2024-12-24 10:30:46 Author: cyble.com(查看原文) 阅读量:5 收藏
Overview
Cyble’s December 19 IT vulnerability report to clients highlighted nine vulnerabilities at high risk of attack, including five under active discussion on dark web forums.
Cyble vulnerability intelligence and dark web researchers also noted threat actor claims of zero-day vulnerabilities for sale affecting Palo Alto Networks devices and Chrome and Edge browsers.
In total, Cyble researchers examined 13 vulnerabilities and 8 dark web exploits to arrive at the list of vulnerabilities that security teams should prioritize for patching. At-risk products include Apache Struts, Qualcomm digital signal processors (DSPs), a WordPress plugin, a Bluetooth flaw affecting Ubuntu, and more.
The Week’s Top Vulnerabilities
CVE-2024-53677: This file upload logic vulnerability in the Apache Struts web application framework has been rated 9.5 severity by the Apache Software Foundation but is still undergoing NVD analysis. An attacker could exploit the vulnerability to manipulate file upload parameters to enable path traversal and potentially upload a malicious file that could be used to perform remote code execution. Recently, researchers disclosed that threat actors are attempting to exploit the vulnerability using public proof-of-concept exploits to allow remote code execution, and exploitation has also been discussed on dark web forums. Cyble also published a separate blog on this vulnerability.
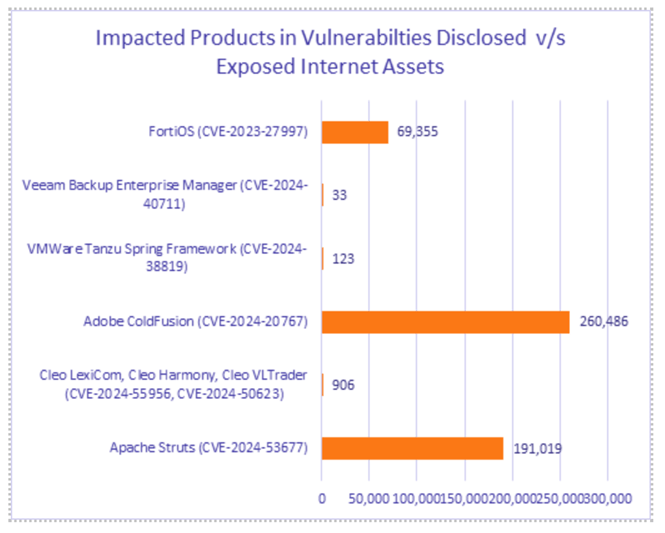
Cyble researchers noted that there are nearly 200,000 vulnerable Apache Struts instances exposed to the internet (image below):

CVE-2024-43047: This vulnerability affects Qualcomm’s Digital Signal Processor (DSP) service, which is utilized in many Android devices. It allows for privilege escalation and arbitrary code execution, posing significant risks to affected systems. Google Project Zero marked the vulnerability as actively exploited in October 2024 and received a fix on Android in November 2024. Researchers also observed that the Serbian government exploited Qualcomm zero-days, including CVE-2024-43047, to unlock and infect Android devices with a new spyware family named “NoviSpy.”
CVE-2024-11972: The CVE for this vulnerability has been reserved but has not yet been created. The flaw affects the Hunk Companion WordPress plugin, which is designed to enhance functionality and build visually appealing websites without extensive coding knowledge. The vulnerability allows attackers to perform unauthenticated plugin installation through unauthorized POST requests, enabling them to install and activate other plugins that may contain known vulnerabilities. According to researchers, attackers are exploiting the vulnerability to install outdated plugins with known flaws from the WordPress.org repository. This allows them to access vulnerabilities that can lead to remote code execution (RCE), SQL injection, cross-site scripting (XSS), or the creation of backdoor admin accounts, posing significant risks to site security.
CVE-2023-45866: This medium-severity vulnerability affects Bluetooth HID Hosts in systems utilizing BlueZ, particularly in Ubuntu 22.04 LTS with the BlueZ 5.64-0ubuntu1 package. This vulnerability allows an unauthenticated peripheral HID device to initiate an encrypted connection, potentially enabling the injection of Human Interface Device (HID) messages without user interaction.
Vulnerabilities and Exploits on Underground Forums
Cyble Research and Intelligence Labs (CRIL) researchers also identified the following exploits and vulnerabilities discussed on Telegram channels and cybercrime forums, raising the risk that they will be exploited in attacks.
CVE-2024-28059: This critical security vulnerability, which was identified in the MyQ Print Server in versions prior to 8.2 (patch 43), allows remote attackers to gain elevated privileges on the target server.
CVE-2024-38819: This high-severity path traversal vulnerability in the Spring Framework specifically affects applications that utilize WebMvc.fn or WebFlux.fn functional web frameworks.
CVE-2024-35250: This high-severity privilege escalation vulnerability in the Microsoft Windows operating system specifically affects the kernel-mode driver.
CVE-2024-40711: This critical vulnerability identified in Veeam Backup & Replication software allows for unauthenticated remote code execution (RCE) due to deserialization of untrusted data.
CVE-2023-27997: This heap-based buffer overflow vulnerability in certain FortiOS and FortiProxy versions may allow a remote attacker to execute arbitrary code or commands via specifically crafted requests, specifically affecting SSL VPNs.
Threat actors were also observed offering a zero-day exploit weaponizing a vulnerability claimed to be present on Palo Alto Network’s PAN-OS VPN-supported devices (asking price: $60,000) and a zero-day exploit weaponizing a vulnerability allegedly present in Chrome and Edge (asking price: $100,000).
Cyble Recommendations
To protect against these vulnerabilities and exploits, organizations should implement the following best practices:
- To mitigate vulnerabilities and protect against exploits, regularly update all software and hardware systems with the latest patches from official vendors.
- Develop a comprehensive patch management strategy that includes inventory management, patch assessment, testing, deployment, and verification. Automate the process where possible to ensure consistency and efficiency.
- Divide your network into distinct segments to isolate critical assets from less secure areas. Use firewalls, VLANs, and access controls to limit access and reduce the attack surface exposed to potential threats.
- Create and maintain an incident response plan that outlines procedures for detecting, responding to, and recovering from security incidents, including ransomware-resistant backups. Regularly test and update the plan to ensure its effectiveness and alignment with current threats.
- Implement comprehensive monitoring and logging solutions to detect and analyze suspicious activities. Use SIEM (Security Information and Event Management) systems to aggregate and correlate logs for real-time threat detection and response.
- Subscribe to security advisories and alerts from official vendors, CERTs, and other authoritative sources. Regularly review and assess the impact of these alerts on your systems and take appropriate actions.
- Conduct regular vulnerability assessment and penetration testing (VAPT) exercises to identify and remediate vulnerabilities in your systems. Complement these exercises with periodic security audits to ensure compliance with security policies and standards.
Conclusion
These vulnerabilities highlight the urgent need for security teams to prioritize patching exploitable vulnerabilities in sensitive products and vulnerabilities that could be weaponized as entry points for wider attacks. With increasing discussion of these exploits on dark web forums, organizations must stay vigilant and proactive.
Implementing strong security practices is essential for protecting sensitive data and maintaining system integrity. A comprehensive threat intelligence solution like Cyble can monitor for threats and leaks specific to your environment, allowing you to respond quickly to events and prevent them from becoming wider incidents.
Related
如有侵权请联系:admin#unsafe.sh