Software supply chain security (SSCS) attacks are on the rise.
In fact, according to Infoworld, “we are in the midst of a rapid surge in software supply chain attacks,” with a staggering 742% annual increase, resulting in costs exceeding $4 million. Gartner predicted that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
The growing number of high-profile SSCS attacks and data breaches (such as SolarWinds, NotPetya, CCleaner, Target, Equifax and Kaseya VSA) have increased awareness of SSCS vulnerabilities. This alarming trend emphasizes the need for enterprises to allocate more resources into securing their software development and deployment processes, from code to cloud.
But how did we get here? Fifteen years ago, most enterprises exclusively relied on internally developed code. Today, however, most modern code bases are largely built with open source packages and third-party code. While this shift accelerates development and fosters more innovative code, it also introduces more vulnerabilities – whether from human error, careless exposure of secret keys (passwords, encryption keys, and access tokens), or malicious third-party code. Additionally, the recent uptick in AI-generated code from digital assistants like ChatGPT, GitHub Copilot, and Codestral has further increased the risk of insecure code finding its way into enterprise applications.
Like it or not, modern development requires the use of third-party codebases, despite the risks they may bring. That’s why enterprises need a solution to effectively manage and mitigate the risks associated with these third-party libraries.
AppSec Has Traditionally Focused on Internally Developed Code
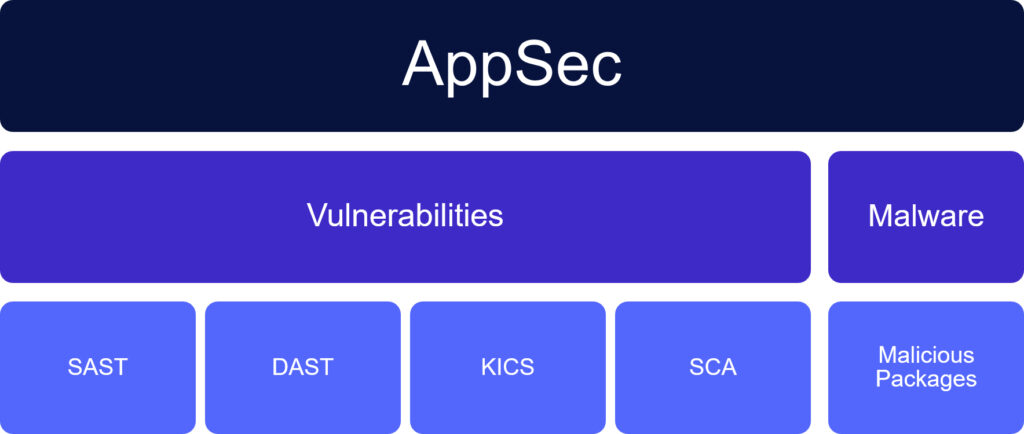
Figure 1 – Traditional application security focused only on finding vulnerabilities in proprietary code.
Until recently, application security (AppSec) primarily focused on the code developed by the enterprise in-house. This made it easier to detect and remediate security vulnerabilities, because the code was exclusively written by their own developers. Vulnerability detection for these code bases generally relied on static application security testing (SAST) and dynamic application security testing (DAST).
In fact, when Checkmarx was founded 18 years ago, we also focused on this traditional AppSec model, concentrating on securing the code developed internally by enterprises.
Why Software Supply Chain Security Now?
What changed? In recent years, the importance of securing the software supply chain from code to cloud has grown steadily among enterprise CISOs, AppSec managers, DevOps teams, and developers.
This shift is driven by four key factors:
- Extensive use of open source packages and other third-party code
- Migration of applications to the cloud (cloud-native applications)
- Incorporation of automated compile/deploy workflows (CI/CD)
- Proliferation of attacks on the software supply chain
These changes in modern development have introduced greater risks to software security than ever before. Securing applications now requires involvement from every stage of the software development lifecycle (SDLC), from code to cloud. To address these new threat vectors, Checkmarx developed a comprehensive, integrated solution that protects the entire software supply chain.
SSCS Begins With SCA and Malicious Package Protection
Surveys indicate a dramatic increase in the use of open source libraries, with up to 97% of applications now incorporating open source code. This statistic is not surprising, considering how open source libraries significantly speed up development and reduce business costs.
However, this new, increased use of open source code has also exposed enterprises to a massive new threat vector: both unintentional vulnerabilities and intentionally malicious code – both of which can be exploited.
Checkmarx has adapted to the evolving risks in the software supply chain and has become a leader in addressing these open source risks. How? Our Software Composition Analysis (SCA) solution provides enterprises with a strong protection against these types of malicious packages. Checkmarx’ SCA solution:
- Comprehensively discovers and itemizes all open source packages used in applications (including transitive open source dependencies)
- Identifies open source packages containing vulnerable code, malicious code, or suspicious behavior (such as typosquatting, starjacking, and repojacking)
- Prioritizes remediation efforts using multiple analyses (e.g., reachability/exploitable path analysis and SAST correlation)
- Provides AppSec teams and developers with specific and actionable remediation guidance
- Integrates with CI/CD and IDE tools to smoothly integrate security testing and remediation workflows into existing deployment and development platforms
- Generates an industry-standard software bill of materials (SBOM)
- Detects legal and compliance risks associated with open source licensing issues
- Enforces policy rules to automatically send alerts and prevent builds based on a range of factors
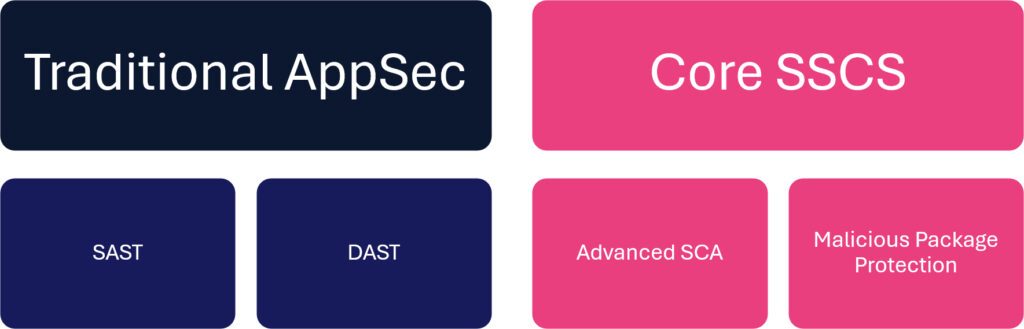
Figure 2 – The first step to expanding application security into software supply chain security is adding advanced SCA with malicious package protection.
Checkmarx One: Advanced AppSec Including SSCS
Unfortunately, even advanced SCA solutions are no longer enough to protect against SSCS attacks. To fully protect the software supply chain, Checkmarx now offers a complete suite of industry-leading solutions to secure both internally developed code and the software supply chain components that they consume.
Checkmarx One is a code- to -cloud platform that provides an integrated SSCS solution that no enterprise can afford to be without. In addition to our SAST, DAST, SCA, and malicious package protection capabilities, Checkmarx One covers the entire software supply chain with the following capabilities:
- Container Security – Identify and mitigate risks in container images, container infrastructure, and runtime code.
- AI Security – Automatically scan AI-generated source code and referenced open source libraries for vulnerable or malicious code.
- IaC Security – Secure cloud infrastructure with proactive vulnerability identification and misconfiguration detection.
- API Security – Discover and remediate every API vulnerability.
- Secrets Detection – Automatically discover the presence of sensitive credentials.
- Repository Health – Get comprehensive health scorecards for software repositories.
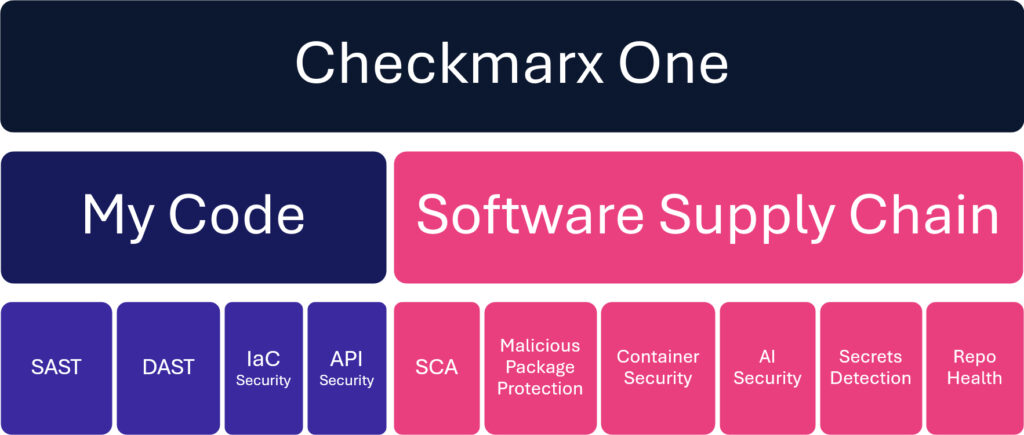
Figure 3 – Checkmarx One delivers comprehensive code-to-cloud application security, including coverage for critical software supply chain dangers.
More About Our Newest Capabilities
Secrets Detection and Repository Health are the newest additions to the Checkmarx One suite aimed at protecting against software supply chain risks. Let’s take a closer look at these new offerings:
Secrets Detection

Figure 4 – Secrets Detection minimizes risk by identifying sensitive credentials that are at risk of being unintentionally exposed.
Enterprises unintentionally expose thousands of secret credentials in GitHub and other publicly accessible or insecure locations every day. This exposure can enable unauthorized access to your systems, potentially resulting in cyber-attacks, financial loss, and reputational damage. Once credentials are compromised, attackers can move laterally within systems to extract data, deploy malware, or launch further attacks on infrastructure, customers, and partners.
Checkmarx’ Secrets Detection minimizes risk by quickly identifying sensitive credentials that may be unintentionally exposed – and pinpoints which ones are still valid. With this insight, your development and security teams can quickly remediate issues by removing exposed secrets and updating them to prevent any unauthorized usage.
Scanning for exposed secrets can be initiated on demand or manually with automatic triggers via SCM integration (e.g., pull request, build). Discovered secrets are automatically validated to determine if they are still in effect and thus potentially exploitable.
This provides three key benefits:
- Minimize supply chain risk by preventing the exposure of secret credentials, reducing the chance of attackers accessing your systems or stealing data.
- Improve regulatory compliance by meeting data protection requirements (e.g., GDPR, HIPAA, PCI DSS, SOX, FISMA, CCPA) and avoiding fines and reputational damage.
- Increase developer efficiency by allowing developers to initiate scans, review discovered secrets, and receive remediation guidance directly within their IDE.
Repository Health

Figure 5 – Repository Health provides ongoing visibility into the security and maintenance health of the code repositories used in enterprise applications.
Enterprises also need a reliable way to continuously evaluate the riskiness of the open source code used in their applications, as well as a method to monitor the quality and security of the repositories containing their internally written code.
Checkmarx’ Repository Health maximizes the security posture of your software supply chain by continuously tracking health scores for all repositories in your applications. Scoring is based on more than a dozen key factors in areas, such as code quality, dependency management, CI/CD best practices, and project maintenance.
Repository Health can automatically scan repositories upon repository updates, ensuring up-to-date repo health metrics with no manual effort. Developers and security teams can also run on-demand repo health scans at any time via API, CLI, or the Checkmarx One UI.
Additionally, repository health scores are included in Checkmarx One reports, providing visibility into – and efficient prioritization of – security vulnerabilities, code quality issues, and repository health risks, all in one place.
The three key benefits this provides include:
- Minimize supply chain risk – Visibility into the security health of open source components and your own code repositories that closes an important gap in software supply chain security.
- Efficient holistic risk prioritization – Identifying and prioritizing high-risk areas across the software supply chain that allows developers and security teams to focus their efforts on the most critical security issues.
- Enhanced transparency and communication – Clear, quantifiable metrics on the security posture of open source dependencies and first-party repositories that improve transparency and communication among stakeholders.
Learn More
Given the wide range of threat vectors facing enterprise applications and the software supply chain, deploying the most comprehensive and effective security solutions is essential. And these solutions must also cultivate an excellent developer experience to encourage adoption and support seamless, efficient workflows.
Relying on a hodge-podge of different tools to protect your supply chain is no longer viable – it is expensive, inefficient, and difficult to maintain. To protect your enterprise from data breaches or other system infiltrations unified platform that covers all your bases. And that’s where Checkmarx comes in.
Contact us for a free demo of Checkmarx One and discover the industry’s best solution for securing your enterprise’s applications and the software supply chain.