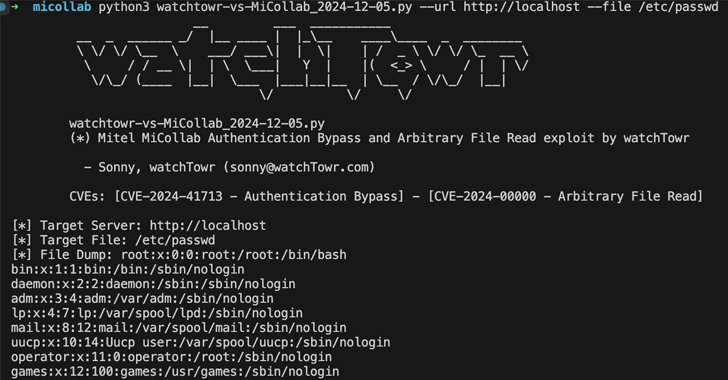
Cybersecurity researchers have released a proof-of-concept (PoC) exploit that strings together a now-patched critical security flaw impacting Mitel MiCollab with an arbitrary file read zero-day, granting an attacker the ability to access files from susceptible instances.
The critical vulnerability in question is CVE-2024-41713 (CVSS score: 9.8), which relates to a case of insufficient input validation in the NuPoint Unified Messaging (NPM) component of Mitel MiCollab that results in a path traversal attack.
MiCollab is a software and hardware solution that integrates chat, voice, video, and SMS messaging with Microsoft Teams and other applications. NPM is a server-based voicemail system, which enables users to access their voice messages through various methods, including remotely or through the Microsoft Outlook client.
WatchTowr Labs, in a report shared with The Hacker News, said it discovered CVE-2024-41713 as part of its efforts to reproduce CVE-2024-35286 (CVSS score: 9.8), another critical bug in the NPM component that could permit an attacker to access sensitive information and execute arbitrary database and management operations.
The SQL injection flaw was patched by Mitel in late May 2024 with the release of MiCollab version 9.8 SP1 (9.8.1.5).
What makes the new vulnerability notable is that it involves passing the input "..;/" in the HTTP request to the ReconcileWizard component to land the attacker in the root of the application server, thus making it possible to access sensitive information (e.g., /etc/passwd) sans authentication.
WatchTowr Labs' analysis further found that the authentication bypass could be chained with an as-yet-unpatched post-authentication arbitrary file read flaw to extract sensitive information.
"A successful exploit of this vulnerability could allow an attacker to gain unauthorized access, with potential impacts to the confidentiality, integrity, and availability of the system," Mitel said in an advisory for CVE-2024-41713.
"If the vulnerability is successfully exploited, an attacker could gain unauthenticated access to provisioning information including non-sensitive user and network information, and perform unauthorized administrative actions on the MiCollab Server."
Following responsible disclosure, CVE-2024-41713 has been plugged in MiCollab versions 9.8 SP2 (9.8.2.12) or later as of October 9, 2024.
"On a more technical level, this investigation has demonstrated some valuable lessons," security researcher Sonny Macdonald said.
"Firstly, it has acted as a real-world example that full access to the source code is not always needed – even when diving into vulnerability research to reproduce a known weakness in a COTS solution. Depending on the depth of the CVE description, some good Internet search skills can be the basis for a successful hunt for vulnerabilities."
It's worth noting that MiCollab 9.8 SP2 (9.8.2.12) also addresses a separate SQL injection vulnerability in the Audio, Web and Video Conferencing (AWV) component (CVE-2024-47223, CVSS score: 9.4) that could have severe impacts, ranging from information disclosure to execution of arbitrary database queries that could render the system inoperable.
The disclosure comes as Rapid7 detailed several security defects in the Lorex 2K Indoor Wi-Fi Security Camera (from CVE-2024-52544 through CVE-2024-52548) that could be combined to achieve remote code execution (RCE).
In a hypothetical attack scenario, the first three vulnerabilities could be utilized to reset a target device's admin password to one of the adversary's choosing, leveraging the access to view live video and audio feeds from the device, or leverage the remaining two flaws to achieve RCE with elevated privileges.
"The exploit chain consists of five distinct vulnerabilities, which operate together in two phases to achieve unauthenticated RCE," security researcher Stephen Fewer noted.
"Phase 1 performs an authentication bypass, allowing a remote unauthenticated attacker to reset the device's admin password to a password of the attacker's choosing. Phase 2 achieves remote code execution by leveraging the auth bypass in phase 1 to perform an authenticated stack-based buffer overflow and execute an operating system (OS) command with root privileges."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.