
2020-11-29 22:08:10 Author: medium.com(查看原文) 阅读量:288 收藏
Hey Fellas! I hope you all are doing good and safe. Thank you so much for showing your interest in my previous blogs and making it first viral blog post of the InfoSec Write-Ups.
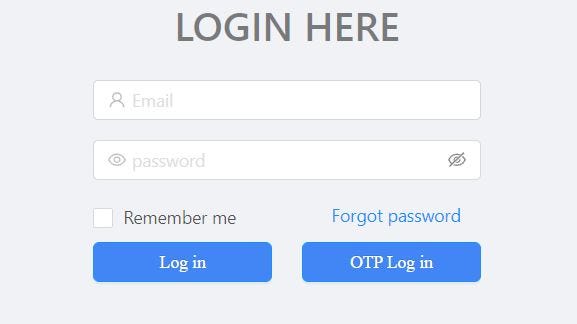
I was testing a private program recently, let’s take target.com as an example. On the Log-In page, there is a functionality “OTP Log In”. In which OTP is sent to the registered mobile number.
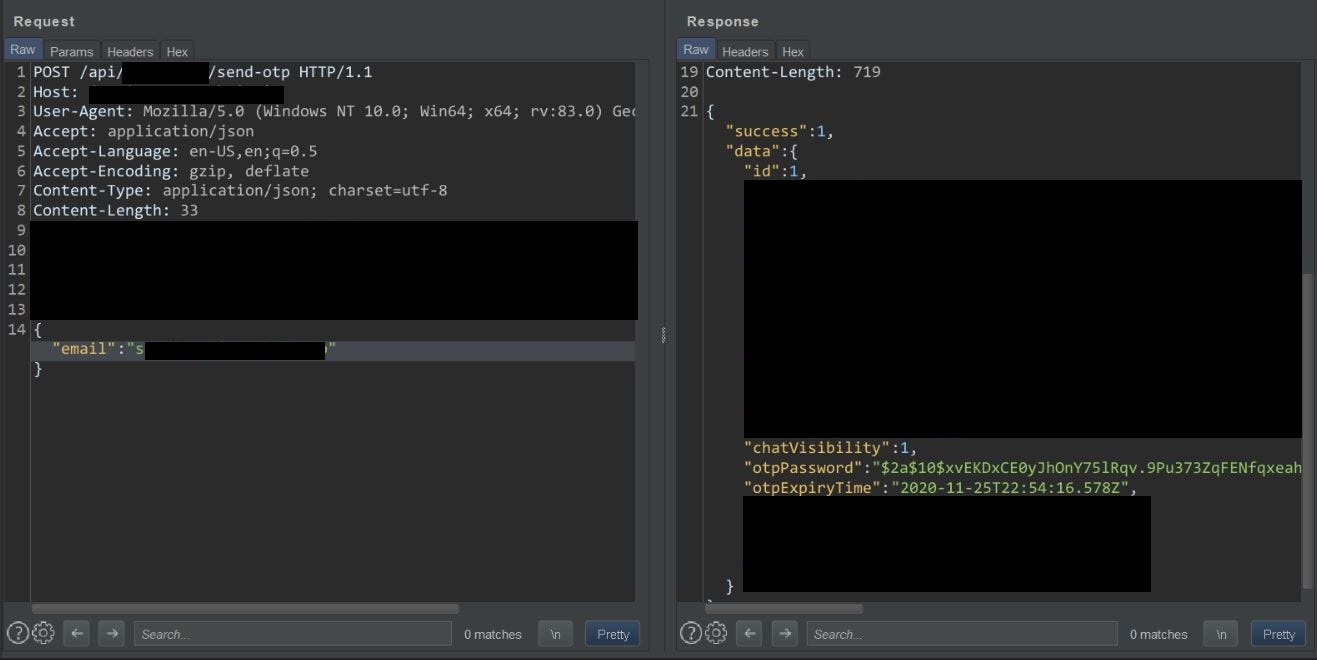
To check if the OTP is leaking in response body or not, I intercepted the “OTP Log In” request in burp. And, yes, I was right. The OTP had leaked in the response body with the name “otpPassword” but the OTP was in an encrypted format i.e Bcrypt.
With the help of this nice tool (https://github.com/BREAKTEAM/Debcrypt), I easily decrypt the OTP value and successfully TakeOvered the victim’s account.
Steps:
- “otpPassword”:”$2a$10$hs/tvUkd4GveEdx/hACRDehWza38Z1ncMAEFeOtG77/l.Ja0ktuQa”
2. Copy the Bcrypt Encrypted Value to Decrypt it.
3. Provided the value to this tool.
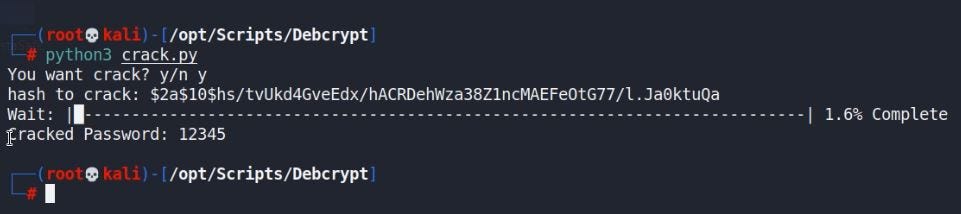
4. OTP for login is “12345”.
5. ATO is Successful.
I hope you enjoyed this writeup!, Follow me on Twitter for some cool tricks.
如有侵权请联系:admin#unsafe.sh