2020-10-29 00:15:00 Author: www.synopsys.com(查看原文) 阅读量:287 收藏
Posted by on Wednesday, October 28th, 2020
Three WPA authentication bypass vulnerabilities were found in wireless routers using the Defensics fuzz testing tool.
WPA3 will become a mandate for all new wireless devices, which can only be a good thing considering the number of vulnerabilities found in WPA2 implementations. Learn about the basic concepts (and common weaknesses) of WPA authentication, how these vulnerabilities work, and how proactive fuzz testing can identify and address similar issues in WPA implementations.
Note: CVE-2019-18989, CVE-2019-18990, and CVE-2019-18991 were initially disclosed on September 28, 2020.
About Wi-Fi protected access
It’s a commonly accepted best practice to use some form of Wi-Fi protected access (WPA) authentication/encryption in 802.11 WLAN networks. The most ubiquitous version now is WPA2, which has been around since 2004. We have grown accustomed to the sense of protection; authentication keeps unauthorized users off the WLAN, and encryption keeps your payload private from snooping users of the same WLAN.
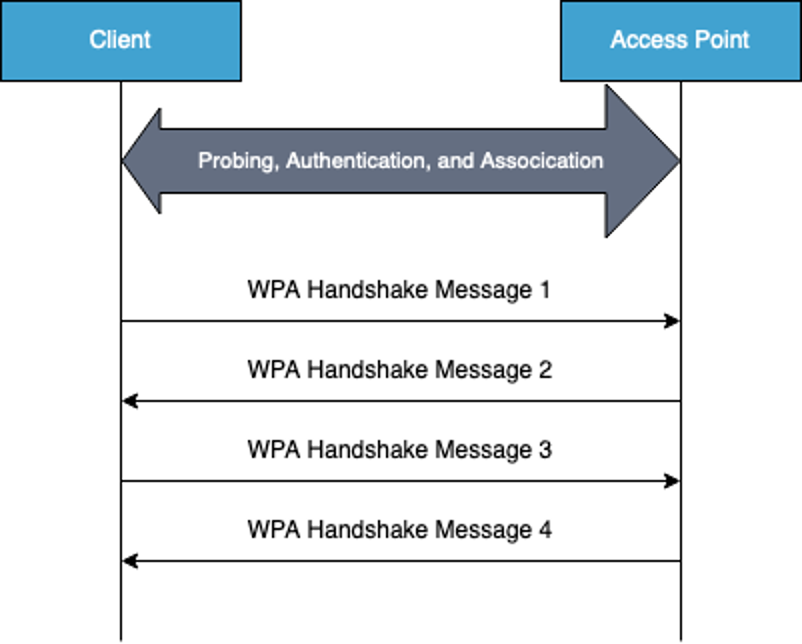
A preshared key, also known as an access point password, is used to calculate the pairwise master key with the access point name (SSID). Each client has the same pairwise master key on the same access point, and authentication and encryption in WPA2 are done with a handshake. After the client has successfully been associated with the access point, the access point sends the handshake message to the client, and the client sends its own handshake message back. These first two messages contain a nonce value from both sides. With these two nonce values, a pairwise master key, and MAC addresses, both the client and the access point can calculate a pairwise key. The pairwise key is used for actual encryption and decryption between client and access point. If an eavesdropper sees the full handshake and knows the preshared key, all data between client and access point is exposed.
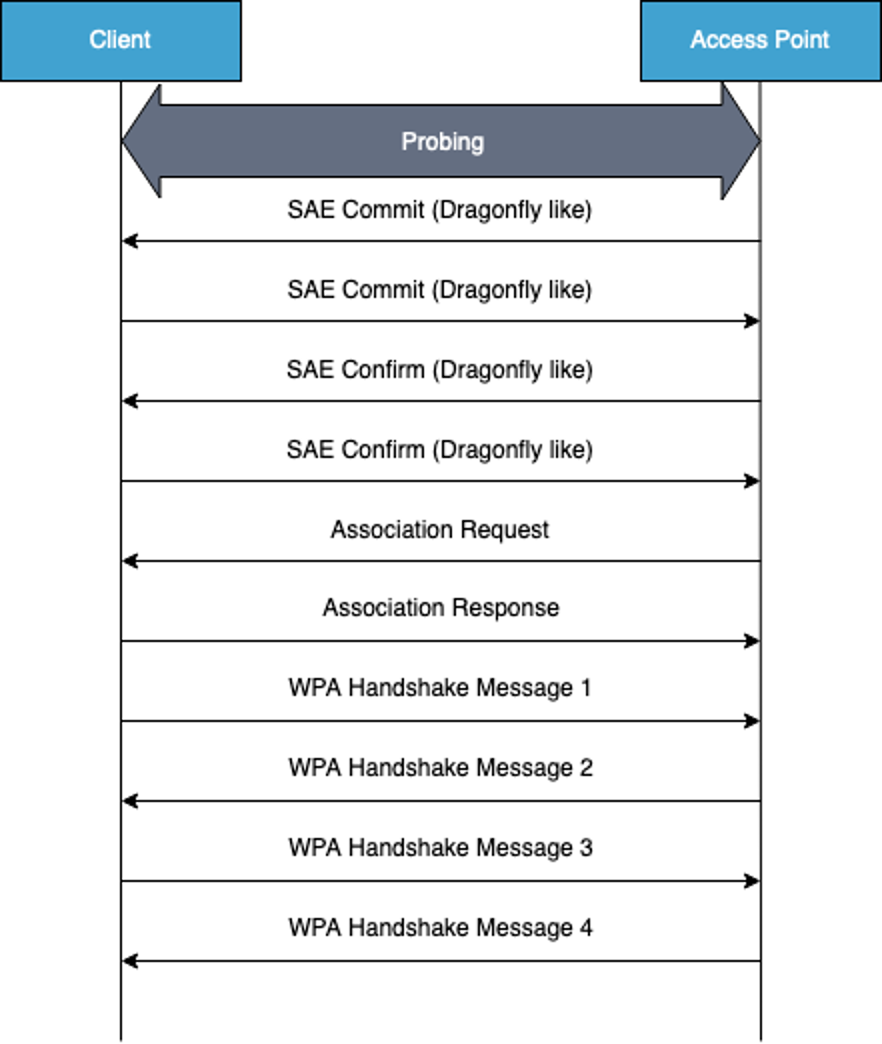
WPA3 tries to fix this by using a Dragonfly-like protocol instead of a preshared key to calculate the pairwise master key. The preshared key is used to pick coordinates (called a Password Element) from an elliptic curve; the Password Element is then manipulated for both the client and the access point. Both client and access point will generate their own points on the curve (called Commit Elements) based on original coordinate point. Only the parameters that were used to determine how the Commit Elements were manipulated are transferred between the client and the access point. Both Commit Elements are then used to calculate the pairwise master key in both the client and the access point. Since these parameters are random numbers, the pairwise master key is different every time, even for the same client using the same access point. After this, WPA3 does a handshake similar to what WPA2 does where the pairwise key is received. Since the pairwise master key is unique each time, so is the pairwise key. This is called forward secrecy.
As one would expect, only authenticated devices can send and receive packets in a WPA2/WPA3 network. Nonauthenticated devices would see only encrypted packets without any knowledge of their contents.
WPA authentication bypass vulnerability
During the development of the latest Synopsys Defensics® 802.11ac fuzzing test suites, we discovered a vulnerability in a variety of WPA2-enabled devices. This vulnerability allows unencrypted packets from a source with no WPA2 credentials to be sent to a WPA2-protected network, and then be routed to adjacent networks by the vulnerable WLAN router. By our understanding, this should not happen and will open the door for some possibly problematic exploit situations.
A malicious attacker can send unencrypted packets that will be routed to adjacent networks as regular packets. A response would even be sent back, but it would be encrypted. Since the attacker controls what’s being sent for the network, these encrypted response packets can reveal information about applications or network layouts. We have been able to open the UDP port to a network’s NAT and then access the network via the WAN port by using a secondary machine on the WAN port. This means that an attacker can open a UDP connection from the internet to a local network using UDP. The attacker needs only to be in range of the wireless network initially. This vulnerability allows the exploitation of other vulnerabilities that can be mitigated by using protected networks.
We have verified that the vulnerability exists in a wide range of access point devices originating from various vendors. The devices use a variety of chipsets from different manufacturers. As we have access to a limited number of routers/access point devices, we don’t know the exact number of vulnerable devices. We have tested around 20 different devices, 8 of which were found to be vulnerable to this issue. So far, we have not found any WPA3 supporting access points to have this vulnerability.
The following CVEs are related to this vulnerability:
As of this writing, there are no publicly available firmware updates for any of the routers we tested. Many router models proved to be vulnerable at this point are older, legacy models, so it’s unlikely that all/many will get patched firmware. In those cases, the best mitigation is to replace the devices.
Testing WPA implementations with Defensics
We are pleased to announce the release of Defensics WLAN FuzzBox. This newly redesigned set of wireless test suites provides better support of new protocols such as 802.11ac, WPA3 security extension, and 802.11ax (partial) support. These new offerings provide our valued customers with the opportunity to expand their wireless network test coverage and perform faster, parallel test execution of their WLAN products.
The CyRC Vulnerability Advisory on authentication bypass vulnerabilities found in multiple wireless router chipsets were discovered using Synopsys’ Defensics fuzz testing tool. Since the discovery, we have added new capabilities that enable customers to detect similar vulnerabilities more easily:
- Defensics FuzzBox 802.11 WPA AP or Client Test Suite for WPA 4-way handshake testing
- Defensics FuzzBox 802.11 WPA3 AP or Client Test Suite for WPA3 Dragonfly-like and WPA 4-way handshake testing
- Defensics FuzzBox 802.11 AP or Client Test Suite for WLAN connection testing
These test suites upgrade the testing capabilities of the previous generation of 802.11 test suites.
So far, we have not observed this issue in WPA3 devices, but the WPA3 protocol itself is not immune to this kind of vulnerability. The WPA3 test suite is focused on fuzz testing the WPA3 Dragonfly-like protocol and the WPA handshake, but it also checks that UDP packets are not routed without proper authentication.
Learn more about Defensics’ advanced, enterprise-grade fuzz testing solution
![]()
如有侵权请联系:admin#unsafe.sh