Welcome hackers, here you go with one of the most interesting topics – cracking passwords. In this post, I am explaining the process of cracking hashes from shadow files in Linux machines.
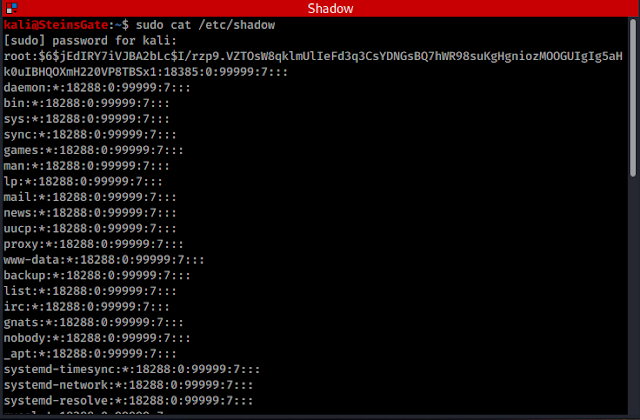
Shadow file is located in /etc/shadow.
Shadow contains all the user's passwords in an encrypted form. You need to have sudo privileges to view or download
the shadow hash.
Example:
Username:Hash_Algorithm:Salt:Hash:last_pass_change:min_days:max_days
kali:$6$H6LRx0yQ62gqLdg7$88r9sgiYtcMKELXTGvyFBPtZmTV.xw4CRamKwYjYIWxiXi3o9dKOlK.2yC3PM2JHRl/xfhXS2kleJmP63nSTJ/:18288:0:99999:7:::
You can find the Hash_Algorithm by
checking the ID, below are the most commonly used hashing algorithms.
- $1$ is MD5
- $2a$ is Blowfish
- $2y$ is Blowfish
- $5$ is SHA-256
- $6$ is SHA-512
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE ONLY, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
You need to have root privileges to view or download shadow files. after you download or copy the hashes from shadow files, either john the ripper or hashcat can be used to crack the hashes.
Installing John The Ripper
sudo apt-get update
sudo apt install john
Shadow file is saved in the location /etc/shadow, to read it, use theh command "cat /etc/shadow "
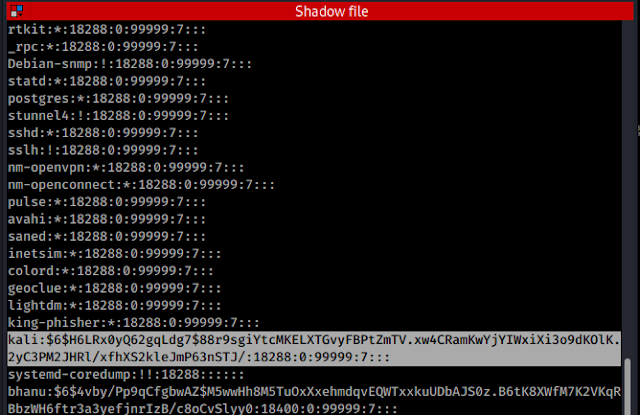
Copy the hash that needs to be cracked
Save the hash in a new file using either nano,vim,etc...
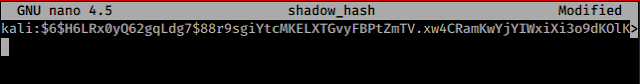
Here I am using nano, Paste the hash
in the terminal à ctrl+x à y
Now use the below command to crack the
hashes, --wordlist = Location of your wordlist or dictionary, shadow_hash here
is the filename. if the hashes of the passwords match our hash - you can get the password or else you need to use a different password.
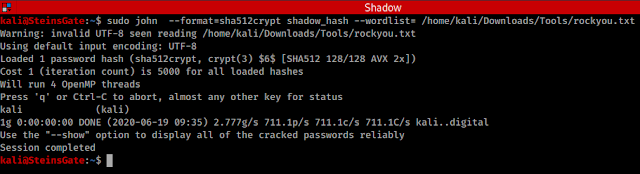
sudo john --format=sha512crypt shadow_hash --wordlist= /home/kali/Downloads/Tools/rockyou.txt
After the successful password crack, to
view the password use -–show option
sudo john --format=sha512crypt shadow_hash --show
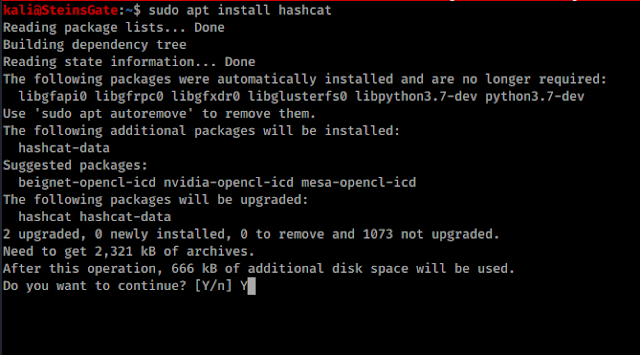
Installing hashat
sudo apt-get update
sudo apt install hashcat
Below is the example of methods that
can be used, you can find it by using hashcat –help command
0500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) | Operating Systems
3200 | bcrypt $2*$, Blowfish (Unix) | Operating Systems
7400 | sha256crypt $5$, SHA256 (Unix) | Operating Systems
1800 | sha512crypt $6$, SHA512 (Unix) | Operating Systems
122 | macOS v10.4, MacOS v10.5, MacOS v10.6 | Operating Systems
1722 | macOS v10.7 | Operating Systems
7100 | macOS v10.8+ (PBKDF2-SHA512) | Operating System Use the below command to crack shadow hashes
using hashcat
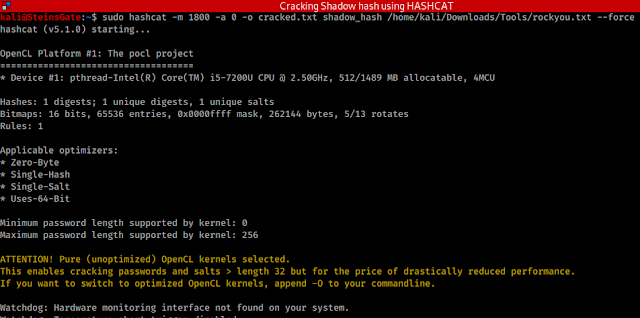
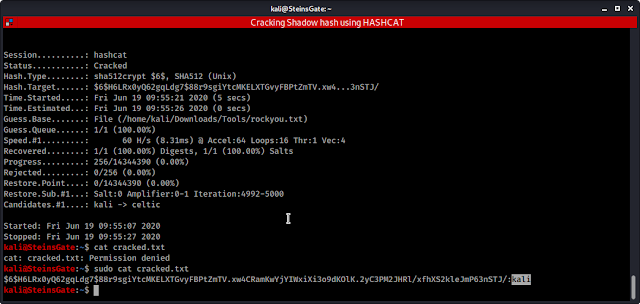
sudo hashcat -m 1800 -a 0 -o cracked.txt shadow_hash /home/kali/Downloads/Tools/rockyou.txt --force