Introduction
In a recent incident response case, we dealt with a variant of the Mimic ransomware with some interesting customization features. The attackers were able to connect via RDP to the victim’s server after a successful brute force attack and then launch the ransomware. After that, the adversary was able to elevate their privileges by exploiting the CVE-2020-1472 vulnerability (Zerologon).
The identified variant abuses the Everything library and provides an easy-to-use GUI for the attacker to customize the operations performed by the malware. It also has features for disabling security mechanisms and running system commands.
This ransomware variant is named “Elpaco” and contains files with extensions under the same name. In this post, we provide details about Elpaco, besides already shared, as well the tactics, techniques and procedures (TTPs) employed by the attackers.
Analysis
First look at the sample
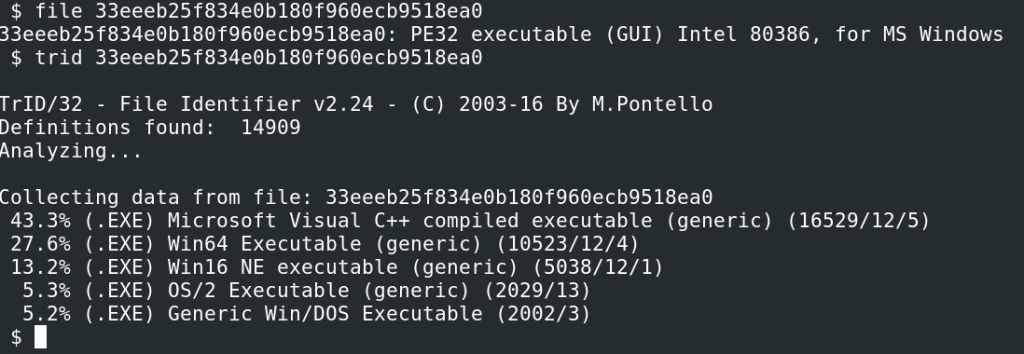
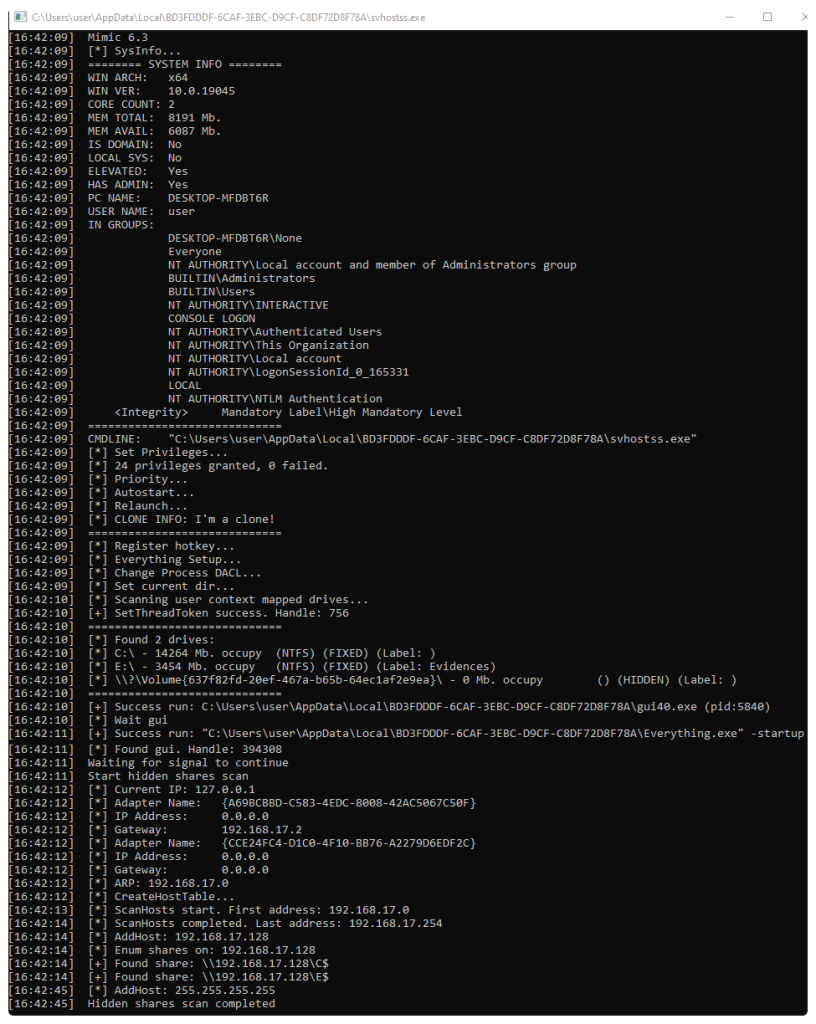
Our analysis started with a basic inspection of the sample. First, we verified its properties, such as the file type, strings and capabilities, as shown in the images below.
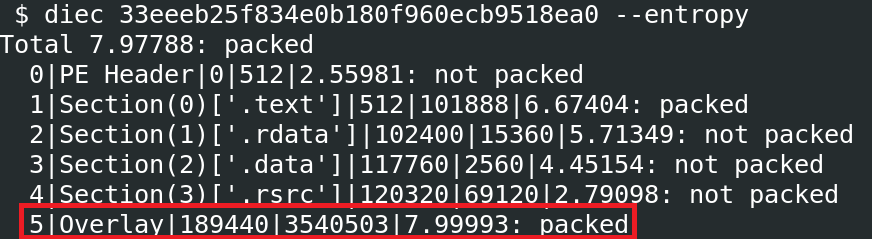
Interestingly enough, the malware used a 7-Zip installer mechanism, so it was classified as packed by most malware analysis tools and raised suspicions with detection tools.
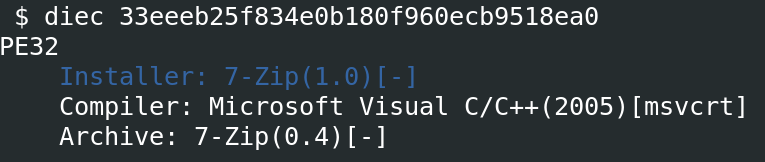
We inspected the file as a ZIP and found that the sample abused the Everything library, a legitimate filename search engine that provides fast searching and real-time updates by indexing files in Windows systems.
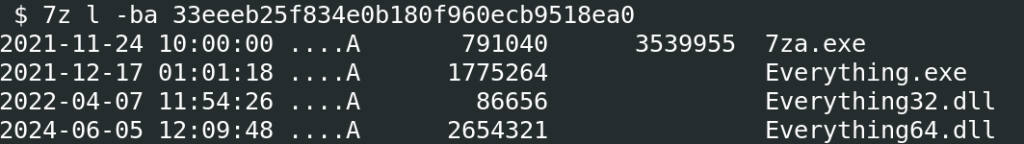
The artifact abused this library in similar ways to the Mimic ransomware discovered earlier by TrendMicro: it contained legitimate Everything applications ( Everything32.dll and Everything.exe) and a password-protected archive with malicious payloads, named Everything64.dll. The remaining file inside the archive was a legitimate 7-Zip utility for extracting the malicious archive contents. The Mimic ransomware searches for specific files using Everything APIs, encrypts user data, demands ransom payments, and exhibits sophisticated features like multi-threaded encryption to speed up the attack. Mimic also avoids detection by obfuscating its code, which makes it harder for security tools to detect and block the attack.
By analyzing Elpaco strings, we were able to identify the command used to extract the Everything64.dll file, including its password.
2e434 RunProgram="hidcon:7za.exe x -y -p7183204373585782 Everything64.dll" |
7-Zip extraction command
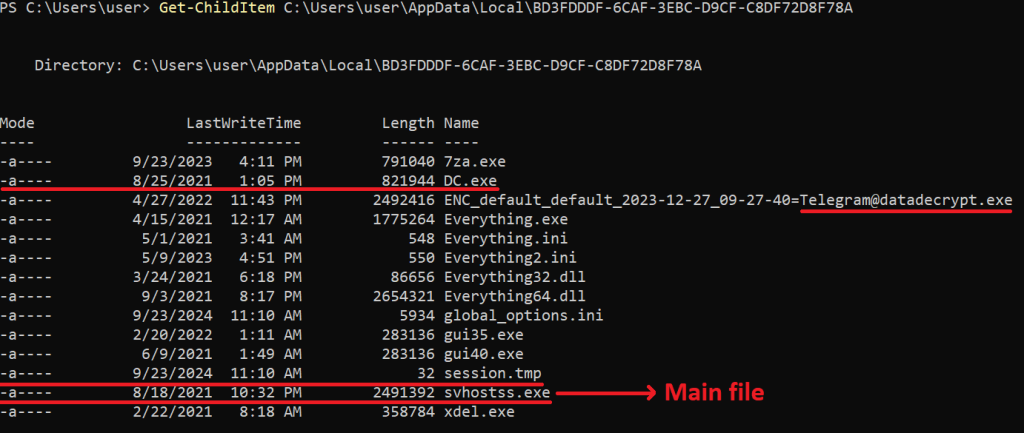
When executed, the malware unpacked the archive and dropped the necessary files into the %AppData%\Local directory, inside a separate directory with a randomly generated UUID as the name.
C:\Users\user\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\ |
Destination directory
Sample contents
The archive contents are required for encrypting files and performing additional tasks in the operating system.
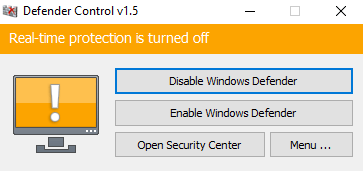
For example, the DC.exe binary is the Defender Control tool for enabling and disabling Windows Defender. It is triggered by the sample once unpacked.
The sample also drops a file called session.tmp into the same destination directory. This is a session key for resuming encryption if the malicious process is interrupted, as by a process kill.
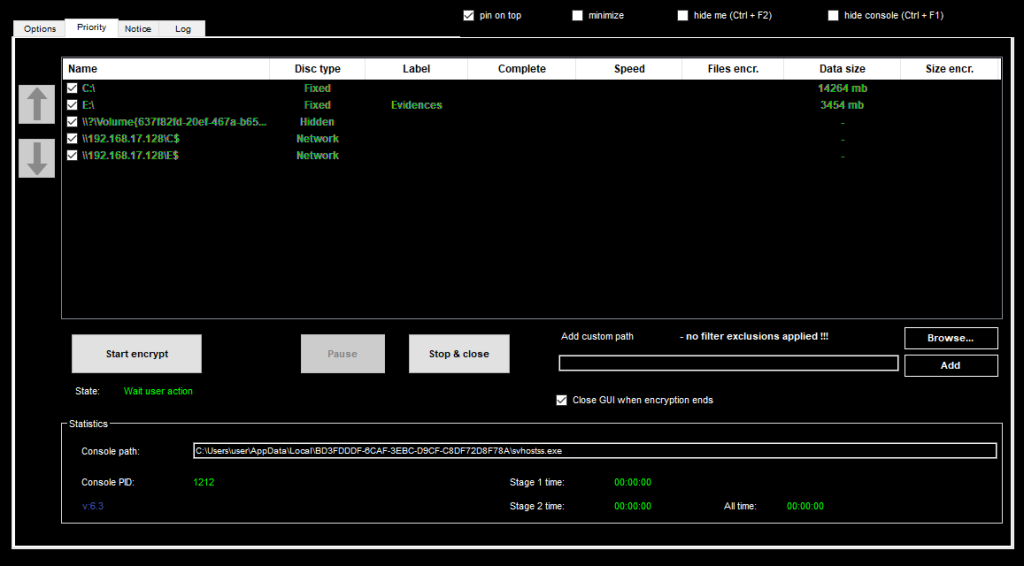
However, the most interesting artifact is svhostss.exe, which is the main console used by the malware. It is worth mentioning that this name closely mimics svchost.exe, a legitimate Windows process. This naming pattern is often used by threat actors to confuse less experienced individuals during memory analysis. The svhostss.exe file is indeed the binary that performs malicious instructions. The malware comes with a GUI under the name gui40.exe, located in the same directory. It interacts with the console and facilitates operations like customizing ransomware properties, such as a ransom note or allowed directories/files, and performing actions in the target system.
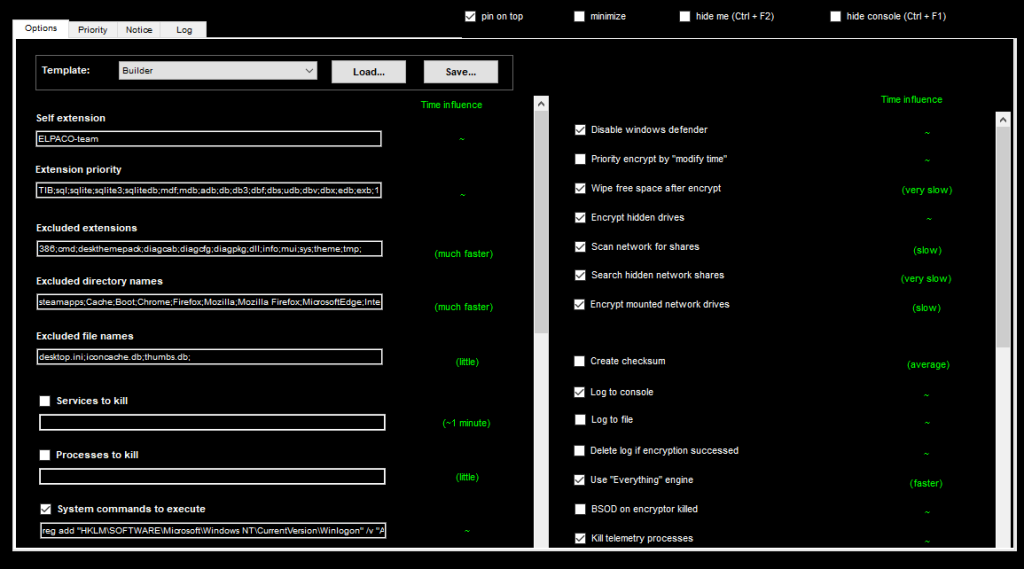
In the GUI, the operator can select entire drives for encryption, perform a process injection to hide malicious processes, customize the ransom note, change the encryption extension, set the order of encryption based on the original file format, and exclude specific directories, files or formats from encryption.
It is also possible to kill certain processes specified by the operator and execute system commands, all of which makes this threat highly customizable.
Data import and export
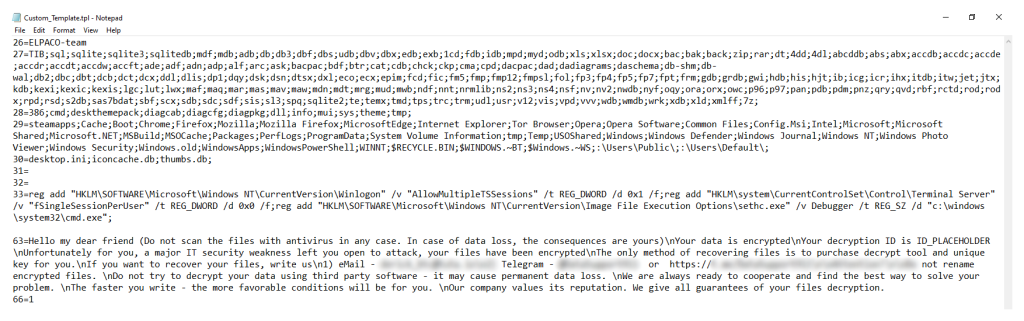
The sample allows for the import and export of malware configuration files according to the parameters set by the operator. There are several built-in templates within the malware for the operator to choose from. The image below shows an exported configuration file; note that each configuration is preceded by a number that represents its ID.
The console interface, running alongside the GUI, gathers detailed information about the system, including drives and file shares.
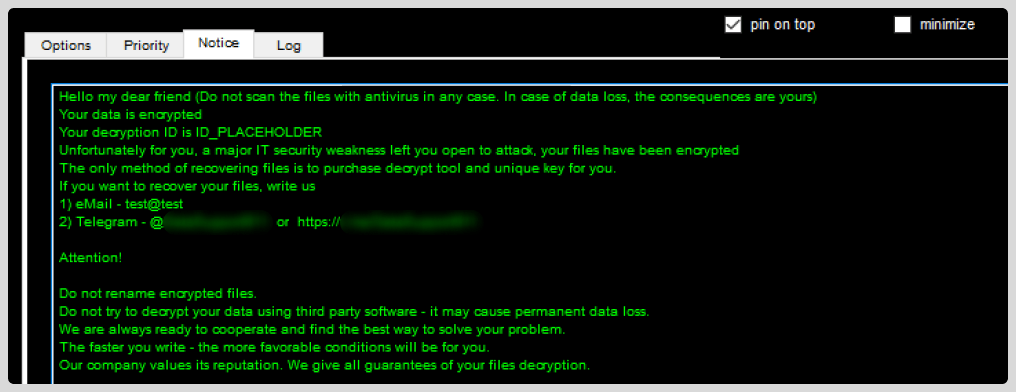
The malware creates the following registry keys — note that all files with the default .ELPACO-team extension are classified as “mimicfiles” and configured to open the ransom note ( Decryption_INFO.txt).
HKLM\SOFTWARE\Classes\.ELPACO-team\: "mimicfile" HKLM\SOFTWARE\Classes\mimicfile\shell\open\command\: "notepad.exe "C:\Users\user\AppData\Local\Decryption_INFO.txt"" |
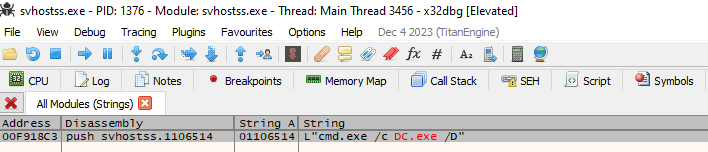
Also, the artifact configures the Run registry key to execute svhostss.exe and display the ransom note at startup.
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\svhostss: ""C:\Users\user\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF- C8DF72D8F78A\svhostss.exe"" HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\svhostss.exe: "notepad.exe "C:\Users\user\AppData\Local\Decryption_INFO.txt"" |
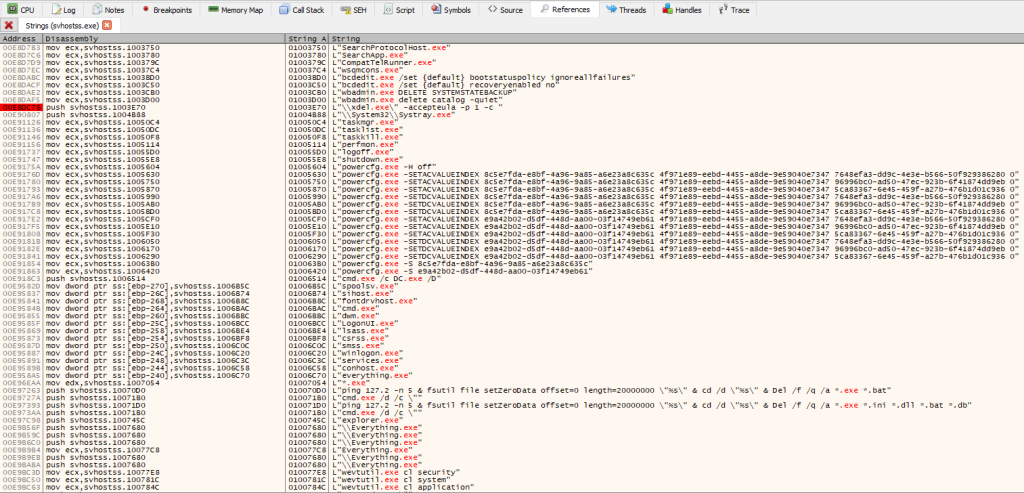
It is noteworthy that the main binary, svhostss.exe, lacks significant protection from analysis, so we were able to easily see certain command executions performed by the malware.
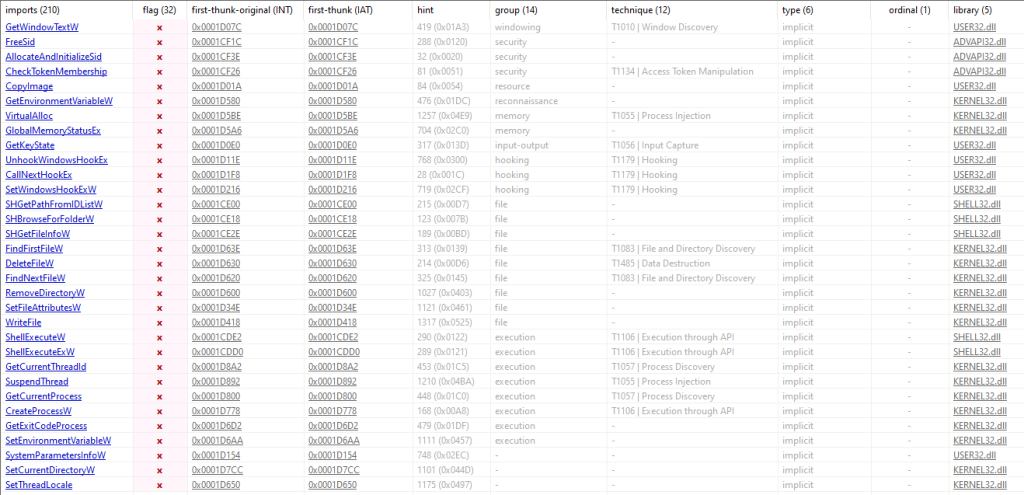
We were also able to find suspicious imports of the functions FindFirstFileW, WriteFile, FindNextFileW and ShellExecuteW. These are typically used in ransomware samples for file manipulation, while the latter is often used for calling an external program, such as PowerShell, cmd.exe or a third-party component, for deleting the malware.
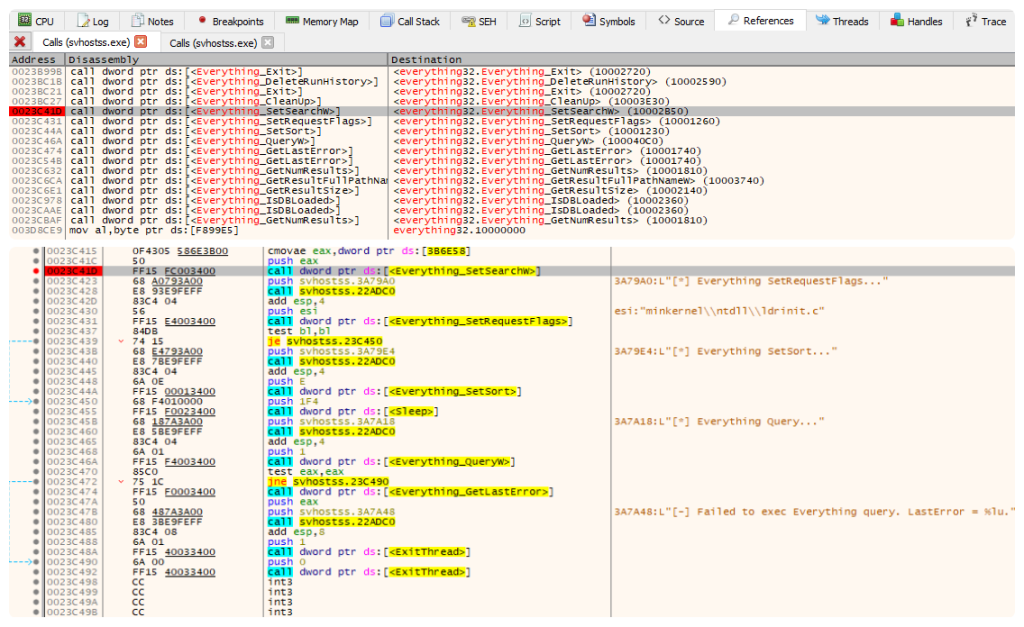
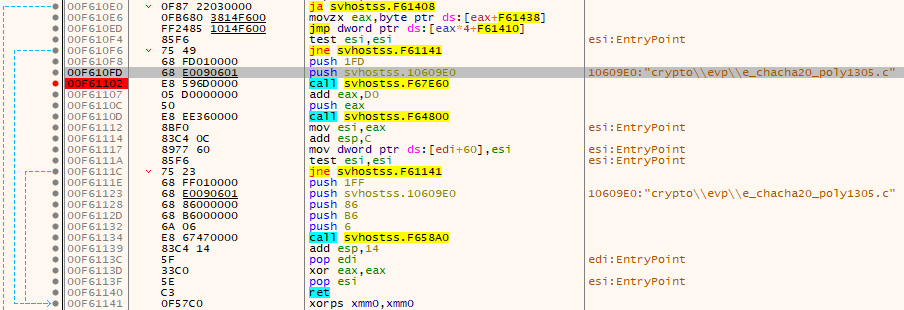
In the case of the Elpaco and Mimic variants, it uses the SetSearchW function exported from the legitimate Everything DLL to search the victim’s files, as shown in the images below. Interestingly enough, we detected no functions for data exfiltration.
Detection and analysis evasion
The artifact encrypts the victim’s files with the stream cipher ChaCha20. The key for this cipher is encrypted by the asymmetric encryption algorithm RSA-4096 — without the key we were unable to decrypt the files.
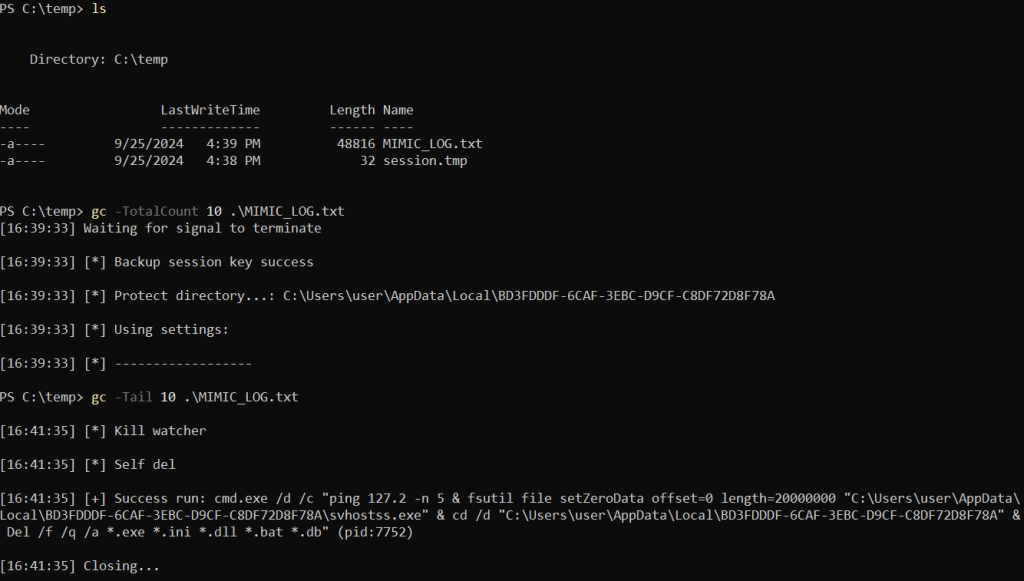
As shown in the image below, all procedures performed by the ransomware during execution are logged to C:\temp\MIMIC_LOG.txt. The artifact also drops a copy of the session.tmp key file into the same C:\temp directory.
The last step in malware execution is calling the Del command to delete all executables, configuration files, DLLs, batch files and database-related files in the ransomware directory. Interestingly enough, before deleting, the sample uses the fsutil LOLBin, as shown in the image above, to securely erase svhostss.exe file, without the possibility of its recovery.
YARA rules
Based on our analysis of the sample, we developed the following YARA rules for detecting both the dropper and the console interface used by the GUI. The rules take into account the file type, relevant strings and library imports.
Elpaco dropper:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
import "pe" rule elpaco_dropper { meta: author = "Kaspersky - GERT" description = "Yara rule for detecting the Elpaco dropper." target_entity = "file" strings: $s1 = "-p7183204373585782" wide ascii nocase $s2 = "Everything64.dll" wide ascii nocase $s3 = "ELPACO-team.exe" wide ascii nocase condition: (2 of ($s*)) and pe.imports("SHELL32.dll", "ShellExecuteW") and pe.imports("KERNEL32.dll", "LoadLibraryA") } |
svhostss.exe (console interface):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
import "pe" rule elpaco_console { meta: author = "Kaspersky - GERT" description = "Yara rule for detecting the Elpaco/Mimic main console." target_entity = "file" strings: $s1 = "powershell.exe -ExecutionPolicy Bypass" wide ascii nocase $s2 = "Software\\Classes\\mimicfile\\shell\\open\\command" wide ascii nocase $s3 = "cmd.exe /c DC.exe /D" wide ascii nocase $s4 = "MIMIC_LOG.txt" wide ascii nocase $s5 = "mimicfile" wide ascii nocase $s6 = "Everything Setup..." wide ascii nocase $s7 = "[*] Everything Query..." wide ascii nocase condition: (5 of ($s*)) and pe.imports("Everything32.dll", "Everything_SetSearchW") and pe.imports("bcrypt.dll", "BCryptGenRandom") } |
Victims
We used these YARA rules on public sources to detect threat actors who had recently used the Elpaco sample and other Mimic variants, mainly in the United States, Russia, the Netherlands, Germany and France. However, their presence was not limited to those countries, with further cases detected in Canada, Romania, South Korea, the United Kingdom and so on.
Top 5 countries targeted by Mimic (download)
The following chart shows the evolution of Mimic appearances per month.
Mimic appearances per month, 2024 (download)
The collected data shows that Mimic variants, including Elpaco, have been used by attackers at least since August 2023.
Conclusion
In this incident, we observed that the Elpaco ransomware is a Mimic variant that abused the Everything DLL, which is used for file discovery. The artifact presented an interesting user interface for customizing its attributes, while allowing the operator to export the parameters to a configuration file. Unfortunately, the encryption algorithm makes it impossible to decrypt the files on an infected machine without the private key, which makes this threat hard to deal with. Another feature of Elpaco is that it deletes itself after encrypting files to evade detection and analysis. We have observed attacks with Elpaco and other Mimic samples on a massive scale, targeting a wide range of countries worldwide, and we’ll continue monitoring this threat.
Kaspersky products detect the threat described in this article with the following verdicts:
- HEUR:Trojan-Ransom.Win32.Generic (dropper).
- HEUR:Trojan-Ransom.Win32.Mimic.gen ( svhostss.exe).
Tactics, techniques and procedures
Below are the TTPs identified from our malware analysis.
| Tactic | Technique | ID |
| Discovery | Network Share Discovery | T1135 |
| Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| Impact | Data Encrypted for Impact | T1486 |
| Impact | Service Stop | T1489 |
| Impact | Inhibit System Recovery | T1490 |
| Defense evasion | Abuse Elevation Control Mechanism: Bypass User Account Control | T1548.002 |
| Defense evasion | Masquerading | T1036 |
| Defense evasion | Modify Registry | T1112 |
| Defense evasion | Disable or Modify System Firewall | T1562.004 |
| Defense evasion | Process Injection | T1055 |
| Defense evasion | Hide Artifacts | T1564 |
| Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
Indicators of Compromise
- 61f73e692e9549ad8bc9b965e25d2da683d56dc1 (dropper)
- 8af05099986d0b105d8e38f305efe9098a9fbda6 ( svhostss.exe)
如有侵权请联系:admin#unsafe.sh