2020-11-19 01:30:00 Author: www.synopsys.com(查看原文) 阅读量:381 收藏
Posted by on Wednesday, November 18th, 2020
The TARA method provides risk evaluation, assessment, treatment, and planning for identified risks. Learn how to apply this method to the ISO SAE 21434 standard.
In our earlier blog posts we covered the ISO SAE 21434 standard, including the organizational cyber security plan as well as the cyber security assurance levels in depth. We will now look at the impact calculation and detailed threat analysis and risk assessment (TARA) coverage within this new standard.
TARA covers risk evaluation and assessment, as well as the treatment and planning of identified risks. These methods are aligned with NIST SP-800-30 and ISO IEC 31010, which show the attack feasibility or likelihood and associated impacts.
Apply the TARA method
Much like many other risk assessment methods, the TARA method begins with asset identification. The analyst will need to determine the security properties of each asset, and determine damage scenarios along with their impacts. Assets are categorized by the standard confidentiality, integrity, and availability (C, I, A) ratings. Impact is measured from negligible to severe and separated into four categories: safety, financial, operational, and privacy (S, F, O, P). It’s important to consider that all these impacts must be calculated from the road user perspective, not the corporate perspective. Once the impacts of the damage scenarios have been compiled, it’s time to identify threats against them.
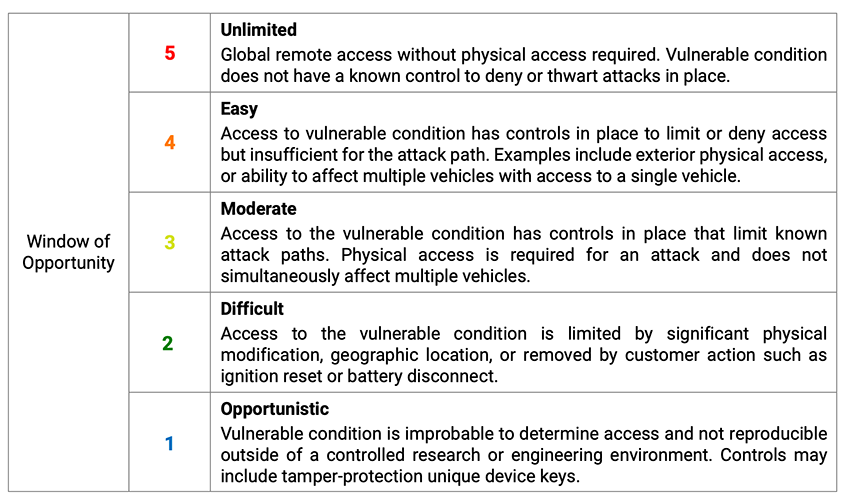
Threats or vulnerabilities are identified by common definitions such as “man-in-the-middle” or “buffer overflow” and rated in multiple categories that affect the road vehicle and ultimately the user. Time, expertise, knowledge, window of opportunity, and equipment are important threat categories to include. Establishing the proficiency and duration of an attack might include definitions around the use of bespoke tooling, insider knowledge, and opportunity windows of attack. In addition, equipment and window of opportunity may require definitions around specialized unlocking mechanisms, and proximity-based vs. long-range communications.
The above table provides an example of policy definitions using ratings for vulnerability or threat conditions defined previously. Within organizational policies and procedures, you will need to define a common lexicon for these threat categories, asset classifications and ratings, and impact categories and ratings. Ensuring that TARA language and judgement is consistent across all evaluations is essential for a cyber security assurance program.
Calculate and communicate the risk
Taking both the maximum composite rating of the assets and the geometric mean of the vulnerable conditions, we can compare these values against the defined impact severities to determine the overall risk. While these are simple calculations, the important consideration is chained vulnerability conditions, also known as attack path analysis. This will need to be identified during the impact analysis, and vulnerabilities and controls will be associated together in the TARA method output. Attack paths will be given a feasibility rating, and ultimately a risk determination will be made based on the calculations.
After making the calculation, you will have a list of impact scenarios with identified risk ratings. These risks will generate a composite score of the risk to the system, and provide a numerical representation for comparison of other systems and projects over time. A risk treatment decision will need to be made to avoid, reduce, transfer, or accept the risk.
The illustration above shows the mapping of three important risk measurements. The risk tolerance, or upper risk limit, is established by the organization prior to TARA method calculation. This is seen as an unacceptable risk level from the four impact categories listed above. The risk caution is the lower risk limit, and it defines the negligible risk from recognized risk levels. And the third risk measure is the organization’s baseline risk, which is adjusted for the average risk calculation or the sum of projects for the firm. This allows an organization to see how identified risks rate in comparison to previously calculated risks.
Ready to get started?
Speak with a Synopsys automotive expert today.
![]()
如有侵权请联系:admin#unsafe.sh