Welcome to ANY.RUN’s monthly updates, where we give you all the details on our latest features and enhancements.
November has been a month of innovation at ANY.RUN, with major upgrades. We’ve launched Smart Content Analysis as part of Automated Interactivity, updated the home screen of TI Lookup featuring an interactive MITRE ATT&CK matrix connected with real-world samples, and expanded our detection capabilities with new YARA rules, signatures, and Suricata rules for even more comprehensive threat coverage.
Here’s everything you need to know about our November updates!
Product Updates
Automated Interactivity: Stage 2
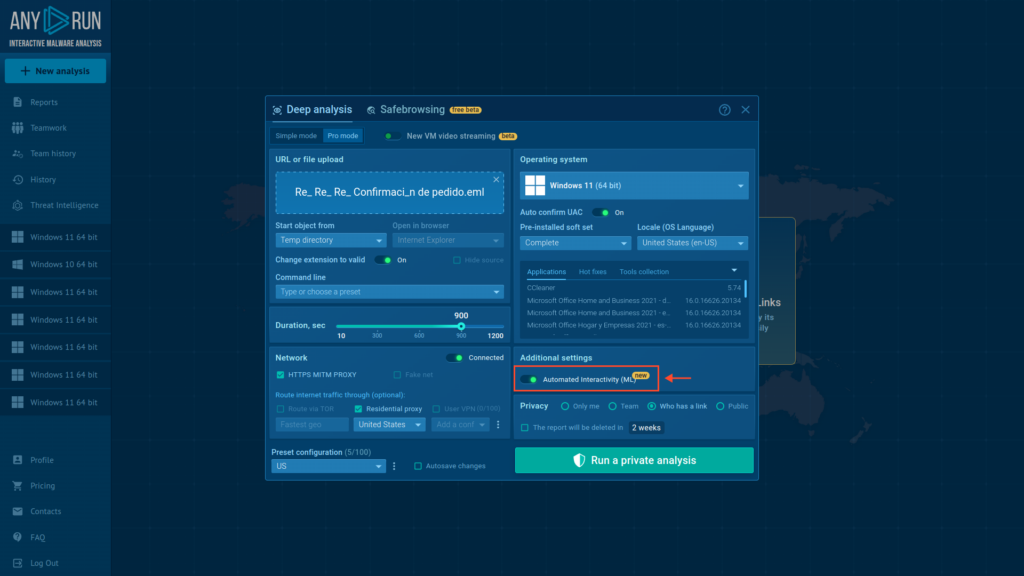
Last year, we introduced Automated Interactivity, a feature that simulates user behavior inside the ANY.RUN sandbox to automatically trigger cyberattacks. It was a game-changer, helping analysts streamline tasks like clicking buttons or solving CAPTCHA challenges.
Now, we’re thrilled to unveil Stage 2 of this feature: Smart Content Analysis, a major upgrade that offers better detection and execution of complex threats.
This update makes your security workflow more efficient by enhancing detection capabilities, automating time-consuming tasks, and simplifying complex analyses. It saves analysts valuable time, provides deeper insights, and helps teams respond to threats faster and more effectively.
What is Smart Content Analysis?
Smart Content Analysis enhances Automated Interactivity by analyzing and detonating malware and phishing attacks at every step of the kill chain. Here’s how it works:
- Identifying content: It scans for URLs, email attachments, or hidden malicious components.
- Extracting key data: This includes extracting URLs from QR codes or bypassing rewritten links from security filters.
- Simulating actions: It interacts with extracted content, such as opening links, solving CAPTCHA challenges, or launching payloads.
Automated Interactivity is available to Hunter and Enterprise-plan users and can be manually enabled in any sandbox session.
MITRE ATT&CK Techniques with Real-World Samples inside TI Lookup
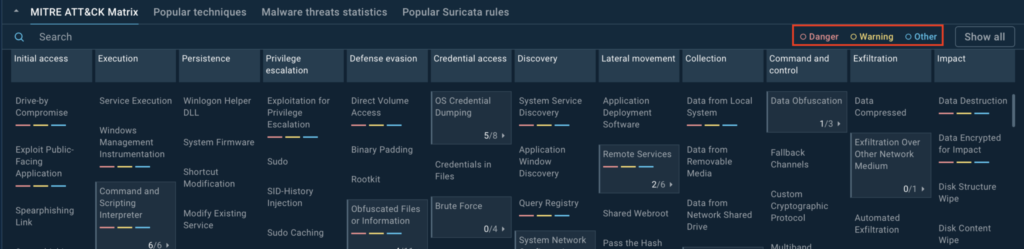
We’re thrilled to announce a major update to TI Lookup, now featuring a redesigned home screen integrated with the MITRE ATT&CK matrix. This upgrade turns the matrix into an interactive tool, bridging the gap between theoretical frameworks and practical, real-world threat analysis.
What’s new?
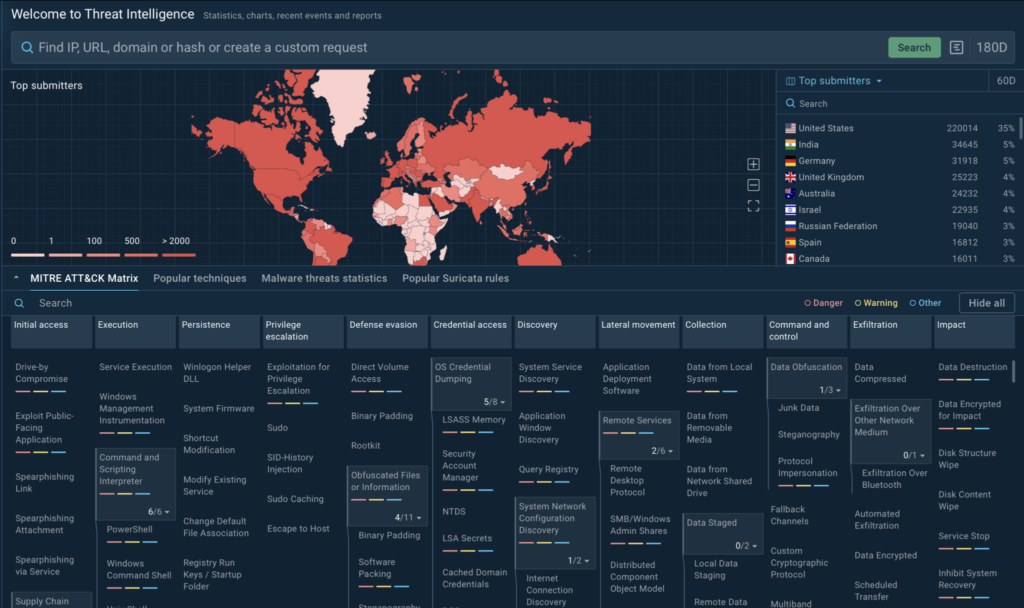
- Interactive MITRE ATT&CK matrix: All techniques and tactics are now neatly organized in a functional, actionable layout.
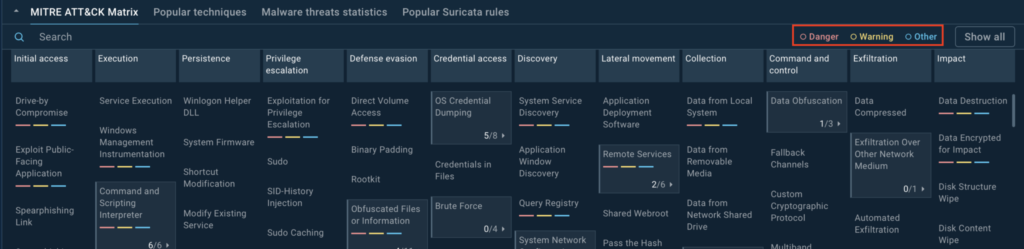
- Filtering options: Prioritize techniques by risk level—red for high risk, yellow for moderate, and blue for less urgent.
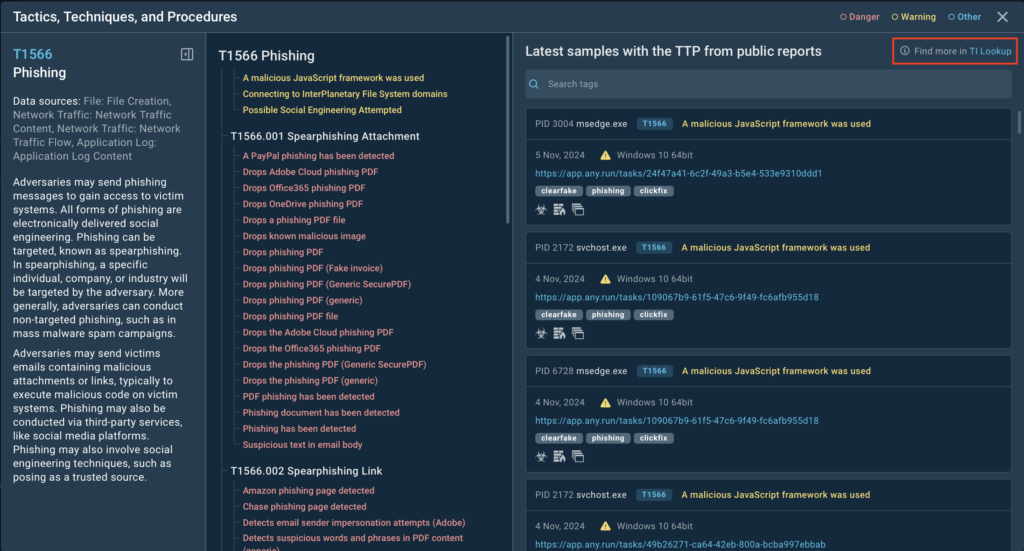
- Real-world sample connections: Click on any technique to see related malware samples and how they behave in real attacks.
Best of all, this feature is completely free and available to everyone right now. Dive into the MITRE ATT&CK matrix on TI Lookup and start exploring it today!
Threat Coverage Update
Enhanced Network Threat Detection
In November, we expanded our Suricata rule collection with an additional 7,206 rules, significantly enhancing network threat detection.
The new rules were added using domains derived directly from Public submissions, supplemented by data from TI Lookup and advanced processing logic.
Key highlights:
- Focus on threat group activity: We continue to monitor the operations of major threat groups and phishing kits, leveraging this information to enhance detection capabilities.
- Community engagement: Regular updates and insights into phishing threats are shared through our dedicated weekly post on X, helping you stay informed about the latest developments in the phishing and malware attacks.
Recent Updates in Suricata Rules
Our latest Suricata updates have focused on enhancing detection accuracy for phishing campaigns and domain-related threats. Here are some examples of the recent additions:
MassBass phishing campaign detection– A massive phishing attack that we named MassBass, has been identified and tagged in our Suricata rules:
TI Lookup: Search MassBass-related rules and insights here
CrossDomain rules detection– These Suricata rules for domains were created using data from public submissions and include “CrossDomain” in their rule names.
TI Lookup: You can explore CrossDomain-related activity and insights using our TI Lookup tool:
Search CrossDomain
New Signatures
This month, we’ve added a total of 56 new signatures to enhance our detection capabilities, covering a wide range of malicious behaviors and threats.
- Office/archive exploit: Detection of deliberately damaged files exploiting the self-repair mechanism.
- Kms tool: Identification of unauthorized kms activation tools.
- Torvil mutex: Discovery of torvil-related mutex activity.
- Cve-2024-43451: a critical vulnerability (example session).
- Untrusted certificate execution: alerting on files executed with untrusted certificates.
- Silentkill: a sophisticated malware strain identified.
- Rhysida: a ransomware strain (example session).
- Secretsdump: detection of credential-stealing activity.
- Gumen: a unique malware variant (example session).
- Badrabbit: identification of the infamous ransomware.
- Ateraagent: detection of unauthorized agent installations (example session).
- Lunam and Luna: discovery of related malware strains (example session).
- Behavioral detection of attempts to establish rdp connections using configuration files extracted from outlook emails.
- Identification of conti-based ransomware, formbook, and xworm.
- Detection of expresszip malware (example session).
Browser extension module
A new signature module for browser extensions was introduced, enabling in-depth content analysis of web pages. Besides, the following signatures were added:
- Obfuscated JavaScript.
- Fake Microsoft authentication pages.
- Email addresses embedded in URLs.
- Phishing kits such as Tycoon2fa and Mamba2fa.
New YARA Rules
This month, 9 new YARA rules were implemented, further enhancing our detection capabilities. Notable additions include:
- winPEAS detection (example session)
- rhysida YARA rule (example session)
APT Detection Update
This month, we’ve enhanced our detection capabilities against APT groups, specifically focusing on Lazarus and Rhysida. To address these threats, we’ve added 2 YARA rules and approximately 20 tailored signatures, ensuring more precise tracking and analysis of their activity.
Get Your Black Friday Deals from ANY.RUN!
Black Friday 2024 is here, and ANY.RUN has prepared exclusive time-limited offers to help you save big while enhancing your security workflow:
- Hunter Plan: Get two annual subscriptions for the price of one—perfect for individual researchers who want to collaborate.
- Enterprise Plan: Buy 5 licenses and get 2 free, or 10 licenses with 3 free plus a complimentary Threat Intelligence Lookup plan. Special renewal bonuses available!
- TI Lookup: Double your search requests with every subscription purchase.
Offers will expire on December 8th, 11:59 PM PST. Don’t miss out: secure your deal today!
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need