file repository or there is a regulatory requirement that specifies the use of anti-malware scanning. Organizations should use the same anti-malware vendor on end-user endpoints and server workloads to take advantage of the same policy management system and the same contract. There are several significant benefits that cloud workload protection platforms provides to an organization. For example, an effective tool facilitates shared responsibility between the organization and its cloud providers in securing workloads hosted in the cloud. Although the task division of shared responsibility can vary, the organization is usually responsible for the security of data, hosts, containers, servers, networks, users and credentials, and resource configuration in the cloud. The cloud provider is responsible for the security of routers, switches, hubs, the hypervisor, and the data center of the cloud. Read more on how to locate hidden cloud credentials across your org, here. Attackers understand where the weaknesses in the shared responsibility model exist and target them. A CWPP tool can help with shared responsibility by protecting assets inside the cloud from attacks that bypass cloud vendors' defenses. Platforms also provide comprehensive and consolidated visibility of on-prem and cloud workloads, which can be a significant challenge for larger enterprises. Bringing on-prem and cloud visibility information together is a significant security benefit provided by CWPP. Comprehensive visibility reduces overall risk and boosts threat detection and response. Other CWPP benefits include: lower upfront costs, reduced cost of hardware, lower maintenance and operational overhead; the scalability of application capacity based on demand; better and faster customer response times; and the ability to stand up and use from anywhere and collect analytics from applications. Schedule a demo to see how Uptycs protects your on-prem and cloud workloads. To implement an effective cloud workload protection program, Gartner recommends that security and risk management leaders take the following steps: So, what does the future hold for CWPP? The cloud environment's growing complexity is likely to spur the consolidation of cloud workload protection with similar types of platforms, such as cloud security posture management (CSPM) and cloud access security broker (CASB). In particular, the convergence of CWPP and CSPM functionality is leading to a new category of cloud security: a cloud-native application protection platform (CNAPP). By combining capabilities, CNAPP allows organizations to scan workloads and configurations in development and protect them at runtime. As organizations mull which platform or platforms to select, they should thoroughly understand and consider the benefits of a cloud workload protection platform. The platform handles cloud and on-prem workloads in a way that works with modern workflows. Also, security visibility is an essential feature. And CWPP provides organizations with key tools to address their part of the shared responsibility model. Learn more about cloud security and CWPP: Featured image by Peggy und Marco Lachmann-Anke from Pixabay.
What Does a CWPP Do?
What Is a Benefit of Cloud Workload Protection (CWPP)?
What Is a Workload in Computing?
Layers of CWPP Controls
Benefits of CWPP
CWPP Implementation Steps
The Future of CWPP (& CSPM & CNAPP …)
Read more about Cloud Security and Best Practices:

CWPP Meaning - What is a Cloud Workload Protection Platform (CWPP)?
2024-8-2 20:41:0 Author: www.uptycs.com(查看原文) 阅读量:4 收藏
2024-8-2 20:41:0 Author: www.uptycs.com(查看原文) 阅读量:4 收藏
文章来源: https://www.uptycs.com/blog/what-you-need-to-know-about-cwpp-cloud-workload-protection-platform
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
