tl;dr
CVE-2020-5902 was disclosed on June 1, 2020 by F5 Networks in K52145254 as a CVSS 10.0 remote code execution vulnerability in the Big-IP administrative interface. By June 3, 2020 NCC Group observed active exploitation. This blog is a summary of what we know as the situation develops.
About the Research and Intelligence Fusion Team (RIFT):
RIFT leverages our strategic analysis, data science, and threat hunting capabilities to create actionable threat intelligence, ranging from IoCs and detection capabilities to strategic reports on tomorrow’s threat landscape. Cyber security is an arms race where both attackers and defenders continually update and improve their tools and ways of working. To ensure that our managed services remain effective against the latest threats, NCC Group operates a Global Fusion Center with Fox-IT at its core. This multidisciplinary team converts our leading cyber threat intelligence into powerful detection strategies.
The Vulnerability / Patch
In K52145254 there is the following mitigation:
<LocationMatch ".*\.\.;.*"> Redirect 404 / </LocationMatch>
This regex checks for:
..;
As such the vulnerability can be described as a directory traversal vulnerability. This ability combined with functionality native to the device provides the ability to access files, upload files and execute any code without authentication.
Exploitation
The graph below shows the exploitation seen on NCC Group’s honeypot during the morning of June 5, 2020.

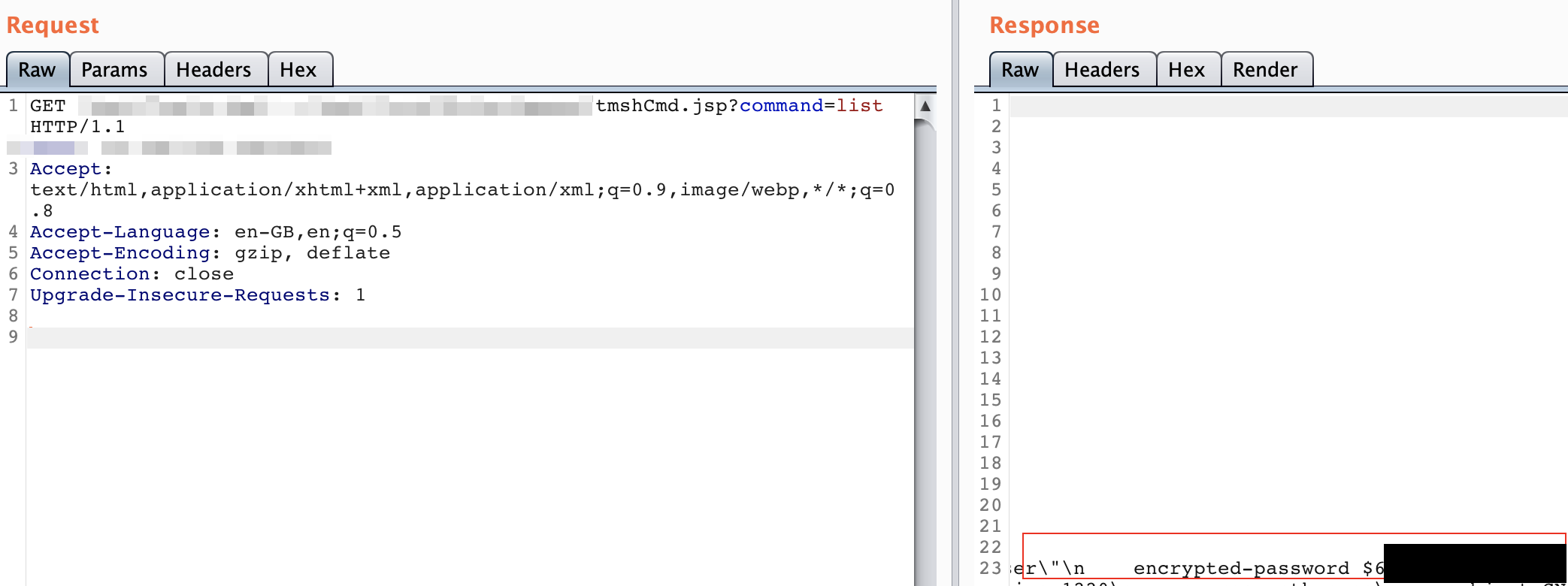
Exploitation is varied including the access of password hashes:

As of Saturday remote code execution capabilities existed.
The first IPs we observed actively exploiting the issue we published at 5pm UTC on June 4th, 2020 – https://github.com/nccgroup/Cyber-Defence/tree/master/Intelligence/CVE-2020-5902
Impact
As the devices are load balancers they provide the opportunity to:
- Acquire credentials
- Perform traffic interception and modification
- Pivot into the internal network
- Acquire the private keys to any SSL/TLS certificates on the device
Incident Analysis
There are forensics artifacts available, although the log they are stored is limited to 20MB and thus risks cycling quickly.
$ journalctl | grep -F "..;" Jul 04 06:53:25 localhost.localdomain logger[16837]: [ssl_acc] xxx.xxx.xxx.66 - - [04/Jul/2020:06:53:25 -0700] "/tmui/login.jsp/..;/login.jsp" 404 226 Jul 04 06:53:25 localhost.localdomain logger[16838]: [ssl_req][04/Jul/2020:06:53:25 -0700] xxx.xxx.xxx.66 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 "/tmui/login.jsp/..;/login.jsp" 226 Jul 04 07:06:47 localhost.localdomain logger[16837]: [ssl_acc] xxx.xxx.xxx.65 - - [04/Jul/2020:07:06:47 -0700] "/tmui/login.jsp/..;/..;/tmui/Control/jspmap/tmui/accessctrl/ssoconfig/create.jsp" 404 277 Jul 04 07:06:47 localhost.localdomain logger[16838]: [ssl_req][04/Jul/2020:07:06:47 -0700] xxx.xxx.xxx.65 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 "/tmui/login.jsp/..;/..;/tmui/Control/jspmap/tmui/accessctrl/ssoconfig/create.jsp" 277 Jul 04 07:23:48 localhost.localdomain logger[16838]: [ssl_req][04/Jul/2020:07:23:48 -0700] xxx.xxx.xxx.65 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 "/tmui/login.jsp/..;/..;/tmui/tmui/locallb/workspace/fileRead.jsp" 261 Jul 04 07:23:48 localhost.localdomain logger[16837]: [ssl_acc] xxx.xxx.xxx.65 - - [04/Jul/2020:07:23:48 -0700] "/tmui/login.jsp/..;/..;/tmui/tmui/locallb/workspace/fileRead.jsp" 404 261 Jul 04 09:09:03 localhost.localdomain logger[29148]: [ssl_acc] xxx.xxx.xxx.65 - - [04/Jul/2020:09:08:25 -0700] "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp" 200 4453 Jul 04 09:09:03 localhost.localdomain logger[29149]: [ssl_req][04/Jul/2020:09:08:25 -0700] xxx.xxx.xxx.65 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256 "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp" 4453
The wider HTTP log configuration differs from a default configuration. The configuration causes it to send its output to a pipe. In the default configuration nothing consumes this pipe.
# # The location and format of the access logfile (Common Logfile Format). # If you do not define any access logfiles within a <VirtualHost> # container, they will be logged here. Contrariwise, if you *do* # define per-<VirtualHost> access logfiles, transactions will be # logged therein and *not* in this file. # #CustomLog "logs/access_log" common # # If you prefer a logfile with access, agent, and referer information # (Combined Logfile Format) you can use the following directive. # CustomLog "/var/run/httpd.pipe" acc_combined
Other forensic artifacts made include new .jsp files or similar used to achieve code execution.
Change Log
This blog was last updated June, 5th 2020 @ 15:40
June 5th, 2020 @ 15:40 – v1.0
Published