2024-12-16 00:1:0 Author: mp.weixin.qq.com(查看原文) 阅读量:4 收藏
自上篇文章〔L4LB四层负载均衡IP伪造漏洞〕以来,已经快四五个月没更新,不是笔者太懒,而是实在太忙了,忙得连放屁的时间都没有。得益于社区朋友的贡献,增加了一些新特性,今天来分享给大家。
eCapture v0.9.0版本发布
新功能: 支持Docker镜像拉取,添加对 OpenSSL 3.4.0 的支持,支持 gnutls 的 keylog 和 pcap 模式,允许捕获 IPv6 数据包,拆分日志记录器。 错误修复: 修复了多个系统和功能的关键错误,包括在 Ubuntu 24.04 上的初始化脚本问题和 arm64 版本的兼容性问题。 改进: 更新了日志记录器,优化了构建过程,添加了新的工作流和文档更新。
科普:eCapture是什么
eCapture旁观者[1]是一个无需CA证书,无侵入的HTTPS/TLS明文抓包工具。可以在Linux 4.18以上版本使用,同时也支持Android arm64 5.5以上版本。项目发布三年累计14000颗星。
功能介绍
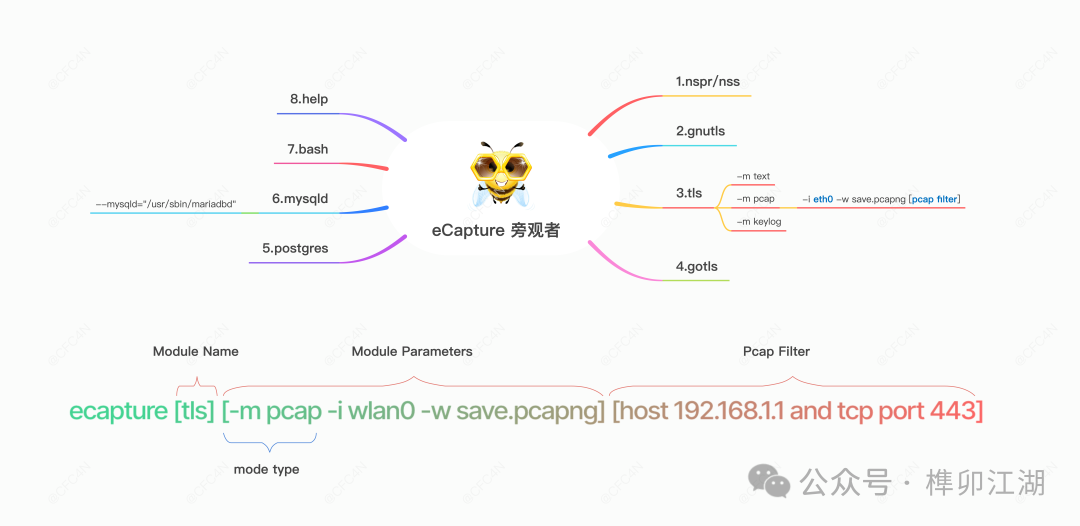
eCapture 有8个模块,分别支持openssl/gnutls/nspr/boringssl/gotls等类库的TLS/SSL加密类库的明文捕获、Bash、Mysql、PostGres软件审计。
bash 捕获bash、zsh命令行的输入输出 gnutls 捕获基于gnutls类库加密通讯的明文内容 gotls 捕获使用Golang语言编写的,基于内置crypt类库实现TLS/HTTPS加密通讯的明文内容 mysqld 捕获Mysqld的SQL查询,适用于数据库审计场景,支持Mysqld 5.6/5.7/8.0等 nss 捕获基于nss类库加密通讯的明文内容 postgres 支持postgres 10+的数据库审计,捕获查询语句 tls 捕获基于Openssl/Boringssl的加密通讯的明文内容,支持Openssl 1.0.x/1.1.x/3.x系列所有版本,支持BoringSSL所有发行版本
你可以通过ecapture -h来查看这些自命令列表。
重大更新
支持Docker Image镜像启动,可以到Docker Hub下载。 支持 gnutls模块的keylog和pcap模式对Gnutls TLS[2]类库的密钥捕获、pcapNG格式文件存储;支持文本模式 -m text下,HTTP 2.0的内容解码;支持IPv6 协议的网络包捕获; 支持非Android的boringSSL库加密通讯的明文、密钥、pcapNG捕获; 支持Zsh Shell[3]的命令执行安全审计; 支持OpenSSL模块的文本模式下,五元组关联数据; 增加eCapture项目的国内下载地址:https://ecapture.cc/zh/download/[4] (自费CDN小水管,各位黑客大哥别把我账号刷欠费了 
 )
)
Gnutls TLS类库捕获
在eCapture的gnutls模块中,新增TLS加密通讯的密钥捕获,以及保存为pcapNG格式文件。
目标进程类库确认
以使用gnutls类库的git命令为例,当执行git pull时,会调用git-remote-http程序来访问远程仓库,该程序使用Gnutls类库
ldd /usr/lib/git-core/git-remote-http
linux-vdso.so.1 (0x0000ffff9c6ff000)
libcurl-gnutls.so.4 => /lib/aarch64-linux-gnu/libcurl-gnutls.so.4 (0x0000ffff9c550000)
libpcre2-8.so.0 => /lib/aarch64-linux-gnu/libpcre2-8.so.0 (0x0000ffff9c4b0000)
...
演示过程
完整演示如下:
首先,在终端中启动ecapture
sudo ecapture gnutls -m pcapng -i ens160 -w gnutls-github.pcapng tcp port 443
之后,在另外一个终端拉取git仓库
git pull
演示结果
eCapture的结果输出:
sudo ecapture gnutls -m pcapng -i ens160 -w gnutls-github.pcapng tcp port 443
2024-12-15T13:31:38Z INF AppName="eCapture(旁观者)"
2024-12-15T13:31:38Z INF HomePage=https://ecapture.cc
2024-12-15T13:31:38Z INF Repository=https://github.com/gojue/ecapture
2024-12-15T13:31:38Z INF Author="CFC4N <[email protected]>"
2024-12-15T13:31:38Z INF Description="Capturing SSL/TLS plaintext without a CA certificate using eBPF. Supported on Linux/Android kernels for amd64/arm64."
2024-12-15T13:31:38Z INF Version=linux_arm64:v0.9.0:6.5.0-1025-azure
2024-12-15T13:31:38Z INF Listen=localhost:28256
2024-12-15T13:31:38Z INF eCapture running logs logger=
2024-12-15T13:31:38Z INF the file handler that receives the captured event eventCollector=
2024-12-15T13:31:38Z INF listen=localhost:28256
2024-12-15T13:31:38Z INF https server starting...You can upgrade the configuration file via the HTTP interface.
2024-12-15T13:31:38Z INF Kernel Info=5.15.167 Pid=150461
2024-12-15T13:31:38Z INF BTF bytecode mode: CORE. btfMode=0
2024-12-15T13:31:38Z INF GnuTlsProbe init eBPFProgramType=PcapNG model=PcapNG
2024-12-15T13:31:38Z INF module initialization. isReload=false moduleName=EBPFProbeGNUTLS
2024-12-15T13:31:38Z INF Module.Run()
2024-12-15T13:31:38Z INF GnuTLS version found Version=3.7.3
2024-12-15T13:31:38Z INF GnuTLS binary path binaryPath=/lib/aarch64-linux-gnu/libgnutls.so.30 elfType=2
2024-12-15T13:31:38Z INF BPF bytecode loaded bytecode filename=user/bytecode/gnutls_3_7_3_kern_core.o
2024-12-15T13:31:38Z INF Hook type: Gnutls elf ElfType=2 IFindex=2 IFname=ens160 PcapFilter="tcp port 443" binrayPath=/lib/aarch64-linux-gnu/libgnutls.so.30
2024-12-15T13:31:38Z INF Hook masterKey function: gnutls_handshake
2024-12-15T13:31:38Z INF target all process.
2024-12-15T13:31:38Z INF packets saved into pcapng file. pcapng path=/home/cfc4n/gnutls-github.pcapng
2024-12-15T13:31:39Z INF perfEventReader created mapSize(MB)=4
2024-12-15T13:31:39Z INF perfEventReader created mapSize(MB)=4
2024-12-15T13:31:39Z INF module started successfully. isReload=false moduleName=EBPFProbeGNUTLS
2024-12-15T13:31:43Z INF CLIENT_RANDOM save success ClientRandom=8517a6741b2a67369079309c2eac84094aacecef39a5514c6da25da7e219401d TlsVersion=GNUTLS_TLS1_3 eBPFProgramType=PcapNG
2024-12-15T13:31:44Z INF packets saved into pcapng file. count=35
2024-12-15T13:31:46Z INF packets saved into pcapng file. count=2
^C2024-12-15T13:32:15Z INF packets saved into pcapng file. count=37
2024-12-15T13:32:15Z INF Module closed,message recived from Context
2024-12-15T13:32:15Z INF iModule module close
2024-12-15T13:32:15Z INF bye bye.
可以清楚得看到TLS通讯协议是GNUTLS_TLS1_3,密钥的ClientRandom是8517a6741b2a67369079309c2eac84094aacecef39a5514c6da25da7e219401d。
Wirehark查看网络包
如图,不光能看到网络包对应发起的进程信息,还能看到HTTPS的明文内容。
Docker Hub
eCapture的Docker Hub仓库地址为:https://hub.docker.com/r/gojue/ecapture[5] ,当前最新版为 v0.9.0 。
# 拉取镜像
docker pull gojue/ecapture:latest
# 运行
docker run --rm --privileged=true --net=host -v ${宿主机文件路径}:${容器内路径} gojue/ecapture ARGS
Zsh Shell审计
启动命令sudo ecapture zsh,即可捕获zsh上运行的所有命令,对于安全审计场景,还是比较方便快捷的。
其他更多功能,请查看项目变更日志。
变更日志
功能
feat: 在 gnutls 中支持 keylog 和 pcap 模式 feat: 移除 tcp 数据包限制 kern: 支持 openssl 最新版本(3.4.0, 1.1.1w 等) feat: 以文本模式解析 http2 数据 feat: 允许捕获 ipv6 数据包 kern: 在 ebpf TC hook 中支持 uid/pid 过滤 user: 拆分记录器,将其分为记录器和事件收集器 kern: 添加对非 Android boringssl 库的支持 kern: 调整密钥获取的时机,以区分 TLS feat: 支持捕获 zsh 命令 feat: 用远程地址信息丰富地址信息 feat: 支持新版本检测功能
Bug 修复
builder: 修复 init 脚本在 ubuntu 24.04 系统上无法运行的问题 #667 修复 uprobe 类型 hook 的参数错误问题 修复 arm64 版本无法工作的 bug (#649) builder: docerk 构建错误:未找到头文件 修复 Golang TLS 模块中读取函数返回值的问题 fix: 修复在调试模式下 make 时未声明标识符的错误 fix: 回退到默认版本并发出警告 fix: 创建 output.log 失败 pkg: 修复在关闭的通道上发送数据的问题 fix: HEAD 请求中的 DumpResponse 错误 fix: 截断的主体转储错误 user: 修复 #553, hashLen不允许超过 64 字节android 版本编译失败 user: 修复 #542,masterkey 被多次写入 pcapng fix: pcap 过滤器未按预期工作 fix: 修复 ecapture Docker镜像CVE-2024-24790[6]fix: 处理器打印 incoming chan is full并退出
改进
cli: 使用格式化记录器 rs/zerologchore: 在构建过程中使用 -tags 'netgo'以避免由于不同 Linux 发行版中的 glibc 版本不同而导致的 SIGSEGV常量参数通知 cli: 更新 docker 使用说明 添加可能的 Linux 内核配置路径 user: 在 gotls 模块中格式化 clientRandom字符串cli: 支持记录器级别 使用 kprobe/__sys_connect替代uprobe/connectmakefile: 优化内核头文件的生成机制 添加 dockerfile BPF 名称应在 _core/_noncore后附加user: 为面向服务的架构做准备 docs: 修复日语翻译 chore: 在 rpmBuild.spec中移除未使用的标志BuildRequiresworkflows: 更新 Linux 源 tgz 文件版本 build(deps): 将 golang.org/x/crypto从 0.23.0 升级到 0.31.0feat: 检测 CAP_BPF pkg: 添加 http2 请求/响应单元测试 feat: 在销毁 socket 时清理映射 user: 调整内核版本显示的时机,避免过低
感谢
感谢社区小伙伴的贡献:Leon Hwang[7]、SenberHu[8]、yuweizzz[9]、sancppp[10]、Nadeshiko Manju[11]、行旅途[12]、w568w[13] 等,一起继续为爱发电。
eCapture旁观者:https://ecapture.cc
[2]Gnutls TLS:https://gnutls.org/
[3]Zsh Shell:https://www.zsh.org/
[4]https://ecapture.cc/zh/download/:https://ecapture.cc/zh/download/
[5]https://hub.docker.com/r/gojue/ecapture:https://hub.docker.com/r/gojue/ecapture
[6]CVE-2024-24790:https://github.com/advisories/GHSA-49gw-vxvf-fc2g
[7]Leon Hwang:https://github.com/asphaltt
[8]SenberHu:https://github.com/senberhu
[9]yuweizzz:https://github.com/yuweizzz
[10]sancppp:https://github.com/sancppp
[11]Nadeshiko Manju:https://github.com/Zheaoli
[12]行旅途:https://github.com/xxxxxliil
[13]w568w:https://github.com/w568w
如有侵权请联系:admin#unsafe.sh