
2020-11-22 07:22:41 Author: medium.com(查看原文) 阅读量:286 收藏
Hello,
First of all, sorry for not posting for such a long period of time. I was really busy in this lockdown pushing my HackerOne Reputation & other stuff.
I am writing this blog to talk about my methodology and how without using any tool I found multiple vulnerabilities on one of my First Targets.

Anyways, let’s come to our topic, I won’t disclose the company name as it was a private program but will refer to it as shopping.com as it was a shopping website.
This was my first ever Target from which I received bounty, as the first bounty is always a special one. I continued hacking on the Target to report some more reports and get some more bounties
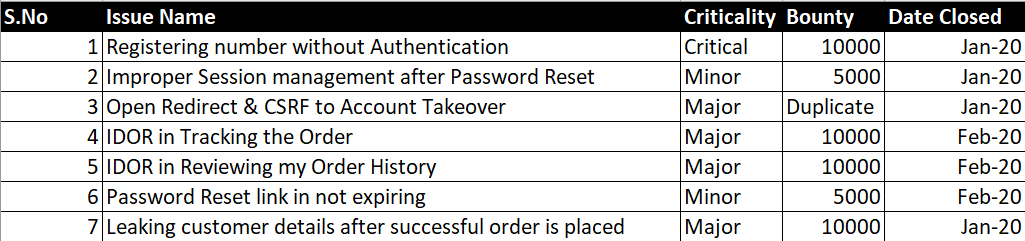
(Registering number without Authentication)
Here is the blog which I wrote earlier this year about this:
(Improper Session management after Password Reset)
In this case scenario, I created an account and Logged it in two browsers. I changed the password of the account in one browser and tried to make edits on the Second browser which went successfully, hence the Improper Session Management flaw, which is obviously a minor severity.
(Open Redirect and CSRF to Account Takeover)
Here the Case was a bit different, I Observed when I delete something from my Cart a POST request is sent in which there was a redirect parameter in the Request body, I quickly changed the Parameter value to my server and it redirected to my server and the Interesting thing was It came with the User Cookies.
I Converted it into a CSRF POC via Burp suite and made a request with a different account and I was successful to redirect the victim to the attacker's website and stealing their cookies
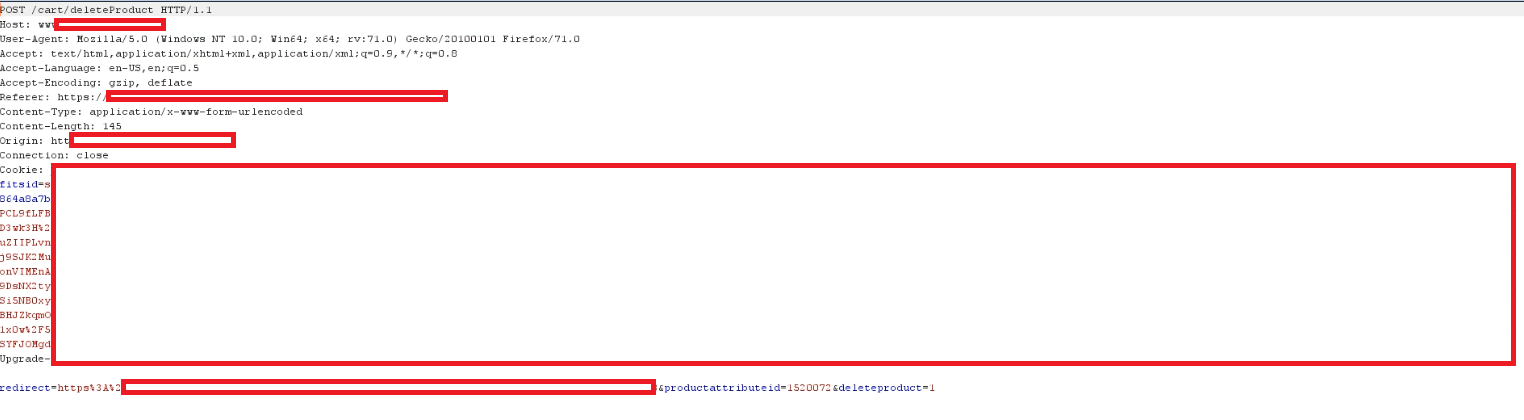
(IDOR in Tracking Order)
So on this shopping.com website, there was a “Track my Order” Option which is after a successful order is placed, a person can track the order with the order id. So with this feature, an attacker can take out the details of any victim if he knows the phone number of the victim and he doesn’t need to know the order number because with the help of the Burp Suite Intruder (for a better understanding referrer to Screenshot below) he can brute force and find a correct order number and get the details of his order which leaks the Address and other personal information of the Victim

Here I bruteforced the id_order parameter with my other account’s mobile number and got all the orders placed by the second account.
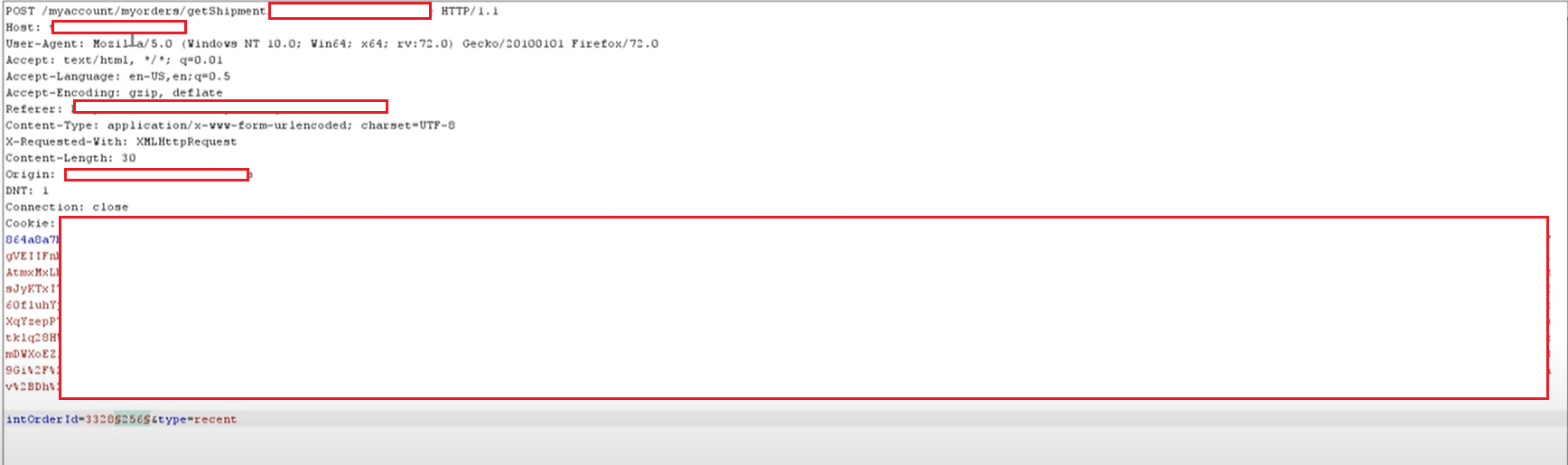
(IDOR in Reviewing my Order History)
On a Special Note: These features were only available to me After made a Purchase on the shopping.com
Here the Case was pretty simple, I went into my “My Orders” page and when I click on my order it refreshes the page and shows the ordered product, I intercepted the Request and again clicked on the ordered product & to my surprise, there was again an “intOrderId” parameter in the Request body, I quickly sent it into Burp intruder and Guess what I have multiple order details leaking PII of their Customer
(Password reset link not expiring)
Well, it was also a minor bug and it was quite simple too. For reference, I’m posting a Hackerone report which will give you an Idea (Also it may vary from program to program)
(Leaking customer details after a successful order is placed)
Again this Issue was also found after making a successful order, Here when I placed an order the URL was something like this “https://www.shopping.com/orderconfirm?secretkey=<some-key>&orderid=<order-id>”
I changed the order in decreasing order and PII starts disclosing which included name, address, phone number, and Mode of payment done.
Takeaways –
I would say my takeaway from this experience was to stay at a target and understand it, make yourself feel comfortable, and don’t Rush. If you are eligible to make a purchase DO it!! It will definitely bring something with it.
That’s all for this blog. Hope you liked it.
Connect with me on LinkedIn, Twitter
If you enjoyed this blog, please click the 👏 button and share it to help others find it.
如有侵权请联系:admin#unsafe.sh