
阅读: 0
北京时间5月13日,微软发布5月安全更新补丁,修复了111个安全问题,涉及Microsoft Windows、Internet Explorer、Microsoft Edge、.NET Framework、Microsoft Office、Visual Studio等广泛使用的产品,其中包括特权提升和远程代码执行等高危漏洞类型。
本月微软月度更新修复的漏洞中,严重程度为关键(Critical)的漏洞共有16个,重要(Important)漏洞有95个。其中Win32k 特权提升(CVE-2020-1054)漏洞PoC的已公开,请相关用户及时更新补丁进行防护,详细漏洞列表请参考附录。
参考链接:
https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-May
重点漏洞简述
根据产品流行度和漏洞重要性筛选出此次更新中包含影响较大的漏洞,请相关用户重点进行关注:
- CVE-2020-1054(PoC已公开)/CVE-2020-1143:Win32k 特权提升漏洞
由于Windows kernel-mode driver未能正确处理内存中的对象,导致存在两个特权提升漏洞。攻击者可通过登录目标系统并运行特制的应用程序来进行利用,成功利用此漏洞的攻击者可以在系统内核模式中执行任意代码。
官方通告链接:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1054
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2020-1143
- CVE-2020-1067:Windows 远程执行代码漏洞
Windows 在处理内存对象的过程中存在远程执行代码漏洞。具有域用户帐户的攻击者通过发送特殊的请求,从而使 Windows 执行提升权限的任意代码。成功利用此漏洞可以在受影响的Windows上以更高的权限执行任意代码。
官方通告链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1067
- CVE-2020-1153:Microsoft 图形组件远程代码执行漏洞
Microsoft Graphics Components在处理内存对象的过程中存在远程代码执行漏洞。攻击者可通过诱导用户打开特制文件来利用此漏洞,成功利用此漏洞的攻击者可在目标系统上执行任意代码。
官方通告链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1153
- CVE-2020-1062:Internet Explorer 内存损坏漏洞
当 Internet Explorer 不正确地访问内存中的对象时,存在远程执行代码漏洞。该漏洞可能以一种攻击者可以在当前用户的上下文中执行任意代码的方式损坏内存。成功利用该漏洞的攻击者可以获得与当前用户相同的用户权限。当用户访问一个特别设计的、由攻击者控制的web页面时,可能会触发此漏洞。
官方通告链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1062
- CVE-2020-1023、CVE-2020-1024、CVE-2020–1102和CVE-2020-1069:Microsoft SharePoint 远程执行代码漏洞
以上4个为微软SharePoint中的远程代码执行漏洞。攻击者可以利用此类漏洞获得在受影响终端或服务器上执行任意代码的能力。由于SharePoint无法检查应用程序包的源标记,前3个漏洞可以诱导用户打开一个特别制作的SharePoint应用程序文件从而进行利用。由于SharePoint Server无法正确识别和筛选不安全的 ASP.NET Web 控件,经过身份验证的攻击者通过上传一个特别制作的页面到SharePoint服务器,可成功利用CVE-2020-1069漏洞。
官方通告链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1023
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1024
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1102
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1069
- CVE-2020-0901:Microsoft Excel 远程执行代码漏洞
由于Microsoft Excel无法正确处理内存中的对象,导致存在远程执行代码漏洞。攻击者通过诱使用户使用受影响版本的Microsoft Excel打开经过特殊设计的文件进行利用。成功利用此漏洞的攻击者可以获得与当前用户相同的系统控制权限。
官方通告链接:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0901
影响范围
以下为重点关注漏洞的受影响产品版本,其他漏洞影响产品范围请参阅官方通告链接。

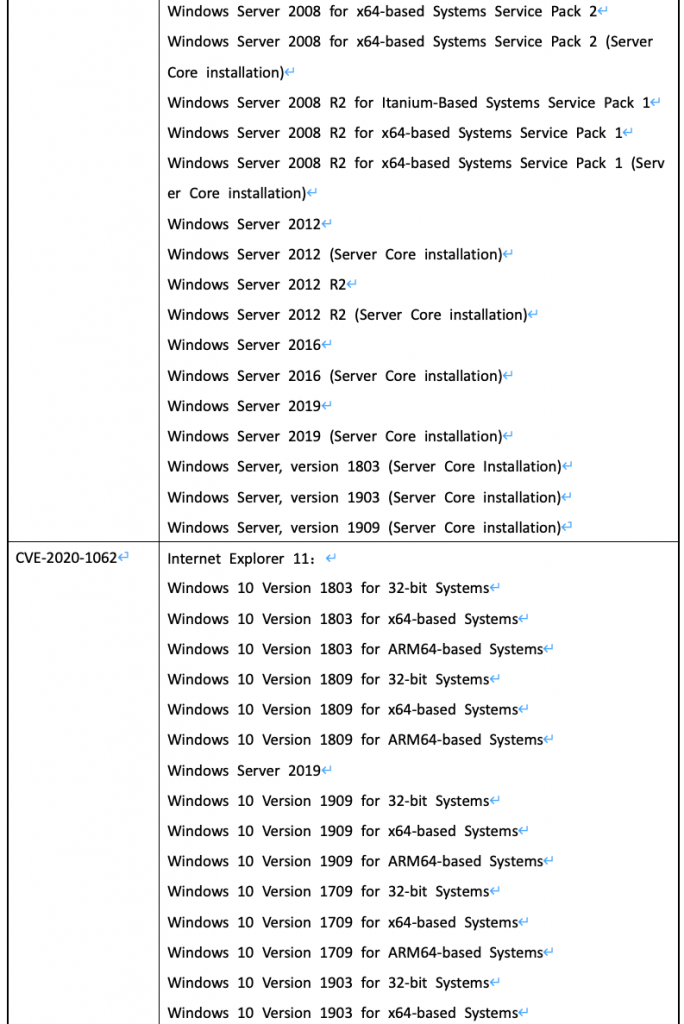
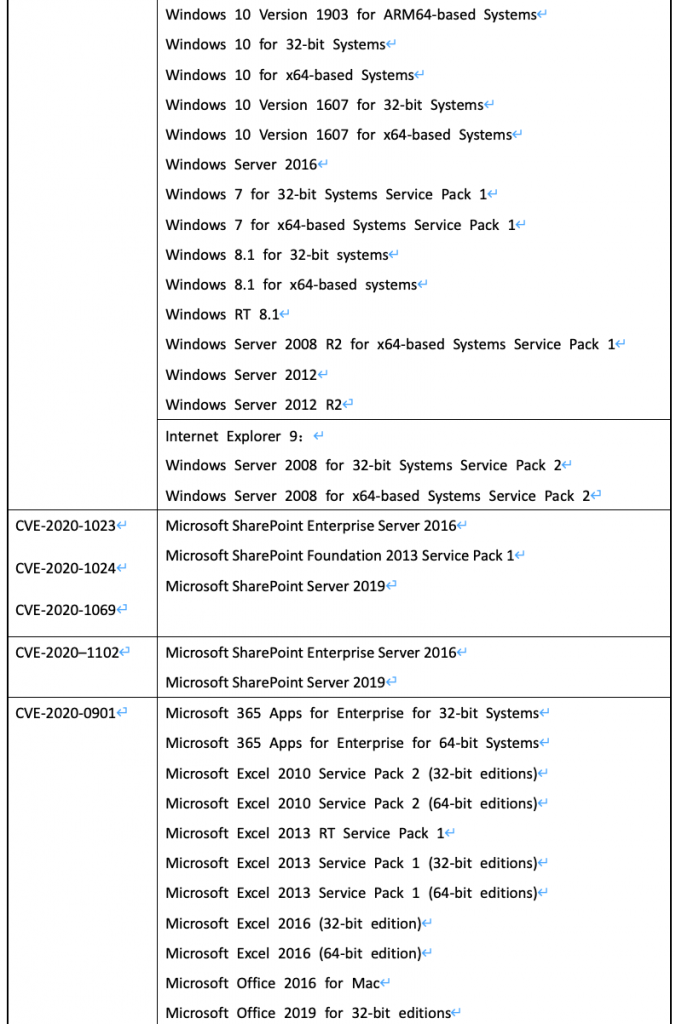
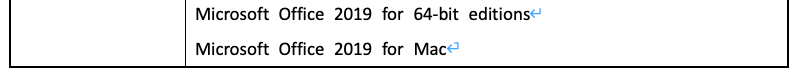
漏洞防护
目前微软官方已针对受支持的产品版本发布了修复以上漏洞的安全补丁,强烈建议受影响用户尽快安装补丁进行防护,官方下载链接:
https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-May
注:由于网络问题、计算机环境问题等原因,Windows Update的补丁更新可能出现失败。用户在安装补丁后,应及时检查补丁是否成功更新。
右键点击Windows图标,选择“设置(N)”,选择“更新和安全”-“Windows更新”,查看该页面上的提示信息,也可点击“查看更新历史记录”查看历史更新情况。
针对未成功安装的更新,可点击更新名称跳转到微软官方下载页面,建议用户点击该页面上的链接,转到“Microsoft更新目录”网站下载独立程序包并安装。
附录:漏洞列表
| 影响产品 | CVE 编号 | 漏洞标题 | 严重程度 |
| Microsoft Graphics Component | CVE-2020-1117 | Microsoft Color Management 远程代码执行漏洞 | Critical |
| Microsoft Graphics Component | CVE-2020-1153 | Microsoft Graphics Components 远程代码执行漏洞 | Critical |
| Microsoft Office SharePoint | CVE-2020-1023 | Microsoft SharePoint 远程代码执行漏洞 | Critical |
| Microsoft Office SharePoint | CVE-2020-1024 | Microsoft SharePoint 远程代码执行漏洞 | Critical |
| Microsoft Scripting Engine | CVE-2020-1037 | Chakra Scripting Engine 内存破坏漏洞 | Critical |
| Microsoft Office SharePoint | CVE-2020-1069 | Microsoft SharePoint Server 远程代码执行漏洞 | Critical |
| Microsoft Office SharePoint | CVE-2020-1102 | Microsoft SharePoint 远程代码执行漏洞 | Critical |
| Microsoft Scripting Engine | CVE-2020-1065 | Scripting Engine 内存破坏漏洞 | Critical |
| Microsoft Windows | CVE-2020-1028 | Media Foundation 内存破坏漏洞 | Critical |
| Microsoft Windows | CVE-2020-1126 | Media Foundation 内存破坏漏洞 | Critical |
| Microsoft Windows | CVE-2020-1136 | Media Foundation 内存破坏漏洞 | Critical |
| Visual Studio | CVE-2020-1192 | Visual Studio Code Python Extension 远程代码执行漏洞 | Critical |
| Internet Explorer | CVE-2020-1064 | MSHTML Engine 远程代码执行漏洞 | Critical |
| Internet Explorer | CVE-2020-1093 | VBScript 远程代码执行漏洞 | Critical |
| Microsoft Edge | CVE-2020-1056 | Microsoft Edge 特权提升漏洞 | Critical |
| Internet Explorer | CVE-2020-1062 | Internet Explorer 内存破坏漏洞 | Critical |
| .NET Core | CVE-2020-1108 | .NET Core & .NET Framework 拒绝服务漏洞 | Important |
| .NET Core | CVE-2020-1161 | ASP.NET Core 拒绝服务漏洞 | Important |
| .NET Framework | CVE-2020-1066 | .NET Framework 特权提升漏洞 | Important |
| Active Directory | CVE-2020-1055 | Microsoft Active Directory Federation Services 跨站脚本漏洞 | Important |
| Common Log File System Driver | CVE-2020-1154 | Windows Common Log File System Driver 特权提升漏洞 | Important |
| Microsoft Dynamics | CVE-2020-1063 | Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability | Important |
| Microsoft Edge | CVE-2020-1059 | Microsoft Edge 欺骗漏洞 | Important |
| Microsoft Edge | CVE-2020-1096 | Microsoft Edge PDF 远程代码执行漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-0963 | Windows GDI 信息泄露漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1054 | Win32k 特权提升漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1135 | Windows Graphics Component 特权提升漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1140 | DirectX 特权提升漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1179 | Windows GDI 信息泄露漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1141 | Windows GDI 信息泄露漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1142 | Windows GDI 特权提升漏洞 | Important |
| Microsoft Graphics Component | CVE-2020-1145 | Windows GDI 信息泄露漏洞 | Important |
| Microsoft JET Database Engine | CVE-2020-1175 | Jet Database Engine 远程代码执行漏洞 | Important |
| Microsoft JET Database Engine | CVE-2020-1051 | Jet Database Engine 远程代码执行漏洞 | Important |
| Microsoft JET Database Engine | CVE-2020-1174 | Jet Database Engine 远程代码执行漏洞 | Important |
| Microsoft JET Database Engine | CVE-2020-1176 | Jet Database Engine 远程代码执行漏洞 | Important |
| Microsoft Office | CVE-2020-0901 | Microsoft Excel 远程代码执行漏洞 | Important |
| Microsoft Office SharePoint | CVE-2020-1099 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-1101 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-1107 | Microsoft SharePoint 欺骗漏洞 | Important |
| Microsoft Office SharePoint | CVE-2020-1100 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2020-1103 | Microsoft SharePoint 信息泄露漏洞 | Important |
| Microsoft Office SharePoint | CVE-2020-1104 | Microsoft SharePoint 欺骗漏洞 | Important |
| Microsoft Office SharePoint | CVE-2020-1105 | Microsoft SharePoint 欺骗漏洞 | Important |
| Microsoft Office SharePoint | CVE-2020-1106 | Microsoft Office SharePoint XSS Vulnerability | Important |
| Microsoft Windows | CVE-2020-1021 | Windows Error Reporting 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1010 | Microsoft Windows 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1048 | Windows Print Spooler 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1071 | Windows Remote Access Common Dialog 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1076 | Windows 拒绝服务漏洞 | Important |
| Microsoft Windows | CVE-2020-1078 | Windows Installer 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1084 | Connected User Experiences and Telemetry Service 拒绝服务漏洞 | Important |
| Microsoft Windows | CVE-2020-1116 | Windows CSRSS 信息泄露漏洞 | Important |
| Microsoft Windows | CVE-2020-1118 | Microsoft Windows Transport Layer Security 拒绝服务漏洞 | Important |
| Microsoft Windows | CVE-2020-1124 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1134 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1137 | Windows Push Notification Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1138 | Windows Storage Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1143 | Win32k 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1144 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1149 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1150 | Media Foundation 内存破坏漏洞 | Important |
| Microsoft Windows | CVE-2020-1151 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1155 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1156 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1157 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1158 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1186 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1189 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1190 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1067 | Windows 远程代码执行漏洞 | Important |
| Microsoft Windows | CVE-2020-1068 | Microsoft Windows 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1070 | Windows Print Spooler 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1072 | Windows Kernel 信息泄露漏洞 | Important |
| Microsoft Windows | CVE-2020-1077 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1079 | Microsoft Windows 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1081 | Windows Printer Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1082 | Windows Error Reporting 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1086 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1088 | Windows Error Reporting 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1090 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1111 | Windows Clipboard Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1112 | Windows Background Intelligent Transfer Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1121 | Windows Clipboard Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1123 | Connected User Experiences and Telemetry Service 拒绝服务漏洞 | Important |
| Microsoft Windows | CVE-2020-1125 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1131 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1132 | Windows Error Reporting Manager 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1139 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1164 | Windows Runtime 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1165 | Windows Clipboard Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1166 | Windows Clipboard Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1184 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1185 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1187 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1188 | Windows State Repository Service 特权提升漏洞 | Important |
| Microsoft Windows | CVE-2020-1191 | Windows State Repository Service 特权提升漏洞 | Important |
| Power BI | CVE-2020-1173 | Microsoft Power BI Report Server 欺骗漏洞 | Important |
| Visual Studio | CVE-2020-1171 | Visual Studio Code Python Extension 远程代码执行漏洞 | Important |
| Windows Hyper-V | CVE-2020-0909 | Windows Hyper-V 拒绝服务漏洞 | Important |
| Windows Kernel | CVE-2020-1114 | Windows Kernel 特权提升漏洞 | Important |
| Windows Kernel | CVE-2020-1087 | Windows Kernel 特权提升漏洞 | Important |
| Windows Scripting | CVE-2020-1061 | Microsoft Script Runtime 远程代码执行漏洞 | Important |
| Windows Subsystem for Linux | CVE-2020-1075 | Windows Subsystem for Linux 信息泄露漏洞 | Important |
| Windows Task Scheduler | CVE-2020-1113 | Windows Task Scheduler 安全功能绕过漏洞 | Important |
| Windows Update Stack | CVE-2020-1110 | Windows Update Stack 特权提升漏洞 | Important |
| Windows Update Stack | CVE-2020-1109 | Windows Update Stack 特权提升漏洞 | Important |
| Internet Explorer | CVE-2020-1092 | Internet Explorer 内存破坏漏洞 | Important |
| Microsoft Scripting Engine | CVE-2020-1035 | VBScript 远程代码执行漏洞 | Important |
| Microsoft Scripting Engine | CVE-2020-1058 | VBScript 远程代码执行漏洞 | Important |
| Microsoft Scripting Engine | CVE-2020-1060 | VBScript 远程代码执行漏洞 | Important |
