2024-11-2 06:0:12 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:14 收藏
Executive Summary
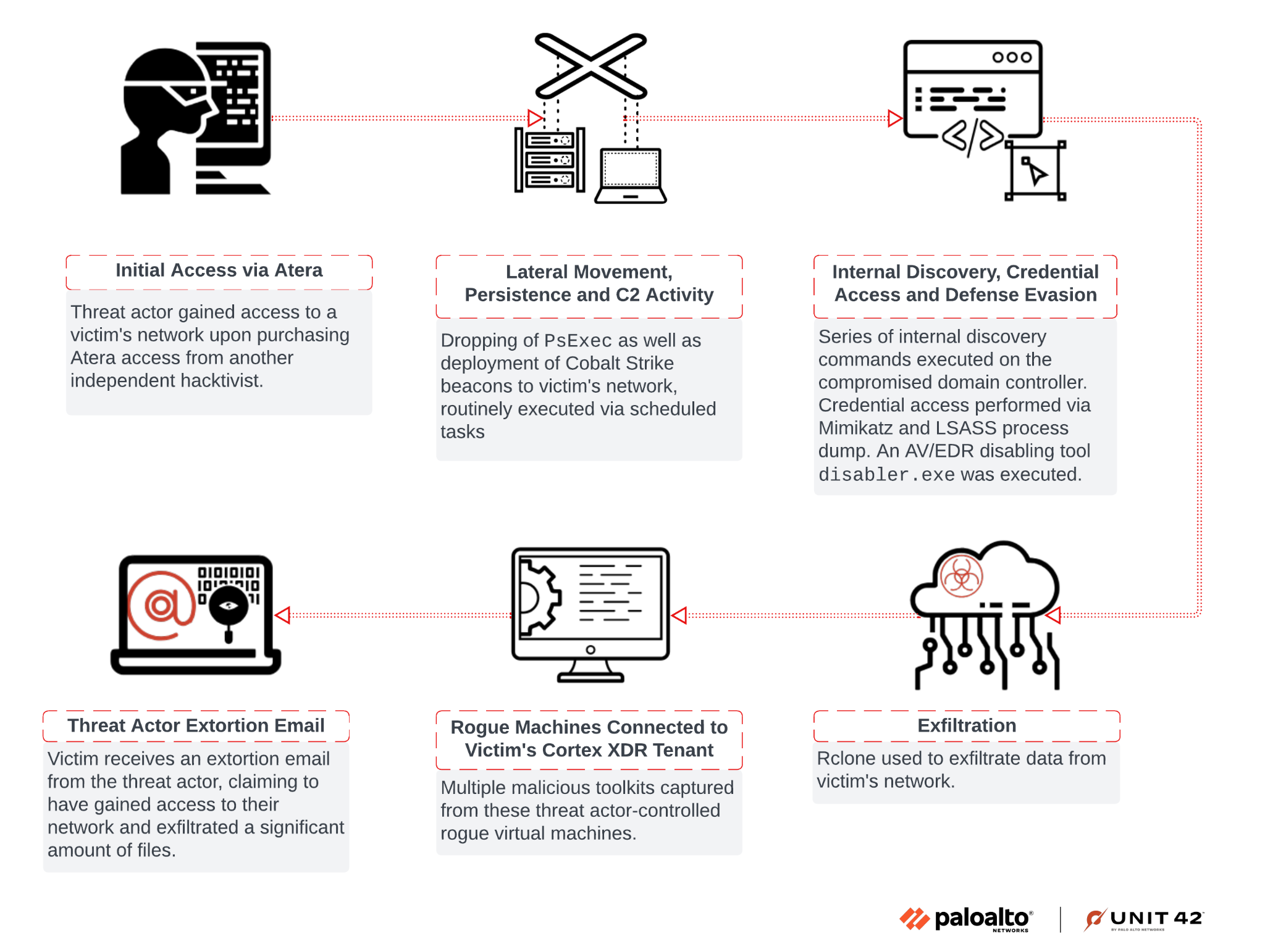
This article reviews an incident where a threat actor unsuccessfully tried bypassing Cortex XDR. By digging further into the incident, the process instead provided us with insight into the threat actor's operations.
In a recent investigation involving an extortion attempt, we discovered a threat actor had purchased access to the client network via Atera RMM from an initial access broker. We discovered the threat actor used rogue systems to install the Cortex XDR agent onto a virtual system. They did this to test a new antivirus/endpoint detection and response (AV/EDR) bypass tool leveraging the bring your own vulnerable driver (BYOVD) technique.
Connectivity between this virtual system and the client's network inadvertently gave Unit 42 investigators a certain level of access to the rogue systems. This provided visibility into various tools and files held by the threat actor. While the threat actor intended to find a way to bypass Cortex, in actuality this activity helped Unit 42 protect other organizations by providing unique visibility into the threat actor's tooling, targeting and persona.
In this report, we provide an overview of the attack that occurred, details about the AV/EDR bypass tool, and its sale on cybercrime forums. Most importantly, we offer a walkthrough for how Unit 42 researchers managed to unmask one of the threat actors involved. We’ll give a peek into all the discoveries related to the identification of the threat actor.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Extortion, Data Exfiltration |
Overview
Unit 42 was called to assist with an extortion incident. Through the investigation process, we encountered two endpoints involved in the attack that were unknown to the client environment.
As a means to test an AV/EDR bypass tool, these endpoints had older versions of Cortex XDR agents installed. Unbeknownst to the threat actor, we were able to access these rogue endpoints.
We also discovered a series of toolkits and other files belonging to the threat actor on the system, which included the bypass tool. We successfully traced and identified posts related to the sale of this specific tool on cybercrime forums like XSS and Exploit.
Using files obtained from the rogue endpoints and subsequent investigation, we discovered the true identity of one of the threat actors involved in the incident. We also found additional information about the individual's personal and professional background.
Figure 1 presents a high-level chain of events in the attack investigated by Unit 42.
AV/EDR Bypass Tool
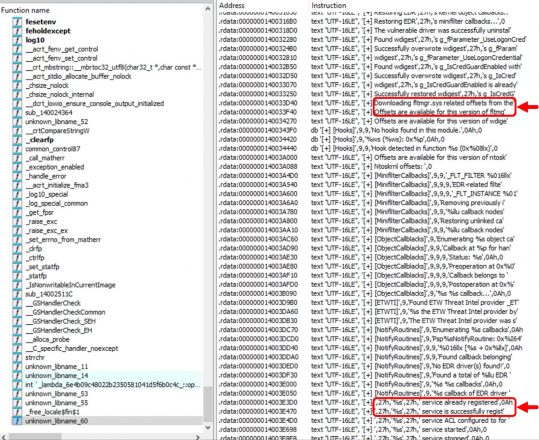
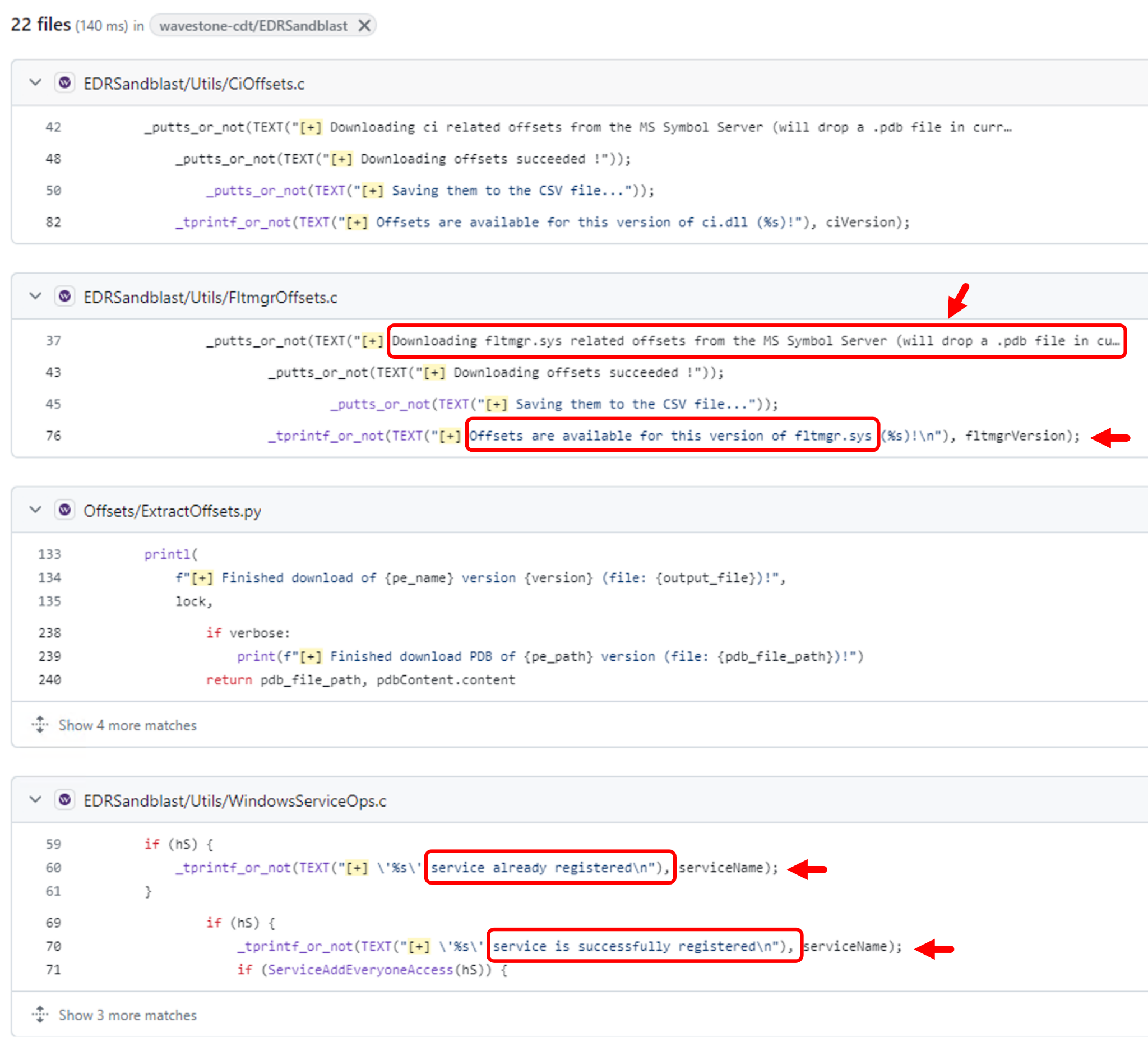
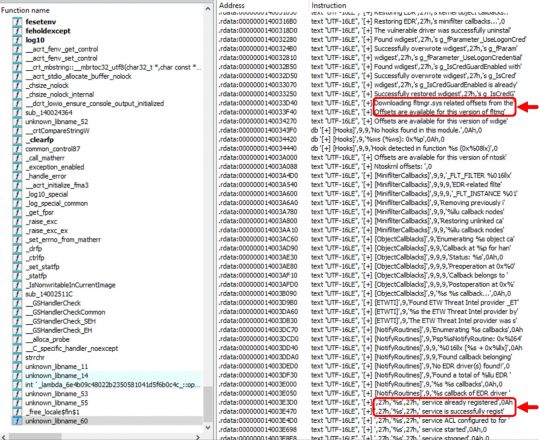
The particular tool, named disabler.exe, appears to use the publicly available source code from EDRSandBlast with small modifications and removal of the CLI features. This is evidenced by similarity in content in EDRSandBlast source code files shown in Figure 2 and referenced in the binary as shown in Figure 3. We have noted some of the similarities in red in both figures.
The tool's primary function is to target and remove EDR hooks in user-mode libraries and kernel-mode callbacks. It includes a companion file, wnbios.sys or WN_64.sys, which is a vulnerable driver that the tool attempts to load and gain access to.
Based on certain files and folders in one of the rogue endpoints, we searched cybercrime forums such as XSS and Exploit to identify the likely seller of this bypass tool.
Identifying the Seller of the Bypass Tool
The rogue system had a hostname of DESKTOP-J8AOTJS and contained several directories with interesting names under the file path Z:\freelance. This led us to the hypothesis that these were names or monikers of various other affiliates as shown below in Figure 4.
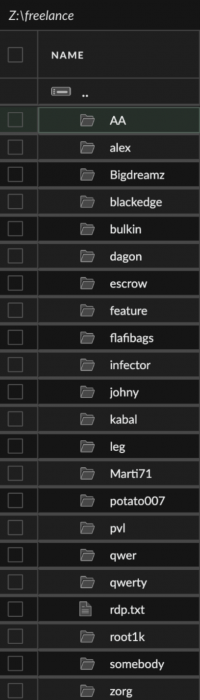
With that in mind, we searched cybercrime forums for usernames matching any of the directory names under Z:\freelance. While some of them were either too noisy or didn’t return any result at all, the rest did return some interesting hits. The matching names consistently posted either in the Russian language, or they posted in Russian-based cybercrime forums, the most common being XSS and Exploit.
The username that piqued our interest the most was Marti71. This username posted in multiple places looking for tools to bypass AV/EDR. Figure 5 shows one such example, with the post translated to English as follows:
Greetings, everyone!
Does anyone have an out-of-the-box solution to kill antivirus software? I'm ready to purchase several solutions with regular support/subscription.
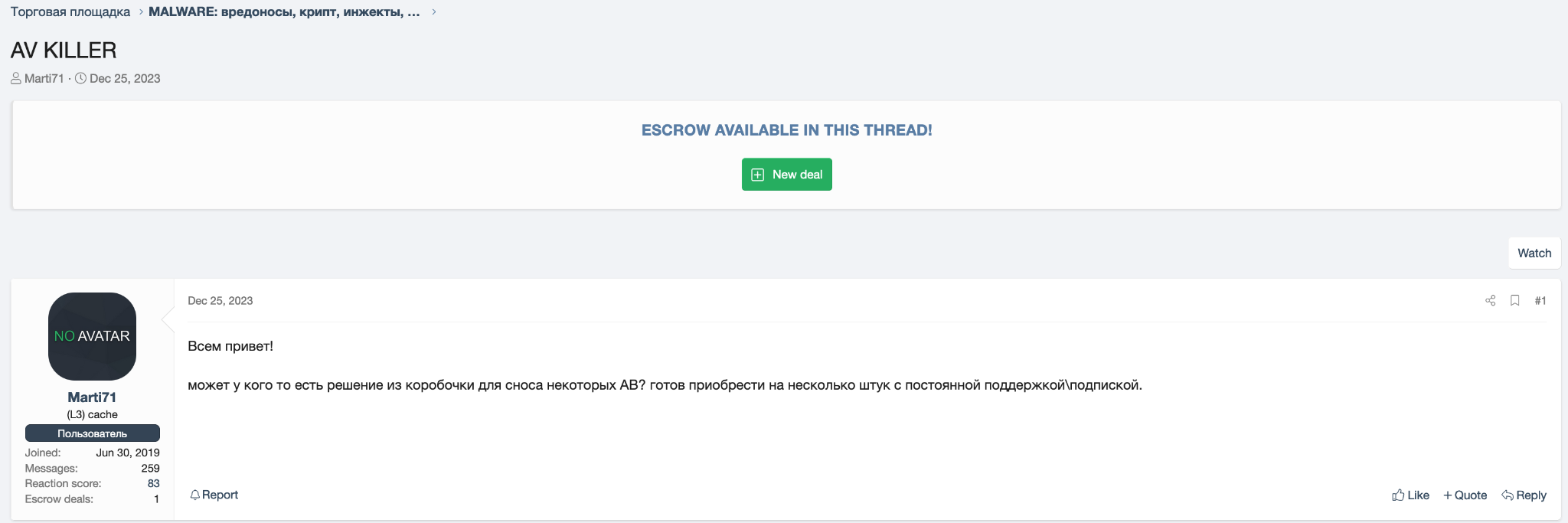
The final post on this thread was from a user account named KernelMode, suggesting an AV/EDR bypass tool.
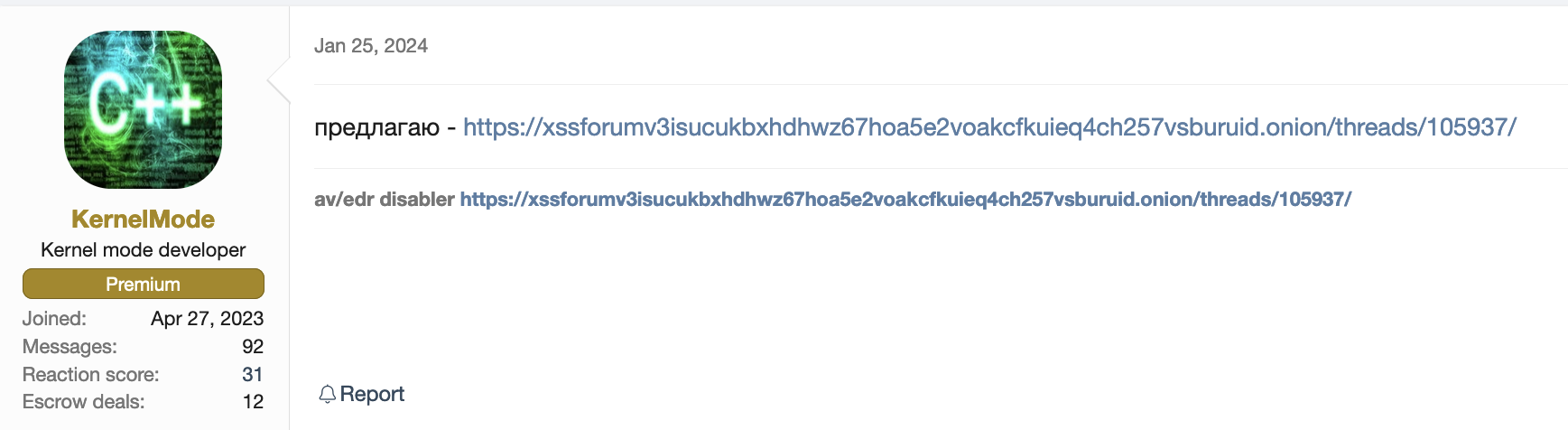
Pivoting to the link in KernelMode's post in Figure 6, we found a thread that KernelMode initiated to sell subscriptions to an AV/EDR bypass tool as Figure 7 shows. However, the post contains nothing that would confirm that the person or people behind KernelMode are the developers of this bypass tool.
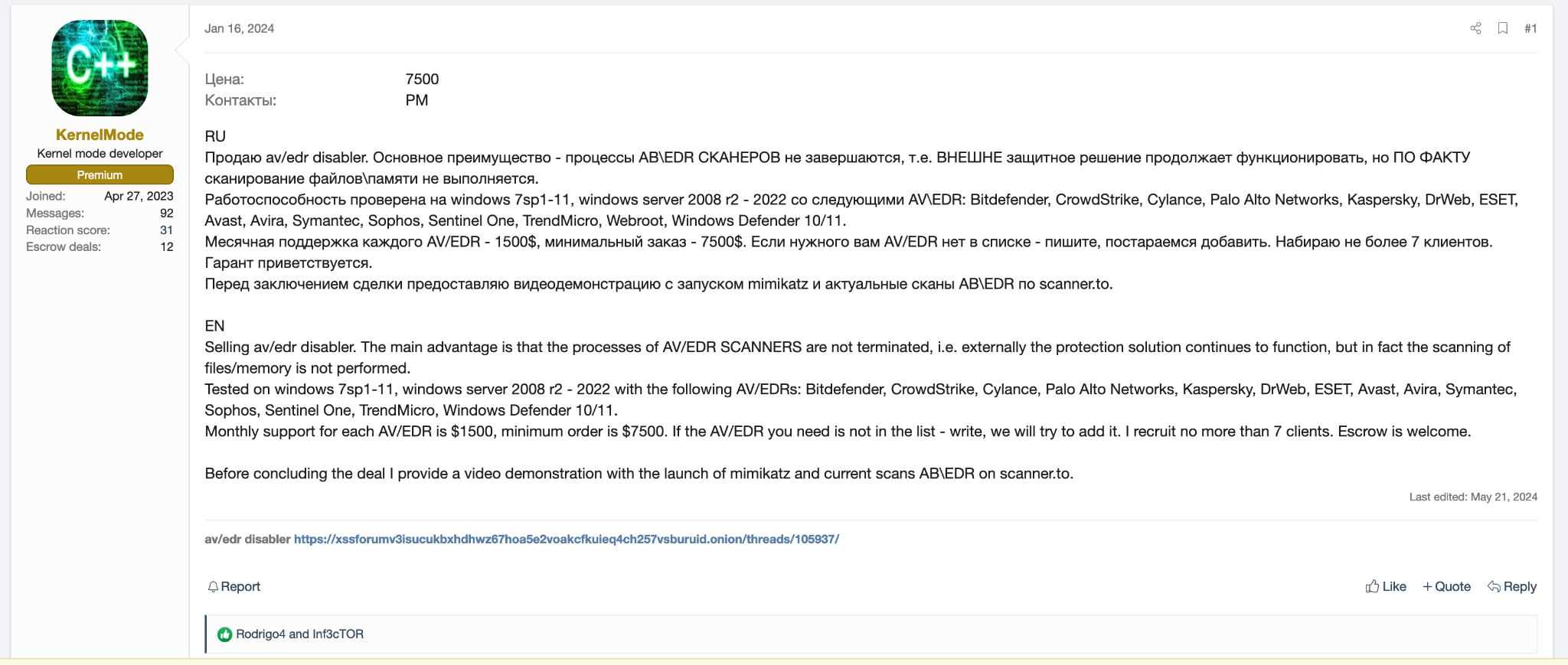
Marti71 also posted on this thread as shown in Figure 8, which seems to indicate a positive experience with the tool.
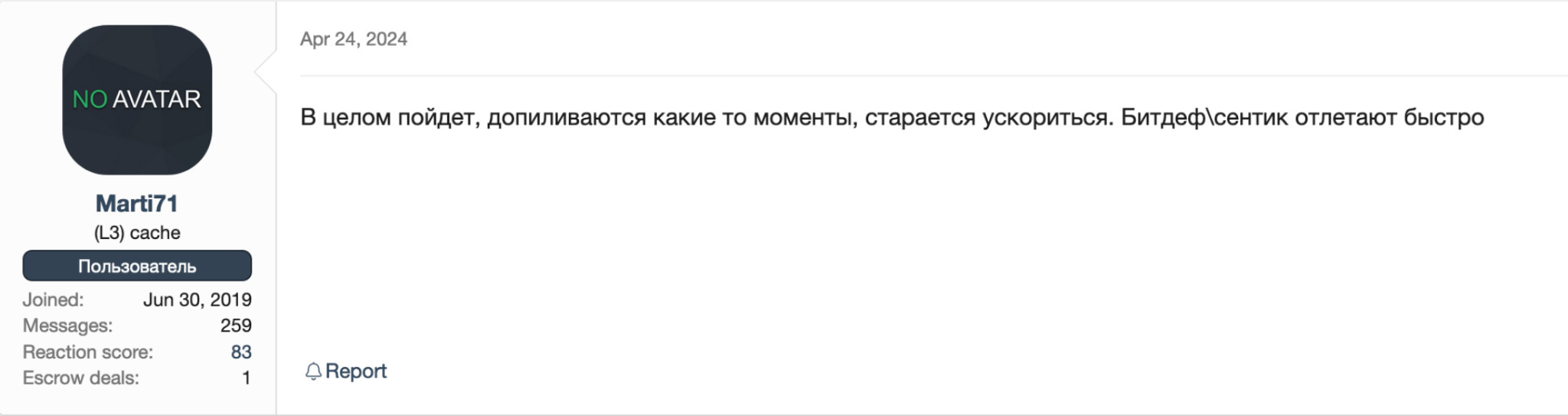
This Russian language post translates to In general, it will go, finishing some moments, trying to speed up. Bitdef/sentic fly off quickly.
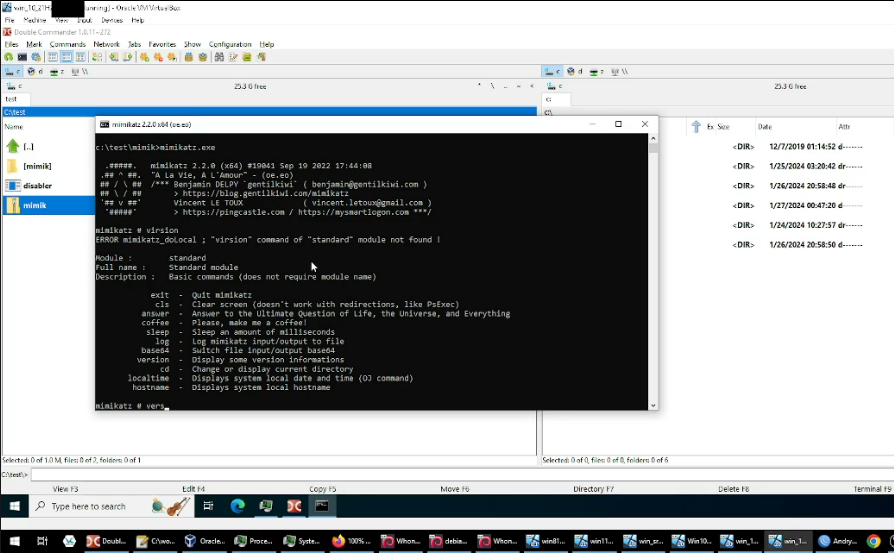
Going back to KernelMode’s post, the actor mentions at the end that they will provide a video demonstration. We were able to procure an archive of multiple recordings demonstrating the tool. Each recording shows a particular AV/EDR agent installed at that point that included the execution of the bypassing tool followed by a successful execution of Mimikatz. The intent of the demonstration is to illustrate that the AV/EDR agent has been bypassed to an extent.
We found files for such tool demonstration recordings on the rogue system as well. Comparing the recordings on the rogue system with recordings from KernelMode revealed they were exactly the same. Figure 9 shows a screenshot from one of the recordings.
Peek into the Rogue System
Overview of Tools and Files
We retrieved a portion of files in the shared Z:\ drive of the rogue system DESKTOP-J8AOTJS. Figure 10 shows some of the files captured.
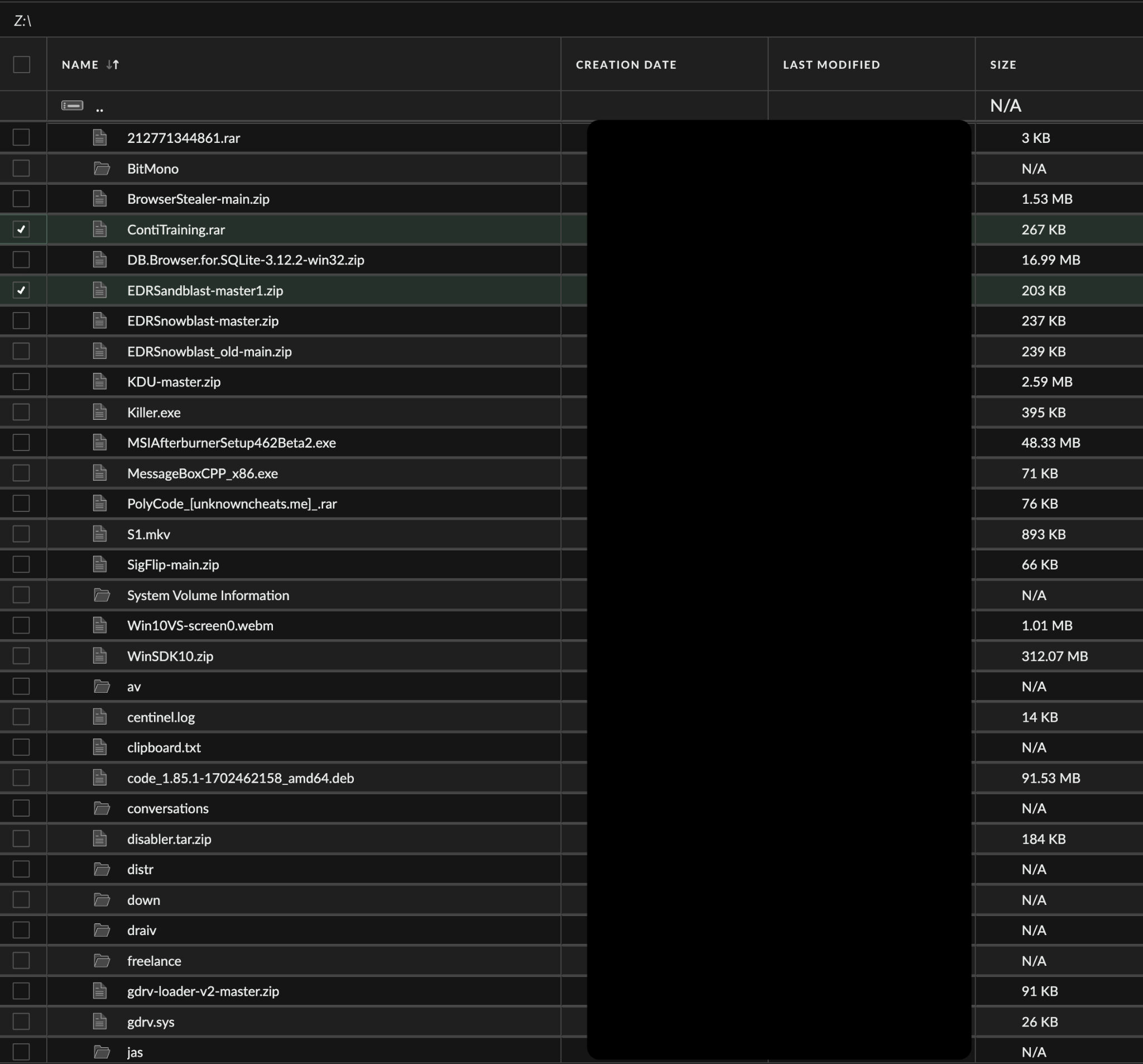
Highlights of the captured material include:
- An encrypted archive file ContiTraining.rar was present in the system
- The extracted archive contains a torrent file named ContiTraining.torrent that was created on Aug. 14, 2021
- This torrent file would reach out to the following servers to download the Conti playbook that was publicly leaked in 2021:
- udp[://]tracker.coppersurfer[.]tk:6969
- udp[://]9.rarbg[.]to:2920
- udp[://]tracker.opentrackr[.]org:1337
- udp[://]tracker.leechers-paradise[.]org:6969
- udp[://]exodus.desync[.]com:6969
- Files specified by ContiTraining.torrent to be downloaded:
- Кряк 2019.rar
- Метасплоит US.rar
- Метасплоит RU.zip
- Network Pentesting.rar
- Cobalt Strike.rar
- Powershell for Pentesters+.rar
- Windows Red Team Lab+.rar
- WMI Attacks and Defense +.rar
- Abusing SQL Server Trusts in a Windows Domain+.rar
- Attacking and Defending Active Directory+.rar
- GCB.zip
- GeekBrayns Реверс-инжиниринг.rar
- A folder with files containing personally identifiable information (PII) and other confidential information on one individual such as:
- Their name
- Device details
- Phone number
- An account number
- A two-factor authentication-based key
- Multiple copies of the AV/EDR bypass tool along with video demonstrations, as explained above
- Various builds of the Mimikatz tool, probably for the purposes of testing out the AV/EDR bypass tool
- Various tools that were either sourced from GitHub or underground forums, with functionalities such as:
- Shellcode generation and execution
- Kernel driver utilities
- Code obfuscation
- Protection bypass
- Anti-cheat bypass
- A presentation deck by a researcher from a Russian institute on compiler obfuscation
- An installer and multiple other files pertaining to an EDR product, likely used once again for testing the AV/EDR bypass tool
- A text file with escrow payment details (shown in Figure 11)
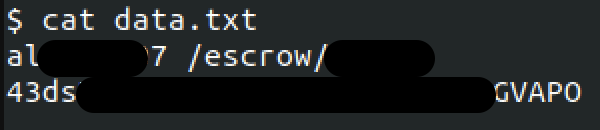
- Another text file containing a long list of host IP addresses along with their credentials
- A portion of those credentials likely corresponds to various compromised hosts.
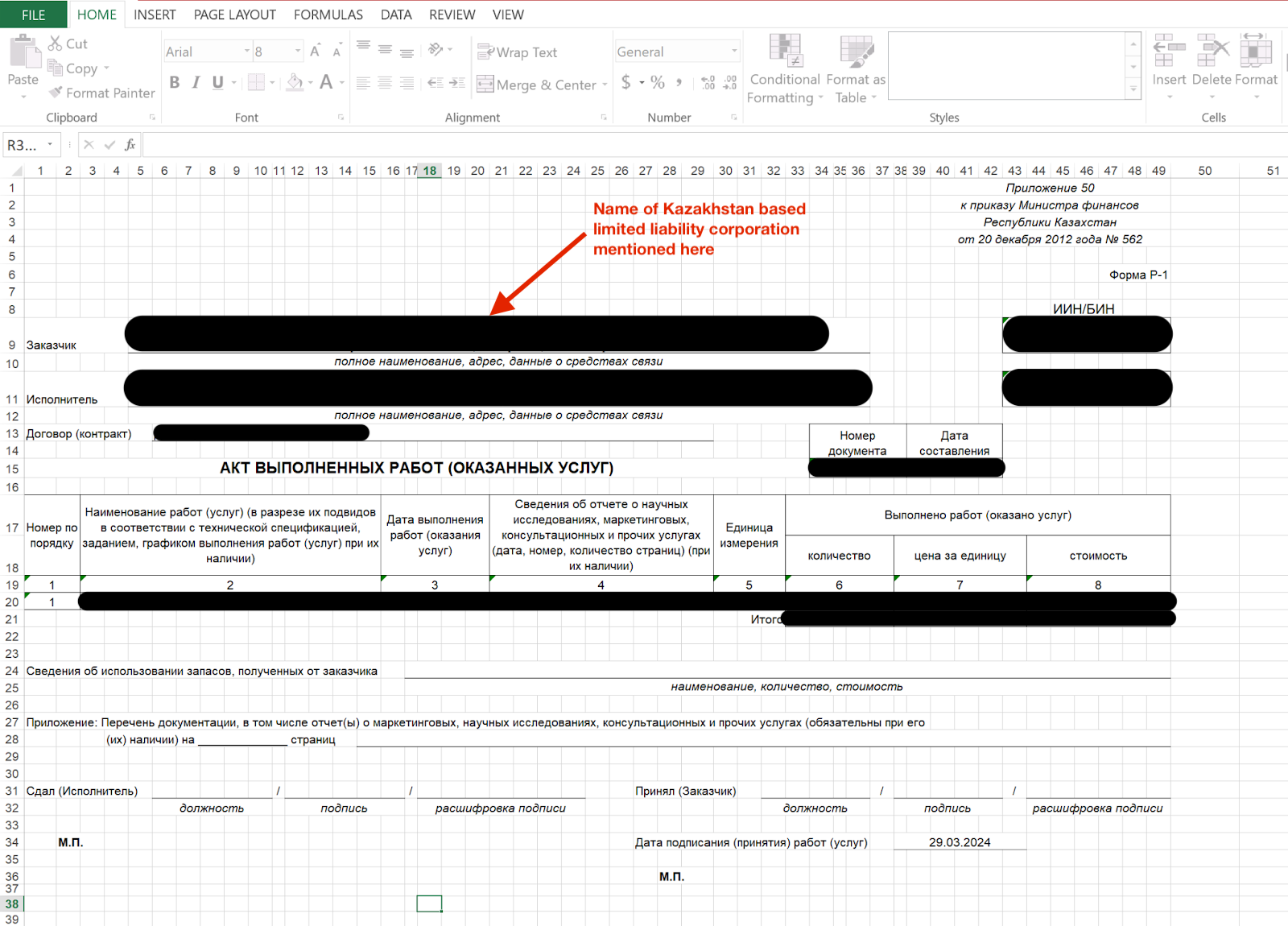
- Р-1 form expense spreadsheet
One file from the rogue system that caught our attention was Р-1 (акт выполненных работ) № <redacted> от <redacted>.xls, which translates to “act of completed work.” The spreadsheet contains a “P-1 form” for a transaction between two limited liability companies based in Kazakhstan, as shown in Figure 12.
According to a post on the government procurement site for the Republic of Kazakhstan, the P-1 form is used to document completed work, services rendered, invoices (as in this case), and other related items. The name of one of the companies exposed in this document reveals a piece of information that is vital when it comes to threat actor profiling.
Artifacts from AV/EDR Bypass Tool Recording
We previously mentioned the presence of multiple video files demonstrating the AV/EDR bypass tool against various endpoint protection products. These files are identical to the ones provided by a user account named KernelMode on various cybercrime forums.
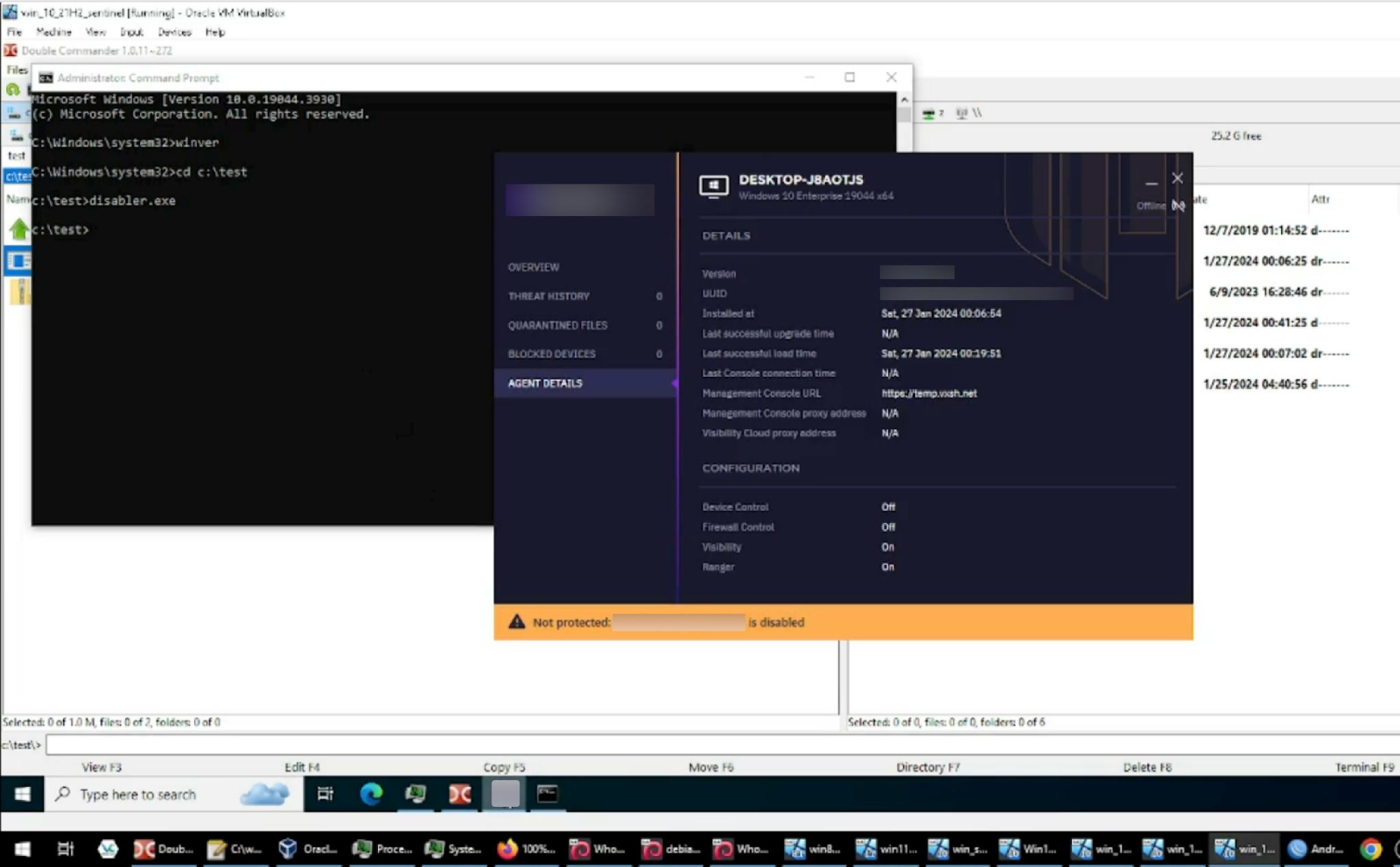
We found the video recording shown in Figure 13, and noted a few relevant details on an AV/EDR agent panel and the taskbar of the host machine.
Our observations based on the video noted in Figure 13 include:
- The AV/EDR bypass tool is being tested in a virtual machine and is accessible via Oracle VM VirtualBox. Looking at the taskbar of the host machine (as shown at the bottom of Figure 13 above), it appears that the individual recording the demonstration video is accessing multiple instances of virtual machines.
- The virtual machine hostname displayed on the AV/EDR agent panel is DESKTOP-J8AOTJS. This also happens to be the hostname of the rogue system behind the attack that we managed to capture. With this piece of information, we can confirm that the rogue system is a virtual machine.
- The management console URL on the agent panel seems rather unconventional: https[://]temp.vxsh[.]net. A quick search on this domain reveals a Telegram channel where a user shared a fake token to install the AV/EDR agent. Base64-decoding of the fake token unveils that exact URL. We cannot confirm if the agent can still be installed via this particular fake token.
- Looking at the titles of open applications in the Windows taskbar in the host machine, the first one from the right, beside the Google Chrome icon, is incomplete but appears to have a name in it showing as “Andr.”
- While going through the remaining videos, we identified the same application in the taskbar but this time, the first word “Andry” is visible in the title “Andry-ad…” as shown below in Figure 14. The icon indicates this application is likely WinBox, a utility used to remotely log into and administer Mikrotik routers. We believe that “Andry” is part of the username logged into a Mikrotik router.
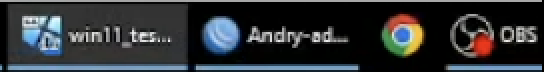
Figure 14. Snippet of Windows taskbar from one of the demonstration videos.
- As shown above in Figure 14, another application visible in the taskbar is OBS Studio, a free and open-source tool for video recording and live streaming. Threat actors often abuse, take advantage of or subvert legitimate products for malicious purposes. This does not imply that the legitimate product is flawed or malicious.
Browser History
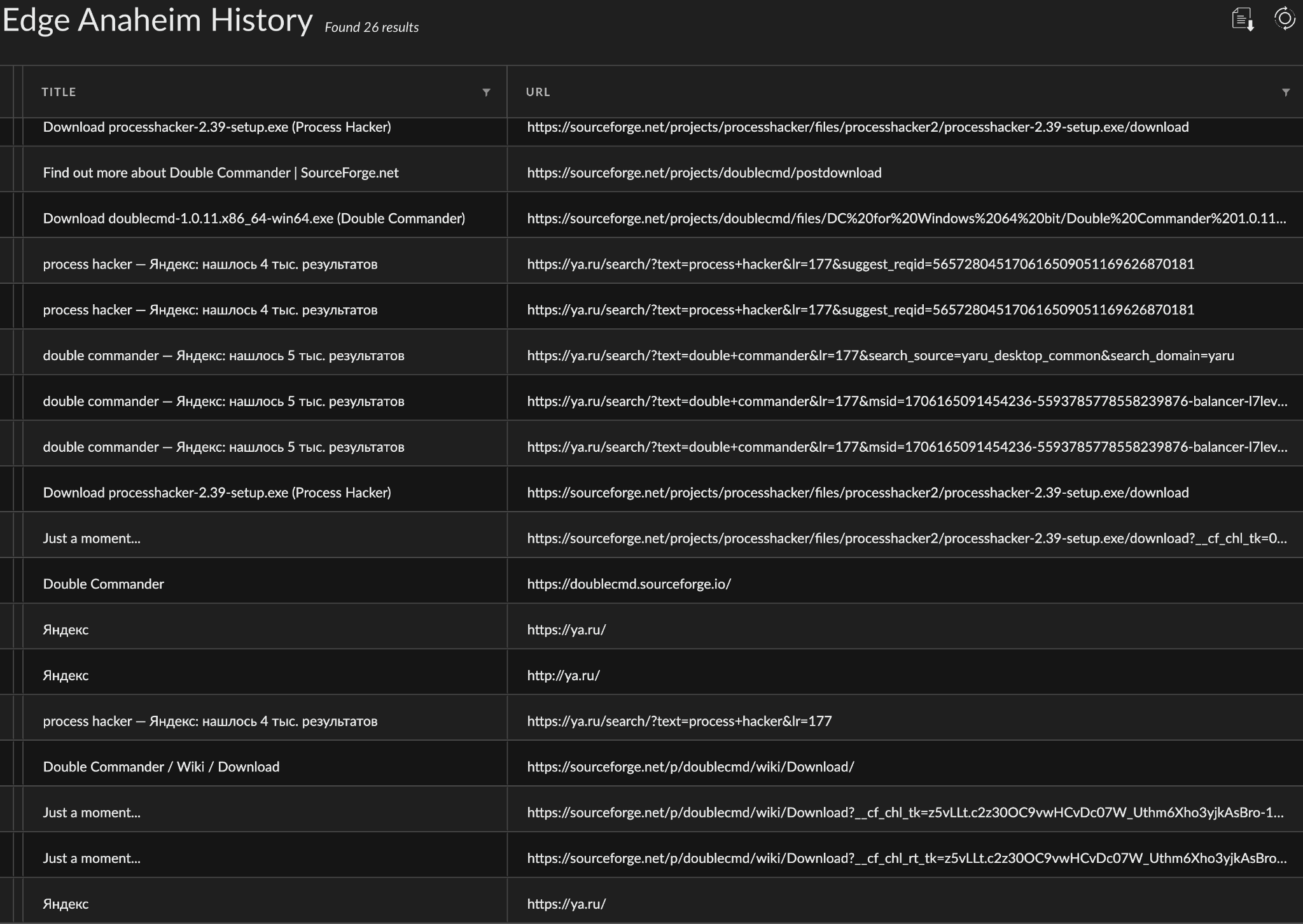
Through Cortex XDR we got a peek into Edge browser activity on DESKTOP-J8AOTJS as shown below in Figure 15. We observed the adversary's operations included visiting the following websites to search for and download certain tools such as Process Hacker and Double Commander.
- ya[.]ru: Yandex (Russian-based search engine)
- sourceforge[.]net
Additional Findings
TTP Overlaps with Conti Playbook
As noted in the previous section, the rogue system contained ContiTraining.rar, but we found no indication that the attackers downloaded material from the Conti playbook on the rogue system. However, we observed some overlaps between the Conti playbook and tactics, techniques and procedures (TTPs) captured during this incident attack chain, such as:
- Use of Atera agent to access the client network and maintain persistence
- Cobalt Strike beaconing activity
- Use of PsExec for lateral movement
- Data exfiltration using Rclone utility
Findings from Cobalt Strike Watermark
We extracted configuration data from Cobalt Strike beacons used during the attack, and the watermark ID across all the extracted configuration data was 1357776117. Threatfox has so far identified around 160 unique IPv4 and domain names associated with this particular Cobalt Strike watermark ID.
Cobalt Strike activity has frequently been noted in ransomware attacks, and a small portion of the identified Cobalt Strike IPv4 and domain names have also been associated with Dark Scorpius (aka Black Basta) ransomware. Despite the association of Cobalt Strike with ransomware, we did not observe any attempts to deploy ransomware during our investigation. We speculate this might be because the threat actor lost access to the network before attempting further actions.
Threat Actor Profiling
Files on the rogue system, like the AV/EDR bypass tool demonstration videos and the P-1 form, constitute an operational security (OpSec) failure by the threat actor that exposed information we believe helps us identify them.
We identified the LinkedIn profile of the individual whose name (“Andry”) we captured from the video. The individual is employed at the company based in Kazakhstan listed in the P-1 form. Furthermore, we found a matching profile on the Russian social networking platform VKontakte, which reveals more details about the individual.
We also gathered additional details on the organization employing this individual, including its website, legal address and registration details. According to its website, the company currently has five employees, including the individual in question. The website also provides a personal and professional description for each of its employees, providing further insight on the individual we believe to be involved in this attack.
KernelMode Connection
Revisiting some of the points we covered so far:
- The rogue system DESKTOP-J8AOTJS contained multiple recordings of an AV/EDR bypass tool being demonstrated against various EDR products
- Those exact videos were also distributed by an actor that uses the moniker KernelMode on different cybercrime forums
- The Windows taskbar exposed the name of the host machine in those recordings
- Additionally, a P-1 expense form was present on the rogue system, revealing the name of the company employing the individual
- We pivoted on this information to discover what we believe to be the true identity of the individual, along with personal and professional details
With these points in mind, we assess with moderate confidence that the individual in question is one of the people, if not the only person, behind KernelMode. Moreover, based on the individual’s background and relevant information we gathered, this individual is likely one of the developers, if not the only developer, of the AV/EDR bypass tool.
However, we cannot ascertain if this particular individual is the owner of the rogue virtual machine DESKTOP-J8AOTJS, and by extension, the person behind this whole attack. This is primarily due to the following reasons:
- The rogue individual is definitely one of the active users of DESKTOP-J8AOTJS, but access to this virtual machine could have been shared across multiple individuals. There isn’t concrete evidence to suggest otherwise.
- There is no indication of DESKTOP-J8AOTJS being involved in the attack, except for the purposes of AV/EDR bypass.
Conclusion
Recently, there has been a growing trend in the use of AV/EDR bypass tools, extending beyond the incident discussed here. These tools will likely continue to evolve in their attempts to exploit various security platforms.
Ongoing monitoring of underground forums provides valuable insights into the latest developments and techniques of these tools. Threat actors and developers monetize such platforms on a subscription basis, regularly releasing updates as part of their affiliate payment plans.
This incident allowed us to expose a rogue system and, by extension, the toolkit and files owned by the threat actor. Using all the information gathered, Unit 42 unveiled what we believe to be the true identity of one of the threat actors and assessed their involvement in this incident.
Organizations should consider blocking the indicators of compromise provided in this report, as they are associated with the arsenal observed in the incident, as well as the toolkit present in the rogue system. More broadly, we recommend reviewing your security tool policies and configurations to ensure that agent tampering protection is enabled, preventing malicious activities targeting the endpoint protection agents on your systems.
Palo Alto Networks Protection and Mitigation
For Palo Alto Networks customers, our products and services provide the following coverage associated with this group:
- Advanced WildFire cloud-delivered malware analysis service accurately identifies the known samples as malicious.
- Advanced URL Filtering and Advanced DNS Security identify known URLs and domains associated with this activity as malicious.
- Cortex XDR and XSIAM detect and prevent all samples mentioned in this article.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Host Based
SHA256 hash:
- 3758c5eb1fbab2362ef23091f082710606c1b4ebaeaff9b514896dc2a1e2ab17
- File name: disabler.exe
- File description: AV/EDR bypass tool based on EDRSandBlast
SHA256 hash:
- 1228fd70d7ce0f31f7e7c98520e66a01935e428be561ce0d25140ba33598f688
- File name: 0bffbb8.exe
- File description: Cobalt Strike beacon
SHA256 hash:
- 6106d1ce671b92d522144fcd3bc01276a975fe5d5b0fde09ca1cca16d09b7143
- File name: WNBIOS.sys
- File description: Vulnerable driver loaded by disabler.exe
SHA256 hash:
- 6106d1ce671b92d522144fcd3bc01276a975fe5d5b0fde09ca1cca16d09b7143
- File name: WN_64.sys
- File description: Vulnerable driver loaded by disabler.exe
SHA256 hash:
- 14364f1969b83cf4ec2c0e293c6b4d8f750932f6cbf9a8f32173400de33469fd
- File name: abased.dll
- File description: Cobalt Strike beacon
SHA256 hash:
- 264a29a703682456ebe9f679a0e7d18291af84ef4b53a669c2555061e4972394
- File name: vm32.dll
- File description: Cobalt Strike beacon
SHA256 hash:
- 61c0810a23580cf492a6ba4f7654566108331e7a4134c968c2d6a05261b2d8a1
- File name: mimikatz.exe
- File description: Mimikatz credential access tool
SHA256 hash:
- 8d36705a5b7f6179fdef2d600276f9c0cc6cb3b0a670c11d66baaaea6bd2c8ad
- File name: mimik.zip
- File description: Archive that contains mimikatz.exe
SHA256 hash:
- 41f32a3d67b3f983c82070e067a121dd5b8fae2804c97e684acc7f599ba308da
- File name: safetykatz.exe
- File description: SafetyKatz, modified version of Mimikatz
SHA256 hash:
- 6e37a054bd7c49b233cace747951911f320bd43be8a79ce455b97403c2f7de2c
- File name: mmk.exe
- File description: Mimikatz credential access tool
SHA256 hash:
- aa97acd5628c1f7a16cb98e7b9ce7228119759133f1649b1d5ed849a1a98448b
- File name: http_test_180424.exe
- File description: Cobalt Strike beacon
SHA256 hash:
- 97f2676c6d1e16264584ce4c1f1e8790598ba2a85ae08e3d6e394669240b9908
- File name: v1.dll
- File description: Cobalt Strike beacon
SHA256 hash:
- 0112e3b20872760dda5f658f6b546c85f126e803e27f0577b294f335ffa5a298
- File name: vmware.exe
- File description: Renamed Rclone binary
SHA256 hash:
- 7c8559134a49c8d8739b66a549f10b22d4fd16afaff51976562f995b2bcd01a9
- File name: 5bb646d.exe
- File description: Cobalt Strike beacon
SHA256 hash:
- 1228fd70d7ce0f31f7e7c98520e66a01935e428be561ce0d25140ba33598f688
- File name: 0bffbb8.exe
- File description: Cobalt Strike beacon
SHA256 hash:
- 22f52c9e66330642e836aaf1b6573dd7452e76e0f0b5e6ac594a0278689e1d8f
- File name: socksnet.exe
- File description: SOCKS5 proxy
SHA256 hash:
- 49d01f2e32808e24dc8129d3c1ebe444f71792ddec2efabee354335fc6d6f64c
- File name: Rubeus.exe
- File description: Rebeus, a toolkit for Kerberos interaction and abuse
SHA256 hash:
- 71dfb3f52df040644221f8c59215f83eb516186b6f82dbbb2c16bf3c22e4baf6
- File name: SharpRDP.exe
- File description: Tool used for remote desktop connection
SHA256 hash:
- d0c1662ce239e4d288048c0e3324ec52962f6ddda77da0cb7af9c1d9c2f1e2eb
- File name: Advanced_Port_Scanner_2.5.3869.exe
- File description: Advanced port scanner
SHA256 hash:
- 8b9c7d2554fe315199fae656448dc193accbec162d4afff3f204ce2346507a8a
- File name: advanced_port_scanner.exe
- File description: Advanced port scanner
SHA256 hash:
- f1c45cbbd98619e197154085a05fd972283af6788343aa04492e35798a06e2b7
- File name: sh.exe
- File description: SharpHound tool
Network Based
| IP address or Domain | Description |
| 94.75.225[.]81 | External IP address of rogue system DESKTOP-J8AOTJS |
| 82.192.88[.]95 | External IP address of FTP server used by Rclone. Linux machine with OpenSSH 8.4p1 Debian 5 |
| 89.251.22[.]32 | IP address of server hosting Cobalt Strike payload |
| 180.131.145[.]85 | IP address of Cobalt Strike C2 server |
| beamofthemoon[.]com
mail.beamofthemoon[.]com store.beamofthemoon[.]com |
Domains used by Cobalt Strike C2 server |
Appendix
Incident Attack Lifecycle
| MITRE Tactic | Description |
|---|---|
| Initial access (TA0001) | Access to the client network via Atera RMM purchased from an initial access broker. |
| Persistence (TA0003) | Creation of scheduled tasks to routinely execute Cobalt Strike beacons. |
| Defense Evasion (TA0005) | AV/EDR bypass tool called disabler.exe. It uses the static library from EDRSandBlast, a hack tool designed to unhook EDR hooks in both user-mode libraries and kernel-mode. |
| Credential Access (TA0006) | The threat actor leveraged Mimikatz and executed PowerShell to obtain lsass.exe process dump. |
| Discovery (TA0007) | A series of internal discovery commands on a compromised domain controller using built-in tools such as nltest, net, dsquery and rundll32. |
| Lateral Movement (TA0008) | The threat actor used Windows RDP and PsExec to move laterally between systems in the victim environment. |
| Exfiltration (TA0010) | Attackers used Rclone to exfiltrate data from the victim environment to a Secure File Transfer Protocol (SFTP) server. |
| Command and Control (TA0011) | Cobalt Strike Beacon activity on multiple systems. |
如有侵权请联系:admin#unsafe.sh