2020-11-27 16:03:12 Author: medium.com(查看原文) 阅读量:271 收藏
Hi guys, this is my first english write-up, so I’m sorry for my bad english grammar.
Obviously, I discovered a bug but I was not sure exactly what caused it. So I said, I have to investigate this case!
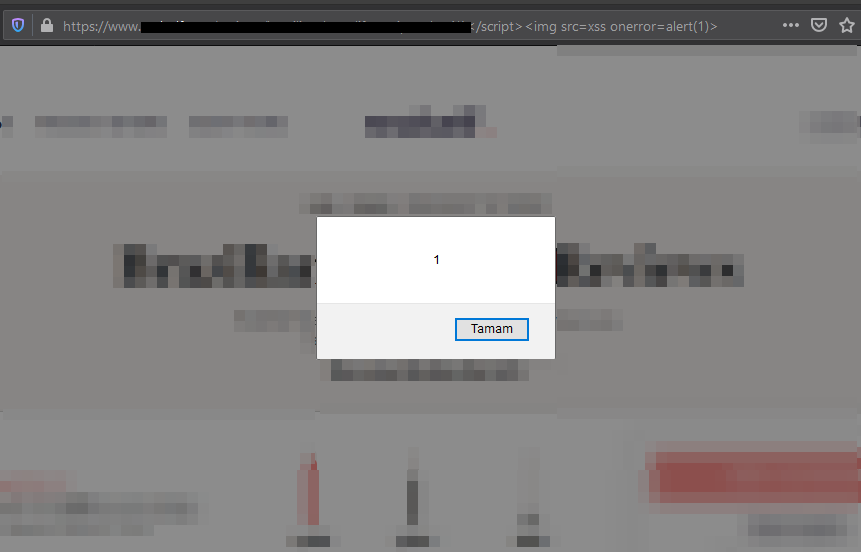
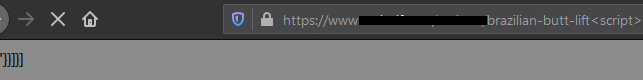
I found this worth exploring because this site did not seem to be receiving an input from me. However, the <script> tag I added to the end of the URL was revealing some characters on the page. (like: "}}] )
But, how?
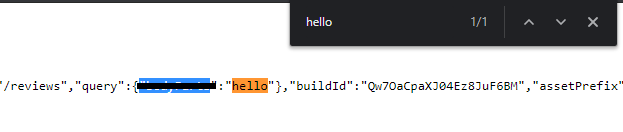
When I examined the source code, every value I added to the end of the URL was assigned to a JSON-generated variable. Then, I saw that the JSON data was put between<script> tag.
Just like that:
At this point, all we have to do is close it using the </script> tag, then enter XSS payload.

Finally;
target.com/affected/url</script><img src=xss onerror=alert(1)>
And it’s fixed!
Thanks!!!
如有侵权请联系:admin#unsafe.sh