
2024-10-17 18:0:5 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:1 收藏
Executive Summary
Unit 42 researchers have found that certain third-party utilities and applications pertaining to archiving, virtualization and Apple’s native command-line tools do not enforce the quarantine attribute. This can pose a threat to the integrity of a security feature on macOS known as Gatekeeper, which is responsible for ensuring that only trusted software runs on the system. A bypass of Gatekeeper could leave the user unprotected from risky applications that may attempt to execute malicious content.
One of the key components of the Gatekeeper security feature on macOS is a metadata attribute that the browser adds to downloaded files, which triggers Gatekeeper to validate the application. Apple assumes that developers will comply with their security guidelines regarding the inheritance of extended attributes, to ensure that this scanning mechanism can properly function. Because this is not necessarily the case, this can pose a weakness in the Gatekeeper mechanism.
We urge all third-party developers to comply with Gatekeeper’s security requirements by enforcing the attribute on all files their applications handle. This will help to reduce the risk of malicious Gatekeeper bypasses.
Gatekeeper is an essential security mechanism on macOS; ideally its integrity will not rely on the goodwill of developers but on Apple’s enforcement of the quarantine attribute propagation where relevant. While Apple expects third-party application developers to keep a certain standard, some built-in utilities do not comply with this standard. Should Apple choose to do so, addressing this issue could be a positive step toward making the system more secure.
Palo Alto Networks customers are protected from malicious content from third-party applications through Cortex XDR and XSIAM.
| Related Unit 42 Topics | macOS, Apple |
The Gatekeeper Mechanism
Gatekeeper is a security mechanism on macOS that ensures only trusted software runs on the system. When a user downloads software from outside the Apple App Store, Gatekeeper confirms that the software is from a verified developer and hasn't been altered.
Gatekeeper requests the user’s approval before opening the downloaded software for the first time, as shown in Figure 1.
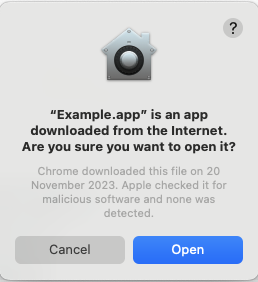
Apps that Apple adds to their own App Store go through a process called Notarization in which Apple scans the application to verify it is properly signed and that it is not malicious.
The Com.apple.quarantine Extended Attribute and Its Role in the Gatekeeper Mechanism
On macOS, extended attributes are additional pieces of metadata that the user or system can associate with a file. These attributes can be used to store additional information.
Extended attributes on macOS don't have any permission system. This means that any user or process can delete, add or modify any attribute without requiring any special permissions.
This lack of permission system affects the com.apple.quarantine attribute, which is the focus of this research. The com.apple.quarantine extended attribute is automatically added to newly downloaded files on macOS.
Upon execution of a newly downloaded file, this extended attribute will trigger Gatekeeper to check and validate the binary before it allows execution. This checking process includes asking for the user’s consent.
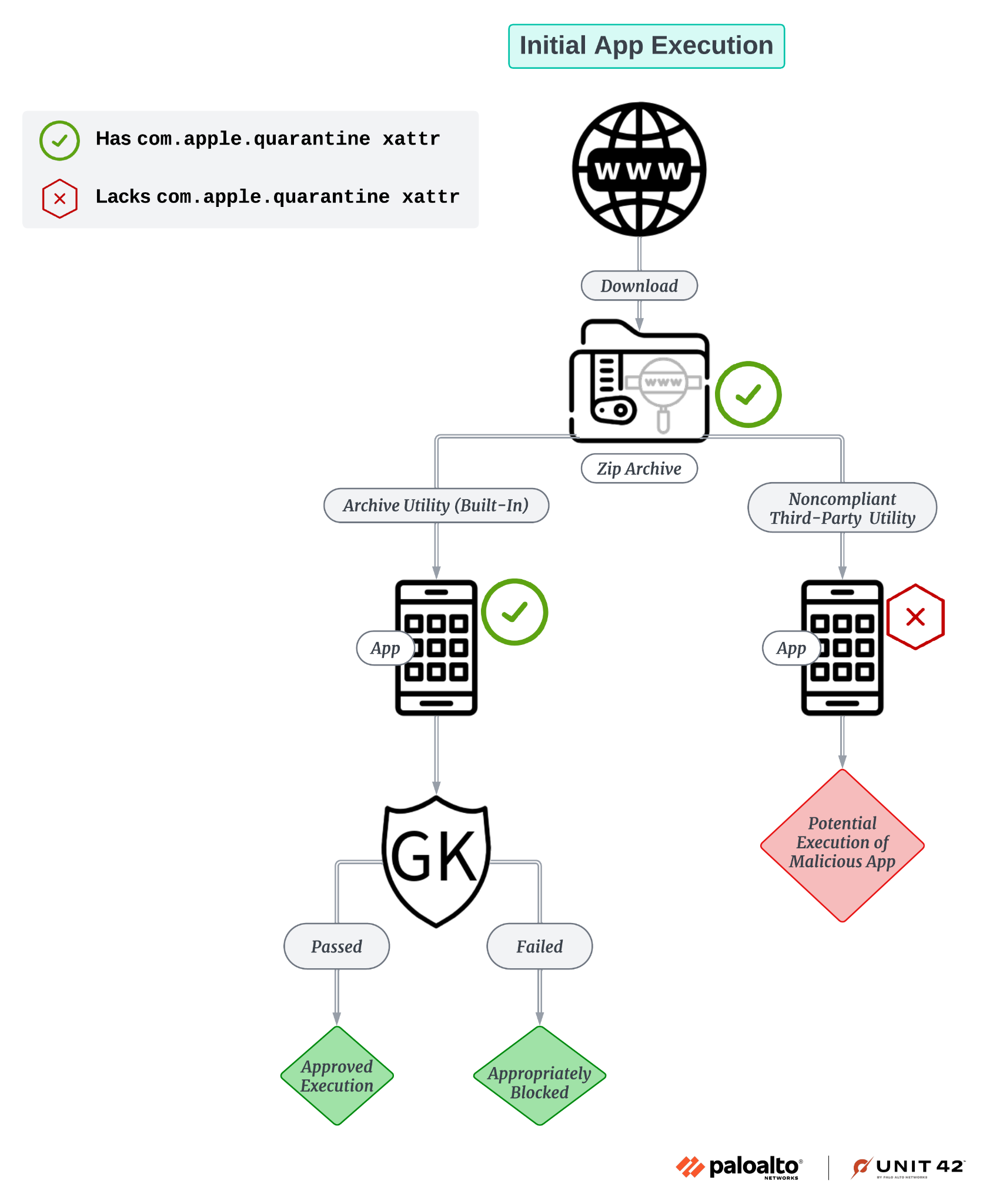
Gatekeeper will clear the extended attribute after a successful examination. Files lacking the com.apple.quarantine will be excluded from a Gatekeeper check, as shown in Figure 2.
Past Gatekeeper Bypasses
In recent years, we have seen several examples where attackers and security researchers have put focus on ways to bypass the Gatekeeper mechanism. In these bypasses, the root cause was the lack of the com.apple.quarantine extended attribute, caused by subverting Apple’s inheritance logic of the quarantine attribute.
Many malware and adware families (such as CoinTicker, Shlayer and Bundlore) use the built-in utility curl to download their payload. In this way, they can bypass Gatekeeper because curl does not set the quarantine attribute.
Security researchers have reported vulnerabilities related to the use of crafted ZIP archives and revealed issues with the inheritance of the com.apple.quarantine extended attribute from the archive file.
- CVE-2022-32910 (disclosed by Ferdous Saljook)
- CVE-2022-22616 (disclosed by Ferdous Saljooki, Mickey Jin and Jaron Bradley)
Apple has addressed all the above CVEs in later macOS versions.
Apple’s Oversight Over Third-Party Applications
When looking at third-party applications and utilities, Apple assumes developers will comply with their security guidelines regarding properly propagating the com.apple.quarantine extended attribute to the relevant destination files, to maintain the security mechanism’s integrity.
During our research, we came across vulnerable applications from different genres, such as virtualization and file archiving.
We reached out to Apple regarding this security issue and received the following statement:
“We have determined this issue is best addressed by you sending your report to the third-party app developer. It's up to the developer to implement quarantining, and this isn't an app we can directly support.”
Research Method
We began our research by examining Archiver, which is a popular third-party archiving application for macOS. While working with this application, we noticed that the extracted files did not inherit the quarantine attribute upon extraction of .archiver files, which allowed for the Gatekeeper bypass.
We then looked for this behavior in other file formats supported by this application. We discovered that other popular archiving file types such as ZIP, RAR and 7ZIP don't inherit the quarantine attribute either when using this app. We assumed that if it happened in this one third-party application, it could happen in other archiving tools and applications as well.
At first, we looked for similar applications and manually tested whether this issue reappeared, which it did in several other cases. After seeing that this issue was more widespread, we tried to look for a more efficient method to monitor for this behavior.
We decided to programmatically monitor whether different third party apps were writing files lacking the quarantine extended attribute. As a result, we noticed this behavior in multiple apps and utilities from different categories.
Figure 3 shows how we used the xattr utility for this purpose, to both display and manipulate extended attributes.
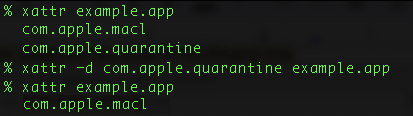
We found that there were three main categories of application where files were not properly inheriting the com.apple.quarantine attribute. The first is archive applications, the second was virtualization software and the third was command-line tools. The next sections will discuss in more details which applications and circumstances we observed this in.
Archive Applications
Apple states that user-installed unarchiving tools preserve quarantine. As we can see in the following examples, there are some third-party archive tools that do not enforce that, which means that Gatekeeper won’t scan the extracted files.
These are the utilities and formats that we tested and found vulnerable:
- iZip: ZIP, TAR and 7Z
- Archiver: ARCHIVER, ZIP, TAR and 7Z
- BetterZip: ZIP, TAR and 7Z
- WinRAR: ZIP, TAR and 7Z
- 7z Utility: DMG, ZIP and 7Z
Virtualization
In VMware Fusion, when copying a file from a host machine to a guest macOS virtual machine (VM) using VMware tools, the quarantine extended attribute will be dropped from the copied file as shown in Figure 4. This means Gatekeeper won’t scan any files copied into the virtual machine.
Figure 4. Demonstration of copying a file to a VM using VMware Tools removing its com.apple.quarantine attribute.
The nature of copying files into a virtual machine is different from downloading files from an external source, in that the user is more likely to be aware of the nature of the file being copied. In order to enhance security, the user can choose to disable application execution downloaded from outside of the App Store.
Native Command-Line Tools
Generally, Apple does not enforce the quarantine extended attribute in command-line tools. Apple explains that Unix-based networking tools, such as SCP and curl, won’t mark their downloaded files as quarantined.
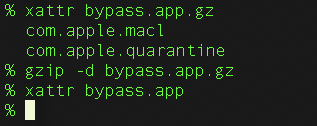
In addition, files unarchived by Unix-based command-line unarchiving tools such as Unzip and tar won’t inherit the quarantine extended attribute, as shown in Figure 5.
Vendors' Responses and Remediation
We have tried to reach the developers for all the mentioned products, and these are the responses we received:
- BetterZip: “BetterZip has been quarantining extracted apps and executables since version 5. Quarantining for nested archives will be included in an update later this week.”
- Archiver: “Thank you for letting us know. Please be advised that we are releasing a series of updates that are addressing these issues.”
- iZip: “v4.6 will be out very soon which sets xattrs of extracted apps to that of the original archive. It's worth noting that iZip never automatically extracts or opens anything without user interaction, but your point is valid so we've implemented the change.”
- VMWare: “Given the security target of preventing the execution of untrusted binaries on a machine using Gatekeeper technology has reliance on the quarantine flag which limits the capabilities of an integrity protection mechanism. For users in high security environments macOS can be configured to only allow execution of software from the App Store."
Conclusion
Gatekeeper is an important security mechanism that draws the attention of both security researchers and attackers. This mechanism makes it more difficult for attackers to execute malicious content from risky applications. However, Gatekeeper’s design relies heavily on the implementation of third-party developers to comply with its security standards.
In addition, Apple does not enforce the quarantine extended attribute on its own native command-line tools. The mechanism’s failure in scanning files in such cases creates weaknesses, which might pose a risk for users. Organizations should take extra caution while using these tools.
As described, the Gatekeeper mechanism faces many potential bypass possibilities. One of the best protections for an organization against a potential attack using a Gatekeeper bypass is to use a multi-layer protection approach.
- Cortex XDR and XSIAM are designed to prevent the execution of known malware, and also prevent the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
Additional Resources
- Resolving Trusted Execution Problems – Apple Developer Forums
- Gatekeeper and runtime protection in macOS – Apple Platform Security
- Gatekeeper’s Achilles heel: Unearthing a macOS vulnerability – Microsoft Security Blog
- Jamf Threat Labs identifies macOS Archive Utility vulnerability allowing for Gatekeeper bypass (CVE-2022-32910) – Jamf
- iZip – izip.com
- RAR for linux and Mac by WinRAR – WinRAR
- Archiver 4 – Incredible Bee
- BetterZip – MacItBetter
- 7-Zip – Igor Pavlov
- Run Windows and More on Mac VMware Fusion
- Notarizing macOS software before distribution – Apple Developer Documentation
- Mac cryptocurrency ticker app installs backdoors – Malwarebytes Labs
- Shlayer Trojan attacks one in ten macOS users – Securelist
- New macOS Bundlore Loader Analysis – taha aka "lordx64" on Medium
如有侵权请联系:admin#unsafe.sh