
2020-07-09 09:00:00 Author: feedproxy.google.com(查看原文) 阅读量:119 收藏
Many of you might not be aware of the amount of free DFIR resources available. Here is a compilation of the most popular new content. Check it out!
July 9, 2020

With more than 21k people register so far to attend the summit, we understand that many of you might not be aware of the amount of free DFIR resources available.
We are proud to offer the community over 150 free tools and countless cheat-sheets, posters, webcasts, and blog posts produced by our faculty and we understand it could be difficult to decide which ones you should “deep-dive” into first. So, we have put together a compilation of the most popular new content by category to make it easier for you.
Getting Started in DFIR
| Kevin Ripa’s 3MinMax: Episode 74: How to Get Started in Digital Forensics There are many misconceptions and it is not easy to start in the field, but then if it was easy, everyone would be doing it, right? FOR498: Battlefield Forensics & Data Acquisition course author Kevin Ripa tells you how to get started in the field in 3 minutes or less. | SANS@MIC: Getting Started in Digital Forensics Authors of the New FOR308: Digital Forensics Essentials course, Kathryn Hedley, Jason Jordaan and Phill Moore talk about what's needed to build your foundation in DFIR. |
SANS Technology Institute | Graduate Certificate in Incident Response
Discover the graduate certificate program in Incident Response from the SANS Technology Institute.
- Earn 4 GIAC certifications as you progress this highly technical 13-credit-hour program.
- A 100% online option is available. SANS.edu programs are accredited and eligible for most corporate tuition plans.
- Eligible for U.S. VA Education Benefits. Applications are accepted monthly.
Join a free online info session on Wed, July 29, at 1 pm (EDT) to learn about all SANS.edu graduate programs.
Incident Response and Threat Hunting
| 3 Key Lessons CTI Teams Should Learn From Cyber Threat Intelligence Summit 2020 This presentation identifies areas where organizations should put more focus in order to stop tilting at windmill. | Case Study: Improving a Mature Hunt Program SANS Threat Hunting Summit 2019 David Bianco and Cat Self discuss coming into an existing threat hunting program, prioritizing areas for improvement, and implementing those improvements to make a great hunting program even better. |
 |  |
| NEW – Linux Shell Survival Guide v2.3 This guide is a supplement to the SANS FOR572: Advanced Network Forensics and Analysis by course author Phil Hagen. It covers some of what we consider the most useful Linux shell primitives and core utilities. | UPDATED – Find Evil Poster The FOR508: Advanced Incident Response, Threat Hunting & Digital Forensics course poster helps you understand lateral movement tools and techniques. It provides information on how to hunt more efficiently, quickly perform incident response scoping, and better anticipate future attacker activity. |
Memory Forensics SkillBuilder Series: User-Mode Process Dump Analysis with WinDbg In this webcast series, FOR526: Advanced Memory Forensics & Threat Detection course author Alissa Torres walks through analysis of process dumps to uncover code injection, user-mode hooking and user activity. | HuntWorld Adversaries have been coming to our networks for nearly 20 years, repeating the same intrusions day after day, while we repeat more or less the same responses day after day. In this talk Rob Lee exploriesthe hunting culture over the years and studying what works, what doesn’t, and what the future holds. |
| WEBCAST: The State of Malware Analysis - Advice from the Trenches When investigating an incident, we seek useful, actionable information about the malicious software discovered on the affected systems. What tools and techniques can assist with such efforts? Course author Lenny Zeltser along with FOR 610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques course instructors Jim Clausing, Evan Dygert, Anuj Soni and Jake Williams share perspectives on the state of malware analysis. Read the State of Malware Analysis - Advice from the Trenches Blog | Distributed Evidence Collection and Analysis with Velociraptor: Fast, Surgical, at Scale...and Free!
DFIR Summit 2019 |
Operating System & Device In-Depth Forensics
 | 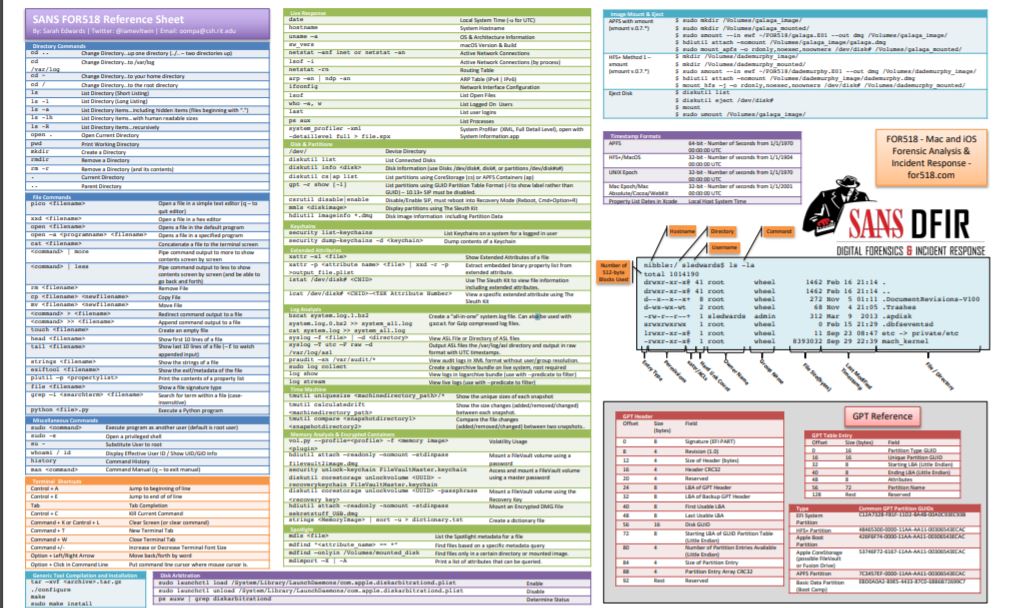 |
| NEW – Interactive Mobile Forensics Poster All the content from the FOR585: Smartphone Forensic Analysis In-Depth course poster in an interactive format to help you navigate and search for content faster. | UPDATED: Mac Forensics Reference Cheat-Sheet Authored by FOR518: Mac & iOS Forensic Analysis & Incident Response course author Sarah Edwards, this cheat-sheet describes the core functions and details of the HFS+ Filesystem. |
| WEBCAST: Cloud Storage Acquisition from End Point Devices Cloud storage data can be more accessible on the local device and can contain files and metadata distinctly different than the current cloud repository. However, endpoint collection includes its own set of challenges. In this webcast, SANS Senior Instructor co-author of the FOR500: Windows Forensic Analysis course Chad Tilbury, discusses these challenges and provide a strategy for ensuring you are not missing critical evidence in your investigations. Read the Cloud Storage Acquisition from End Point Devices Blog | Finding Evil in Windows 10 Compressed Memory |
DFIR Tools
| Webcast: How to start with the SIFT WorkStation SIFT® - A digital forensics and incident response-based Linux distribution bundling most open-source DFIR tools available. Listen to SIFT Distribution author Rob Lee on how to start with the tools. |
| Webcast: SOF-ELK - A free, Scalable Analysis Platform for Forensic, Incident Response, and Security Operations In this webcast, FOR572: Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response course author Phil Hagen explores SOF-ELKs use cases, types of log data currently supported, as well as how to load data from live or archived sources. We will also show the various dashboards supplied with the VM and show how new features can be activated through the projects GitHub repository. |
 |
| Poster: EZTools Command Poster EZTools - Cutting-edge open-source windows based digital forensics tool suite for scalable, scriptable, fast forensics. Listen to tool’s author Eric Zimmerman webcast about how to use the tools. Listen to poster author Mark Hallman on how to use the poster |
 |
| Cheat-sheet: REMnux Usage Tips for Malware Analysis on Linux Authored by FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques course and REMnux Distribution author Lenny Zeltser, this cheat sheet outlines the tools and commands for analyzing malicious software on the REMnux Linux Distribution. |
如有侵权请联系:admin#unsafe.sh