October 2024 heralded a new chapter in supply chain security challenges, characterized by innovative attack techniques and cryptocurrency-focused threats. A groundbreaking entry point exploitation technique affecting multiple package ecosystems was unveiled, while the NPM ecosystem witnessed the first-ever use of Ethereum smart contracts for malware C2 infrastructure. The month also saw multiple sophisticated attacks on cryptocurrency wallets through PyPI packages and a notable compromise of the popular lottie-player package, despite 2FA protections, highlighting the increasing complexity of supply chain security threats.
Let’s delve into some of the most striking events of October:
This New Supply Chain Attack Technique Can Trojanize All Your CLI Commands
A new supply chain attack technique exploits entry points in various programming ecosystems, allowing attackers to trojanize CLI commands. This stealthy method poses risks to developers and enterprises, bypassing traditional security checks. (Link to report).
With 2FA Enabled: NPM Package lottie-player Taken Over by Attackers
NPM package lottie-player compromised via leaked automation token, bypassing 2FA. Malicious versions injected code to trick users into connecting crypto wallets. Swift response: safe version released, compromised versions unpublished. (Link to report).
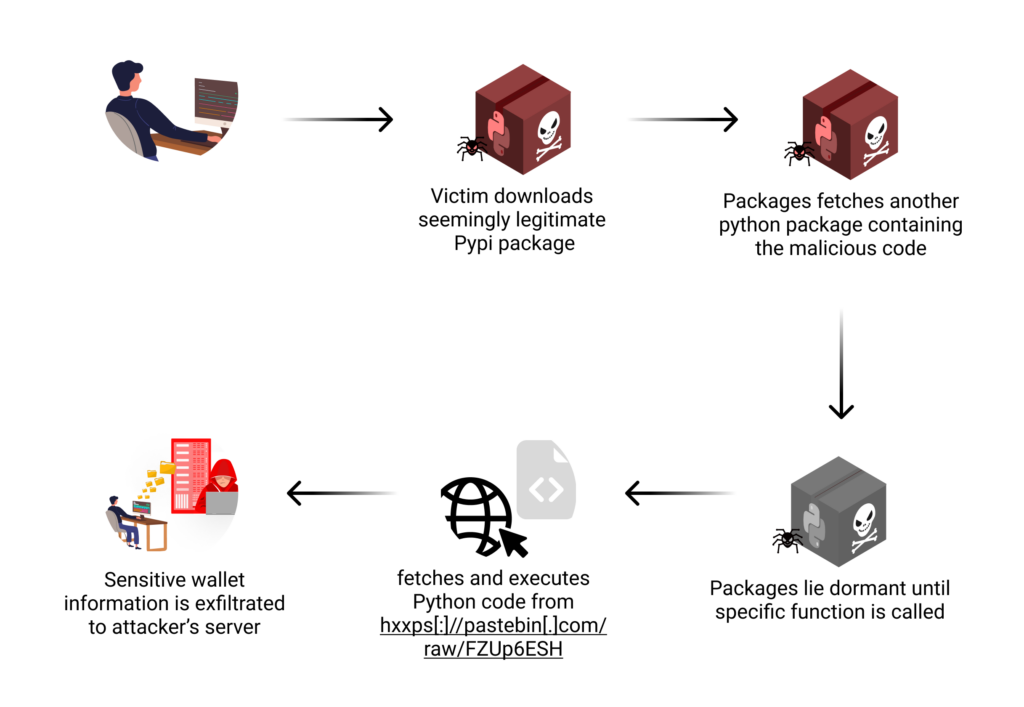
Crypto-Stealing Code Lurking in Python Package Dependencies
A sophisticated cyber attack on PyPI targeted cryptocurrency wallets through malicious packages. The attack used deceptive strategies, distributed malicious code across dependencies, and only activated when specific functions were called, making detection challenging. (Link to report).
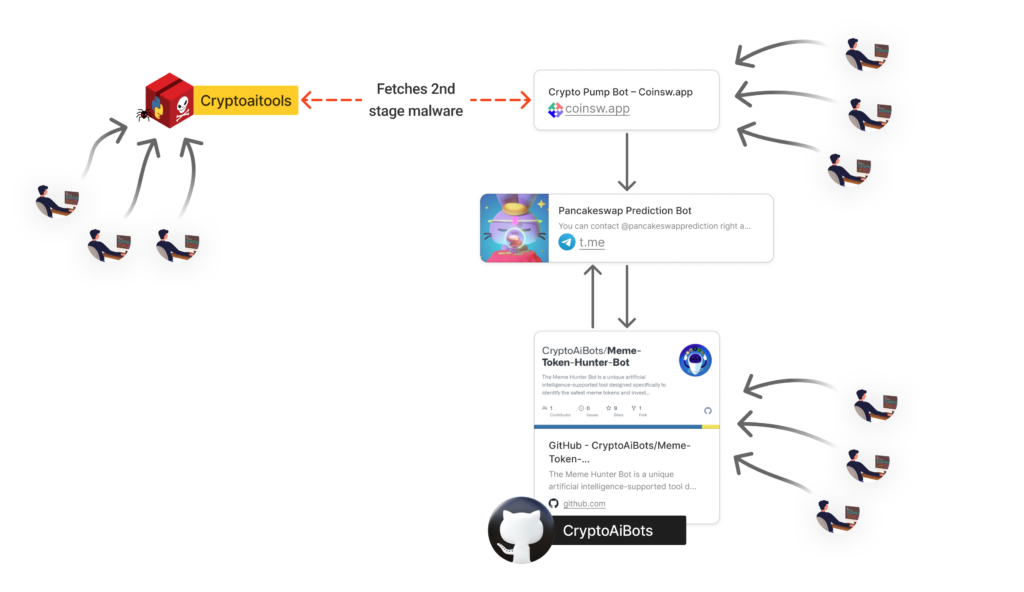
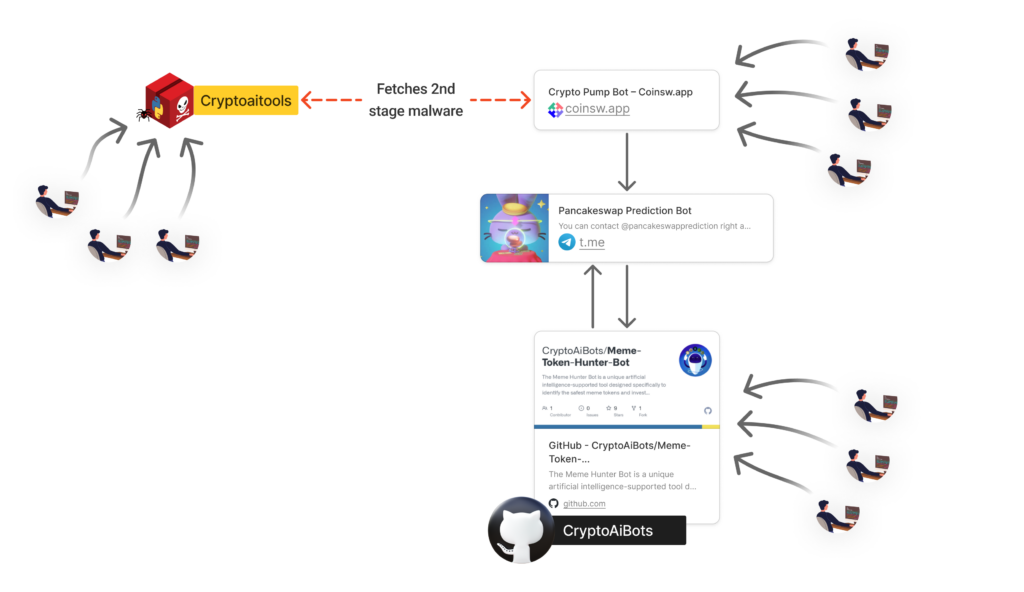
Cryptocurrency Enthusiasts Targeted in Multi-Vector Supply Chain Attack
A malicious PyPI package “cryptoaitools” targeted cryptocurrency enthusiasts through a multi-vector supply chain attack. It used deceptive GUI, multi-stage infection, and comprehensive data exfiltration to steal crypto-related information from Windows and macOS users. (Link to report).
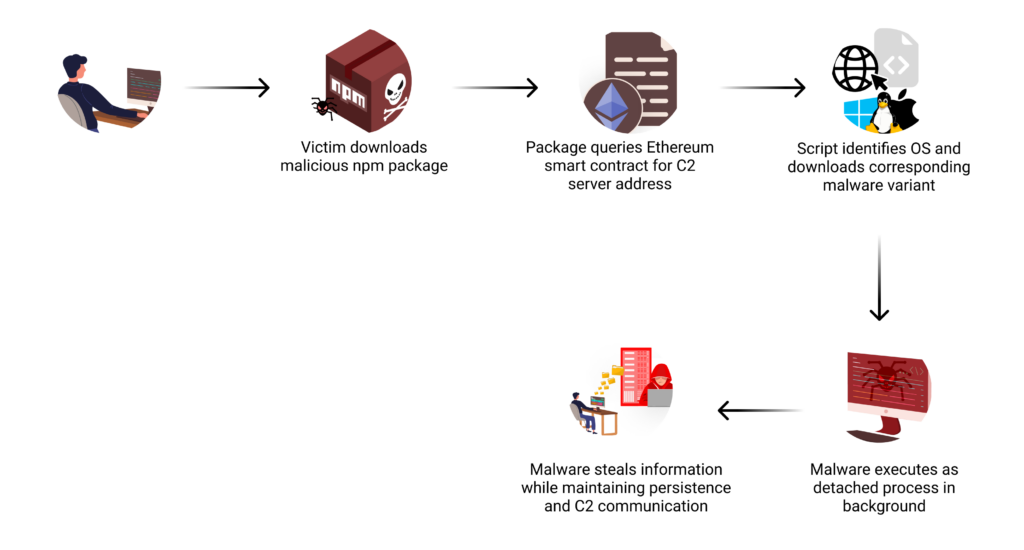
Supply Chain Attack Using Ethereum Smart Contracts to Distribute Multi-Platform Malware
A sophisticated NPM supply chain attack uses Ethereum smart contracts for C2 distribution. The cross-platform malware, targeting popular testing packages, affects Windows, Linux, and macOS through Typosquatting and preinstall scripts. (Link to report)
* * *
Our team will continue to hunt, squash attacks, and remove malicious packages in our effort to keep the open-source ecosystem safe.
I encourage you to stay up to date with the latest trends and tactics in software supply chain security by tuning into our future posts and learning how to defend against potential threats.
Stay tuned…
Working to Keep the Open Source Ecosystem Safe