2024-11-22 16:23:19 Author: securityboulevard.com(查看原文) 阅读量:0 收藏

Phishing attacks are among the most common—and costly—cyber threats affecting anyone using the Internet. These attacks, often disguised as legitimate emails, trick people into sharing sensitive information or unknowingly downloading harmful software, with billions lost yearly.
To combat this, organizations are turning to DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC is an email authentication protocol designed to prevent email spoofing, a tactic at the heart of most phishing schemes. Yet, despite its effectiveness, many companies have yet to adopt DMARC, leaving them vulnerable to email-based attacks.
To help you better understand the risks associated with phishing attacks and the importance of DMARC in defending against them, we’ve highlighted the most common phishing tactics, the risks, and how they exploit email vulnerabilities. We will also explain how DMARC can effectively protect your organization from email spoofing, a major contributor to phishing attacks.
Key Takeaways
- DMARC coverage among major companies varies significantly by country, with Denmark leading at 59% coverage.
- 41% of banking institutions lack DMARC protection.
- 25.5% of email senders using p=none plan to upgrade to a stronger DMARC policy within the next year.
- In the second quarter of 2024, the number of phishing attacks reached 877,536.
- The majority (94%) of organizations fell victim to phishing attacks during 2024.
- It takes 60 seconds to fall for phishing emails.
- Phishing was the top initial infection vector in manufacturing, representing 39% of incidents.
- With AI, a deceptive phishing email can be generated in as little as 5 minutes.
Topics Covered
- Overview of Cybercrime Statistics
- DMARC Statistics
- Phishing Statistics
- Phishing Attacks by Industry
- AI and Phishing
- Awareness and Prevention
Overview of Cybercrime Statistics
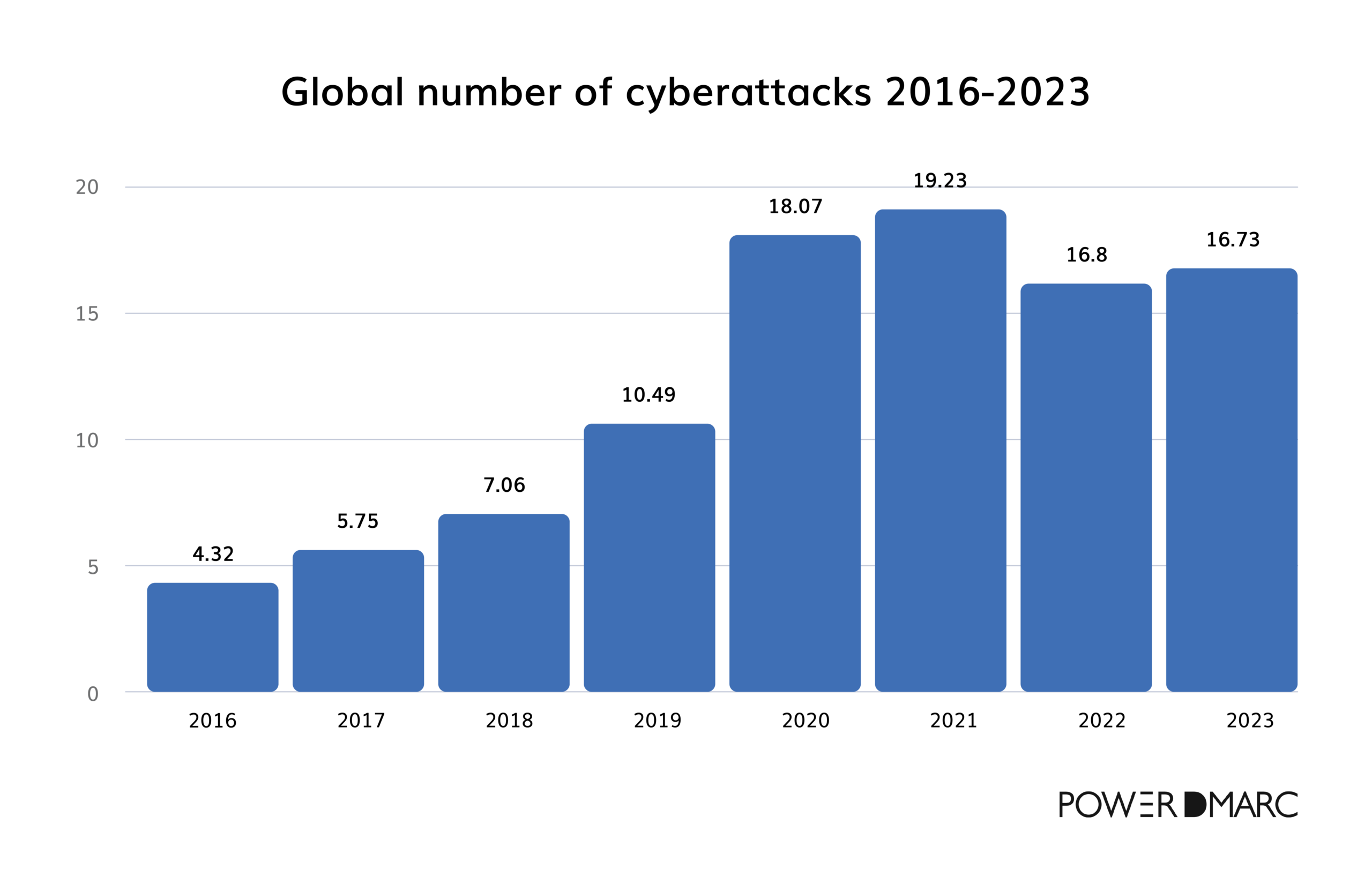
The global number of cyberattacks through the years has introduced us to a clear, simple yet terrifying story: cyberattacks have been increasing sharply over the past years and are not going away anytime soon.
Back in 2016, we saw about 4.3 million attacks globally, but in just five years, that figure reached over 19 million. This was a dramatic leap, especially during the 2020-2021 period, as more people moved online due to the pandemic. Although 2022 and 2023 showed a slight decrease, with 16.7 million attacks reported last year, cyber threats remain an issue.
Phishing scams take the lead
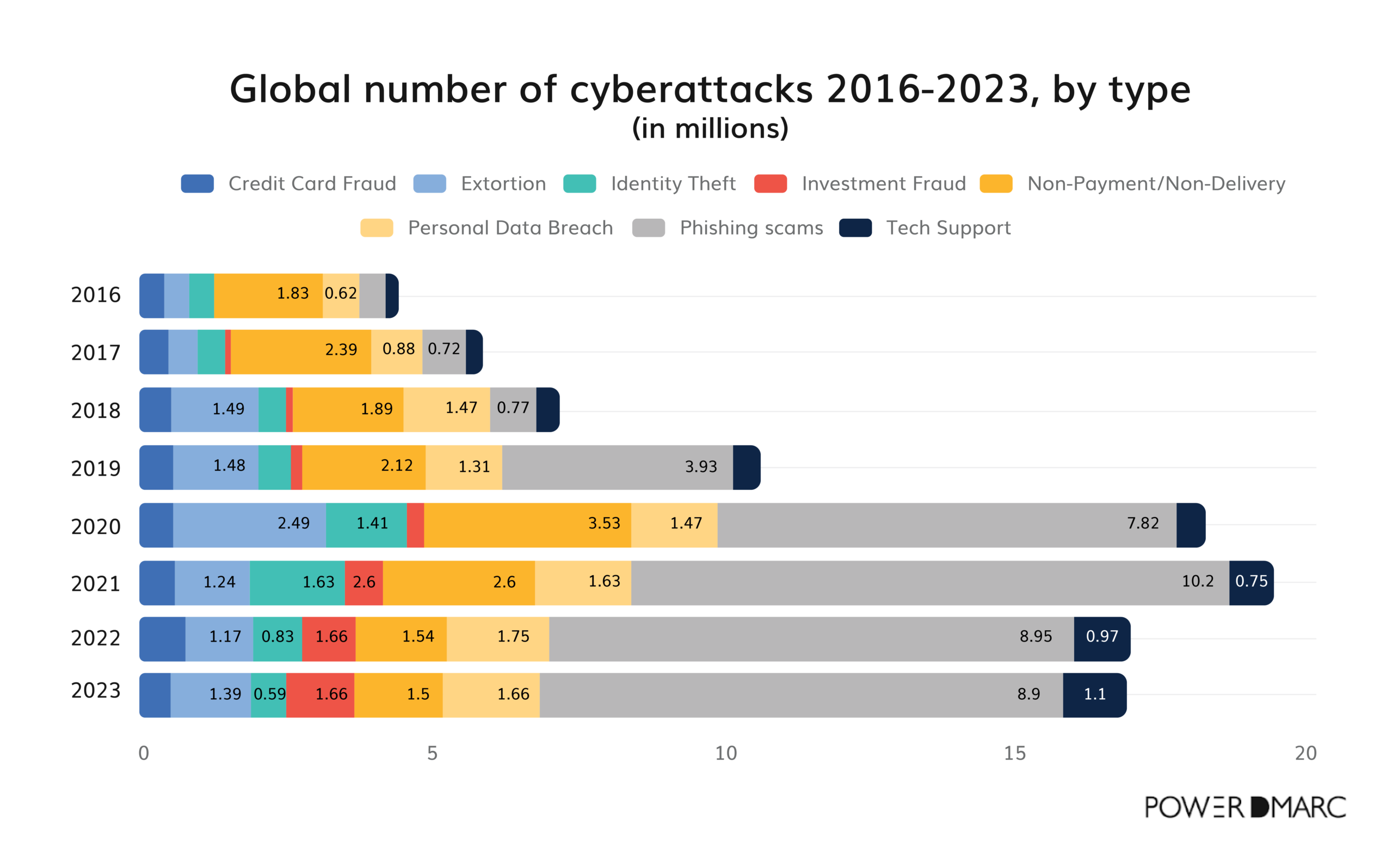
Not all cyberattacks are created equal, and when we look at the data by type, some interesting patterns emerge.
Phishing attacks have gained global popularity, going from 0.44 million in 2016 to nearly 9 million in 2023. Phishing’s big spike around 2019 to 2021 (from 3.93 to 8.95 million) coincides with a time when many people were already on edge, adapting to digital-only communication during the pandemic.
Personal data breach ranked second, followed by non-payment/non-delivery cases
Personal data breach ranked second, with 1.66 million incidents worldwide, followed by 1.5 million non-payment/non-delivery cases. Other attacks follow as shown:
- Extortion – 1.39 million
- Investment Fraud – 1.18 million
- Tech Support – 1.1 million
- Identity Theft – 0.59 million
- Credit Card Fraud – 0.41 million
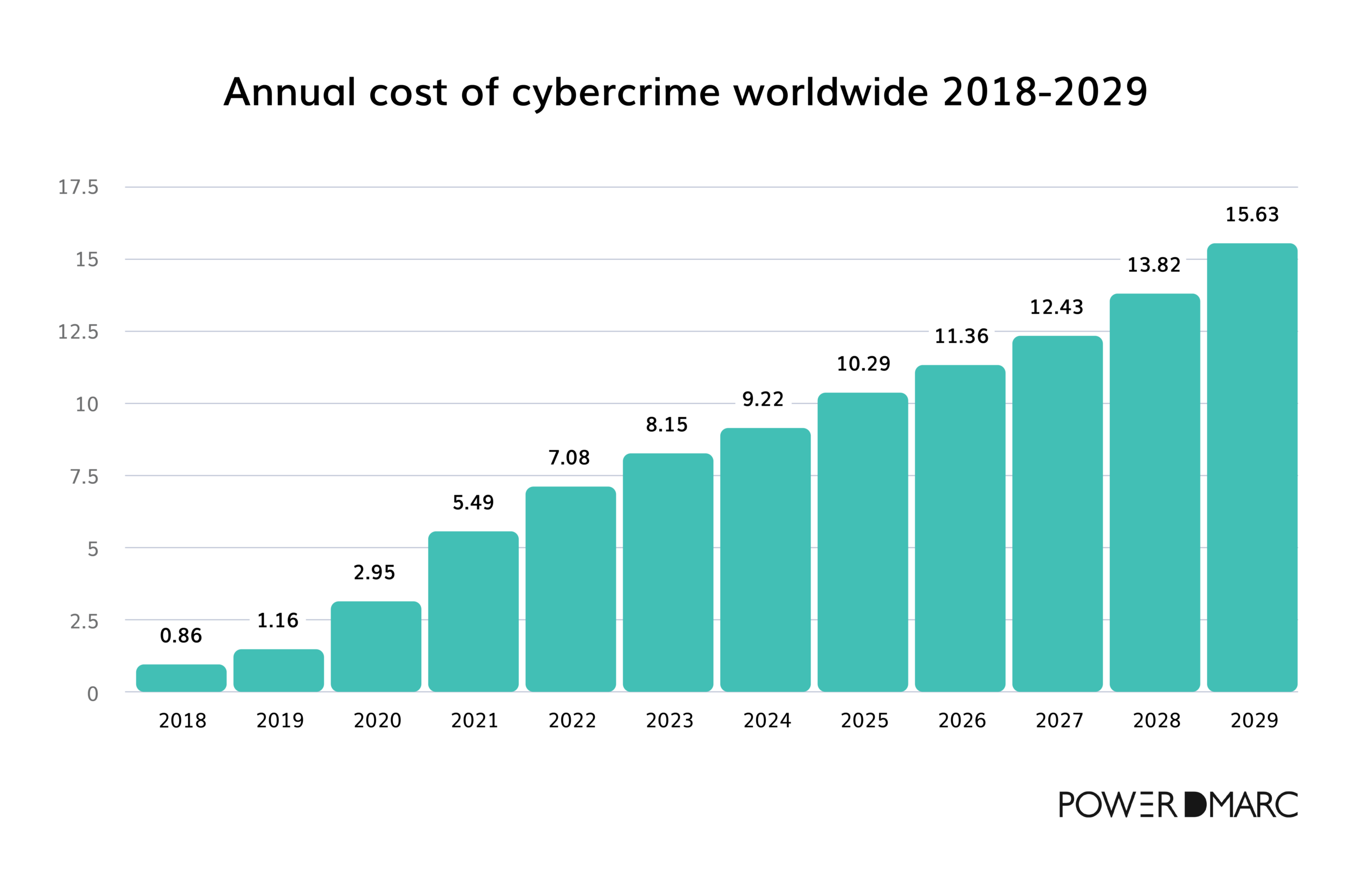
The rising cost of cybercrime (2018-2029)
Cyberattacks have become increasingly sophisticated and, with that, increasingly costly. In 2018, global cybercrime costs were estimated at $860 billion. Fast-forward to 2024, we’re looking at an estimated $9.22 trillion—nearly ten times as much in just five years. Projections show this trend continuing, with costs potentially reaching over $15 trillion by 2029.
Cybercrime in the U.S. by type
In the U.S., phishing was the most reported type of cybercrime in 2023, affecting nearly 300,000 individuals. This aligns with the global data mentioned above, as phishing remains one of the most common and damaging attack types.
Other major attack types
- Personal Data Breaches – Affected over 55,000 people.
- Non-Payment/Non-Delivery Scams: Affected around 50,000 people.
- Extortion: About 48,000 individuals in the U.S. reported extortion attempts.
Cybercrime worldwide by type
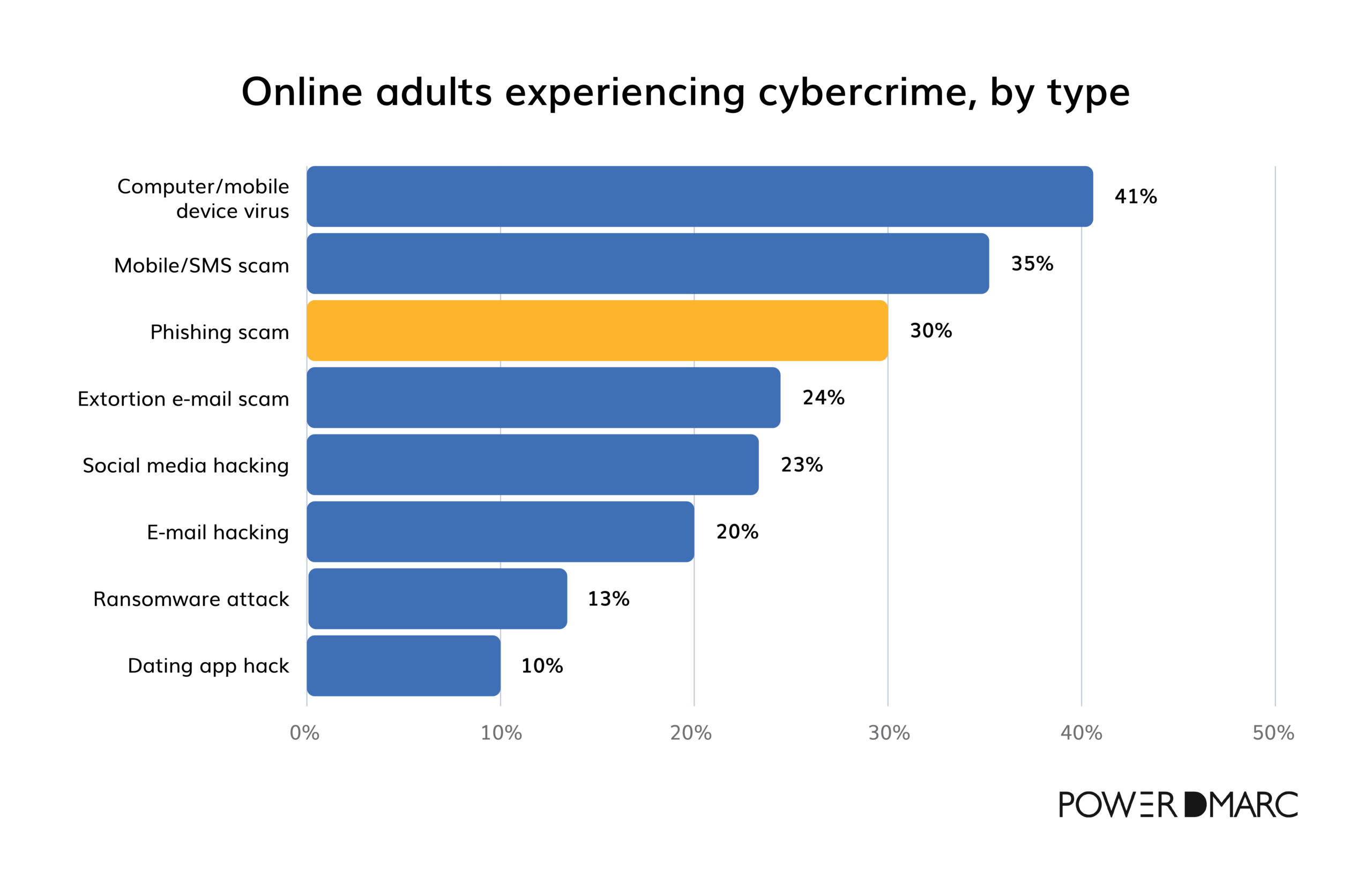
Globally, cybercrime has impacted a significant share of adults, with some types more common than others. For instance, 41% of online adults report experiencing viruses or malware on their devices. Phishing scams are also common, affecting about 30% of users, while mobile/SMS scams have impacted 35%.
Cybercrime beyond phishing
While phishing holds our attention, other attacks are also widespread. Social media and email hacking affect around 23-20% of online adults, showing how attackers are increasingly targeting personal accounts where people are more vulnerable. Ransomware and even dating app hacks are also on the rise, adding new layers to the types of threats people face.
DMARC Statistics
As the threats mentioned above evolve, managed DMARC solutions are becoming crucial tools. They help organizations strengthen email security by monitoring for suspicious activity and ensuring legitimate messages reach their destinations without disruption.
As required by Google and Yahoo, companies sending over 5,000 email messages through Google or Yahoo must adopt DMARC to comply with updated authentication standards. This move led to a 65% reduction in unauthenticated emails to Gmail, according to their latest data.
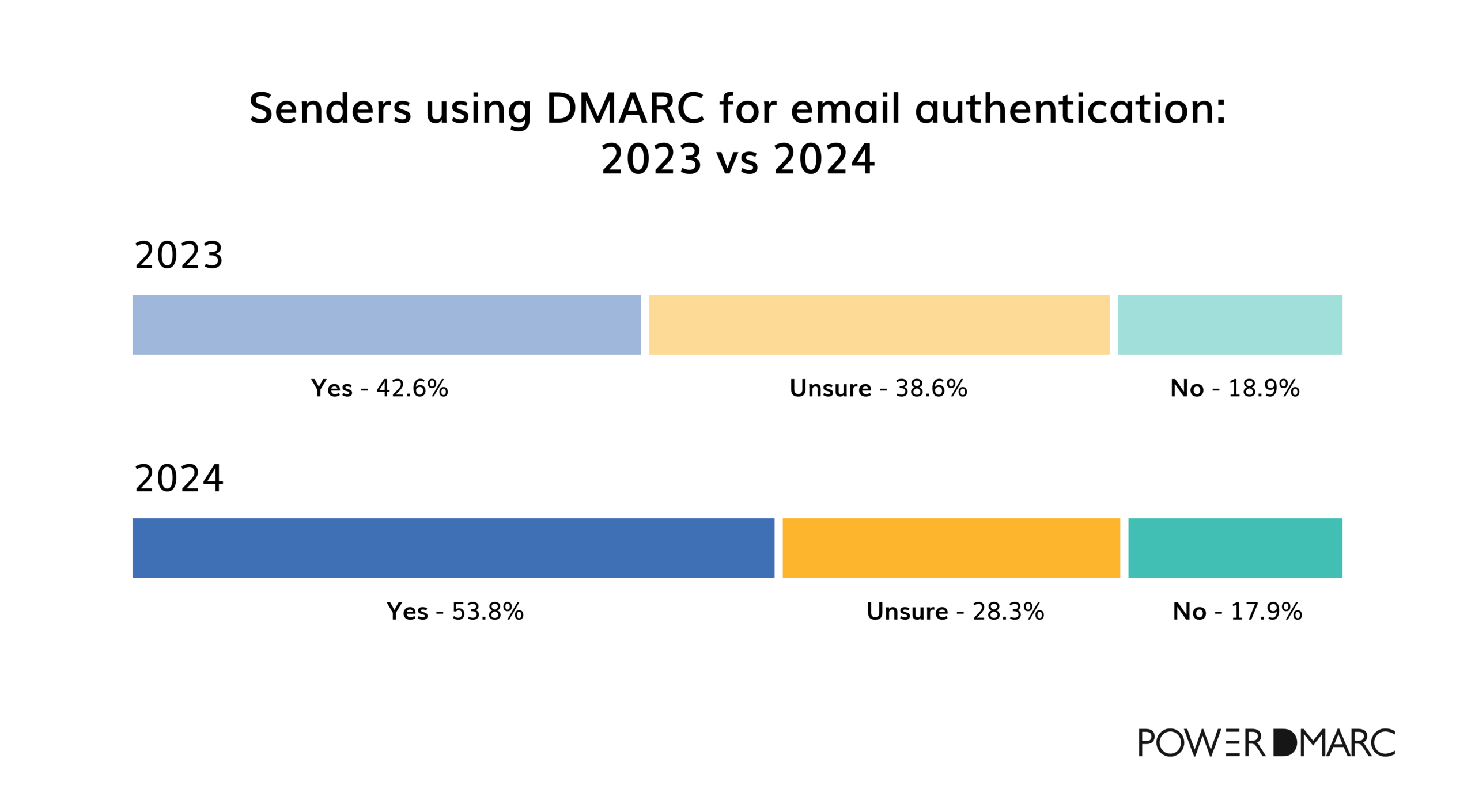
To support this trend, the state of email deliverability in 2024 shows an 11% increase in the adoption of DMARC, reaching 53.8% compared to 42.6% in 2023.
The requirements are expected to go beyond email marketers, compelling all companies, especially those lagging behind in adopting SPF, DKIM, and DMARC, to catch up. By the end of 2024, 70% of large enterprises with over 1,000 employees are projected to implement DMARC policies, significantly strengthening email security.
DMARC implementation statistics
According to the latest DMARC statistics, DMARC adoption has doubled over the past year, rising from 55,000 to 110,000 new domains per month in 2024.
Another examination of over 1 million websites shows that DMARC adoption remains low, with only 33.4% having a valid DMARC record.
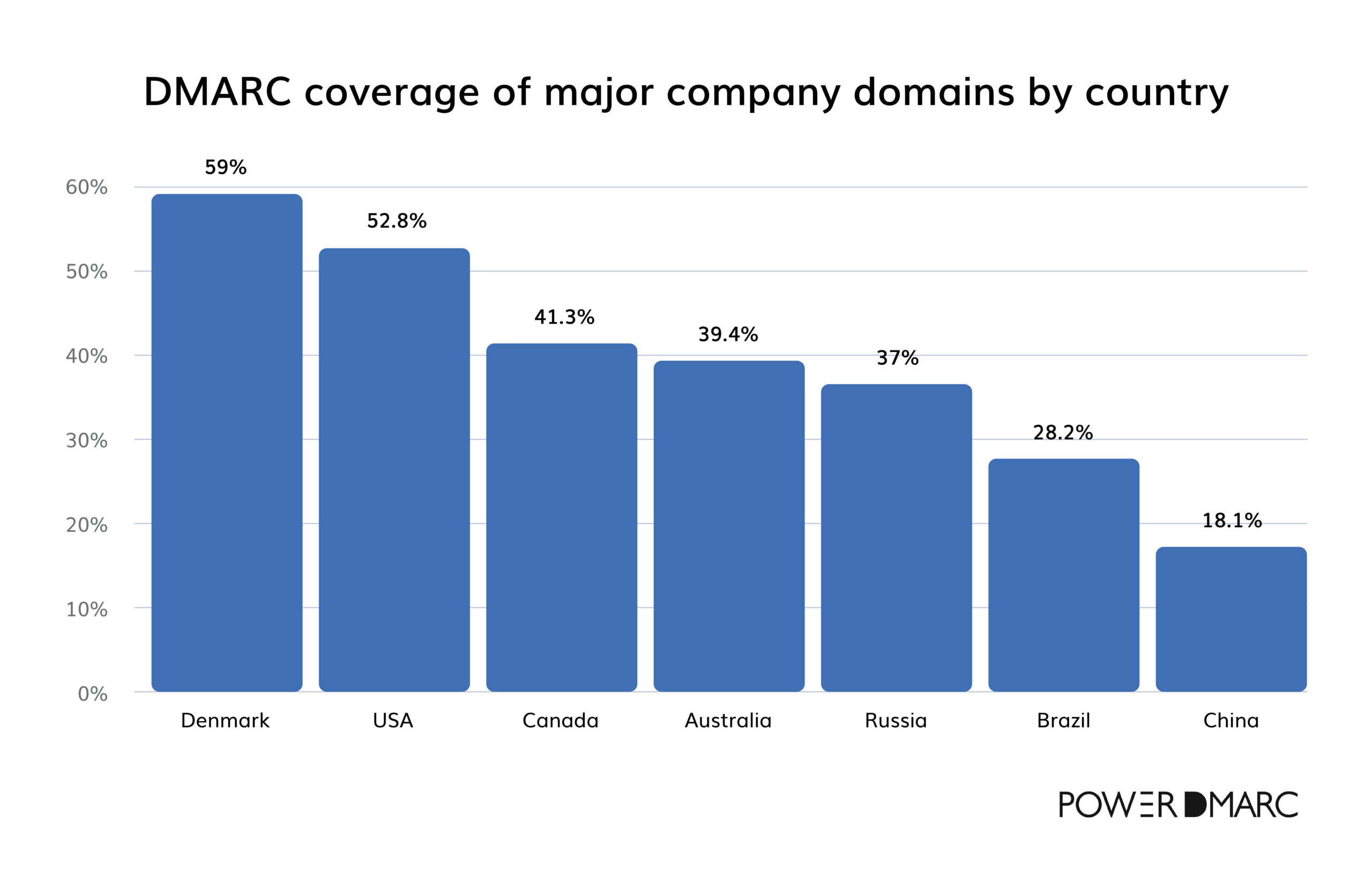
DMARC coverage by country
DMARC coverage among major companies varies significantly by country, with Denmark leading at 59% coverage. The United States follows in second place; however, nearly half of U.S. company domains still lack DMARC protection.
Even at its highest, no country has exceeded 59% DMARC coverage—falling short of the levels needed to effectively combat email scams and spoofing globally.
According to additional data from PowerDMARC, Switzerland has 44.2% of domains with proper DMARC records, placing it slightly above average in terms of adoption. Malaysia and Kuwait follow with 39.5% and 41.25% coverage, respectively, based on PowerDMARC’s findings. Meanwhile, Qatar and Chile trail further behind, with only 35.15% and 35.9% of domains in each country correctly configured, according to the same data.
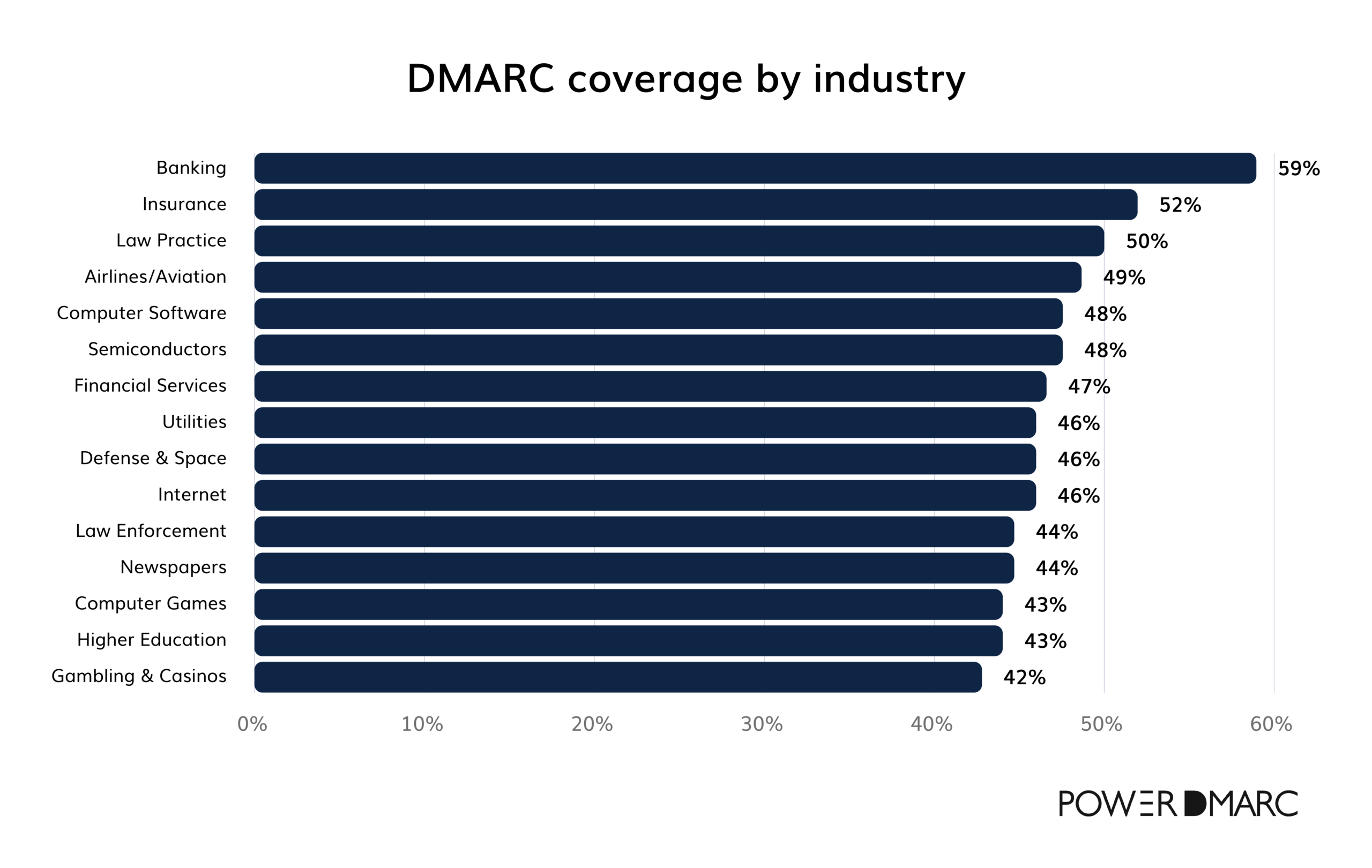
DMARC coverage by industry
Despite DMARC adoption trends improving, critical sectors like banking still demonstrate alarming gaps in email security.
41% of banking institutions lack DMARC protection, leaving customers vulnerable to phishing and financial fraud. While the banking industry has the highest adoption rates compared to other sectors, the current level of protection is inadequate for safeguarding sensitive communications.
Other industries fare worse:
- Only 52% of insurance and law firms have implemented DMARC.
- Sectors like aviation, semiconductors, computer software, and financial services hover slightly above 45% adoption rates.
DMARC policy trends
Regarding the DMARC implementation, most domains lack strict enforcement, limiting its full security benefits. A majority (68.2%) use a “none” DMARC policy, allowing emails that fail DMARC checks to be delivered without restriction. Only 12.1% use “quarantine” to send suspicious emails to spam, and just 19.6% have a strict “reject” policy to block non-compliant emails.
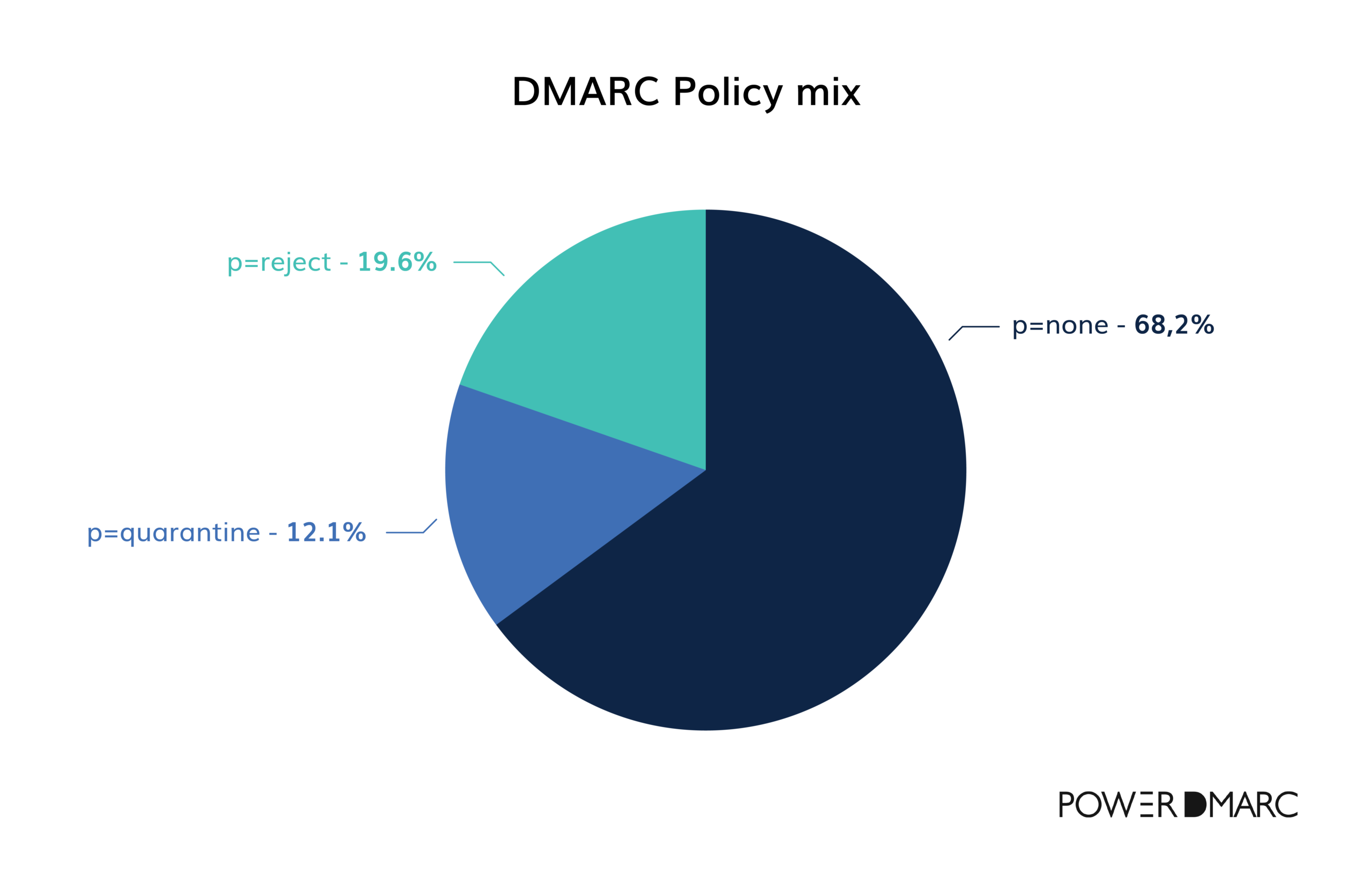
Although adopting stricter policies like p=quarantine or p=reject is essential for enforcement, many companies remain hesitant to make the shift:
- 25.5% of senders using p=none plan to upgrade to a stronger DMARC policy within the next year.
- 61% will only update their policy if required by regulatory or business needs.
- 13% have no plans to strengthen their policy, as they already meet current DMARC requirements.
To fully grasp the stakes, it’s essential to look beyond the DMARC statistics and delve into the growing threat of email phishing attacks.
Let’s take a look!
Phishing Statistics
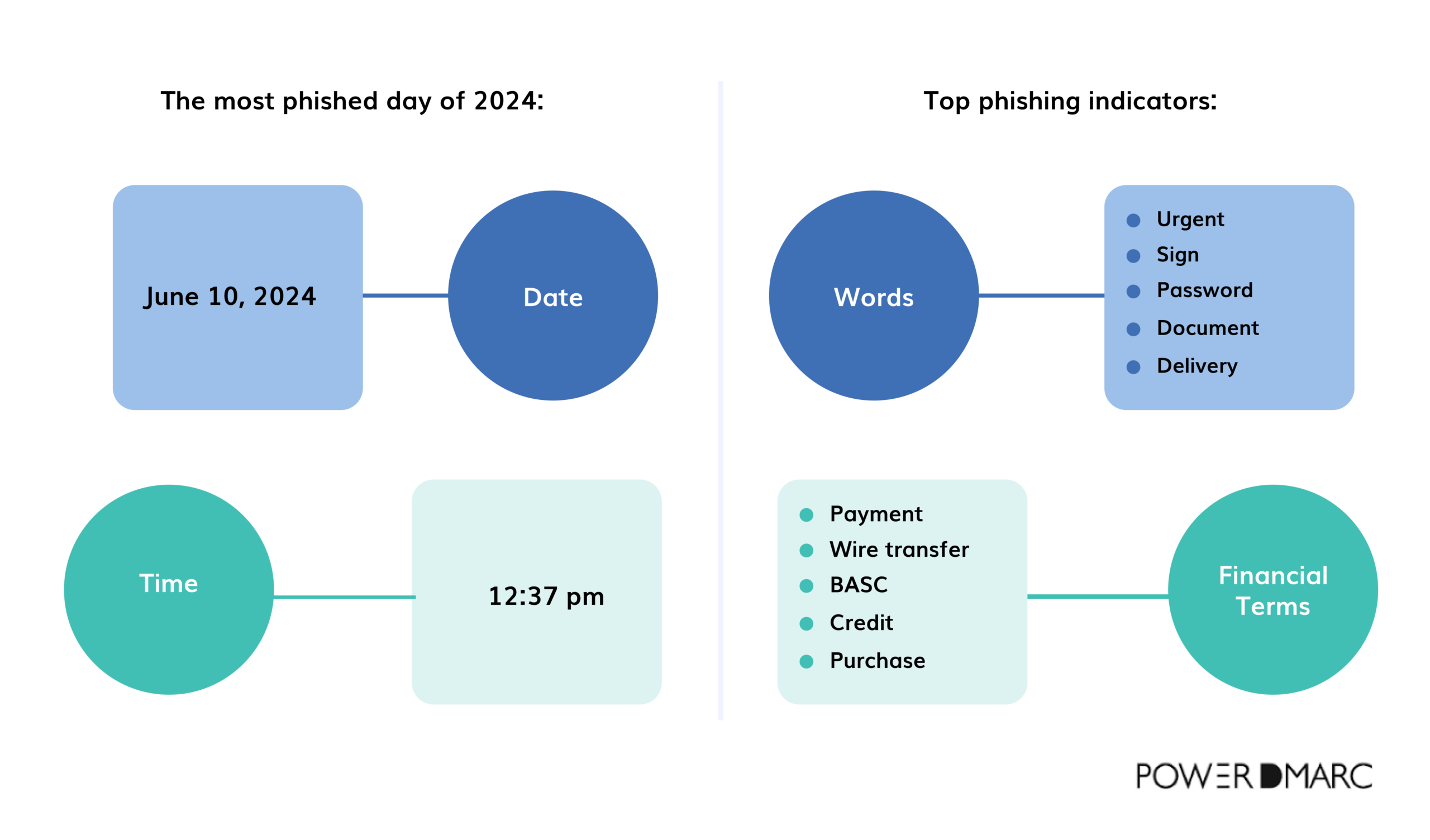
June 10, 2024, at precisely 12:37 p.m., marked the peak of phishing activity for the year. This day saw a huge surge in phishing emails, reflecting a concerning trend that had been building over the previous months.
Between April 1 and June 30, phishing emails spiked by 28% compared to the first quarter of 2024. Scammers relied heavily on attention-grabbing words like “Urgent,” “Sign,” “Password,” “Document,” and “Delivery” to lure people in, along with financial terms like “Payment,” “Wire transfer,” “BACS,” “Credit,” and “Purchase.”
These words were strategically chosen to prompt people to act without second-guessing, a reminder of how sophisticated phishing tactics have become in their pursuit of personal and financial information.
Email phishing statistics
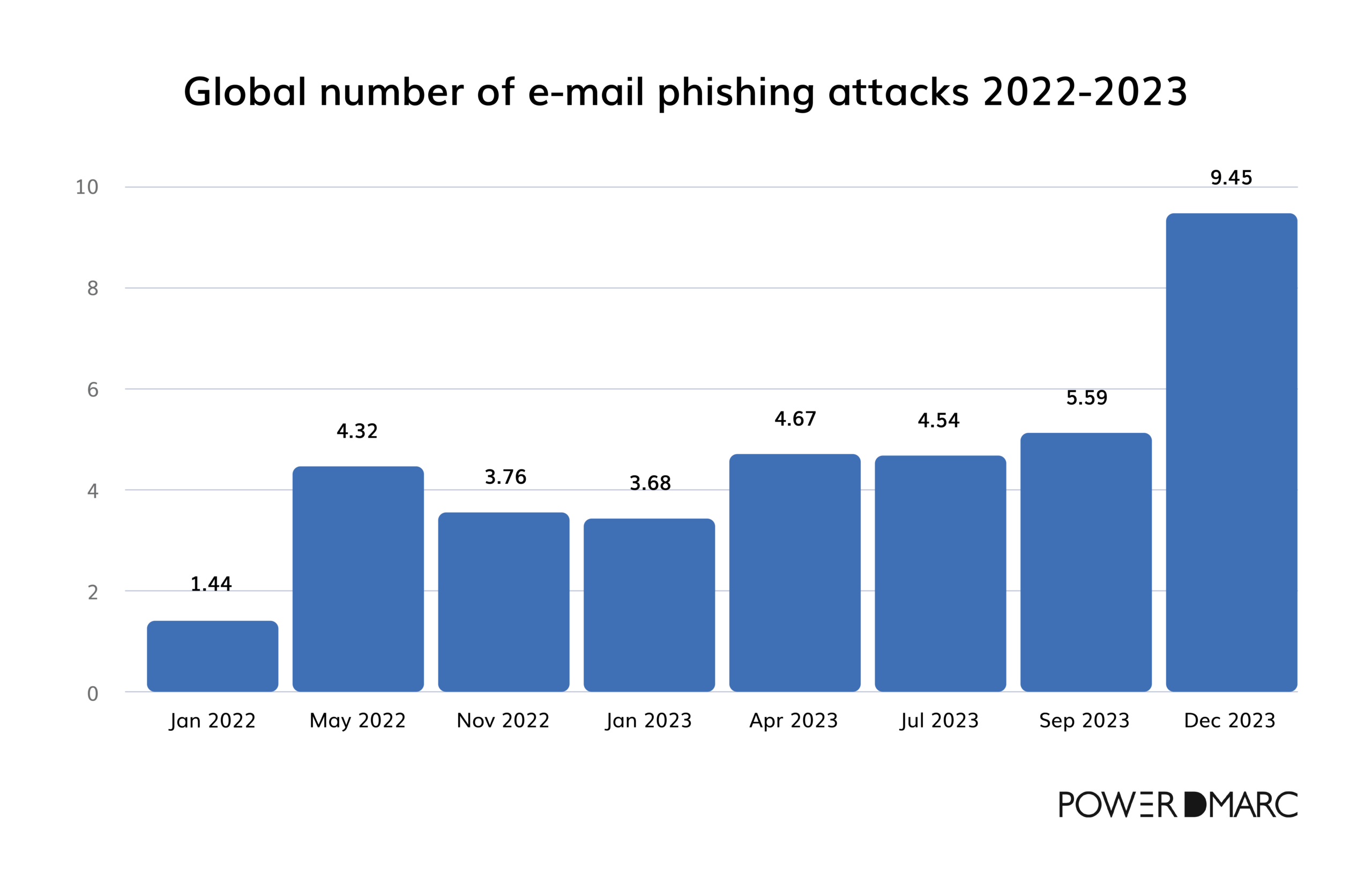
When analyzing the timeline from January 2022 to December 2023, we notice a concerning upward trend regarding email phishing attacks:
Initial trends in 2022
- In January 2022, the number of detected phishing emails started at 1.44 million. By May 2022, phishing attacks increased, reaching 4.32 million. After a mid-year peak, November 2022 showed a slight decline to 3.76 million, which was still much higher than in January.
Escalation in 2023
- January 2023 recorded 3.68 million phishing emails—still notably higher than the same month in 2022. By April 2023, the count rose further to 4.67 million. July 2023 saw a slight decrease to 4.54 million but quickly went up to 5.59 million in September 2023. By December 2023, the number of phishing attacks reached 9.45 million—a 70% increase in just three months.
Phishing site trends over time (2013-2024)
The number of unique phishing sites has fluctuated over the years, with a notable peak in 2022 and early 2023, when over a million sites were detected each quarter. Following this spike, there has been a steady decline in Q3 2023 through Q2 2024, dropping to around 877,536 sites..

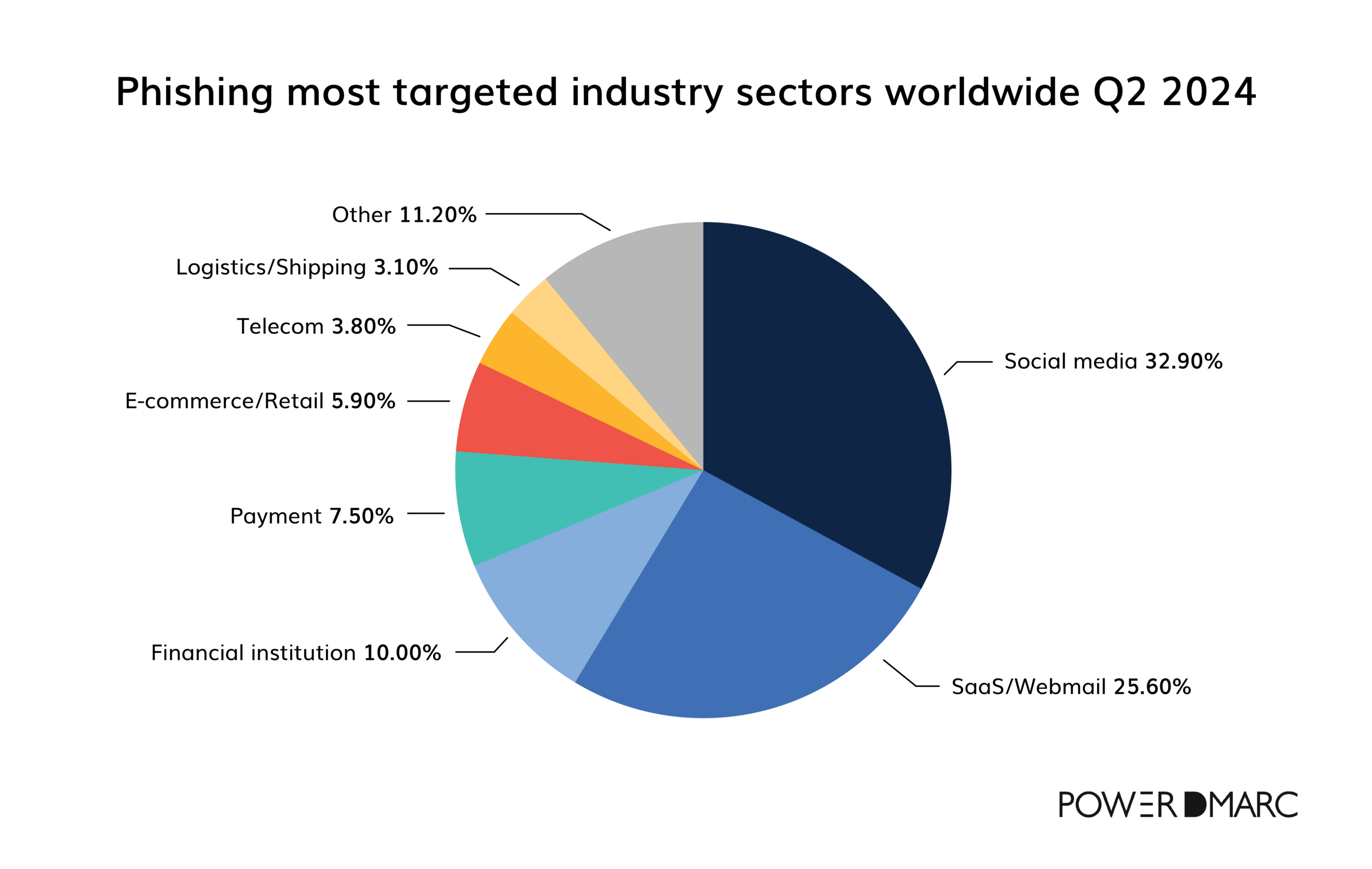
Targeted online industry sectors in phishing (Q2 2024)
Phishing attacks in Q2 2024 targeted social media the most (32.9%), followed by SaaS/Webmail (25.6%) and financial institutions (10%). These sectors are likely targeted due to the large user bases and valuable data associated with these platforms.
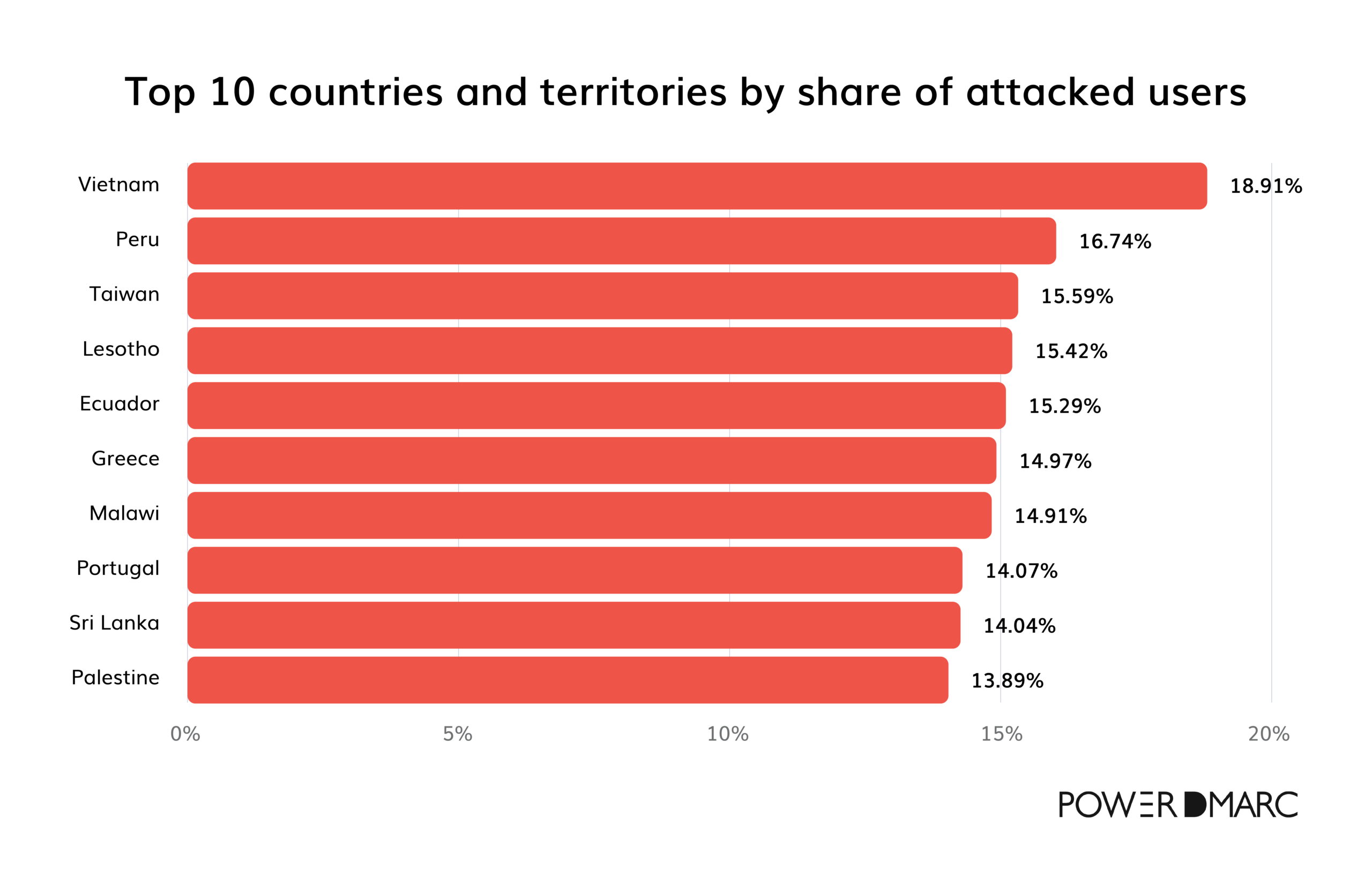
Top 10 countries most affected by phishing attacks (2024)
In 2024, phishing attacks have targeted users worldwide, with certain countries experiencing high rates of these cyber threats. Vietnam leads with 18.9% of users attacked by phishing, followed by Peru at 16.7% and Taiwan at 15.5%.
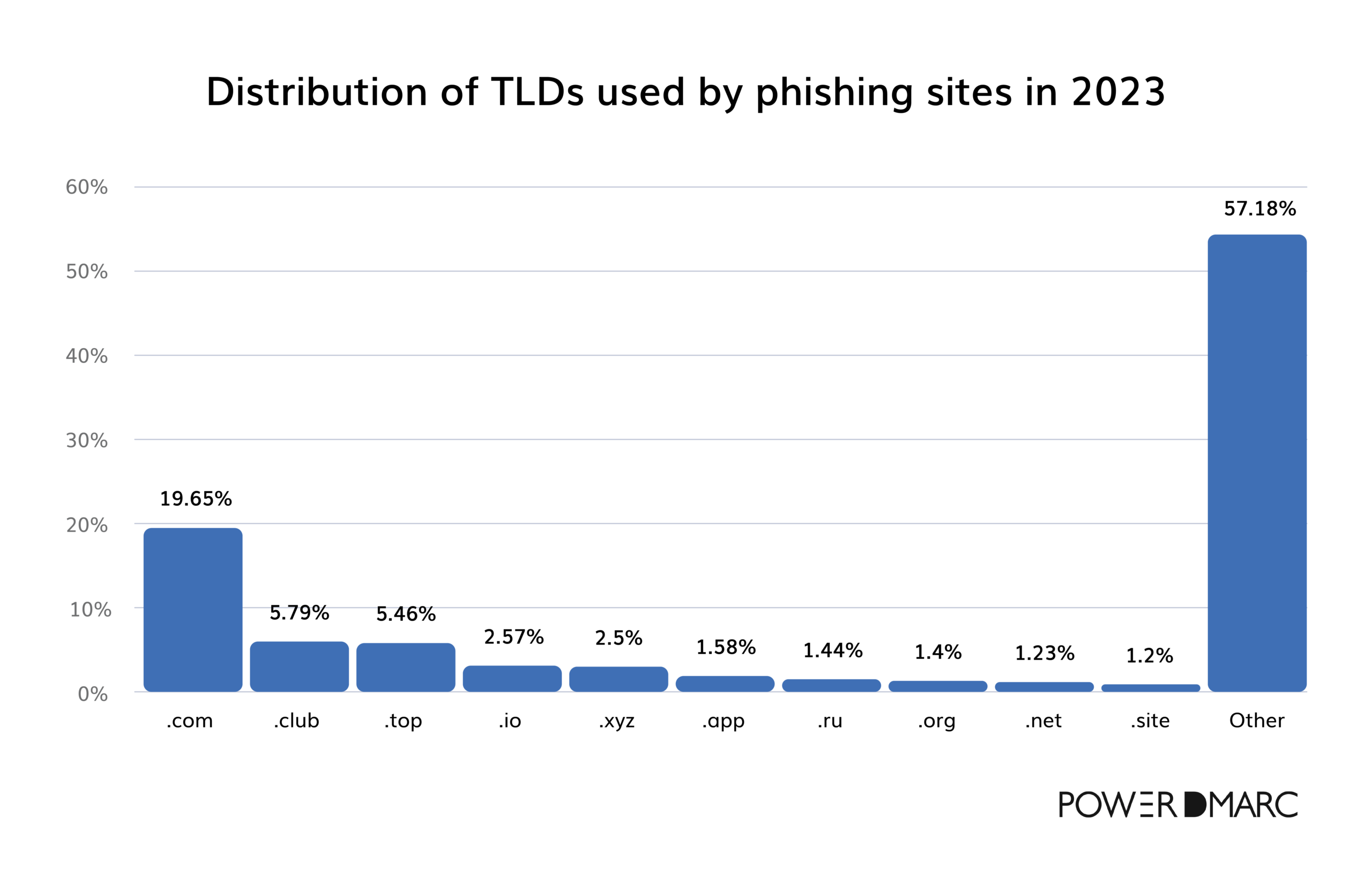
Top-level domains used in phishing
Phishing sites often use familiar TLDs to appear legitimate, though newer TLDs are gaining ground. In 2023, “.com” was the most common TLD in phishing attacks (19.65%), followed by alternative TLDs like “.club” (5.79%) and “.top” (5.46%).
Phishing targeting brands (2009-2024)
The number of brands targeted by phishing has grown over time, reaching the highest point in 2022 at around 621. Afterward, a gradual decline occurred through 2023 and 2024, potentially due to improved brand monitoring and phishing prevention techniques or shifting tactics by attackers.
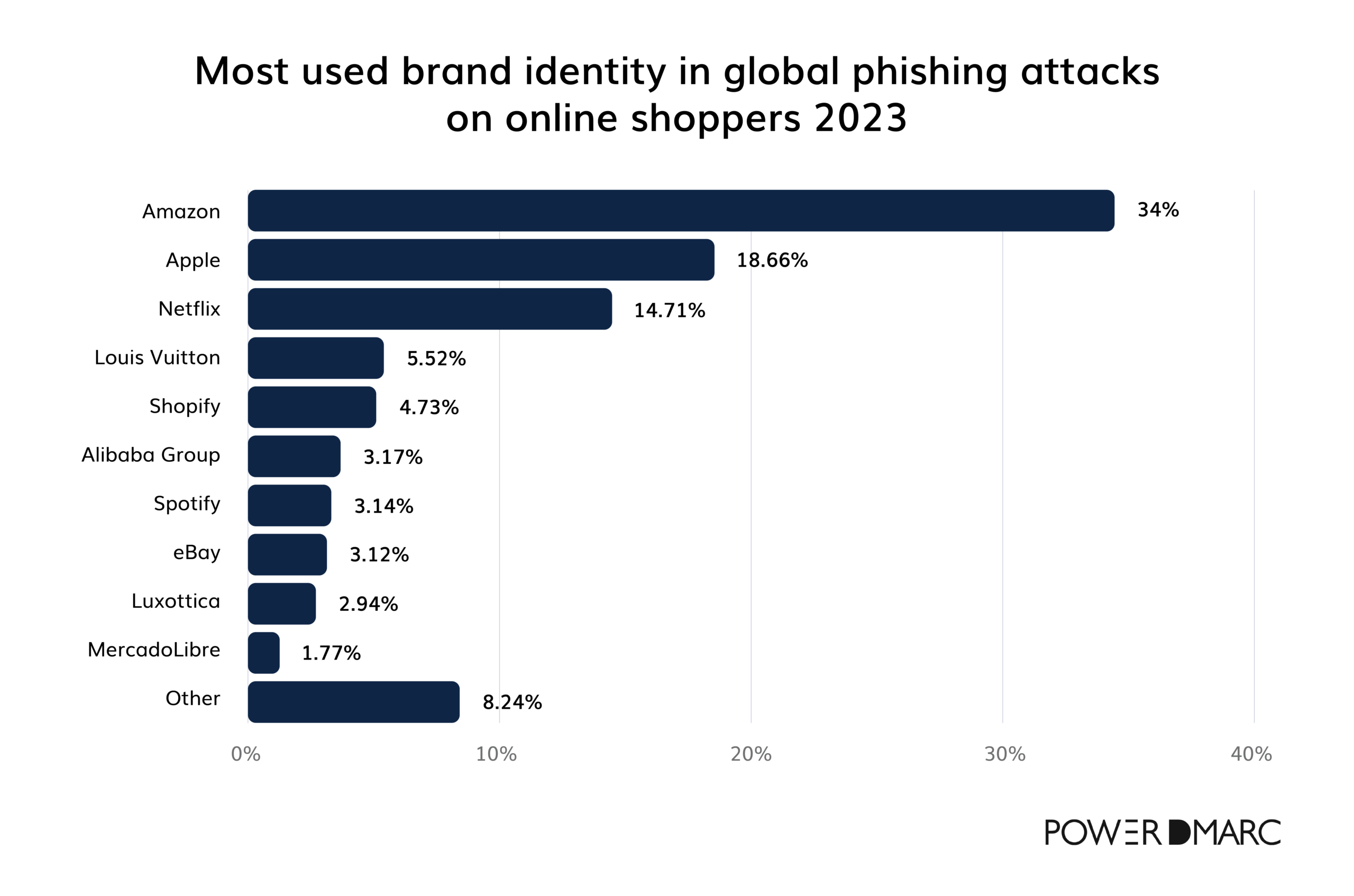
Most impersonated brands in online phishing
One thing we know for sure about phishing is that attackers focus on well-known brands with global customer bases to maximize the likelihood of successful phishing. That said, Amazon (34%) was the top brand impersonated in phishing attacks against online shoppers in 2023, with Apple (18.6%) and Netflix (14.7%) also highly targeted.
Most impersonated SaaS brands:
- Salesforce
- Notion.so
- Box
- 1Password
- Zoom
- Rapid7
- Marketo
- ServiceNow
- NetSuite
- Workday
Most impersonated financial services brands:
- MasterCard
- Truist Financial
- Investec
- Generali Group
- Bitcoin
- OpenSea
- Bank of America
- Binance
- Visa
- Nationwide
Most impersonated social media brands:
- YouTube
- Parler
- Discord
Most impersonated EMEA brands:
- World Health Organization
- Louis Vuitton
- Investec
- Chanel
- Generali Group
Most impersonated APAC brands:
- LINE
- JCB Global
- State Bank of India
- Toyota
- Toshiba
Most impersonated LATAM brands:
- Banco Bradesco
- Atento
- LATAM Airlines
- California Supermercados
- Locaweb
Phishing Attacks by Industry
Phishing has established itself as a primary attack vector across various industries, with 94% of organizations targeted by one or more phishing attacks in 2024. Attackers leverage phishing as a common entry point for malicious activities, consistently ranking among the top methods for initial infection, especially in sectors like manufacturing, finance, government, and transportation.
Here’s a summary of the position of phishing as an attack vector for each industry:
- Manufacturing – Phishing was the top initial infection vector, representing 39% of incidents.
- Finance and Insurance – Phishing was the most common initial infection vector, representing 28% of cases.
- Professional, Business, and Consumer Services – Phishing was the second most common initial infection vector, representing 31% of incidents.
- Energy – Phishing is not explicitly listed as a top infection vector for this industry. The primary vectors were the exploitation of public-facing applications, valid local accounts, and replication through removable media.
- Retail and Wholesale – Phishing tied for second as an infection vector, alongside exploitation of public-facing applications, each representing 29% of incidents.
- Healthcare – Phishing was the third most common infection vector, accounting for 20% of incidents.
- Government – Phishing was the top infection vector, representing 40% of incidents.
- Transportation – Phishing is the top initial infection vector, alongside the exploitation of public-facing applications, each representing 50% of incidents.
- Education – Phishing was among the top initial infection vectors, along with the use of valid accounts.
Phishing geographic trends
Phishing attacks remain particularly prominent in some areas, while different methods take the lead in others. Despite the regional variations, phishing remains a significant access method globally.
Here’s a breakdown of phishing’s rank as an initial access vector in each region in 2023:
- Europe — Phishing is tied to the use of valid accounts, each accounting for 30% of initial access methods.
- North America — Phishing ranked third as an initial access vector, making up 27% of incidents. The top two were the use of valid accounts (41%) and the exploitation of public-facing applications (32%).
- Asia-Pacific — Phishing was the top initial vector, accounting for 36% of incidents.
- Latin America — Phishing tied for second place with the use of valid accounts, each representing 22% of initial access methods.
- Middle East and Africa —Phishing was not highlighted as a top-ranked initial access method in this region. The primary access vectors were the use of valid local accounts (52%) and valid cloud accounts (48%).
Countries of origin for phishing attacks
According to the latest data, phishing attacks were primarily traced to a few key countries, with the U.S. leading as the top origin. This is due to its extensive digital infrastructure, which provides cybercriminals access to many potential victims.
Other major sources of phishing attacks included the UK, Russia, Germany, Canada, the Netherlands, Poland, China, Singapore, and Australia.
AI and Phishing Attacks
According to a 2024 study, 95% of IT leaders report that cyberattacks are now more sophisticated than ever. The study highlights that AI-powered attacks have been increasing with a 51% rise over recent years. This shift has left many IT leaders feeling vulnerable, with 35% expressing concern about their ability to counteract such attacks effectively.
Time-saving advances with AI-generated phishing
Manually crafted phishing emails take an average of 16 hours to produce. However, with AI, a deceptive phishing email can be generated in as little as 5 minutes—saving cybercriminals nearly two days per email. This efficiency leap opens up large-scale attacks with minimal time investment.
Awareness and Prevention
The median time it takes for users to fall for phishing emails is alarmingly quick, often less than 60 seconds.
According to studies, human error is a critical vulnerability, playing a role in 74% of all breaches. Despite security training, people are still likely to click on phishing links due to ingrained habits or well-crafted social engineering tactics.
Only 1 in 4 employees feel that their organizations are fully prepared for phishing threats across channels. Compounding the issue, only 29% of phishing emails are accurately reported by employees, emphasizing gaps in both awareness and detection skills.
Solutions to prevent phishing attacks
Although complete cybersecurity protection is impossible, quick detection and response can dramatically reduce the impact of breaches on organizations and their customers. Luckily, DMARC offers an essential solution to the problem.
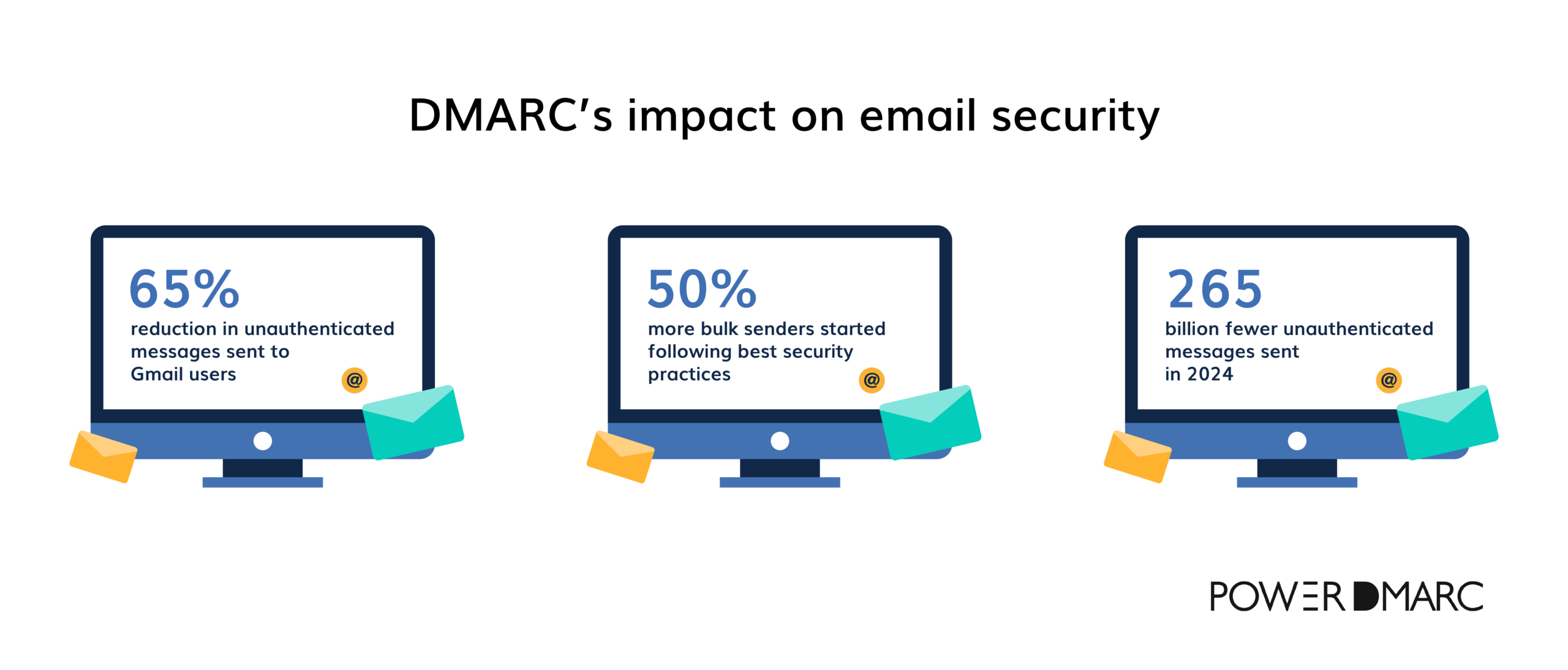
Recent DMARC statistics bring to life the impact of DMARC on email security. Since implementing new sender requirements, Gmail has witnessed a 65% reduction in unauthenticated messages delivered. This substantial decline demonstrates the effectiveness of DMARC in reducing fraudulent emails.
But it does not stop there! 50% more bulk senders have started adhering to best security practices, signaling a broader industry-wide adoption of DMARC and related protocols. Perhaps the most striking is the scale of change DMARC has brought to the global email ecosystem, with 265 billion fewer unauthenticated messages sent in 2024.
To fully grasp what DMARC is, it’s important to first understand its foundational components: SPF and DKIM.
SPF (Sender Policy Framework) is an email authentication protocol that allows domain owners to define which IP addresses are authorized to send emails on behalf of their domain.
DKIM (DomainKeys Identified Mail) works by adding a digital signature to each email. This signature ensures the integrity of the message and proves that it hasn’t been altered since it was sent from the authorized server.
DMARC builds upon both SPF and DKIM, introducing a policy layer that tells email receivers how to handle messages that fail authentication. It ensures that messages align with the domain’s authentication practices and provides a way to report any discrepancies.
Enhancing email security with MTA-STS and BIMI
While DMARC plays a crucial role in email authentication, its effectiveness is significantly enhanced when combined with additional protocols like MTA-STS (Mail Transfer Agent Strict Transport Security) and BIMI (Brand Indicators for Message Identification).
MTA-STS works by enforcing strict security policies for email transmission, ensuring that emails are transmitted over secure, encrypted channels. This eliminates the risk of emails being intercepted or tampered with during transit, adding another layer of protection.
On the other hand, BIMI provides a unique opportunity for brands to increase both email security and brand visibility. By enabling organizations to display their logos in the inbox next to authenticated emails, BIMI offers recipients a visual confirmation of legitimacy. This not only reinforces brand identity but also boosts trust with customers, ensuring that they can quickly identify authentic communications in a crowded inbox.
The challenges of manual implementation
While DMARC, MTA-STS, and BIMI offer clear benefits, manual implementation of these protocols can be complex and error-prone.
Setting up these protocols requires deep technical knowledge, especially when it comes to configuring DNS records and analyzing feedback reports. Without expert oversight, organizations risk exposing their email systems to potential threats.
Given the complexities involved, manual implementation is no longer viable for most businesses. This is where automated and managed email authentication services, such as PowerDMARC, come into play.
PowerDMARC offers streamlined solutions for setting up and maintaining DMARC, MTA-STS, and BIMI, allowing you to fully leverage these protocols without the technical burden. PowerDMARC not only simplifies deployment but also provides continuous monitoring, real-time insights, and expert support, ensuring that email security remains robust and up to date.
What makes PowerDMARC stand out?
With numerous awards, glowing testimonials, and a proven track record of success, PowerDMARC is trusted by 10,000+ customers worldwide looking to enhance their email security.
G2 has recognized PowerDMARC as a leader in DMARC software for Fall 2024, highlighting our dedication to delivering top-tier email authentication solutions.
Get in touch to make the switch to PowerDMARC today and take control of your email domain. Protect your business, build trust, and ensure your communications remain secure.

What clients are saying:

“Came for the aggregated DMARC reporting, stayed because of all the other features included!”
Drew Saum (CEO of ADI Cyber Services)

“Most comprehensive and excellent support!”
Ben Fielding, Fractional CTO

“PowerDMARC has been a game-changer for our IT team!”
Sebastián Valero Márquez, IT Manager at HispaColex Tech Consulting

“Since implementing PowerDMARC for all of our clients, it’s created a much easier process for both onboarding, monitoring, and making changes, even if we aren’t in control of the DNS services.”
Joe Burns, Co-founder and CEO of Reformed IT
Final Thoughts
Phishing is a serious and costly threat, and attacks are becoming more sophisticated, especially with AI. Unfortunately, many organizations are still not fully prepared, lagging behind on essential defenses like advanced email filters, regular employee training, and secure login protocols, leaving them vulnerable to these attacks.
One powerful step companies can take is implementing DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC helps verify that incoming emails genuinely come from the claimed sender, blocking many phishing attempts before they reach inboxes.
However, to truly stay ahead of increasingly sophisticated tactics, organizations need to adopt a multi-layered approach, combining DMARC with vigilant monitoring, ongoing threat education, and a range of security tools. A single phishing email that slips through the cracks can lead to severe consequences, so it’s critical for companies to stay alert and continuously strengthen their defenses.

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ayan Bhuiya. Read the original post at: https://powerdmarc.com/email-phishing-dmarc-statistics/
如有侵权请联系:admin#unsafe.sh