Overview
Pixm Security is excited to share our latest threat intelligence from our 500,000+ user base. This blog post covers zero-day phishing attempts we’ve blocked, key threat insights and tactics to help protect your clients. In this post, we focus on the rise of social media phishing targeting Instagram which is a blind-spot for most organizations. We also saw an uptick in spear phishing using discreet redirect tactics. More details below.
Before we dive in, here is a list of examples of phishing websites that we discovered and we recommend you update your threat intelligence with these URLs.
Phishing URLs
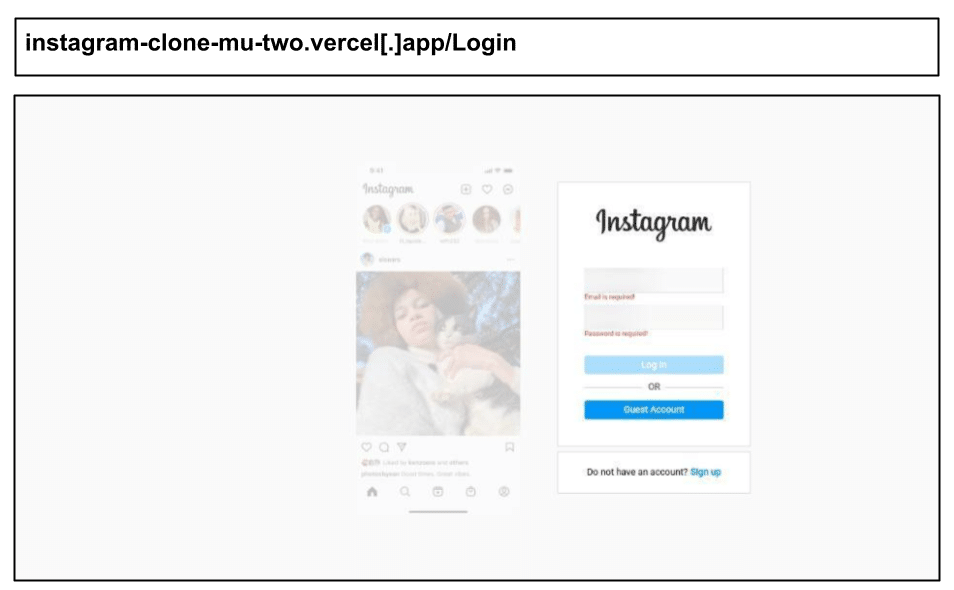
instagram-clone-mu-two.vercel[.]app/Login
scots84[.]com
sellbuyeverything[.]site
aaituljabhvani[.]org/ESEHA/index[.]php
login[.]office-link[.]click
webpage-pop-appropriations-guilty[.]trycloudflare[.]com/login.html
centrilv[.]work/[.]i2tc4mea2v/nmvujul/7222[.]cgi
naplswlwa3uhust5fr2s[.]z13[.]web[.]core[.]windows[.]net/MachelpArN047/index.html
Social Media Phishing Example
On November 15th, a phishing link impersonating Instagram was clicked 16 times in a Texas organization. Although social media access is highly restricted through content filters and firewall products at many sites, these tools do not prevent zero-day phishing links from reaching their intended users. .
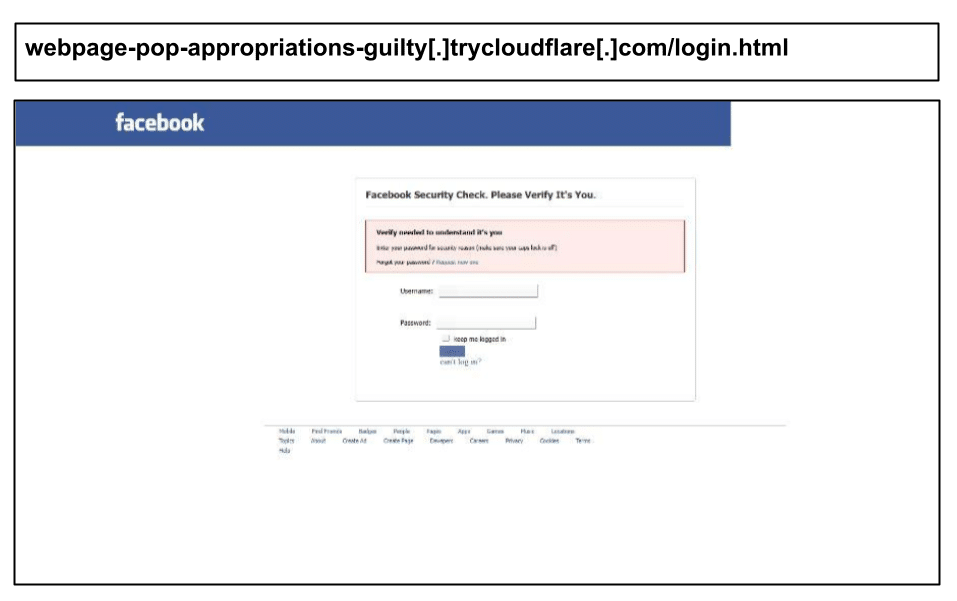
Here is an example of a Facebook phishing page clicked on November 16, mimicking Meta’s security verification process.
Not only can these phishing attempts bypass content filters, but they can also be delivered in apps like Facebook and Instagram’s native messenger apps, which are totally outside the scope of email security tools.
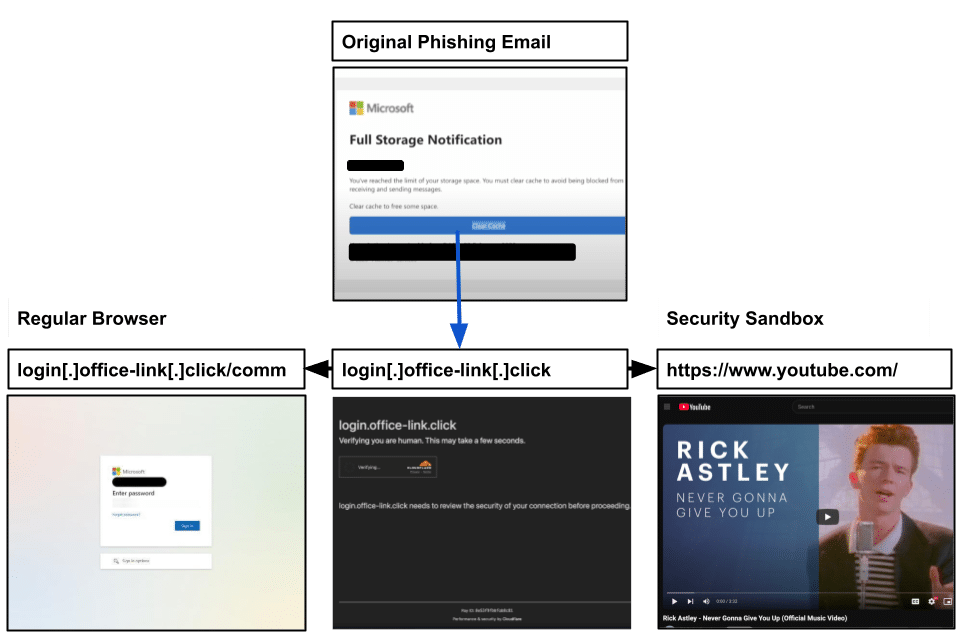
Stealth Redirect Example: Never Gonna Give You Up
A Microsoft spearphish was clicked by an employee on November 18 that exhibited stealth redirect tactics. The link initially leads to a Cloudflare Captcha to ‘verify’ the user. When an analyst opened the link in their Chrome browser, they saw the same phishing page captured by the PIXM browser extension. However, when opening the same link in a server sandbox, they were redirected to a Youtube page.
Examples like this illustrate the tools hackers routinely use to evade detection from security sandboxes embedded in email protection. First, the link requires a human action to resolve. Second, the link will only resolve the phishing attack when clicked on a user device. Simultaneously, a security sandbox is redirected to a Rick Astley music video.
We observed ongoing multi-channel phishing attacks delivered via non-email document-sharing platforms like OneDrive, specifically targeting staff members.
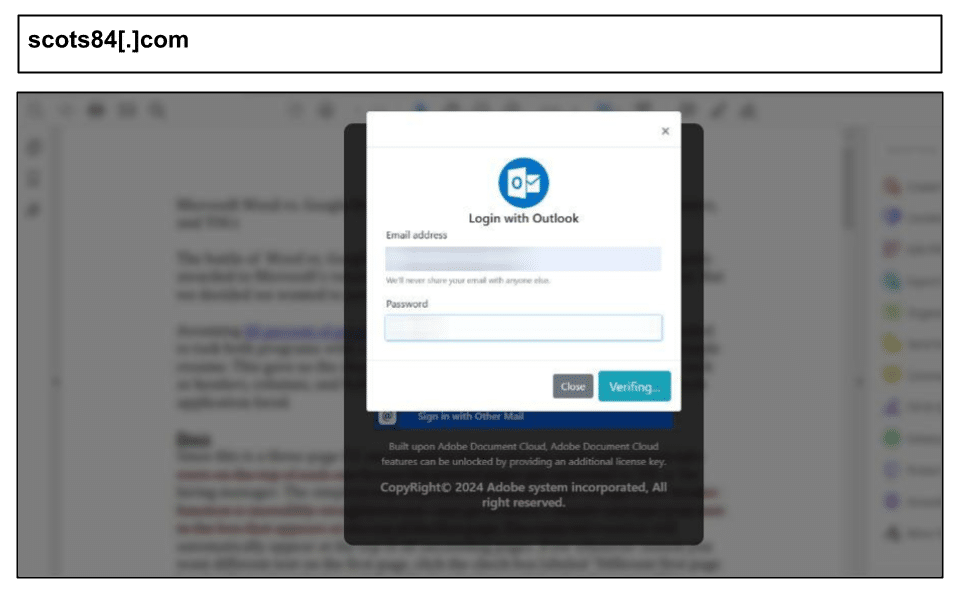
This attack had similar patterns to those observed in October targeting organizations in Texas, Colorado, and Idaho.
Suggested Actions
- Add the specified domains/URL to your block lists.
- Focus awareness efforts on high-risk credentials
- Raise awareness that 50% of phishing occurs outside the corporate mailbox
- Be aware that hackers can use stealthy tactics to conceal phishing attacks until they are opened in the browser, even with email protection
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh