2024-11-12 23:0:0 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
User access reviews are periodic evaluations of access rights to ensure they align with users’ roles, reducing security risks and helping maintain regulatory compliance. The main goal of user access reviews is to prevent unauthorized access to sensitive information, systems, or resources by regularly verifying and adjusting user permissions.
When and where are UARs needed, and what are the key objectives for UAR? How do you implement an effective UAR program? We’ll answer these questions in this article, along with providing a step-by-step guide for you to follow to implement UAR. Then, we’ll take a look at how Hyperproof can help streamline your UAR processes.
Who needs user access reviews?
User access reviews are critical in ensuring access to sensitive systems and data is properly managed in an organization. In highly regulated sectors like fintech and healthcare, user access reviews help organizations meet compliance requirements like ISO 27001 and HIPAA. By regularly conducting user access reviews, compliance heroes help prevent unauthorized access to financial systems and protect their organizations from potential data breaches.
User access reviews are vital for preventing insider threats within large enterprises and government agencies. As employees change roles or leave the organization, user access reviews ensure that access rights are promptly adjusted, minimizing the risk of unauthorized access to sensitive data.
For example, during mergers and acquisitions, user access reviews are crucial in determining access across newly formed entities. This ensures that only appropriate personnel have access to critical information.
The rise of cloud services and remote work has also made user access reviews increasingly important. In cloud and SaaS environments, they help manage access to applications and data. This means that only authorized users can access these resources. Additionally, with more employees working remotely, user access reviews are essential for securing corporate data and preventing unauthorized access from various locations and devices.
Industries like energy, manufacturing, defense, and R&D also rely heavily on user access reviews to protect critical infrastructure and sensitive information. In these high-security environments, regular access reviews help prevent disruptions, safety incidents, and unauthorized disclosures. User access reviews are not only a compliance measure, but also a strategic tool for managing risk, safeguarding valuable assets, and ensuring that access controls remain aligned with an organization’s security and operational needs.
Key objectives of user access reviews:
The primary objectives of user access reviews include:
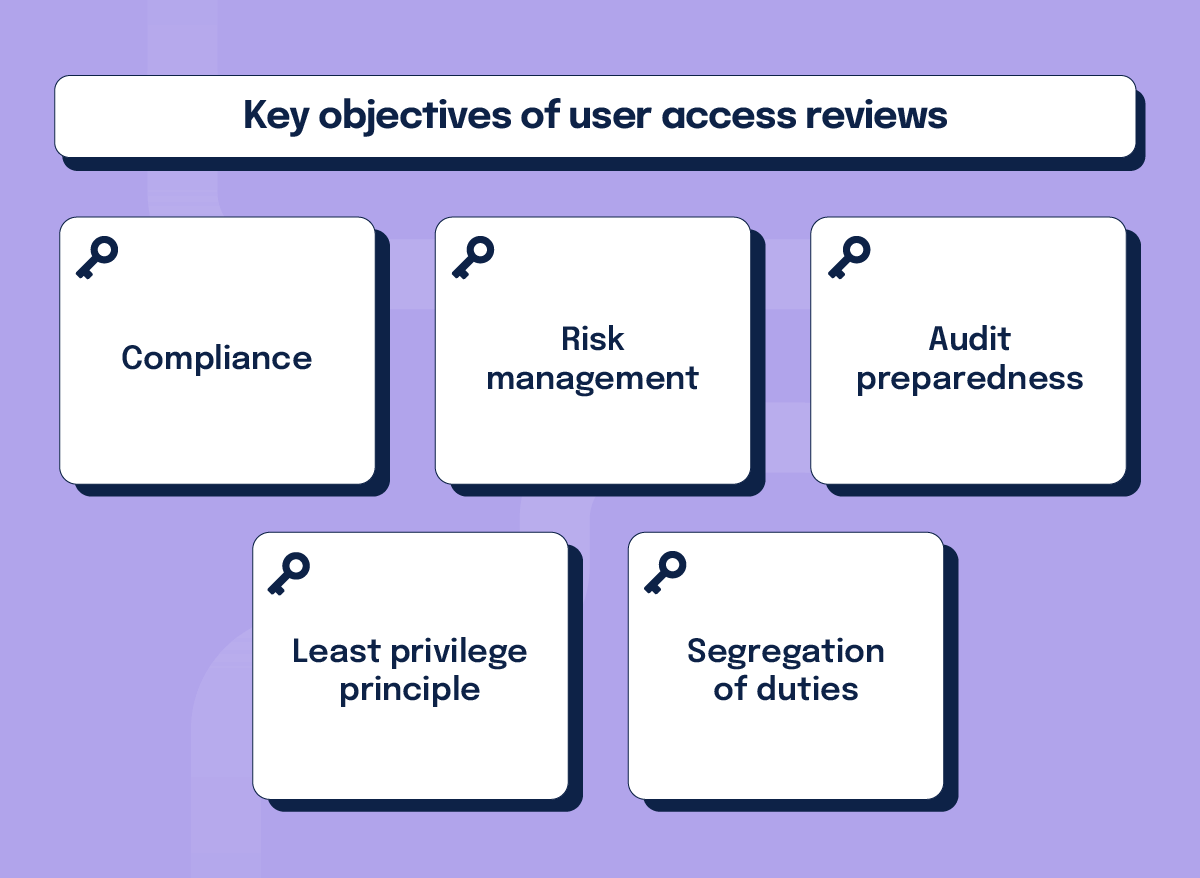
- Compliance: User access reviews are often mandated by regulations like GDPR, PCI DSS, and HIPAA, which require organizations to ensure that access to sensitive data is restricted to authorized personnel only.
- Risk management: Regular reviews help to identify and mitigate risks associated with excessive or unnecessary access, which could lead to data breaches or data misuse.
- Audit preparedness: User access reviews help organizations maintain detailed records of who has access to what, which is crucial during audits.
- Least privilege principle: User access reviews support the enforcement of the principle of least privilege, where users are granted the minimum access necessary to perform their job functions.
- Segregation of duties (SoD): User access reviews help ensure that no single individual has control over all aspects of a critical process, which could lead to conflicts of interest or fraud.
12 steps that establish an effective user access review program
Creating an effective user access review (UAR) program is essential for organizations aiming to enhance their security posture, ensure compliance, and mitigate risks associated with unauthorized access. Here’s how you can establish and maintain a robust UAR program:
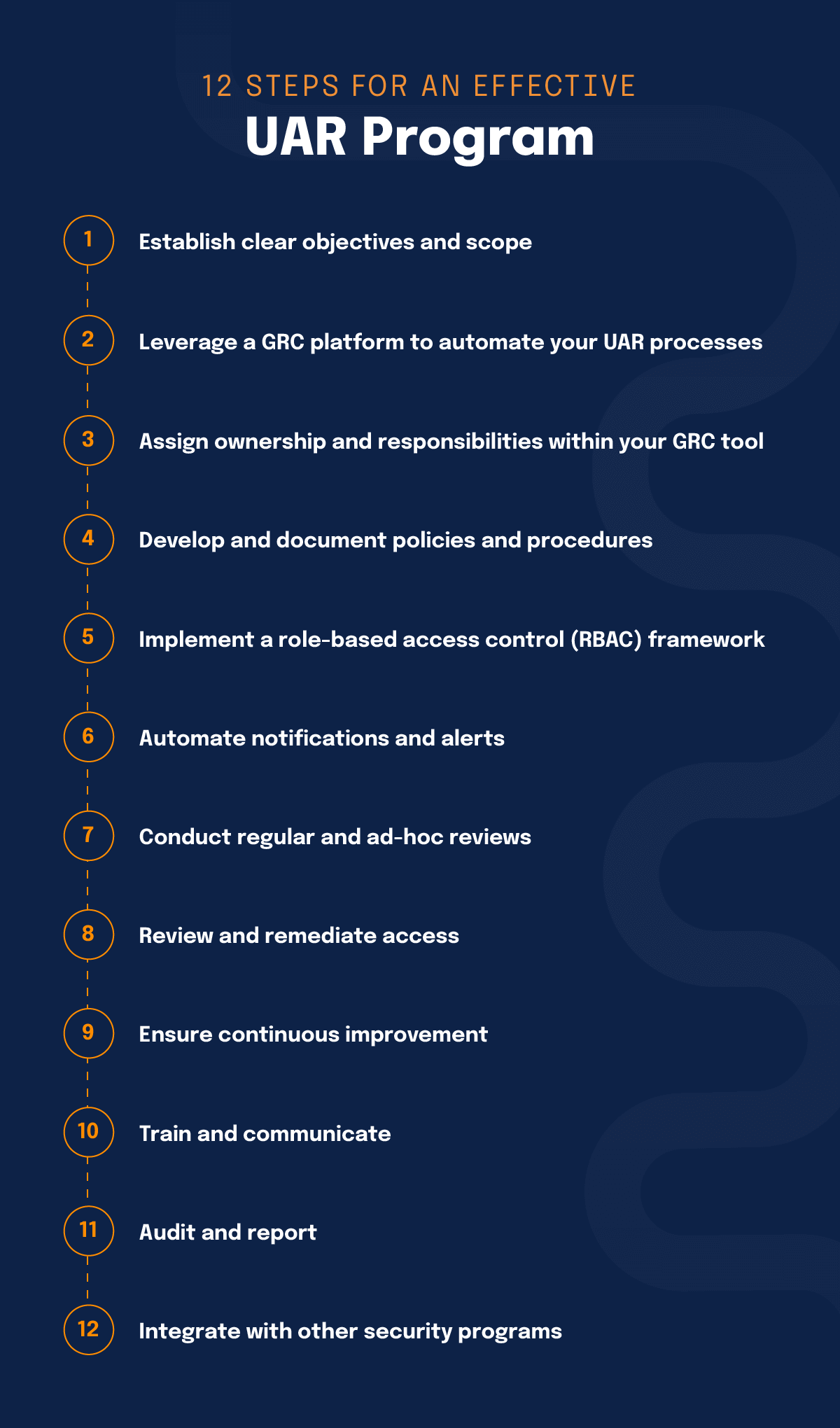
1. Establish clear objectives and scope
- Define objectives: Start by defining the goals of your UAR program. These may include ensuring compliance with regulatory requirements, reducing the risk of data breaches, and enforcing the principle of least privilege.
- Determine scope: Identify which systems, applications, and data repositories will be included in your UAR program. Consider including critical systems like ERP, CRM, and financial systems, as well as those containing sensitive data (e.g., customer data, financial records, intellectual property).
2. Leverage a GRC platform to automate your UAR processes
- Leverage GRC platforms: Access a governance and identity management platform that streamlines the review process, centralizes your work, and facilitates reporting. GRC platforms improve your security and free up valuable team resources to focus on high-impact work.
3. Assign ownership and responsibilities within your GRC tool
- Designate a program owner: Appoint a senior leader, such as your Chief Information Security Officer (CISO) or Compliance Officer, to oversee your UAR program. This person will be responsible for policy development, program execution, and reporting.
- Involve stakeholders: Identify key stakeholders, including IT, HR, Compliance, and department managers, and define their roles in the UAR process. For instance, IT may handle technical execution, while managers review their team members’ access rights.
4. Develop and document policies and procedures
- Create a UAR policy: Develop a formal UAR policy that outlines the purpose, scope, frequency, and procedures for conducting reviews. This policy should be approved by senior management and communicated to all relevant stakeholders.
- Standardize review procedures: Define standardized procedures for conducting user access reviews. This should include steps for identifying access rights, reviewing them, taking corrective actions, and documenting the process.
5. Implement a role-based access control (RBAC) framework
- Define roles and permissions: Implement an RBAC framework, where roles are clearly defined based on job functions. Assign permissions to roles (rather than individuals) to simplify the UAR process. For example, a “Finance Officer” role might include access to financial reporting tools, accounting systems, and payroll applications.
- Map users to roles: Ensure all users are mapped to appropriate roles. For example, an employee working in the finance department would be assigned the “Finance Officer” role, automatically granting them the necessary access permissions. This mapping should be regularly reviewed and updated as users change roles or responsibilities within the organization.
6. Automate notifications and alerts
- Automate notifications and alerts: Set up automated notifications to remind reviewers of upcoming reviews and alert them to any anomalies or access rights that require immediate attention.
7. Conduct regular and ad-hoc reviews
- Schedule regular reviews: Conduct UARs on a regular basis, such as quarterly or annually, depending on the organization’s risk profile and regulatory requirements.
- Perform ad-hoc reviews: In addition to scheduled reviews, conduct ad-hoc UARs in response to specific events, such as a data breach, significant organizational changes, or the introduction of new systems.
8. Review and remediate access
- Managerial review: Department managers or designated reviewers should assess whether each user’s access is appropriate for their current role. This includes verifying that access aligns with the principle of least privilege.
- Remediation process: If inappropriate access is identified, take corrective action immediately. This could involve revoking or adjusting permissions, terminating orphaned accounts (accounts of former employees), or reassigning roles.
- Document findings: Document all findings, actions taken, and justifications during the review. This documentation is crucial for audits and ensuring compliance.
9. Ensure continuous improvement
- Review program effectiveness: Periodically assess the effectiveness of the UAR program. This could involve evaluating metrics such as the number of access violations identified, time taken to remediate issues, and audit findings.
- Incorporate feedback: Gather feedback from stakeholders involved in the UAR process and use it to refine policies, procedures, and tools. Continuous improvement is key to maintaining an effective UAR program.
- Stay updated with regulations: Keep abreast of changes in regulatory requirements and industry best practices to ensure the UAR program remains compliant and effective.
10. Train and communicate
- Educate stakeholders: Provide training to managers, IT staff, and other stakeholders involved in the UAR process. Ensure they understand the importance of the program, their responsibilities, and how to use any tools involved.
- Communicate regularly: Regularly communicate the results of UARs, lessons learned, and any changes to policies or procedures to all relevant parties. Transparency and communication help reinforce the importance of access management.
11. Audit and report
- Internal audits: Conduct regular internal audits of the UAR program to ensure compliance with the established policies and procedures. Audits can identify gaps or weaknesses in the process.
- Reporting to management: Provide regular reports to senior management on the outcomes of UARs, including any risks identified, actions taken, and overall program effectiveness. These reports should help in decision-making and risk management.
12. Integrate with other security programs
- Link with IAM: Ensure that the UAR program is integrated with the organization’s Identity and Access Management (IAM) strategy. This integration helps align user access reviews with broader identity governance initiatives.
- Collaboration with incident response: Collaborate with the incident response team to ensure that any access-related incidents are addressed promptly and that lessons learned are fed back into the UAR program.
How Hyperproof can help streamline user access reviews
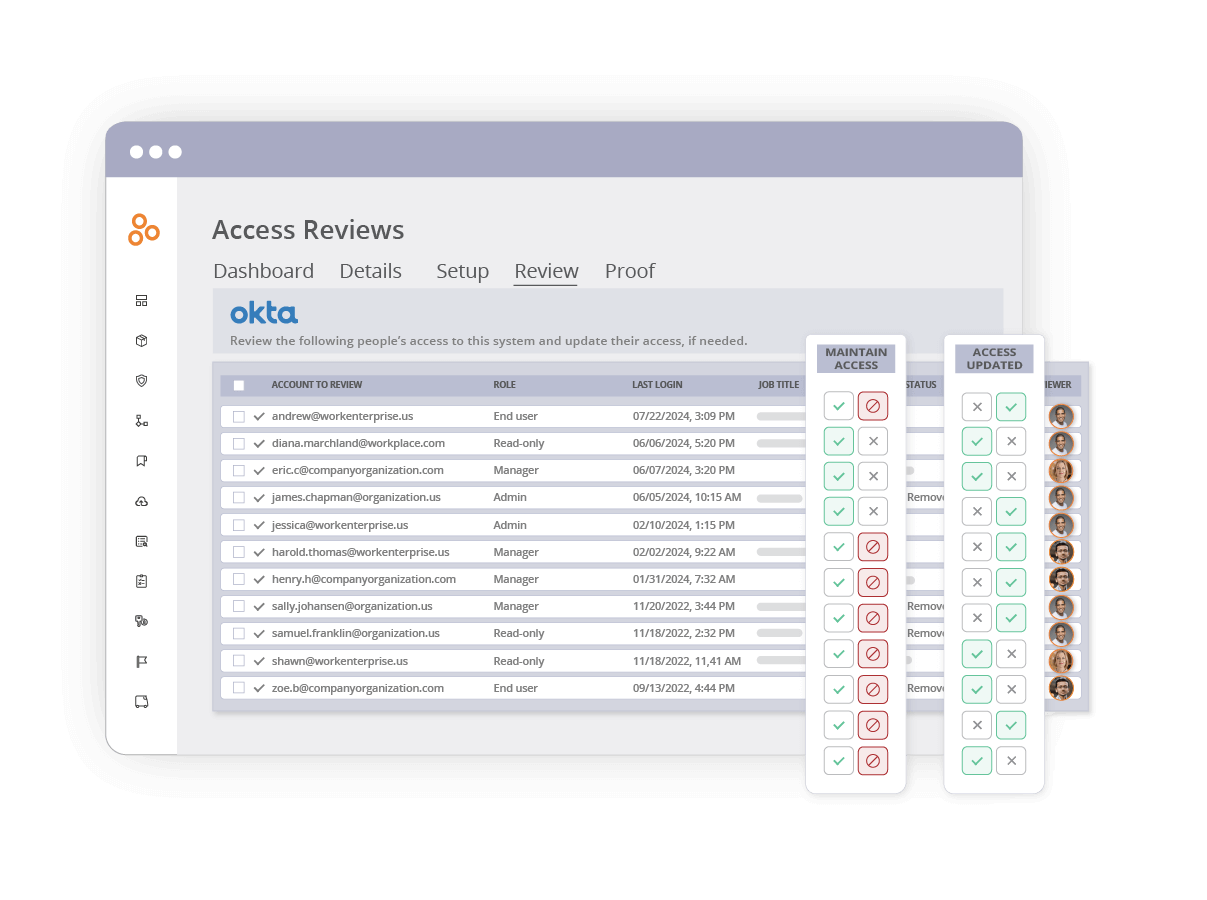
- Seamless integrations: Audit application access in a single place, consolidating user access information across thousands of enterprise apps. Connect effortlessly with HRIS systems and leading platforms like Okta, AWS, Azure, Google, and more to pull user access information into one unified platform.
- Real-time insights: Stay on top of access reviews with real-time status updates and quickly identify areas needing immediate attention.
- Intuitive user experience: Review, adjust, and verify access quickly. Our easy-to-use interface reduces training time, allowing your teams to conduct efficient access reviews and focus on high-impact work.
- Audit readiness: Simplify your audit preparations by linking your access reviews to controls, along with robust reporting that ensures transparency and compliance.
How user access reviews work in Hyperproof
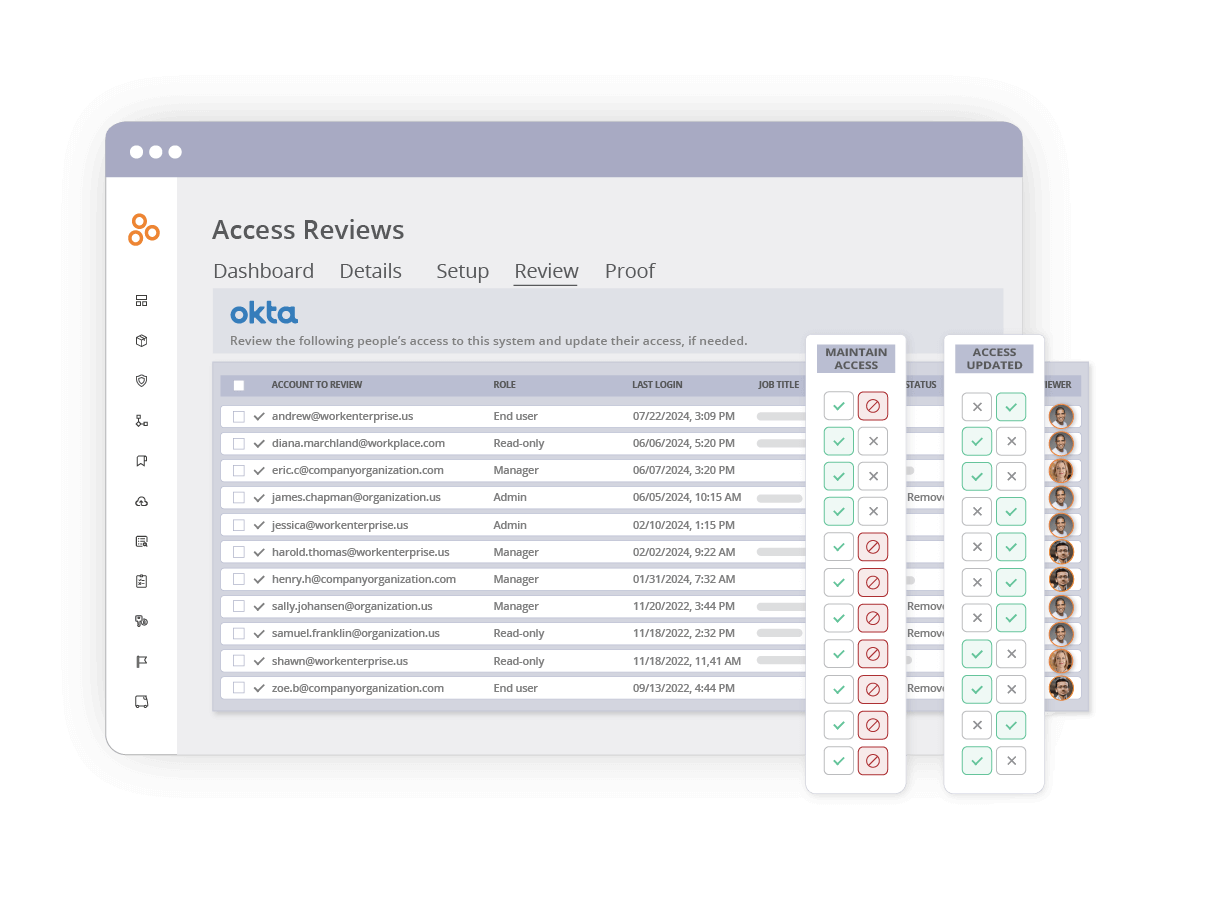
Setting up and executing user access reviews in Hyperproof is simple:
1. Import a people directory from your HRIS or IAM provider into Hyperproof using a Hypersync.
Hypersyncs bring organizational information, including employee names, emails, departments, job titles, statuses (active vs. terminated), managers and managers’ emails into the platform.
2. Select the application(s) you’d like to review by setting up a Hypersync.
Hyperproof imports records of users with access to that app, automatically matches these records to the employees in the directory, and appends information like job titles and statuses to each record.
3. Next, assign each person the role of either Reviewer or Sysadmin.
You can delegate a set of records to review to colleagues outside the security/compliance team.
4. Launch a campaign (workflow) to notify reviewers.
Each Reviewer will receive an email that invites them to complete their review in Hyperproof. The Reviewer can only see the items assigned to them and can verify whether each user’s access level should be maintained or changed. If a user’s access level should be changed, the Reviewer can make a change request to the Sysadmin in Hyperproof.
The Sysadmin can see all change requests, make the changes if necessary in the source application, and then use Hyperproof to attest that the changes have been made.
5. Track the completion of access review time.
Once an access review campaign is marked complete, Hyperproof will automatically generate a report that captures the workflow for the reviewed accounts, making demonstrating compliance easy. A compliance manager can even link each access review campaign to controls to make compliance reporting easier.
Stay ahead of potential threats, meet compliance requirements, and free up your teams to focus on more strategic tasks. If you’re looking to modernize your access review process please reach out to our team or request a demo for more information.
Stay one step ahead with Hyperproof’s User Access Review module
An effective user access review program is not just a checkbox but a critical part of an organization’s overall security and risk management strategy. By following the steps outlined above, you can meet regulatory requirements and protect sensitive data and systems from unauthorized access.
Hyperproof offers a comprehensive and scalable solution for managing user access reviews, making it easier for organizations to stay compliant, reduce risks, and maintain control over user access. By leveraging Hyperproof’s User Access Reviews module, you can streamline your UAR processes to stay ahead of your compliance and security demands and get real-time visibility to avoid delays that can leave your systems vulnerable.
To get started, request a demo today.
The post Creating an Effective User Access Review Program in 12 Simple Steps appeared first on Hyperproof.
*** This is a Security Bloggers Network syndicated blog from Hyperproof authored by Erin Nelson. Read the original post at: https://hyperproof.io/resource/effective-user-access-review-program/
如有侵权请联系:admin#unsafe.sh

