2024-11-25 21:50:14 Author: securityaffairs.com(查看原文) 阅读量:4 收藏
Malware campaign abused flawed Avast Anti-Rootkit driver
Pierluigi Paganini
November 25, 2024

Threat actors exploit an outdated Avast Anti-Rootkit driver to evade detection, disable security tools, and compromise the target systems.
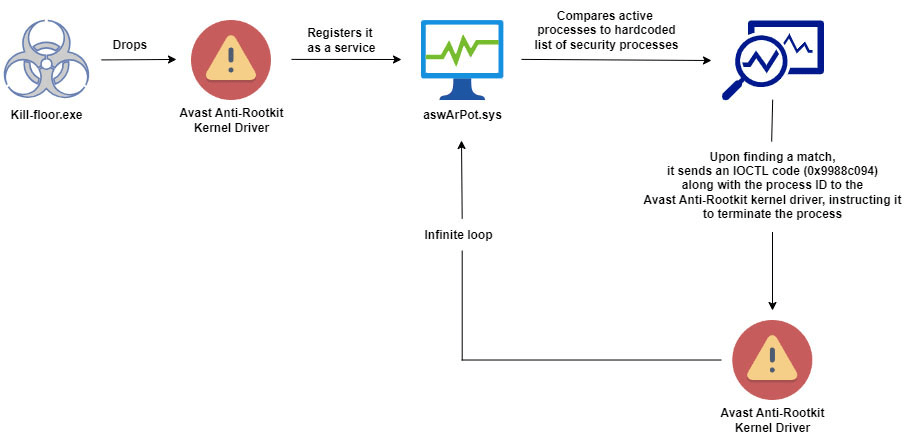
Trellix researchers uncovered a malware campaign that abused a vulnerable Avast Anti-Rootkit driver (aswArPot.sys) to gain deeper access to the target system, disable security solutions, and gain system control. This alarming tactic corrupts trusted kernel-mode drivers, transforming them into tools for terminating protective processes and compromising infected systems.
Threat actors targeted multiple products including Avast, ESET, McAfee, Microsoft Defender, SentinelOne, Sophos, and Trend Micro.
“The malware’s (kill-floor.exe) infection chain begins by dropping a legitimate Avast Anti-Rootkit driver (aswArPot.sys). The malware drops the legitimate kernel driver as ‘ntfs.bin’ in the ‘C:\Users\Default\AppData\Local\Microsoft\Windows’ directory” reads the report published by Trellix.
“Once the legitimate kernel driver is dropped, the malware uses Service Control (sc.exe) to create a service ‘aswArPot.sys’ that registers the driver for further actions. With the driver installed and running, the malware gains kernel-level access to the system, providing it with the ability to terminate critical security processes and take control of the system.”

The Avast Anti-Rootkit driver aswArPot.sys operates at the kernel level, allowing the malware to obtain unrestricted access to the operating system.
The malware includes a list of 142 hardcoded security process names associated with products from various vendors.
Organizations should implement BYOVD (Bring Your Own Vulnerable Driver) protections to protect systems from attacks using vulnerable drivers. These attacks exploit legitimate but flawed drivers to gain kernel-level access, bypassing security. Deploying expert rules to detect and block such drivers based on their unique signatures or hashes is essential.
The report includes Indicators of compromise (IoCs) for this campaign.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Anti-Rootkit driver)
如有侵权请联系:admin#unsafe.sh