2024-11-7 20:20:30 Author: cyble.com(查看原文) 阅读量:11 收藏
Resurfaced BRATA Malware Masquerading As Security Application
Cyble Research Labs (CRL) came across a Twitter post wherein a security researcher mentioned an Android Banking Trojan malware “AMEXTROLL” was being advertised on underground cybercrime forums.
Through our DarkWeb intelligence, CRL found posts made by Threat Actors (TAs) on a cybercrime forum mentioning the AMEXTROLL Android Banking Trojan.
In the post, the TAs claim that their Android malware is encrypted, obfuscated, and persistent with powerful features, the Beta version is available for rent at $3.5k/month, and the test APK is on sale for $300.

AMEXTROLL, also known as BRATA, was first identified in late June 2021, being distributed through different smishing and phishing campaigns targeting Italian banks. Their last attack was identified in April 2022, when the Threat Actors (TAs) changed the malware’s source code to attack specific banking institutions.
The AMEXTROLL malware was also observed being distributed through the below phishing sites:
- “hxxps://infoapp[.]pro/bancobpm[.]apk“
- “hxxps://youapp-conto[.]digital“.
Technical Analysis
APK Metadata Information
- App Name: A Shield Auth
- Package Name: app.opened.upo
- SHA256 Hash: 3c62b24594ec3cacc14bdca068a0277e855967210e92c2c17bcf7c7d0d6b782a
Figure 2 shows the metadata information of the application.

The malicious application pretends to be a security application that provides antispam protection to appear genuine to potential victims.
Manifest Description
The malware requests 27 different permissions from the user, of which it abuses at least 7. These dangerous permissions are listed below:
| Permission | Description |
| READ_EXTERNAL_STORAGE | Allows an application to read from external storage. |
| WRITE_EXTERNAL_STORAGE | Allows an application to write to external storage. |
| READ_SMS | Allows an application to receive SMS messages. |
| SYSTEM_ALERT_WINDOW | Allows an app to create windows on top of app other apps. |
| CALL_PHONE | Allows an application to initiate a phone call without going through the Dialer user interface for the user to confirm the call. |
| READ_CALL_LOG | Allows an application to read the user’s call log. |
| REQUEST_INSTALL_PACKAGES | Allows an application to request installing packages. |
Source Code Review
The application is packed, as most of the components present in the manifest file are missing except for its subclass.

The malicious application unpacks the DEX file present in the assets folder and then loads the classes upon execution. In this case, the dropped dex file name is “XZ2Hvm0dsFgFqwpZtA4n2qFV3VYTnV1V.dex,” which includes all the missing classes.
The AMEXTROLL malware provides the below functionalities:
After installing the malware, the user is prompted to enable the Accessibility Service. Once the user grants this permission, the malware starts abusing the Accessibility Service feature to carry out malicious activities.

The malware uses Virtual Network Computing (VNC) to capture the victim device’s screen to monitor the targeted applications to steal credentials. The screenshot below shows the image of the control panel posted on a cybercrime forum that clearly illustrates how TAs use VNC to monitor the user’s activity in real-time.

The malware executes the code shown in the below image to record the victim’s device screen using VNC.

The malware uses the code shown in the below snippet to collect the victim’s SMS data based on a command received from the Control and Command (C&C) server. TAs can use this stolen SMS data to perform several malicious activities such as stealing contact details, bypassing two-factor authentication, etc.

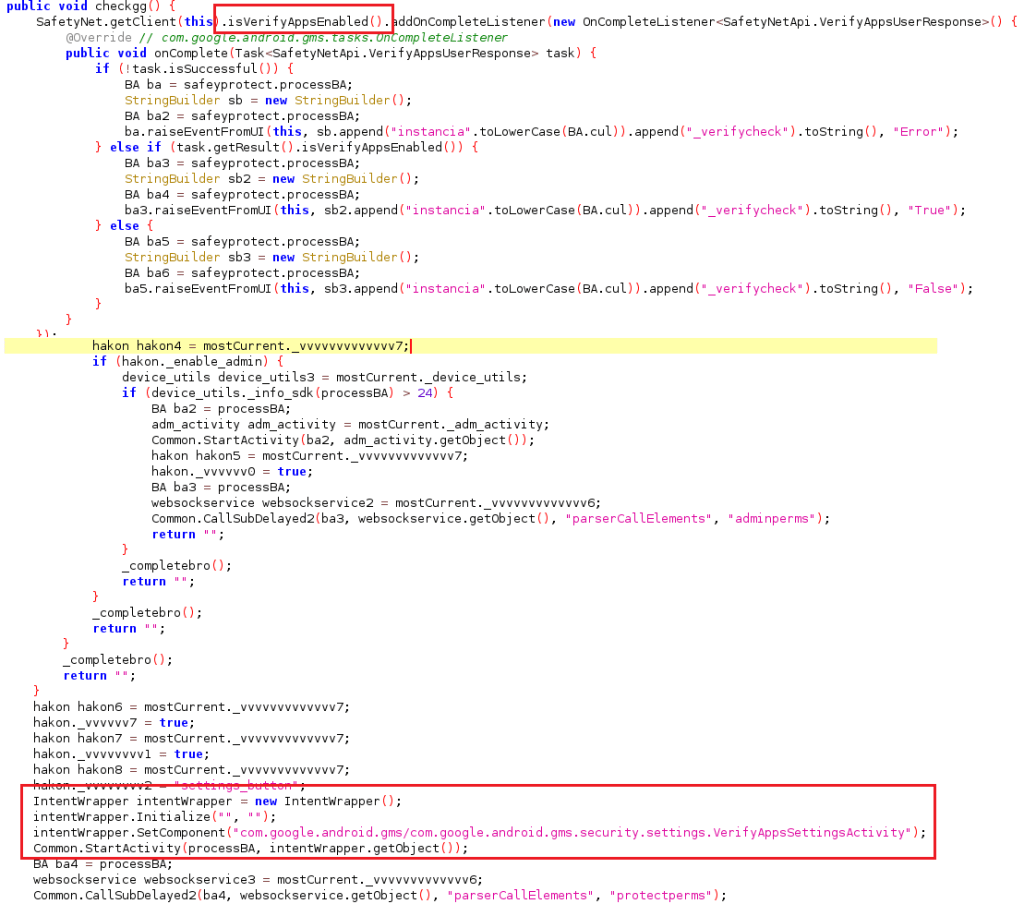
The malware also disables Google Play Protect – built-in protection to bypass malware detection to continue its malicious activities without any interference.

The malware collects installed application information from the victim’s device and downloads the HTML injection page for the targeted applications.
Whenever the user interacts with the targeted application, it will create an overlay to steal any credentials entered by the victim.

Upon receiving a command from the C&C server, the malware removes any anti-virus applications’ installed on the victim’s device and responds with the acknowledgment “protections_removed” after successfully completing the task.

The malware uses USSD (Unstructured Supplementary Service Data) service calls to perform money transfers. To transfer money using USSD, no dialer user interface or internet access is required on the victim’s device.

The commands used by AMEXTROLL to execute it’s malicious operations are:
| Command | Description |
| byebye_format | Formats infected device |
| mute_device | Mute infected device |
| lightScreen | Controls screen brightness |
| sendPushNotify | Sends notifications |
| deletePackageInjected | Deletes injected app |
| get_sms | Collects all incoming SMSM |
| vncSizeQuality | Controls VNC screen size quality |
| vncQuality | Controls VNC quality |
| stop_screen | Stops VNC screen recording |
| getScreen | Collects screen captured by VNC module |
| del_application | Deletes the application received from the C&C server |
| intent_admin | Sent admin intent to start device admin |
| intent_protect | Check and disable Play Protect |
| open_a11y | Opens Accessibility Service screen |
| open_over | Shows screen to grant overlay permission |
| palavra | Collects clipboard data |
| go_home | Takes the user to the home screen |
| go_recent | Takes the user to a recent screen |
| go_back | Takes the user to the back screen |
| get_application | Collects installed application package name |
| del_overlay | Delete overlay file stored on the infected device |
| openApp | Starts the application received from the C&C server |
| killCalls | Ends the call on the infected device |
| run_tel | Runs USSD to perform money transfer |
Conclusion
Banking threats have been rising for some time now and are growing increasingly sophisticated with every new malware variant. AMEXTROLL is one example of such a threat. The malware can perform financial fraud by misusing the victim’s stolen sensitive data.
The BETA version of AMEXTROLL malware is still under development. We foresee that the TA behind the AMEXTROLL will continue to develop new variants of this malware with more targeted applications, new TTPs, and delivery methods.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
How to prevent malware infection?
- Download and install software only from official app stores like Google Play Store or the iOS App Store.
- Use a reputed anti-virus and internet security software package on your connected devices, such as PCs, laptops, and mobile devices.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Enable biometric security features such as fingerprint or facial recognition for unlocking the mobile device where possible.
- Be wary of opening any links received via SMS or emails delivered to your phone.
- Ensure that Google Play Protect is enabled on Android devices.
- Be careful while enabling any permissions.
- Keep your devices, operating systems, and applications updated.
How to identify whether you are infected?
- Regularly check the Mobile/Wi-Fi data usage of applications installed on mobile devices.
- Keep an eye on the alerts provided by Anti-viruses and Android OS and take necessary actions accordingly.
What to do when you are infected?
- Disable Wi-Fi/Mobile data and remove SIM card – as in some cases, the malware can re-enable the Mobile Data.
- Perform a factory reset.
- Remove the application in case a factory reset is not possible.
- Take a backup of personal media Files (excluding mobile applications) and perform a device reset.
What to do in case of any fraudulent transaction?
- In case of a fraudulent transaction, immediately report it to the concerned bank.
What should banks do to protect their customers?
- Banks and other financial entities should educate customers on safeguarding themselves from malware attacks via telephone, SMS, or emails.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access | T1476 | Deliver Malicious App via Other Mean. |
| Initial Access | T1444 | Masquerade as Legitimate Application |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Collection | T1412 | Capture SMS Messages |
| Input Capture | T1417 | Input capture |
| Exfiltration | T1567 | Exfiltration over web services |
| Collection | T1436 | Commonly used ports |
| Impact | T1447 | Delete device data |
| Credential Access | T1414 | Capture clipboard data |
Indicators of Compromise (IOCs):
| Indicators | Indicator Type | Description |
| 45553e3fe188ff71cc343b8a6737196a47cb088503cbc010384c212e1e094418 | SHA256 | Hash of the analyzed APK file |
| 83cf270597ae6b8e88089d340459b6bcbb2c7c9e | SHA1 | Hash of the analyzed APK file |
| 04af65f411817e1f4b267c948f7c4bbc | MD5 | Hash of the analyzed APK file |
| b66260ad4d147efd54e5e52955b2a251e0c13c4e3a01e1ba1c24745181073988 | SHA256 | Hash of the analyzed APK file |
| 72a5c35893019a7ad80546ab10390c3840a01c5b | SHA1 | Hash of the analyzed APK file |
| 31a91ec8d33b85ebb43d269e1e521926 | MD5 | Hash of the analyzed APK file |
| ac230a51c49d651e6bb95903b04c989d7ae8456658d917e4da2d39c3a3a36979 | SHA256 | Hash of the analyzed APK file |
| 200731a47d14b744b87577d3bcbcd1fec52d55f3 | SHA1 | Hash of the analyzed APK file |
| 901bc9b3fd27e4b80a874dfe2f901584 | MD5 | Hash of the analyzed APK file |
| hxxp://152[.]89[.]247[.]159 | URL | C&C server |
| hxxps://infoapp[.]pro | URL | Malware distribution site |
Related
如有侵权请联系:admin#unsafe.sh