
2024-10-4 01:16:26 Author: therecord.media(查看原文) 阅读量:5 收藏
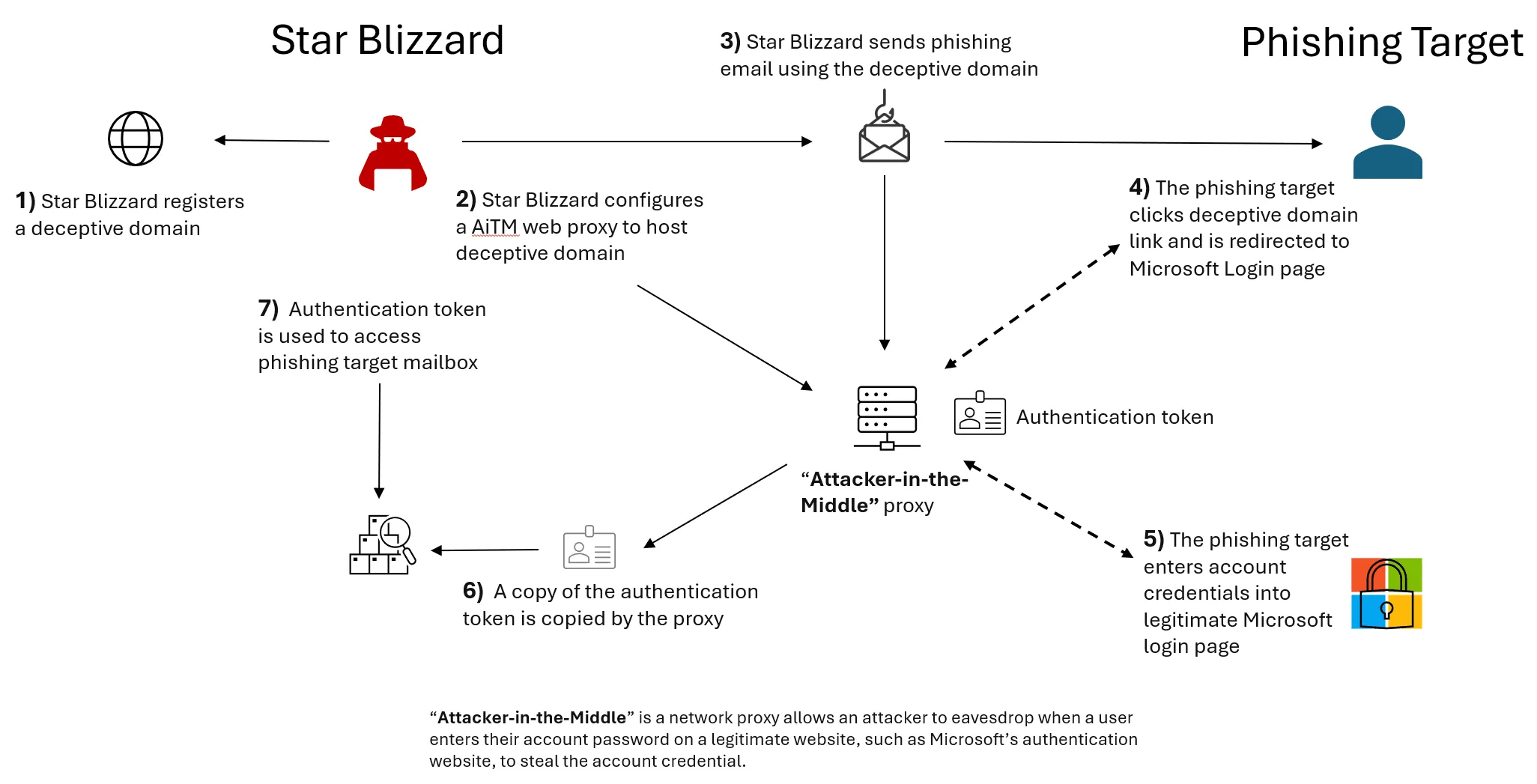
Dozens of domains and websites were taken down by the Justice Department and Microsoft this week after investigators tied the tools to an espionage campaign by the Russian government. The DOJ unsealed a warrant on Thursday authorizing agents to seize 41 internet domains they say are “used by Russian intelligence agents and their proxies to commit computer fraud and abuse in the United States.” According to the documents filed in the U.S. District Court for the Eastern District of Virginia, the domains were “used by hackers belonging to, or criminal proxies working for, the ‘Callisto Group,’ an operational unit within Center 18 of the Russian Federal Security Service (the FSB).” Prosecutors accused Callisto Group of targeting former members of the U.S. intelligence community, former and current Department of Defense and State Department employees, as well as a coterie of military contractors and staff at the Department of Energy. Deputy Attorney General Lisa Monaco said the Russian government “ran this scheme to steal Americans’ sensitive information, using seemingly legitimate email accounts to trick victims into revealing account credentials.” Those credentials were then used to access other government systems because victims often reused the same login information. The stolen documents related to foreign affairs, defense information, nuclear energy technology, research and more. U.S. Attorney Ismail Ramsey for the Northern District of California added that the goal of the operation was to dismantle the infrastructure that Russian cyber-espionage actors use to attack the U.S. and international targets. The Callisto Group used the domains “in an ongoing and sophisticated spearphishing campaign with the goal of gaining unauthorized access to, and steal valuable information from, the computers and email accounts of U.S. government and other victims,” he said. Microsoft filed a corresponding case in civil court requesting authorization to take down 66 other internet domains also used in spearphishing attacks. Between January 2023 and August 2024, the company observed Callisto Group, which they call Star Blizzard, target more than 30 civil society entities and organizations — including journalists, think tanks and nongovernmental organizations (NGOs) — by deploying spearphishing campaigns to exfiltrate sensitive information and interfere in their activities. The actions from the Justice Department and Microsoft build on charges filed in December 2023 against Ruslan Aleksandrovich Peretyatko, an officer at the FSB, and Andrey Stanislavovich Korinets for their alleged roles in Callisto attacks. Assistant Attorney General Matthew Olsen noted that the measures taken on Thursday were part of a larger effort to collaborate with the private sector on cybersecurity issues connected to national security. “Disruptions like the one announced today strip our adversaries of the tools they rely on to target individuals, businesses, and governments all around the world,” Olsen said. “Our fight against this and other cyber-enabled threats to our national security are by no means over.” Steven Masada, assistant general counsel at Microsoft’s Digital Crimes Unit, said in a blog post that the suit was filed with the NGO Information Sharing and Analysis Center (NGO-ISAC) and that more than 100 websites had been seized. A Microsoft spokesperson told Recorded Future News that all of the domains were used in documents and emails to redirect phishing targets to the web proxy in order to steal user credentials. Credit: Microsoft In total, Microsoft has tracked 82 customers that were targeted by Callisto Group since January 2023 — a rate of one attack per week. The group typically spends time crafting personalized phishing emails and creating infrastructure designed to steal credentials. “Rebuilding infrastructure takes time, absorbs resources, and costs money. By collaborating with DOJ, we have been able to expand the scope of disruption and seize more infrastructure, enabling us to deliver greater impact against Star Blizzard,” he said. “While we expect Star Blizzard to always be establishing new infrastructure, today’s action impacts their operations at a critical point in time when foreign interference in U.S. democratic processes is of utmost concern.” Both Citizen Lab and Access Now filed declarations in support of Microsoft’s civil lawsuit. The two organizations published a paper on Callisto Group's actions in August and have since discovered several other victims connected to the campaign. Natalia Krapiva, senior legal counsel at Access Now, said they got involved in the lawsuit because they identified several Russian civil society groups where employee email accounts were targeted or successfully compromised by Callisto Group. Krapiva said Microsoft asked them to contribute to the lawsuit to share stories of how journalists and human rights workers are being targeted through this digital infrastructure. Several impact statements directly from victims are in the filings, which are sealed to protect their identities. “All of the information of their staff — their location, obviously in emails, people's names, contacts — all of that information is now potentially with FSB,” she said. “So [we are] asking the judge to take action, to take down the infrastructure, but also hopefully uncover the identities of these people so there could be potentially sanctions or criminal consequences.” Many of those targeted by Callisto Group “were already under extreme persecution and pressure,” she added, noting that most are exiled and under surveillance, and at constant risk of physical and digital attacks. Krapiva noted that some of the targeted groups had to evacuate staff or even sever connections to people in Russia that could be put in danger if their identities were exposed. Some of them are helping refugees from Russia, including those who have fled persecution by providing legal support and other services. “So this phishing campaign, on top of all of those existing risks, has had really devastating effects. Some of the organizations have told me that this is one of the most serious attacks they have faced in a while,” she said. “There's a very sensitive information that they have in their email account and being exposed to the FSB is really something that was extremely serious and really impacted them psychologically." Callisto Group was implicated by the British government last year in a wide-ranging scheme to interfere in United Kingdom politics by targeting elected officials, think tanks, journalists and others. It has a long history of cyberattacks and espionage dating back to at least 2017, Microsoft’s Masada said. The group has recently shifted its focus to NGOs and think tanks that support military and intelligence officials — particularly those working on issues related to Ukraine and NATO countries, he explained. Star Blizzard spearphishing
Get more insights with the
Recorded Future
Intelligence Cloud.
Tags
No previous article
No new articles
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh
