2024-11-29 13:38:37 Author: isc.sans.edu(查看原文) 阅读量:0 收藏
I was asked how one can decode a bunch of BASE64 encoded IOCs with my tools.
I'm going to illustrate my method using the phishing SVG samples I found on VirusTotal (see "Increase In Phishing SVG Attachments").
In these phishing SVG files, the victim's email address is encoded in BASE64:
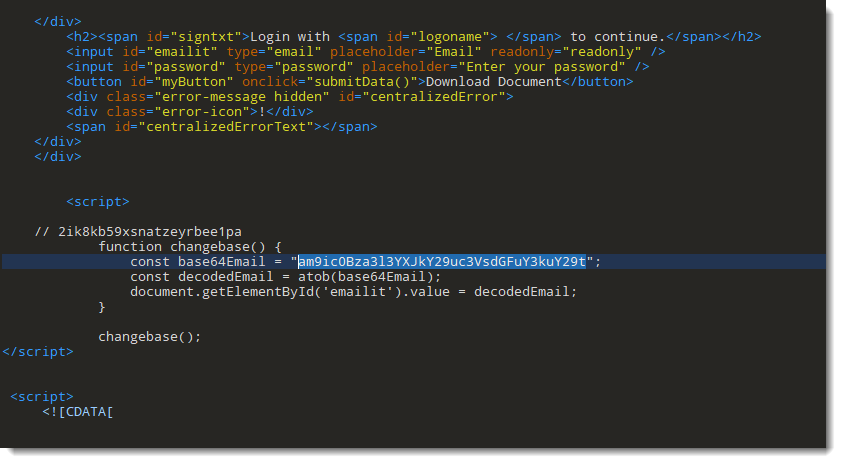
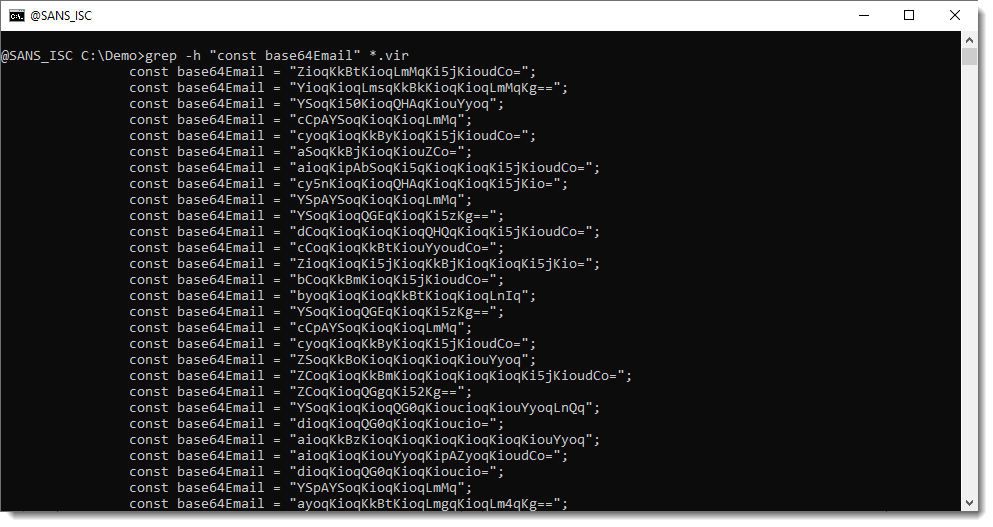
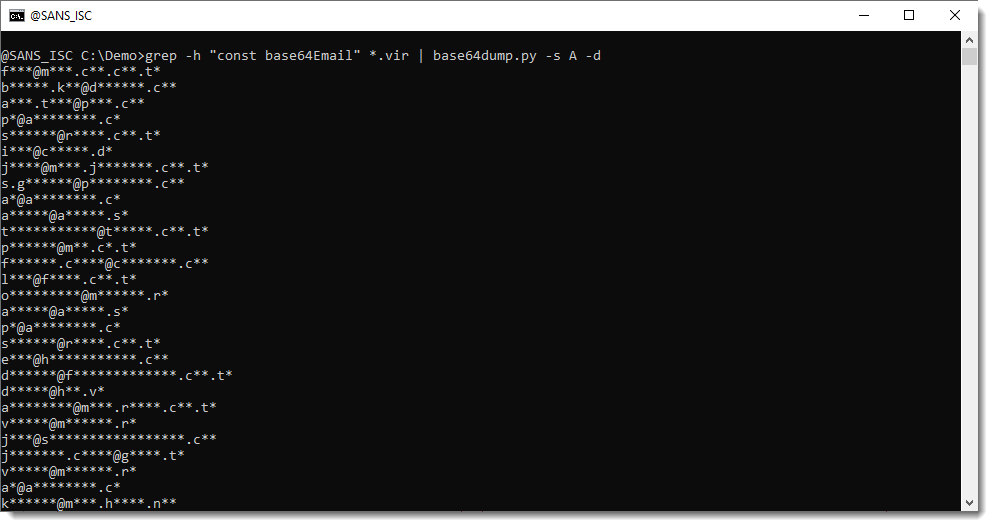
With grep, I can select all these lines with BASE64 encoded email addresses:
Then I can pipe this into base64dump.py, my tool to handle BASE64 (and other encodings):
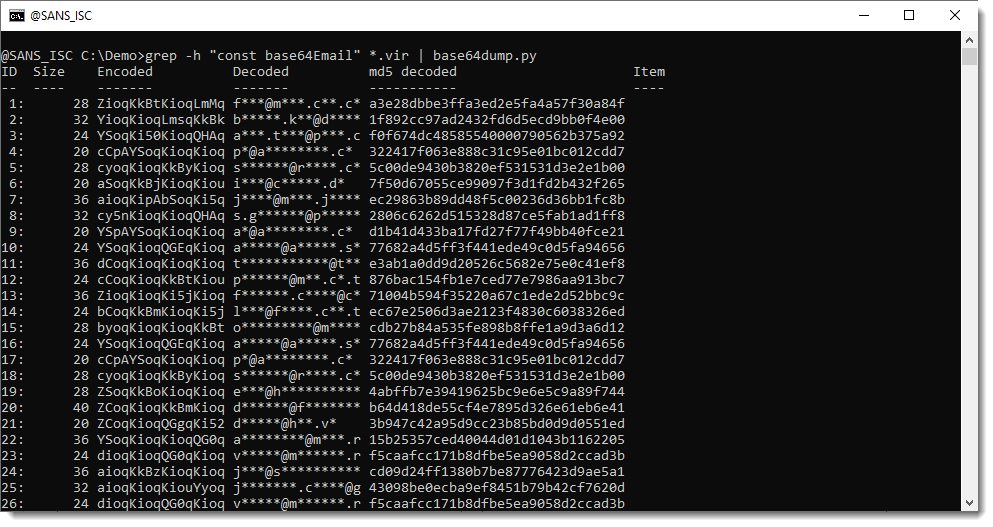
You can see the email address in the "Decoded" column (they are redacted to protect the victims).
To get just this info (decoded email addresses), you can use option -s a to select all decoded items, and option -d to dump the decoded values to stdout, like this:
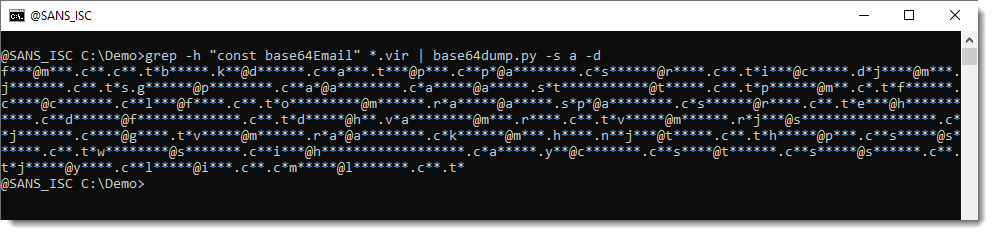
The problem now is that all email addresses are concatenated together. To add a newline (or carriage return - newline in Windows) after each email address, use option -s A (uppercase a):
Didier Stevens
Senior handler
blog.DidierStevens.com
如有侵权请联系:admin#unsafe.sh