Intro
You are a security professional who has been given the task of managing and mitigating the wide array of vulnerabilities within the open source software your organization uses. In an ideal world, you would have the time, energy, and resources necessary to immediately begin addressing and fixing each and every one of these vulnerabilities immediately – including all the new ones coming in.
However, reality is quite different. No one has all the necessary resources readily at their disposal. The number of vulnerabilities in open source software is insurmountable. The reality is that it would take an unprecedented amount of time, manpower, and financial resources to tackle each and every vulnerability.
The only viable solution is to prioritize. So, how do you effectively prioritize your efforts?
Having the right tools in your vulnerability management toolbox is critical. This is where the Exploit Prediction Scoring System (EPSS) comes in.
Understanding EPSS: Enhancing Vulnerability Management
Developed by the Forum of Incident Response and Security Teams (FIRST) [1], EPSS [2] provides a data-driven approach to predicting the likelihood of a vulnerability being exploited in the wild within the next 30 days. By leveraging this industry-recognized standard, organizations can make informed decisions and allocate their limited resources much more efficiently.
At its core, EPSS is a probability score ranging from 0 to 1 (0 to 100%). A higher score indicates a greater likelihood of a vulnerability being exploited. But how is this score calculated, and what factors does it consider?
EPSS considers a wide range of information, including:
- Vendor
- Vulnerability age
- References
- Vulnerability description
- Common Weakness Enumeration (CWE)
- CVSS metrics
- Various exploit lists (e.g., CISA KEV, Google Project Zero, Trend Micro’s Zero Day Initiative)
By analyzing this data[LZ1] [RG2] and monitoring exploitation activity through various methods, such as honeypots, IDS/IPS sensors, and host-based detection, EPSS provides a nuanced understanding of the urgency and impact of vulnerabilities. It uses machine learning to detect patterns and connections between vulnerability data and exploitation activities gathered over time.
Interpreting EPSS Scores
EPSS data is refreshed daily and offers two key metrics: probability and percentiles.
Probability represents the likelihood of a vulnerability being exploited in the wild within the next 30 days, while the percentile indicates the percentage of vulnerabilities that have a score equal to, or lower than, a particular vulnerability’s score.
For example, an EPSS probability of just 0.10 (10%) rests at about the 88th percentile – meaning that 88% of all CVEs are scored lower. These percentiles are derived from probabilities and offer insights into how a particular EPSS probability compares to all other scores – all the other CVEs.
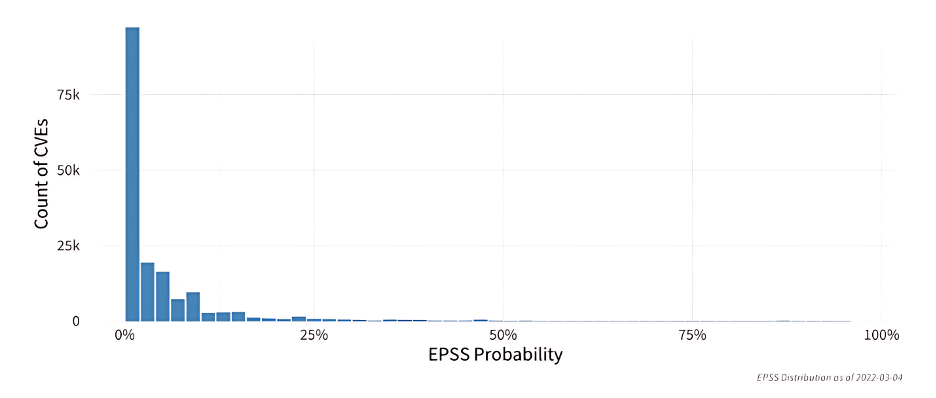
The figure below shows the probability distribution of EPSS scores for over 170,000 vulnerabilities as of March 2022. It illustrates that most vulnerabilities score below 10%, indicating a global measure of vulnerability exploitation in the wild.
Limitations and Considerations
While EPSS is a powerful tool, it’s essential to understand its limitations and use it in conjunction with other exploitability metrics and threat intelligence. Some key points to keep in mind:
- EPSS scores are founded in gathered data, which means they can change over time which could introduce mistakes.
- If there is evidence that a vulnerability is being actively exploited, that information should supersede EPSS, as EPSS is pre-threat intel, and therefore may lag behind live incidents.
- The model only produces scores based on available data, which is based only on disclosed and known incidents – public availability for information the model itself are acknowledged limitations.
- EPSS is a risk management model – just because a vulnerability has been exploited in the past does not guarantee future exploitation and, conversely, just because a vulnerability has been known for a while and not actively exploited does not guarantee it will not surge soon.
EPSS Score vs. CVSS: Understanding the Difference
EPSS and CVSS (Common Vulnerability Scoring System) are both measures to help organizations manage vulnerabilities, but they serve different purposes.
EPSS aims to predict the likelihood of a vulnerability being exploited, using a forward-looking and probabilistic approach. In contrast, CVSS evaluates the severity of a vulnerability by assessing its characteristics and potential impact, with a descriptive and deterministic approach.
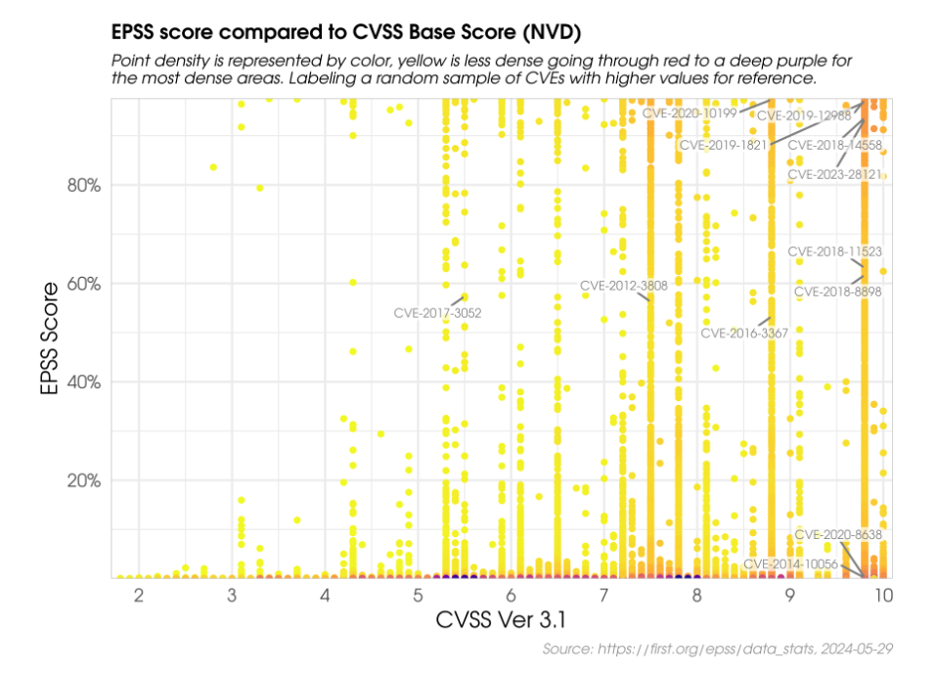
The graph below shows the comparison between CVSS and EPSS scores for a sample of CVEs.
EPSS Value in Prioritizing Remediation and Risk Management
EPSS should be treated as one aspect of the overall vulnerability management picture, complementing other factors like CVSS.
FIRST compares two strategies, one prioritizing CVEs with CVSS 7 and higher, and another prioritizing CVEs with EPSS of 0.1 and higher.
They compared:
Effort – The proportion of vulnerabilities being prioritized for remediation
Efficiency – How efficiently resources were spent by measuring the percent of prioritized vulnerabilities that were exploited.
Coverage – The percent of exploited vulnerabilities that were prioritized, calculated as the number of exploited vulnerabilities prioritized (TP – correctly prioritized) divided by the total number of exploited vulnerabilities (TP + FN – correctly prioritized + incorrectly delayed).
By prioritizing vulnerabilities with an EPSS of 0.1 and higher, organizations can significantly reduce their remediation effort while improving efficiency.
They also analyzed EPSS and CVSS scores to understand their correlation [3]. The analysis showed that attackers do not exclusively target the most impactful or easiest-to-exploit vulnerabilities, challenging the assumption that they only focus on the most severe ones. Therefore, it’s recommended to use a combination of factors to effectively prioritize which vulnerabilities to patch first.
EPSS at Checkmarx
At Checkmarx, we understand the importance of effective vulnerability management. That’s why Checkmarx Customers using the Checkmarx One Platform can leverage the integrated EPSS scores for quicker and more effective risk triaging and remediation.
EPSS complements our existing array of exploitability metrics which include but are not limited to:
- KEV (Known Exploited Vulnerability): A vulnerability cataloged by CISA as a Known Exploited Vulnerability, indicating that it poses a severe and imminent threat.
- POC (Proof of Concept): A Proof of Concept for exploiting the vulnerability is available in the wild, making it easy for threat actors to implement an exploitation of this vulnerability.
- Exploitable Path: This feature analyzes whether your source code provides a path that can be exploited by a specific vulnerability. Checkmarx SCA leverages SAST’s ability to scan the actual project code itself in parallel with scanning the manifest file, validating whether the vulnerable open-source packages are called from your proprietary code and whether the vulnerable methods are used by your code. This enables you to focus on the remediation of actively exploitable vulnerabilities. Exploitable Path also identifies which lines in your project code reach the vulnerable method in the vulnerable package and shows you the full path to the vulnerability.
By combining these tools, our customers can achieve a comprehensive view of their vulnerability landscape and take proactive measures to mitigate risks with high potential to be exploited by malicious actors.
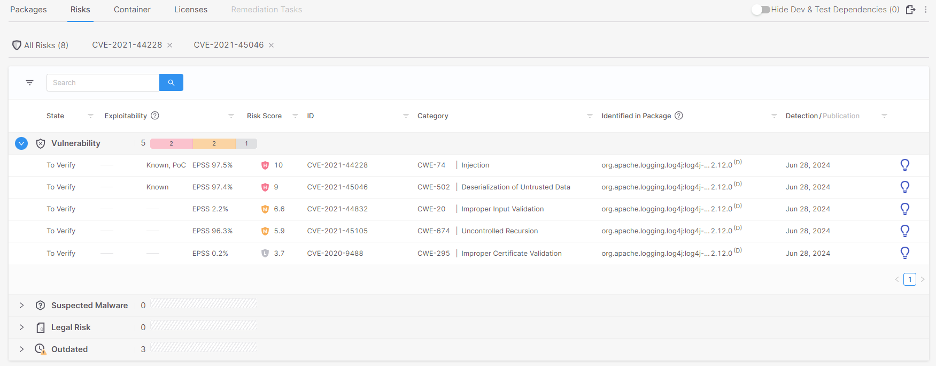
The following displays how EPSS, and other exploitability metrics, are integrated into Checkmarx’ product.
Conclusion
Staying ahead of current threats requires a proactive and data-driven approach. EPSS offers organizations a valuable tool to prioritize their vulnerability management efforts effectively. By leveraging EPSS alongside other exploitability metrics, security professionals can make informed decisions, allocate resources efficiently, and strengthen their overall security posture.
At Checkmarx, we are committed to providing our customers with the most comprehensive and cutting-edge vulnerability management solutions and empowering organizations to navigate the complex landscape of open-source vulnerabilities with confidence and precision.
