The Good
With the US elections just two months away, and absentee voting via email and mail already underway, it is encouraging to see multiple agencies getting serious about election security. The FBI and CISA have made several joint public service announcements with the aim of reducing unnecessary anxiety over foreign intervention while clearly explaining what might actually happen.
The first announcement warned of the potential threat posed by foreign actors and cybercriminals spreading disinformation about the 2020 election results. They note that:
“foreign actors and cybercriminals could create new websites, change existing websites, and create or share corresponding social media content to spread false information in an attempt to discredit the electoral process and undermine confidence in U.S. democratic institutions”.
Acknowledging this will hopefully go some way to persuading the general public that the elections aren’t rigged and that it is worthwhile to make the effort and vote, instead of staying at home (the intent of said foreign actors being to reduce voting levels).
Next, a PSA warned of foreign actors and cyber criminals spreading false rumors that they have somehow compromised election infrastructure and facilitated the “hacking” and “leaking” of U.S. voter registration data. This is done in an attempt to discredit the electoral process and undermine confidence in U.S. democratic institutions. It’s worth noting that much U.S. voter information can be purchased or acquired through publicly available sources, and the FBI and CISA added that they “have no information suggesting any cyberattack on U.S. election infrastructure has prevented an election from occurring, compromised the accuracy of voter registration information, prevented a registered voter from casting a ballot, or compromised the integrity of any ballots cast”.
A further PSA warned of DDoS Attacks against Election Infrastructure that can hinder access to voting information, delay voting and hold up vote counting. The agencies stress that even if such attacks did take place, measures are in place to ensure that they would not prevent anyone from casting their vote.
But the FBI and CISA are not the only agencies that tackle the issue of securing the election process. The House of Representatives unanimously approved legislation that would make hacking voting systems a federal crime. This follows the “Defending the Integrity of Voting Systems Act” approved by Senate last year and will enable the federal government to play a role in helping states defend against threats to elections.
The Bad
CISA has reported that a threat actor attacked an unnamed federal agency network this past week. By leveraging compromised credentials, the cyber threat actor gained persistent access through two reverse Socket Secure (SOCKS) proxies that exploited weaknesses in the agency’s firewall. They reportedly used the agency’s anti-malware product’s software license key and installation guide and “then visited a directory used by the product for temporary file analysis.” After accessing this directory, the attackers were able to run inetinfo.exe, a sophisticated malware dropper and file decrypter, to further the attack.
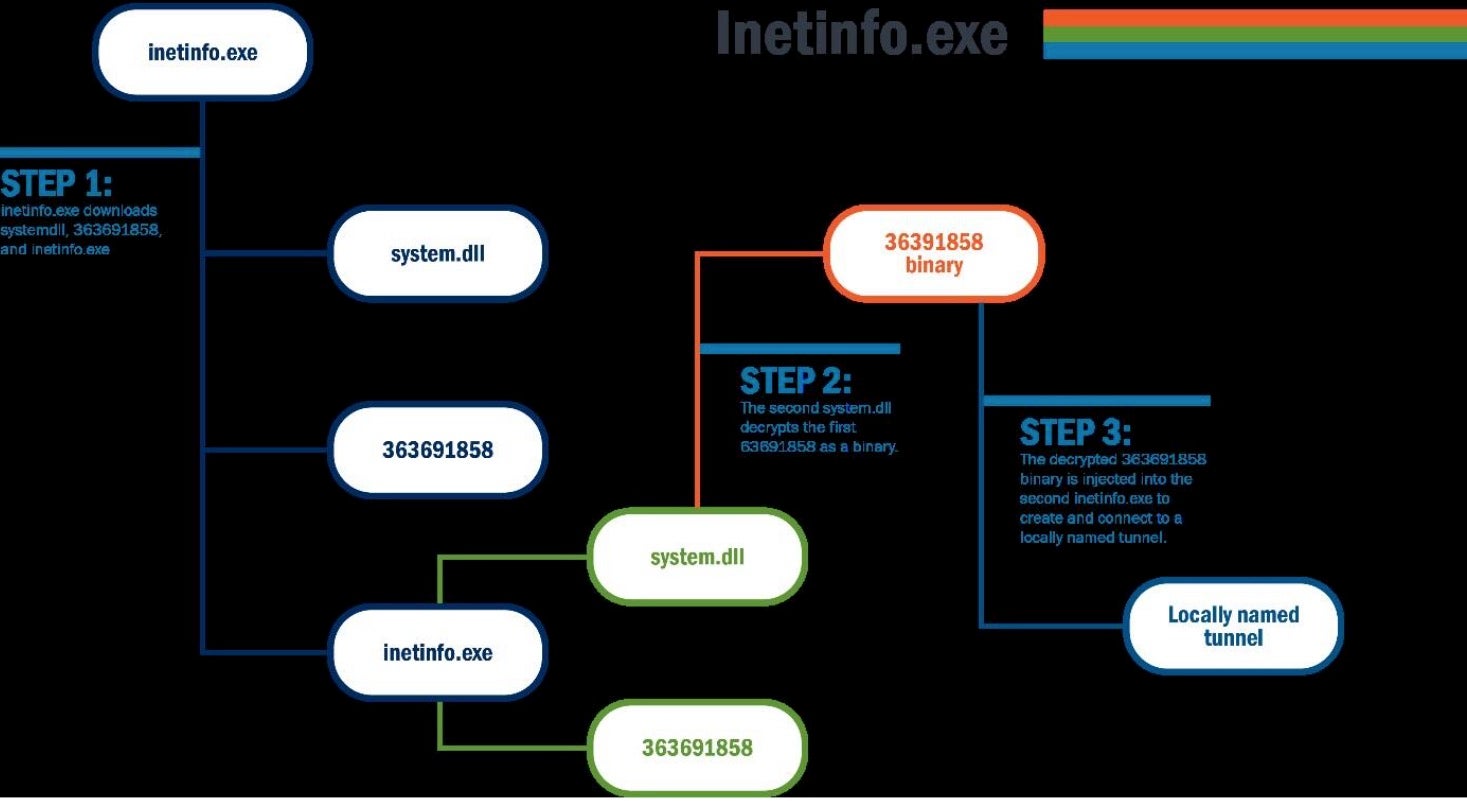
Wired reports that the hackers are none other than Fancy Bear/APT28: a team of hackers working for Russia’s GRU. Referring to a previous report (dating back to May 2020) the FBI noted that Fancy bear attacked US networks and provided an IP of a server in Hungary – the same IP address appears in the CISA report. An older report by the Department of Energy warned that APT28 had probed a US government organization’s network from a server in Latvia, and that Latvian IP address also appears in the report. Moreover, the sophisticated TTPs detailed by CISA match those of APT28 as shown in previous campaigns. While we don’t know which agency was hacked and the extent of the breach, it serves as another reminder of just how capable these threat kinds of APT threat actors are.
The Ugly
As the COVID crisis continues into the last quarter of 2020, with no vaccine in site and with many countries relapsing into lockdowns, some might have expected cybercriminals to ease their onslaught on healthcare facilities. A ransomware attack this week on Universal Health Services (UHS), a Fortune 500 hospital and healthcare services provider, proves just how misplaced any such thoughts really are.
UHS operates 26 Acute Care hospitals, 328 Behavioral Health inpatient facilities, and 42 outpatient facilities and ambulatory care centers in 37 states in the U.S., Washington, D.C., Puerto Rico and the United Kingdom.
The healthcare provider was most likely hit by Ryuk ransomware. BleepingComputer reports that during the cyberattack, files were being renamed with the .ryk extension, a telltale sign of Ryuk.
The immediate result was the shutting down of all supporting IT systems and a return to what the company described as “established back-up processes including offline documentation methods”, meaning pen and paper reporting and scheduling. According to the company, no patient or employee data was compromised in the attack.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Zerologon (CVE-2020-1472): SentinelOne First to Detect on the Endpoint
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
- Unifying Endpoint Security for Enterprise | An Interview With Migo Kedem
- Revisiting the Pyramid of Pain | Leveraging EDR Data to Improve Cyber Threat Intelligence
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization
- What Is Cloud Security (and How Do You Secure the Cloud Today)?
- Feature Spotlight: Automated Application Control for Cloud Workloads
