2024-11-12 16:0:0 Author: msrc.microsoft.com(查看原文) 阅读量:0 收藏
Welcome to the third installment in our series on transparency at the Microsoft Security Response Center (MSRC). In this ongoing discussion, we talk about our commitment to providing comprehensive vulnerability information to our customers.
At MSRC, our mission is to protect our customers, communities, and Microsoft, from current and emerging threats to security and privacy. In our previous blog post, we announced new Cloud Service CVEs to increase transparency, even when customers do not need to manually implement a mitigation. Today, we are adding a new standard machine-readable format called Common Security Advisory Framework (CSAF) to all Microsoft CVE information to help customer accelerate CVE response and remediation.
CSAF files are meant to be consumed by computers more so than by humans, so we are adding CSAF files as an addition to our existing CVE data channels rather than a replacement. Customers can still consume Microsoft’s CVEs via the Security Update Guide or our API based on the Common Vulnerability Reporting Framework (CVRF), which has been the historic standard for providing vulnerability data. They can also subscribe to receive notifications regarding the latest updates or changes to CVE information via email or our RSS feed.
A quick nerdy background on CSAF and related things: CSAF is managed and maintained by Oasis. It supersedes CVRF, which Microsoft has been using to publish CVE information since 2004. CVRF was managed by ICASI and adopted by First.org in 2021. RFC 9116, published by IETF, talks about a security.txt file. This text file, published and maintained by companies around the world, describes how to find security information about that company. Here is the link to the security.txt file for Microsoft. This file informs the public on where we store our CSAF files.
Security.txt file
# Our security acknowledgements page
Acknowledgments: https://msrc.microsoft.com/update-guide/acknowledgement
# Canonical URI
Canonical: https://www.microsoft.com/.well-known/security.txt
# Our Researcher Portal
Contact: https://msrc.microsoft.com/report/vulnerability/new
# Our email address
Contact: mailto:[email protected]
# Our PGP Key
Encryption: https://www.microsoft.com/en-us/msrc/pgp-key-msrc
Expires: 2025-10-10T16:00:00.000Z
# Our Bounty policy
Policy: https://www.microsoft.com/en-us/msrc/bounty/
# Our Coordinated Vulnerability Disclosure Policy
Policy: https://www.microsoft.com/en-us/msrc/cvd
# Our Bounty Legal Safe Harbor Policy
Policy: https://www.microsoft.com/en-us/msrc/bounty-safe-harbor
# Our Common Security Advisory Framework (CSAF) publications
CSAF: https://msrc.microsoft.com/csaf/provider-metadata.json
Preferred-Languages: en
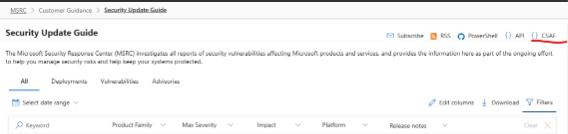
We’ve also added a link to the CSAF directory from the Security Update Guide:
This is the beginning of a journey to continue to increase transparency around our supply chain and the vulnerabilities that we address and resolve in our entire supply chain, including Open Source Software embedded in our products. We are working side by side with other companies in our industry because in many ways, we build products together, and it will take all of us together to meet the needs of our interconnected world.
As always, we look forward to your feedback, which you can provide by clicking on the rating banner at the bottom of every CVE page in the Security Update Guide.
Lisa Olson, Principal Program Manager, Security Release
如有侵权请联系:admin#unsafe.sh