We all have habits. Morning coffee (no sugar, just some milk), two eggs (sunny side up), reading mail wile you are not completely awaken, and a lot more. We all follow some kind of rules we have set for ourselves. We all have some favorites: names, cities and even numbers; maybe an important date or place. Can we exploit people’s habits to break their passwords effectively instead of using brute force? We can, and here’s the how-to.
Once upon a time we’ve been asked for assistance in a serious case, examining the criminal’s hard drive. There was no encryption and no system password, so the criminal’s Windows laptop was easily accessible. We extracted tons of passwords from the Chrome browser; there was nothing interesting except a single bank account, protected with 2fa, but that’s another story. We then broke several Office documents (one with a personal diary, again useless), then discovered a VPN password, then a few other passwords, but no incriminating evidence. We almost gave up, but at the end of the second day, we have found a hidden TrueCrypt volume.
Breaking TrueCrypt (or VeraCrypt nowadays) is a real headache. First, TrueCrypt volumes are not always easy to identify as they have no standard header. Second, TrueCrypt offers the choice of several different algorithms for both hashing and encryption, and no information on them is provided in the container’s header. Third, the recovery speed is extremely low even on high-end hardware, so brute-force is not an option. Even the dictionary attack is almost useless, unless you have a very small “focused” dictionary of words and combinations the owner uses regularly.
Back to our case, we collected everything about the owner, and tried a dictionary attack with maximum mutations. The maximal level of mutations modifies all the words one way or another. Another two weeks had passed, and no results.
As a last resort, we got all of that criminal’s passwords we discovered so far, printed them on a piece of paper, turned off our number-crunching GPU workstation and started thinking. We literally just looked at these passwords. Many of them were completely random, obviously generated by some tool. We have not found any password managers though. The rest of the passwords were very simple and were present in most wordlists, including the one we already tried. Finally we noticed several passwords that followed a specific “pattern”, so to day. The pattern was surprisingly simple: a female name followed by two special characters, then three or four digits, sometimes followed by an underscore.
At that time, we did not have a specific attack that could help with such case. We only had (you bet!) the brute-force attack, the dictionary attack with lots of possible mutations, and attack with custom masks (relatively simple at the time). So we had to write a simple code specifically for that case to generate a very custom dictionary containing passwords that were similar to the ones we have already found. That was a quick and dirty solution, yet it allowed to break the password for that TrueCrypt container in less than half an hour.
Today, you can do much better than that, and in a much easier way. No, EDPR will still not crack “similar” passwords automatically. The main and most effective tool is still your brain. You will first need to understand what the password could be, and establish the rules. But once you did, the rest is much easier: just use the new “Rules editor”.
The Rules
One of the features of Elcomsoft Distributed Password Recovery, which is little known and largely underutilized (more on that later), is the ability to create highly efficient and precisely targeted “hybrid” attacks. This technique allows to dynamically generate passwords based on words from one or two dictionaries and dynamic, scriptable modifications based on a large set of rules. Hybrid attacks can be used for something as simple as generating words “Password1” through maybe “Password1234$” to extremely complex combinations such as “Pa$$w0rd10”, all completely automatically.
So if these hybrid attacks are so powerful, why are their little known and underutilized? Because before this day, the rules (following the John the Ripper syntax) required editing text files with zero feedback, and restarting the EDPR server every time you modified them. Every time you created a rule, you had almost zero indication of what was going on and how the resulting passwords would look like.
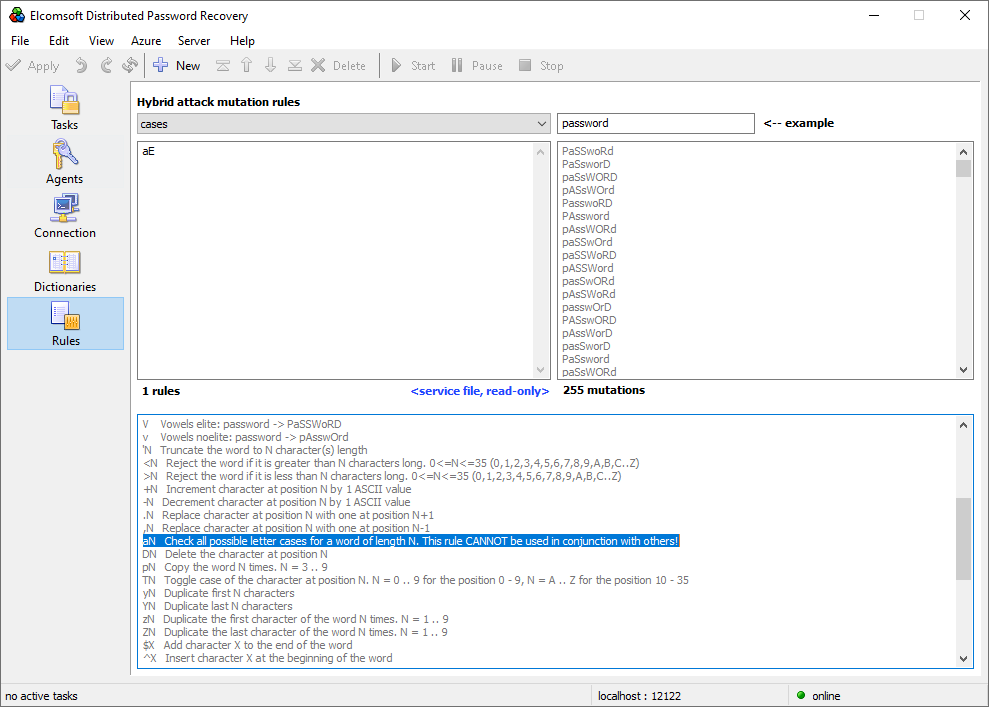
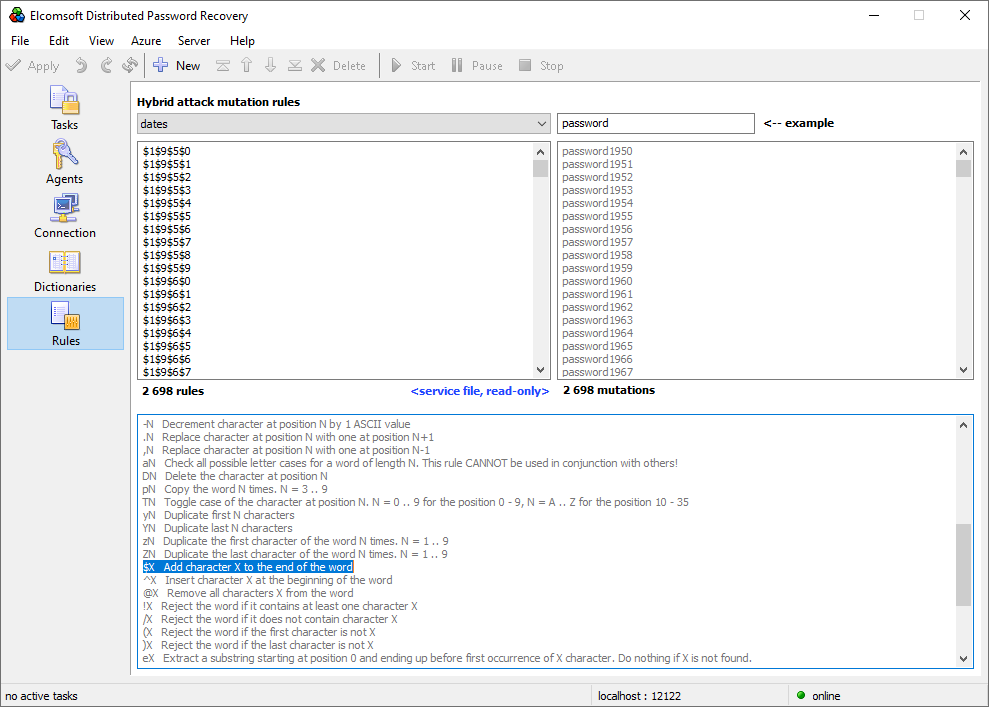
This had come to an end with EDPR’s brand new, fully visual Rules editor. The same familiar John the Ripper syntax can be now used easily, in WYSIWYG (“What You See Is What You Get”) manner. Just enter the test core word (e.g. “password”) and start adding the rules. You’ll see immediately not only how the generated potential passwords will look like, but the number of such passwords per dictionary entry – which is extremely important when estimating the time it takes for the attack to complete.
One of the simplest pre-defined rules checks for all possible cases of the dictionary entry:
Another rule adds a character to the end of the word. The following pre-defined attack adds a date (four digits representing the possible years) to the end of the entry.
There are countless possibilities for using hybrid attacks. The only limit is your imagination and the list of existing passwords.
Let us see what kind of real-world passwords the hybrid attack can break. Have a look at the following list of passwords extracted from the suspect’s computer:
We know some of user’s passwords:
Pl@net Nev@d@ L@ptop Glob@l G@ry c@roline
As you can see, the user makes their passwords by replacing the letter “a” with a similar-looking symbol “@”. It’s easier to remember, but harder to brute-force. To solve this task, you would add a simple substitution rule that looks as follows:
sa@ csa@
Done! All entries from a given dictionary files will have their a’s replaced with @’s.
Conclusion
Using the familiar John the Ripper syntax in a WYSIWYG environment combines the best of the two worlds. We are confident in that the feature will get used in a much wider scope than ever before, helping investigators solve more cases in less time.
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
如有侵权请联系:admin#unsafe.sh