
2020-11-19 01:42:09 Author: medium.com(查看原文) 阅读量:296 收藏
This report is about the missing 2FA check on Instagram login when a user uses the ‘Secure account here’ option from ‘Email changed’ mail-notification which leads to a full 2FA bypass again and again.
A user can set 2FA to secure his/her Instagram account so that no one can successfully login to his/her account even if anyone has the user’s login credentials. If an attacker takes over the victim’s Gmail account connected to his 2FA protected Instagram account, he may be able to change the password (which can easily be recovered on the victim’s side by several ways) but he never can fully open/take-over the victim’s Instagram account. Technically, the attacker cannot create or revoke an active session without passing the 2FA security. But there’s a vulnerability that allows attackers to fully bypass the 2FA. 2FA check’s missing when a user uses the ‘Secure account here’ option from the ‘Email changed’ mail notification (that goes to the priorly connected email).
Reproduction Steps
==
1. User B logs-into User A’s Instagram account.
2. User B replaces User A’s email address ([email protected]) with his own email address ([email protected]) via the ‘Edit Profile’ option.
3. User A finds/gets alert of the unrecognized login of his account.
4. User A goes to login activity and revokes the unrecognized session.
5. User A then changes his Instagram account password.
6. User A also replaces the unrecognized email address ([email protected]) from his profile with his own email address ([email protected])
7. User A now sets 2FA security for his Instagram account.
8. Then; User B gets ‘Email changed on Instagram’ notification-email at his email ([email protected]).
9. User B clicks the ‘Secure your account here’ option there.
10. User B may be asked to verify if ([email protected]) belongs to him; which he verifies using User A’s email login credentials.
11. User B successfully bypasses 2FA there, thus creating an active session of User A’s Instagram account without a 2FA check.
…
You can see the POC video here.
Impact
===
This vulnerability lets an intruder regain access to the victim’s 2FA protected Instagram account without ever requiring a 2FA code.
Now, suppose; In a scenario, an attacker’s got the victim’s Instagram login credentials (password) which is the same for his email account too (Many people do have so). Or, the attacker’s got the login credentials for both the Instagram and email account of the victim. Now, the attacker logins into the victim’s Instagram account and replaces the victim’s email with his own email by editing the profile. Now, the victim gets an alert about an unrecognized login. As soon as he knows, he revokes the unrecognized logged session. He then changes his Instagram password. Moreover, he may replace the attacker’s email with his own email. Then after that, he secures his Instagram account with 2FA security. Now, this may look completely secured to the victim, there’s no normal way for the attacker to get into the victim’s account again. But, the vulnerability is in the mail which the attacker receives at his end as an ‘Email changed in Instagram’ notification, and thus; from the ‘secure your account here’ option at the bottom of the mail, the attacker can automatically log into the victim’s Instagram account without 2FA authorization (with the help of compromised victim’s email). Simply, he bypasses 2FA to get full access to the victim’s Instagram account again.
After I got my eyes on this vulnerability; I quickly reported it to Facebook with a short POC video.
…
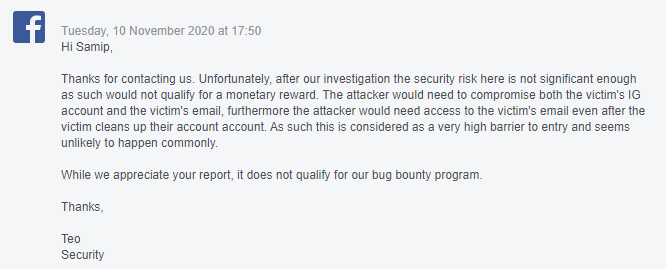
But this was their reply to close the report as Informative:
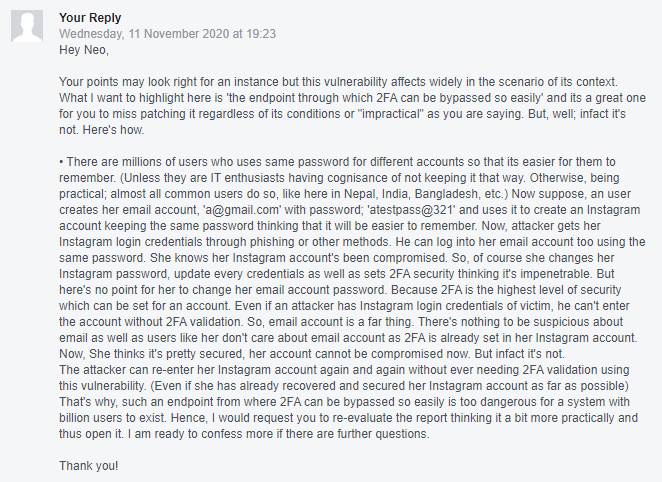
Well as expected, a bit dissatisfaction with the first reply, thus I requested with this reply to reopen it:
So, hence here’s their ultimate reply to this:
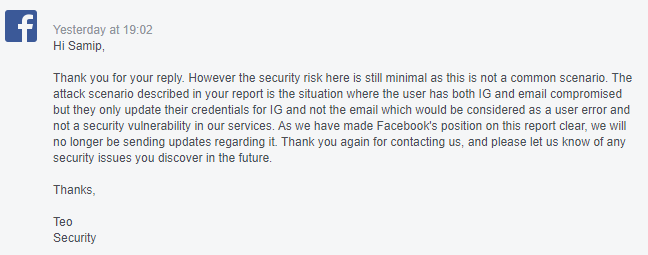
There’s nothing to do after this reply. Hence; “stay calm, make a writeup” :)
Thank you for reading this writeup. If you have any comments on this you can try. If you have any suggestions/queries, I’m available on Facebook/ Instagram.
如有侵权请联系:admin#unsafe.sh