2024-11-28 00:23:29 Author: www.vmray.com(查看原文) 阅读量:2 收藏
The cybersecurity landscape is evolving at an unprecedented pace. For organizations, keeping ahead of potential threats is no longer optional—it’s a necessity. Cybercriminals are becoming more sophisticated, using advanced techniques to evade detection and exploit vulnerabilities. In this environment, security teams face mounting pressures to stay proactive and focused.
Threat intelligence tools have become indispensable allies, equipping organizations with the insights they need to identify, understand, and neutralize threats efficiently. This article will cover:
- The fundamentals and importance of threat intelligence.
- A showcase of leading threat intelligence tools, including the most cutting-edge solutions.
- Practical guidance on choosing tools tailored to your cybersecurity needs.
Let’s explore how these tools can help your team regain control in the face of escalating threats.
What Is Threat Intelligence?
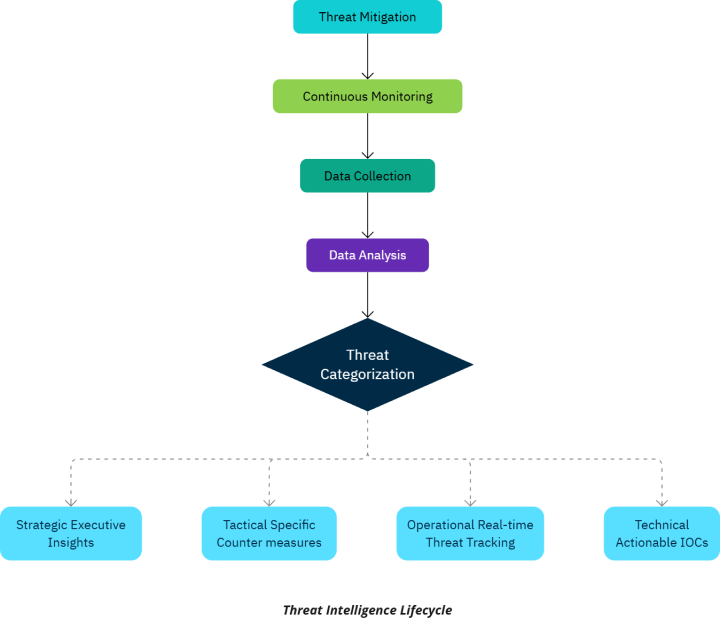
Threat intelligence refers to the process of collecting, analyzing, and applying data about potential or existing cyber threats. Its purpose is simple yet vital: to enable organizations to make informed decisions that enhance their security posture while mitigating risks.
Objectives of Threat Intelligence:
- Detecting Threats Before They Strike: Identify malicious activities and patterns before they disrupt operations.
- Minimizing Vulnerabilities: Strengthen defenses by addressing weaknesses that attackers might exploit.
- Optimizing Response Times: Enable faster, more effective reactions to security incidents to reduce potential damage.
Key Components of Threat Intelligence:
- Understanding the Threat Actors: Whether they’re cybercriminals, hacktivists, or nation-state actors, knowing the “who” behind the attack helps tailor defenses.
- Deciphering Their Methods: Insights into tactics, techniques, and procedures (TTPs) provide clues about how attackers operate.
- Recognizing Indicators of Compromise (IOCs): Spotting anomalies like unexpected file changes or unusual network activity can help identify a breach early.
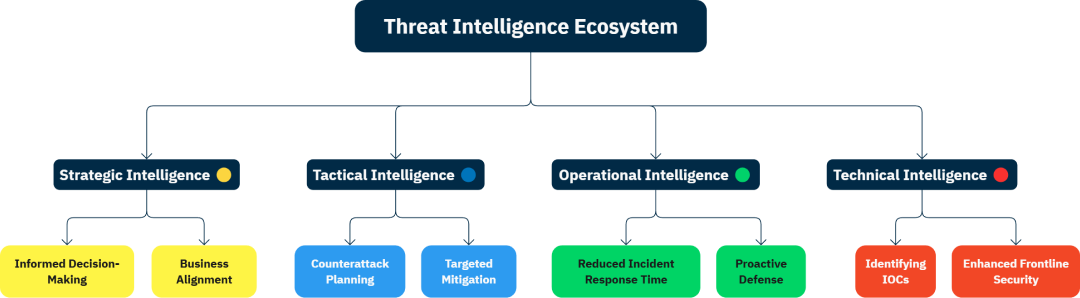
Types of Threat Intelligence:
- Strategic: High-level analysis used by executives to align cybersecurity strategies with business goals.
- Tactical: Focuses on specific attacker methods, aiding teams in deploying effective countermeasures.
- Operational: Provides real-time data on active campaigns and emerging threats for immediate action.
- Technical: Delivers raw, actionable data like IP addresses, domain names, and malware hashes to bolster frontline defenses.
Why Threat Intelligence Tools Matter
The complexity and sheer volume of today’s threats make manual processes impractical. Threat intelligence tools bridge this gap by automating the collection and analysis of vast amounts of data, allowing security teams to focus on what truly matters.
Stay Proactive: Spot Emerging Threats Early
Threat intelligence tools act as an early warning system, monitoring diverse sources of data, including:
- Dark Web Forums: Identifying chatter about planned attacks or leaked credentials.
- Social Media: Monitoring for signs of phishing campaigns or coordinated attacks.
- Industry Reports: Aggregating insights from cybersecurity research and ongoing investigations.
This proactive approach empowers organizations to:
- Anticipate Attacks: Spot patterns indicating potential threats and take preemptive measures. For example, identifying a surge in phishing attempts targeting a specific industry allows teams to deploy preventive measures like additional email filters.
- Integrate Early Warnings with Existing Systems: Tools like SIEM (Security Information and Event Management) platforms deliver real-time alerts that enable swift action.
- Prioritize Vulnerability Management: By focusing on the most dangerous vulnerabilities, teams can allocate resources more effectively, ensuring critical risks are addressed first.
Gain Insights: Understand the Broader Threat Landscape
Beyond detecting immediate threats, intelligence tools provide a broader view of the evolving threat ecosystem. This includes:
- Spotting Trends: For instance, detecting a rise in ransomware targeting healthcare institutions allows organizations in that sector to prepare accordingly.
- Benchmarking Risks: Comparing your security posture against industry peers can highlight areas for improvement and validate existing defenses.
- Enhancing Risk Assessments: Data-driven risk evaluations enable organizations to focus on the most relevant threats, ensuring that limited resources are used strategically.
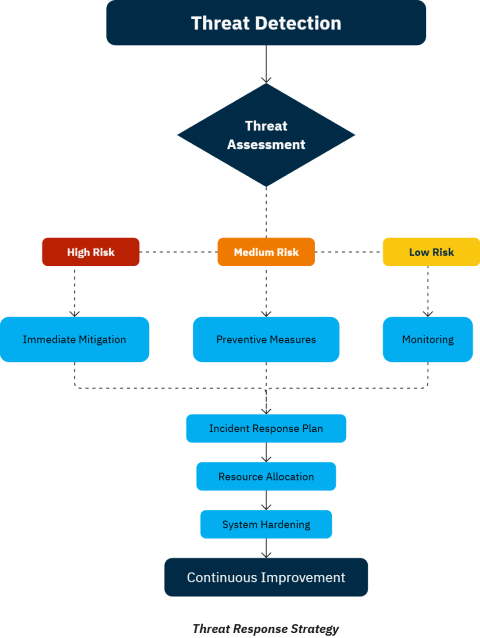
Respond Effectively: Tailor Your Countermeasures
When a threat is identified, the ability to respond effectively is critical. Threat intelligence tools provide the data needed to create precise, impactful response strategies:
- Custom Incident Response Plans: For example, knowing that a particular attacker group targets cloud-based systems allows teams to develop tailored defenses, such as enhancing access controls or patching known vulnerabilities in cloud environments.
Top Threat Intelligence Tools
To build a robust threat intelligence practice, investing in tools that deliver reliable insights and support your team’s objectives is crucial. Here’s a look at some of the top options, highlighting their unique features and value.
1. Recorded Future
A leader in predictive analytics, Recorded Future leverages AI to provide contextual and forward-looking threat intelligence.
Key Features:
- Analyzes data from both open and closed sources.
- Predicts future threats using advanced machine learning models.
- Seamlessly integrates with various security platforms.
Benefits:
- Proactive Defense: Anticipate and mitigate risks before they materialize.
- Enhanced Context: Gain deeper insights into threats with minimal information overload.
2. ThreatConnect
ThreatConnect is a collaborative platform that helps organizations centralize and automate their threat intelligence operations.
Key Features:
- Centralized intelligence management.
- Advanced automation for streamlined workflows.
- Collaboration tools for team-wide sharing of insights.
Benefits:
- Improved Readiness: Stay prepared with real-time updates.
- Team Efficiency: Foster collaboration and simplify threat management.
3. MISP (Malware Information Sharing Platform)
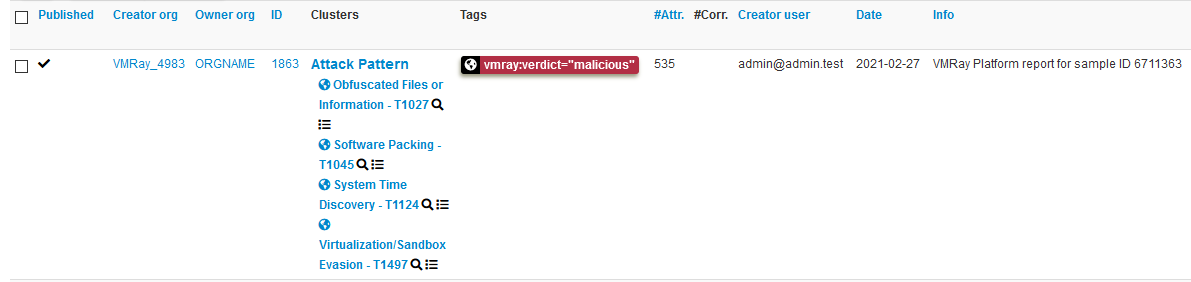
MISP is an open-source threat intelligence platform designed for sharing, storing, and correlating Indicators of Compromise (IoCs) and other critical threat intelligence data. It enables organizations to detect, prevent, and respond to attacks more effectively through collaborative sharing and automation.
Key Features:
- Comprehensive IoC Database: Store technical and non-technical details about malware, threat actors, and incidents, enabling enriched analysis and better threat detection.
- Automatic Correlation: Identifies relationships between attributes, leveraging advanced techniques like fuzzy hashing and CIDR block matching for deeper insights.
- Flexible Data Model: Link complex objects, incidents, and attributes to build comprehensive intelligence reports.
- Seamless Data Sharing: Automatically synchronize and share data with trusted groups or organizations, using granular access controls.
- Real-Time Updates: Publish-subscribe mechanisms deliver real-time notifications of new events or sightings via ZMQ or Kafka.
Benefits:
- Improved Collaboration: Share threat data effortlessly with colleagues and trusted partners, enhancing collective cybersecurity efforts.
- Streamlined Detection: Generate IDS rules, STIX exports, or CSV reports for automated import into detection systems, ensuring faster incident response.
- Efficient Analysis: Correlation capabilities highlight connections across incidents, improving attribution and understanding of TTPs.
- Scalable and Customizable: Supports manual and automated imports/exports, making it suitable for organizations of all sizes.
VMRay & MISP Integration:
VMRay seamlessly integrates with MISP to enrich threat intelligence workflows. This integration enables:
- Direct Feeds from VMRay: Automate the delivery of sandbox analysis results to MISP, providing actionable IoCs like malicious URLs, file hashes, and malware behaviors.
- Streamlined Setup: Start quickly using an install script or Docker to host the MISP feed.
- Enhanced Automation: Feed VMRay’s results into MISP workflows, enabling SOC and threat intelligence teams to act on real-time data effectively.
With MISP’s robust sharing capabilities and VMRay’s advanced analysis, organizations gain a powerful, unified approach to managing and responding to threats. Learn more about setting up the VMRay-MISP integration and transforming your threat intelligence efforts.
4. OpenCTI
OpenCTI is an open-source threat intelligence platform designed to centralize, correlate, and operationalize cyber threat intelligence for enhanced decision-making and faster incident response. It enables security teams to consolidate knowledge and streamline workflows, offering a dynamic and collaborative approach to threat detection and mitigation.
Key Features:
- Data Visualization: Provides intuitive visualizations of threat entities and their connections, enhancing investigations with dynamic knowledge graphs.
- Bi-Directional Integrations: Integrates seamlessly with third-party detection tools, allowing two-way data exchange for improved situational awareness.
- No-Code Automation: Simplifies repetitive tasks with customizable playbooks, eliminating the need for coding expertise.
- Comprehensive Case Management: Streamlines incident response with pre-defined templates, severity matrices, and centralized case tracking.
Benefits:
- Enhanced Threat Visibility: Consolidates internal and external threat data into a single source of truth, reducing false positives and false negatives.
- Faster Incident Response: Automates manual processes to improve MTTD (Mean Time to Detect) and MTTR (Mean Time to Respond).
- Improved Collaboration: Facilitates intelligence sharing with stakeholders through public dashboards, TAXII feeds, and other mechanisms.
- Operational Efficiency: Leverages graph-based visualizations and STIX relationships to pivot seamlessly between threat entities, saving analysts time.
5. TheHive
TheHive is a robust 4-in-1 Security Incident Response Platform (SIRP) designed to enhance the efficiency and collaboration of SOCs, CSIRTs, and CERTs. With advanced integration capabilities, real-time collaboration, and efficient task and evidence management, TheHive is a critical tool for modern incident response.
Key Features:
- Real-Time Collaboration: Enables simultaneous collaboration between analysts, complete with live updates on cases, tasks, and IOCs.
- Task Management: Simplifies assignment, tracking, and importing from sources like email, CTI providers, and SIEMs.
- Customizable Templates: Create tailored cases and tasks with metrics and fields for automation opportunities.
- Evidence Handling: Securely manage evidence, including password-protected files and observables.
Benefits:
- Enhanced Efficiency: Automates repetitive tasks, enabling analysts to focus on critical issues.
- Scalability: Modular architecture accommodates both single-server and complex clustered setups.
- Collaboration: Supports internal and external stakeholder collaboration with clear task visibility.
6. VMRay TotalInsight
VMRay TotalInsight is more than just a threat intelligence platform—it’s a comprehensive solution designed to empower security teams with clarity and precision.
How TotalInsight Stands Out:
- Advanced Analytics and Machine Learning: By analyzing vast amounts of data, the platform identifies trends, vulnerabilities, and emerging threats before they escalate.
- User-Centric Design: TotalInsight features an intuitive interface that simplifies threat detection and response tasks, enabling teams to focus on high-priority issues.
- Seamless Integration: TotalInsight works effortlessly with existing security tools, maximizing the value of your current investments.
Key Features:
- Comprehensive Detection: Uses sandboxing to uncover sophisticated, evasive threats.
- Tailored Intelligence: Delivers insights customized to your organization’s specific needs.
- Automation Integration: Reduces manual tasks, allowing teams to focus on strategic challenges.
Benefits:
- Proactive Defense: Stay ahead of threats by detecting and analyzing them early.
- Efficiency Boost: Streamlined workflows save time and enhance overall team performance.
- Actionable Insights: Focus on real threats without being overwhelmed by noise.
Learn more about VMRay TotalInsight.
7. VMRay ThreatFeed
VMRay ThreatFeed is a real-time intelligence solution that informs organizations about the latest threats and vulnerabilities.
Key Advantages:
- Real-Time Updates: ThreatFeed continuously delivers fresh data on emerging threats.
- IOC Integration: Security teams receive actionable indicators of compromise, enabling swift implementation of defenses.
- Threat Actor Profiles: Detailed insights into adversaries and their methods help teams anticipate future actions.
Benefits:
- Enhanced Efficiency: SOC teams can quickly prioritize and respond to critical threats.
- Precise Data: Avoid wasting time on false positives or irrelevant alerts.
Conclusion
Threat intelligence tools are no longer a luxury—they’re necessary in today’s cyber threat landscape. These tools enable organizations to sift through vast amounts of data, identify real threats, and act decisively.
VMRay’s TotalInsight and ThreatFeed stand out as essential tools for modern security teams, offering actionable intelligence and streamlined workflows to tackle even the most advanced threats. Combined with complementary solutions like Recorded Future and ThreatConnect, organizations can craft a multi-layered defense strategy tailored to their needs.
With the right tools and a proactive mindset, your organization can face the future confidently. Explore VMRay’s solutions today and discover how clarity can transform your threat intelligence approach.
如有侵权请联系:admin#unsafe.sh