
2024-10-17 05:15:48 Author: therecord.media(查看原文) 阅读量:14 收藏
Two Sudanese nationals were indicted on Wednesday in the U.S. for their role in operating the Anonymous Sudan cybercriminal group, which launched hundreds of attacks that knocked critical websites offline. Brothers Ahmed Salah Yousif Omer, 22, and Alaa Salah Yusuuf Omer, 27, were both charged with one count of conspiracy to damage protected computers and Ahmed Salah was also charged with three counts of damaging protected computers. The Justice Department declined to comment on where the two are located or if arrests have been made. The Washington Post, which first reported the charges, said both men were arrested in March. If convicted on all charges, Ahmed Salah could face life in prison while Alaa Salah would face up to five years in federal prison. The unsealed indictment accuses the two of operating and controlling Anonymous Sudan — a notorious operation that launched powerful distributed denial of service (DDoS) attacks against critical infrastructure, corporate networks, and government agencies in the United States and around the world. U.S. Attorney Martin Estrada said Anonymous Sudan “sought to maximize havoc and destruction against governments and businesses around the world by perpetrating tens of thousands of cyberattacks.” “This group’s attacks were callous and brazen — the defendants went so far as to attack hospitals providing emergency and urgent care to patients,” he said. Anonymous Sudan has spent years boasting of its attacks on hospitals, government agencies and companies through its Telegram channel. The Justice Department noted that some of the group’s victims include the DOJ itself as well as the Defense Department, FBI, State Department and government websites run by the state of Alabama. The group also targeted multiple hospitals around the world including Cedars-Sinai Medical Center in Los Angeles and companies like Microsoft. Image: Crowdstrike DDoS attacks are typically temporary, overloading websites with requests to knock them offline for hours or days. But the Justice Department said Anonymous Sudan’s attacks caused “network outages affecting thousands of customers.” “Anonymous Sudan’s DDoS attacks, which at times lasted several days, caused damage to the victims’ websites and networks, often rendering them inaccessible or inoperable, resulting in significant damages,” the DOJ explained. “For example, Anonymous Sudan’s DDoS attacks shuttered the emergency department at Cedars-Sinai Medical Center, causing incoming patients to be redirected to other medical facilities for approximately eight hours. Anonymous Sudan’s attacks have caused more than $10 million in damages to U.S. victims.” The FBI also noted that it used a court warrant in March to seize and disable the group’s DDoS tool, named Distributed Cloud Attack Tool (DCAT) but referred to as “Godzilla” — which they sold as a service to other criminal groups. The tool was used “to launch over 35,000 DDoS attacks, including at least 70 targeting computers in the greater Los Angeles area,” according to Justice Department officials. The warrant allowed law enforcement to seize the servers that launched the DDoS attacks as well as those that relayed attack commands to a larger network of computers. The operations against Anonymous Sudan and DCAT were part of a larger effort called Operation PowerOFF, which is a coordinated partnership between law enforcement agencies and private companies like Amazon, Akamai, Cloudflare, Crowdstrike, Google, Microsoft and others. Several of the companies released blog posts about the information they offered law enforcement to assist the investigation. Amazon’s Tom Scholl said they have used internal tools to request the takedown of infrastructure used by DDoS groups like Anonymous Sudan, noting that over the last year, they have requested “more than 2,500 hosting providers and domain registrars take down more than 80,000 distinct hosts and domains.” According to Amazon researchers, Anonymous Sudan offered DDoS attacks for $100 per day, $600 per week, and $1,700 per month — with dozens of customers. “Criminal groups and other bad actors purchase services from groups like Anonymous Sudan to shut down websites or infrastructure systems,” Amazon said. “In fact, the market has become so sophisticated that groups like Anonymous Sudan will sometimes offer ‘customers’ pricing tiers, and even refunds, if the attack doesn’t have the desired result.” Crowdstrike noted that Anonymous Sudan’s silence since March aligns with the FBI’s operation and added that the group often attempted to paint their attacks as politically or religiously motivated. They often coordinated with other pro-Russian DDoS groups like Killnet and SiegedSec, leading some to initially believe it may have been operated by the Russian government. “It is remarkable that just two individuals, with a relatively small investment of time and resources, were able to create and maintain a DDoS capability potent enough to disrupt major online services and websites,” Crowdstrike said. “Their success stemmed from a combination of factors: a custom-built attack infrastructure hosted on rented servers with high bandwidth, sophisticated techniques for bypassing DDoS mitigation services, and the ability to quickly identify and exploit vulnerable API endpoints that, when overwhelmed with requests, would render services inoperable and disrupt user access.” 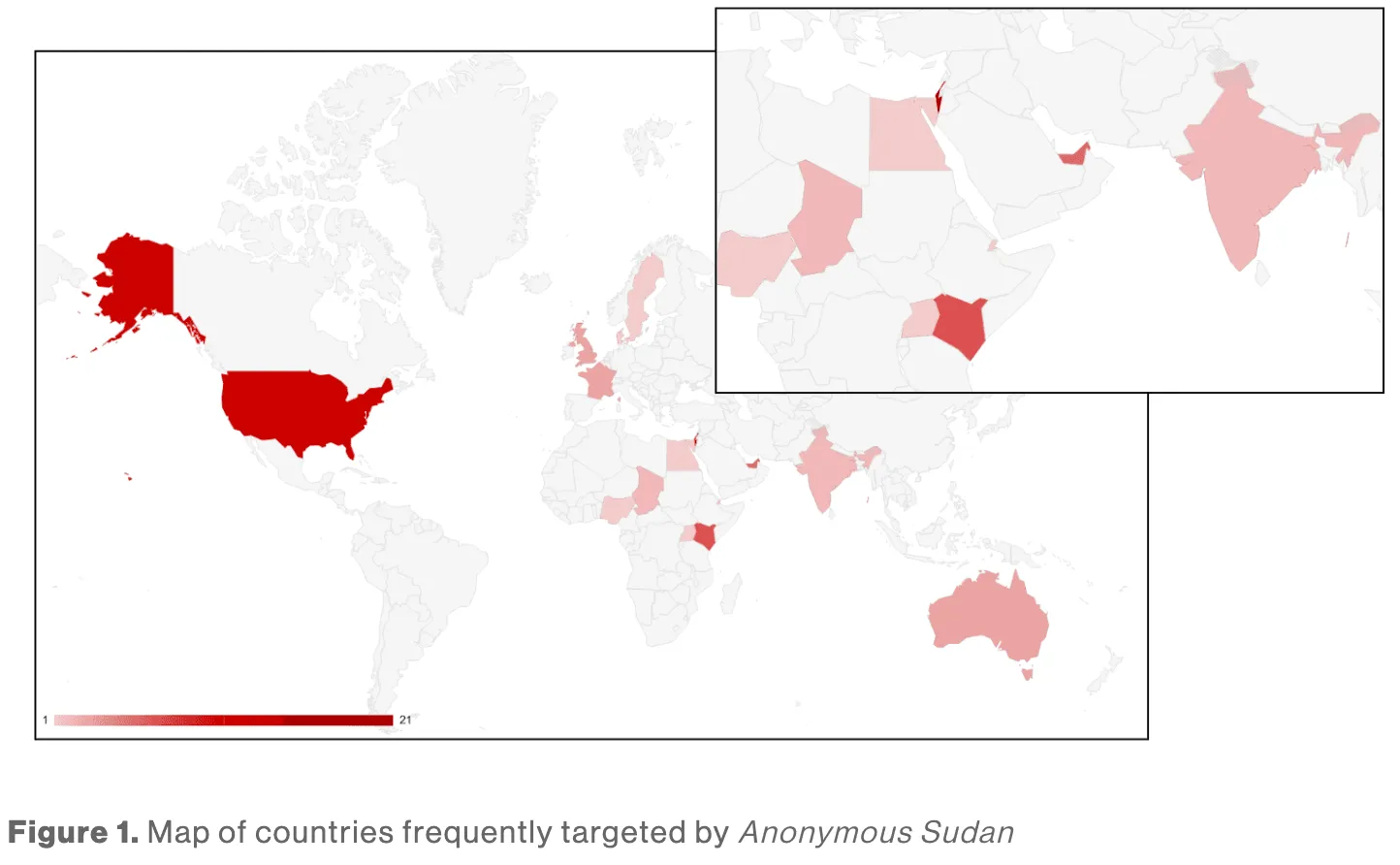
‘Godzilla’
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh
