2020-10-01 00:43:14 Author: blog.elcomsoft.com(查看原文) 阅读量:231 收藏
Everyone’s iPhones contain overwhelming amounts of highly sensitive personal information. Even if some of that data is not stored on the device, the iPhone itself or the data inside can work as a key to other many things from bank accounts to private family life. While there are many possible vectors of attack, the attacker will always try exploiting the weakest link. Learn to think like one, find the weakest link and eliminate the potential vulnerabilities before they are exploited. This guide comes from the forensic guys making tools for the law enforcement, helping the good guys break into the bad guys’ iPhones.
The hardware
Not every model is equally secure. iPhone models up to and including the iPhone X are vulnerable to the checkm8 exploit, allowing partial file system and keychain acquisition even in the passcode is not known. Since this exploit targets a hardware vulnerability in BootROM, it cannot be fixed in iOS updates. If you want a secure phone, one of the devices based on the A12 or newer SoC, here is the list:
- iPhone Xr
- iPhone Xs
- iPhone Xs Max
- iPhone 11
- iPhone 11 Pro
- iPhone 11 Pro Max
- iPhone SE (2020)
- iPhone 12
The point is, you are not safe if you are using older hardware. No matter what you do, older devices are vulnerable to checkm8 exploit.
The software
Keeping iOS up to date is extremely important. At the time of this writing, iOS 14.0.1 is the latest version (with 14.2 beta being actively tested). Using any older version of iOS puts you at risk.
Make sure to set a long and complex backup password. Do it whether you are planning to make local backups or not, as someone may do it instead of you. The password must be complex enough: use at least 8 characters, mixing small and capital letters, digits and special characters. This password also needs to be unique, and should not consist of dictionary words.
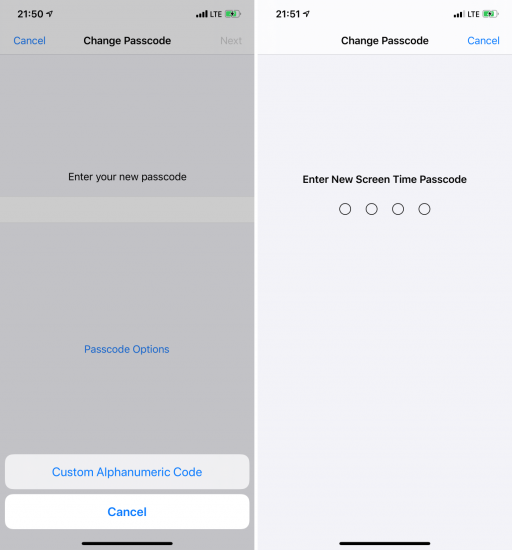
Finally, set the Screen Time passcode – again, whether you use the Screen Time feature on not. That will prevent your backup password from being easily reset if someone gains control over your iPhone. The Screen Time passcode should be different from the device passcode, and should not be easy to crack – please do not set it to your year of birth, the current year, or 0571 (if you know what I mean), or any other year up to date. For more information and some technical details:
- The Most Unusual Things about iPhone Backups
- The Four Ways to Deal with iPhone Backup Passwords
- Using Screen Time Password to Protect iPhone Local Backups
Basic protection
By default, iOS suggests using a 6-digit only (it used to be just 4 digits before). This is convenient, but definitely not secure with existing passcode cracking solutions (which are supposedly exclusive to the law enforcement). We recommend passcodes of 8 digits at least, or a complex alphanumeric passcode if you are concerned about security.
Be aware that using Touch ID or Face ID does not improve the absolute security of your device; instead, these biometric authentication methods may give someone an opportunity to unlock your iPhone without the passcode. Biometric authentication is a compromise, adding convenience at expense of security.
Connections
If you connect your iPhone to any computer, you are at risk if you had established a trusted connection there. More information in The Issue of Trust: Untrusting Connected Devices from Your iPhone.
What can you do? The recommendations are quite simple:
- Use only original cables or certified cables obtained from a trusted source. The ones that “look like the real thing” (but may steal your data) exist, like MG Cable or USB Ninja.
- Use only original chargers (or ones obtained from a trusted source). Very “special” ones exist, too.
- If you desperately need to use a third-party cable or charger, do not establish the “trust relationship” if prompted. If this prompt ever shows up on your device when you are attempting to charge it, be alert. Remember: charging your iPhone does NOT require “trusting” the charger!
- Do not establish “trust relationship” with computers you don’t really trust. If you are not sure you’ve never trusted a non-trustworthy computer, clear your pairing records ASAP.
- Physically protect access to your own computers.
The last one is extremely important. Your hard drive contains data that may help to unlock your iPhone. Use BitLocker on Windows, or FileFault2 on macOS – and of course, use unique and hard-to-break passwords for everything.
SOS!
You should learn how to activate the emergency “S.O.S.” mode on your iPhone. This mode, once invoked, will some encryption keys stored in the device memory, making biometric unlock impossible. In addition, it disables the Lightning port immediately, making the data acquisition much harder, if not impossible. Here is how: The True Meaning of iOS Recovery, DFU and SOS Modes for Mobile Forensics. That’s a life saver, really!
iCloud
Securing the iCloud account is worth a separate article. Just some things to note:
- Make sure you know exactly what data is stored in your iCloud account. Do not assume anything! You might be surprised in both ways.
- Use a strong and unique iCloud password.
- Enable the Find My [Phone]
- Use two-factor authentication.
Note that Apple has access to most of your data stored in iCloud, and may provide it to the law enforcement if served a legal request; see Law Enforcement Support Program for details. All they need is your Apple ID (email), or your phone number, or the device IMEI, or its serial number. You may be able to obtain a copy of your data from Apple, delete all or some data.
Software, part two
How secure are the apps you are using? Every app from messengers to document management tools can pose a security threat. Most modern messages are secure (we personally recommend Signal), but still vulnerable via exploits or malicious software that might be installed silently on your iPhone or your contact’s phone. Also, some messengers store their data in their vendors’ clouds, or create chat backups in Apple iCloud (that applies to any other software, too).
Screen lock
Make sure that your phone locks itself automatically even if you forget to push the Lock/Sleep button. This is easy to do by checking the Display & Brightness | Auto-Lock setting, which could be anything from 30 seconds to 5 minutes. Never use the “Never” setting.
Once your screen is locked, make sure that nothing you don’t want everyone to see can accidentally pop up. In [Touch/Face ID & Passcode] | [Allow access when locked] disable at least the following:
- Notification Centre
- Control Centre
- USB Accessories
The reason for this is privacy. Notifications may and do contain sensitive information from one-time verification codes to personal messages. The Control Center allows activating the Airplane mode, which is frequently done in place of powering the phone down to preserve the encryption keys in your phone’s volatile memory. The last setting allows USB restricted mode.
One more thing: make sure that the [Require passcode] setting is set to “Immediately”.
IoT
Are you an Apple Watch wearer? IoT devices might pose an additional risk. As an example, your Apple Watch could be used to unlock your Mac (if configured). While this adds a bit of extra convenience, do mind the risks. You can read more about the data available in Apple Watch in Apple TV and Apple Watch Forensics 01: Acquisition and Apple Watch Forensics 02: Analysis. To secure your Apple Watch, make sure that you have enabled a passcode, and that the passcode is different from the one on your iPhone.
If you have an Apple TV in your household, you can do literally nothing to secure the data: there is no passcode on Apple TV, and there is no way to set one. The analysis of an Apple TV is available in Apple TV Forensics 03: Analysis.
Other considerations
There are a few other things to consider.
Sideloaded apps
Unlike Android, iOS does not allow sideloading apps (easily). While tracking and spying is as common in iOS apps as it is on Android, iOS 14 is about to deal with it by introducing the new prompt asking the user for tracking permission. (TikTok anyone?)
Jailbreaking
Don’t. A jailbreak exploits vulnerabilities in the device or the operating system. Jailbroken devices are inherently less secure than non-jailbroken ones.
MDM
MDM is a powerful way to add extra security restrictions such as enforcing certain passcode quality or requiring certain automatic screen lock settings. Among other settings, MDM could be used to restrict pairing with new devices, effectively blocking one of the threats.
MDM has an ugly side, too. If a threat-actor gains access to the MDM console, he/she can change settings or track your device.
The cloud
iCloud is the largest risk in the entire ecosystem. Even if you take every step possible to protect your account, Apple is still bound to turn your data over to the law enforcement if served with a proper legal request. The data is more detailed and more comprehensive than one can imagine, and may even include footage from surveillance cameras installed in Apple Stores. While Apple provides some information on what data is stored (and may be revealed), the list in fact it far from comprehensive.
Randomized MAC address
It’s there. Just a small but useful extra. Why does that matter? Use private Wi-Fi addresses in iOS 14, iPadOS 14, and watchOS 7 explains in detail how using a different MAC address with each Wi-Fi network helps further protect your privacy.
Google and Facebook
If you are using Google apps or Google services on your iPhone, be aware about Google’s data collection, processing, retention and disclosure practices.
Even if you don’t have a Facebook account or the Facebook app installed, chances are that most of the many apps you have installed on your iPhone include Facebook’s tracking SDK. Be aware. You can read more about unconsented Facebook tracking within apps. Apple is about to put an end to this practice in further iOS 14 updates sometime in 2021.
Mobile providers
Mobile service providers will turn over a lot of data when requested, including the list Web sites that you visited (DNS queries).
The creepy things
Even if you power down your iPhone but still have the battery connected, your phone might be used as a remote mic.
Conclusion
As secure as it may seem, the Apple ecosystem is not without its flaws. While I tried to list everything I could remember, no single guide is complete: there can be other risks and other mitigations. Making yourself aware of the risks is just the first step in the direction of securing your personal information.
如有侵权请联系:admin#unsafe.sh