2025-1-7 20:45:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏
A relatively new Mirai-based botnet has been growing in sophistication and is now leveraging zero-day exploits for security flaws in industrial routers and smart home devices.
Exploitation of previously unknown vulnerabilities started in November 2024, according to Chainxin X Lab researchers who monitored the botnet's development and attacks.
One of the security issues is CVE-2024-12856, a vulnerability in Four-Faith industrial routers that VulnCheck discovered in late December but noticed efforts to exploit it around December 20.
to leverage zero-day exploits has been leveraging a zero-day exploit for CVE-2024-12856, impacting Four-Faith routers, alongside other custom exploits for flaws in Neterbit routers and Vimar smart home devices.
Botnet profile
The botnet, whose name is a homophobic reference, also relies on custom exploits for unknown vulnerabilities in Neterbit routers and Vimar smart home devices.
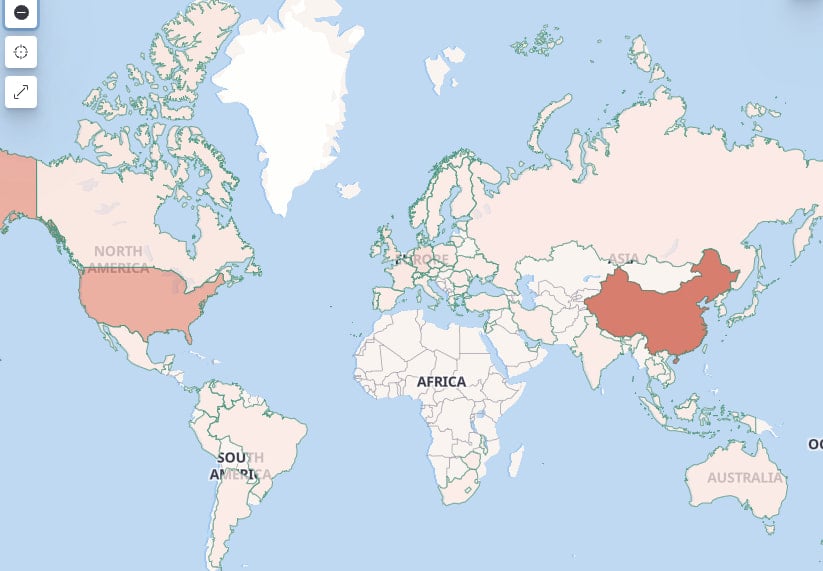
It was discovered last year in February and currently counts 15,000 daily active bot nodes, mostly in China, the United States, Russia, Turkey, and Iran.
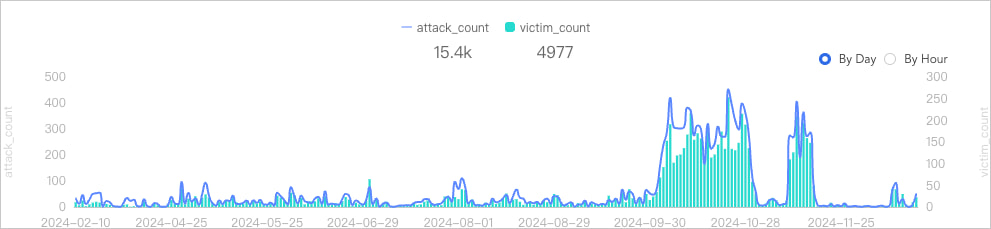
Its main goal appears to be carrying out distributed denial of service (DDoS) on specified targets for profit, targeting hundreds of entities daily, with the activity peaking in October and November 2024.
Source: X Lab
The malware leverages a mix of public and private exploits for more than 20 vulnerabilities to spread to internet-exposed devices, targeting DVRs, industrial and home routers, and smart home devices.
Specifically, it targets the following:
- ASUS routers (via N-day exploits).
- Huawei routers (via CVE-2017-17215)
- Neterbit routers (custom exploit)
- LB-Link routers (via CVE-2023-26801)
- Four-Faith Industrial Routers (via the zero-day now tracked as CVE-2024-12856)
- PZT cameras (via CVE-2024-8956 and CVE-2024-8957)
- Kguard DVR
- Lilin DVR (via remote code execution exploits)
- Generic DVRs (using exploits like TVT editBlackAndWhiteList RCE)
- Vimar smart home devices (likely using an undisclosed vulnerability)
- Various 5G/LTE devices (likely via misconfigurations or weak credentials)
The botnet features a brute-forcing module for weak, Telnet passwords, uses custom UPX packing with unique signatures, and implements Mirai-based command structures for updating clients, scanning networks, and conducting DDoS attacks.
Source: X Lab
X Lab reports that the botnet’s DDoS attacks are short in duration, lasting between 10 and 30 seconds, but high in intensity, exceeding 100 Gbps in traffic, which can cause disruptions even for robust infrastructures.
“The targets of attacks are all over the world and distributed in various industries,” explains X Lab.
“The main targets of attacks are distributed in China, the United States, Germany, the United Kingdom, and Singapore,” the researchers say.
Overall, the botnet demonstrates a unique capability to maintain high infection rates across diverse device types using exploits for n-day and even zero-day flaws.
Users can protect their devices by following the general recommendation to install the latest device updates from the vendor, disable remote access if not needed, and change the default admin account credentials.
如有侵权请联系:admin#unsafe.sh