As cybersecurity threats grow more sophisticated, collaboration becomes a cornerstone of effective defense strategies. This is where MISP, an open-source threat intelligence sharing platform, comes into play.
Recognizing its value, we are excited to announce the launch of our own MISP instance, enabling users to access and use indicators of compromise (IOCs) from ANY.RUN’s Threat Intelligence Feeds.
What is MISP?
MISP, which stands for Malware Information Sharing Platform, is a free, open-source platform designed to facilitate the exchange, storage, and correlation of threat intelligence data. MISP lets organizations and researchers:
- Exchange critical data points to identify cyber threats.
- Share signals or attributes indicating the compromise of information systems.
- Automate the process of data sharing and find correlations between threat data.
Benefits of ANY.RUN’s MISP Instance
With ANY.RUN’s MISP instance, you can:
1. Access ANY.RUN’s TI Feeds
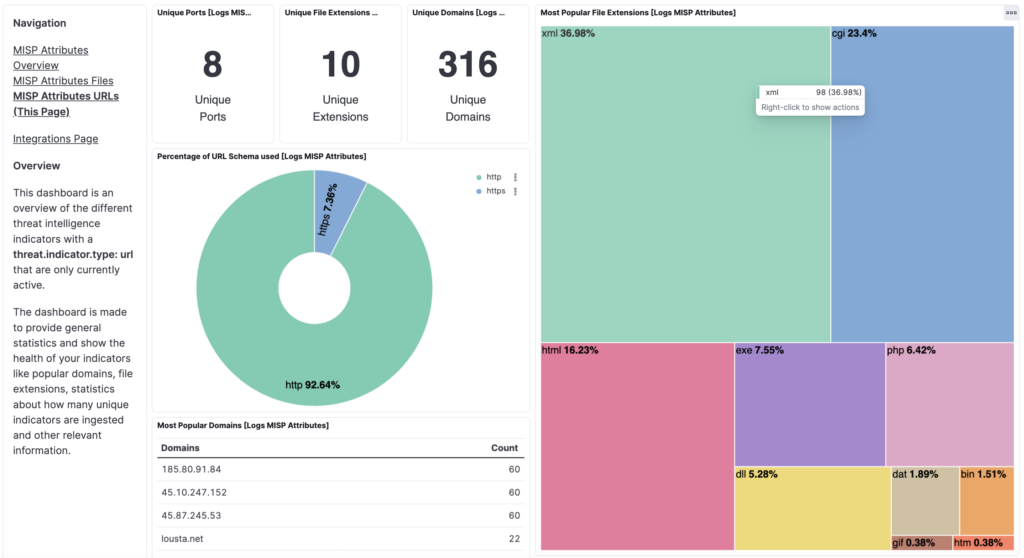
Receive a direct stream of the latest malicious IPs, URLs, domains, ports, file names, and hashes. These are extracted from public malware and phishing samples, including ones not found elsewhere, submitted and analyzed in ANY.RUN’s Interactive Sandbox by security professionals worldwide. IOCs are pulled from different sources, including network activities and malware configurations.
2. Integrate It with Your Security Tools via API
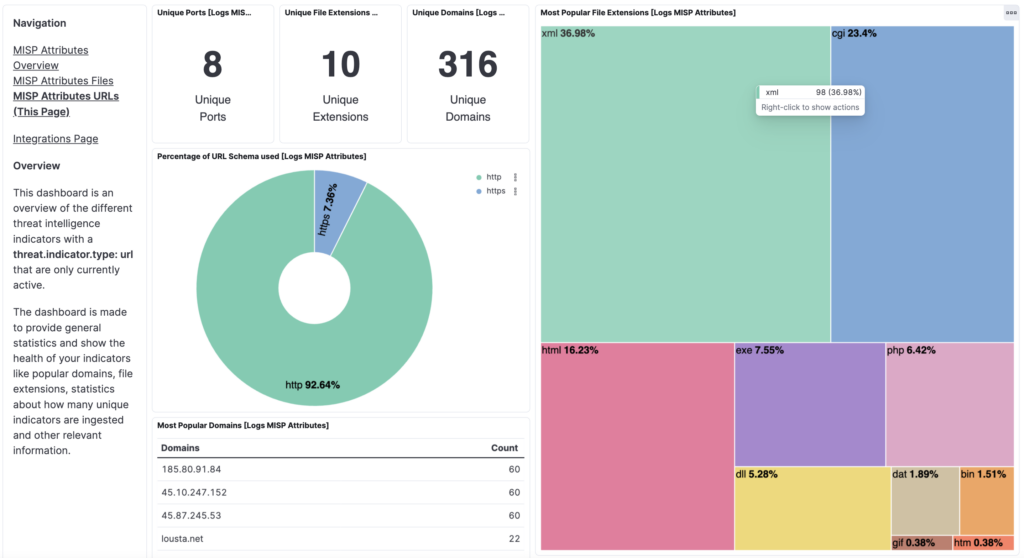
Connect your own monitoring and triage tools and systems, such as SIEM/XDR solutions, to ANY.RUN’s MISP instance via API.
3. Improve Threat Detection
Correlate and enrich your IOCs with ANY.RUN’s to develop a more comprehensive understanding of the threat landscape.
4. Generate IDS Rules
Export indicators (attributes) from ANY.RUN’s MISP instance in NIDS-compatible formats and import them in your detection tools like IDS/IPS or NGFW to improve network security of your organization and ensure proactive defense against current threats.
5. Create Custom Workflows
Leverage ANY.RUN’s indicators in your automated threat analysis workflows.
6. Synchronize MISP Instances
Synchronize your MISP instance with ANY.RUN’s to get relevant threat data.
7. Visualize Threat Intelligence Data
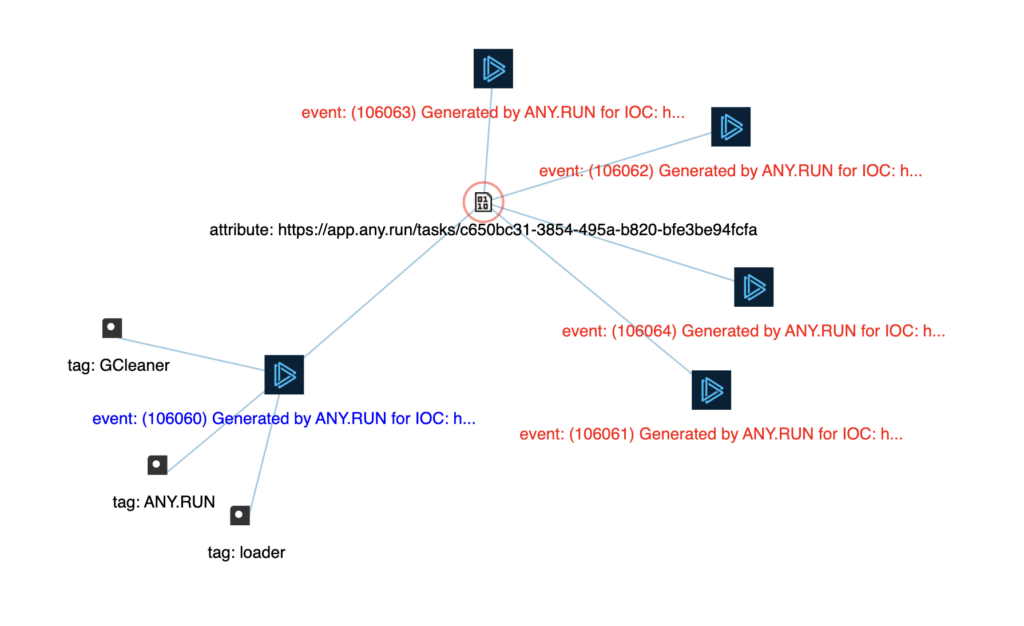
Ensure a more convenient view of relevant threats by visualizing ANY.RUN’s TI Feeds data.
8. Enrich with Your Threat Data
Add your IOCs to the ones provided by ANY.RUN to gain a better picture of the threats at hand.
How to Integrate with ANY.RUN’s MISP Instance
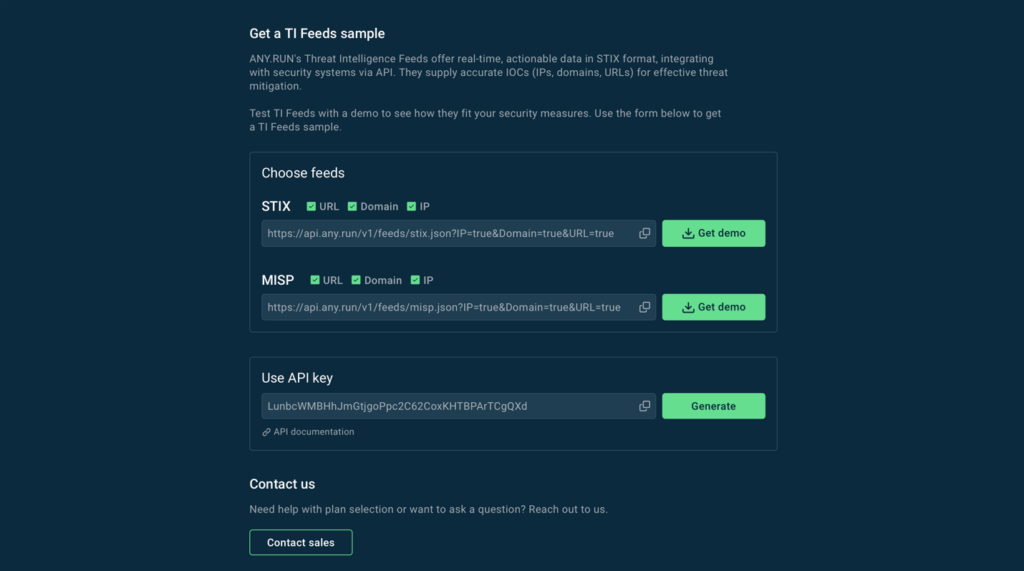
To get started with ANY.RUN’s MISP instance, simply contact our team via this page.
You can test MISP feeds by getting a free demo sample here.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s Threat Intelligence service →