2020-12-08 23:30:02 Author: www.synopsys.com(查看原文) 阅读量:299 收藏
Posted by on Tuesday, December 8th, 2020
Synopsys surveyed 1,500 IT professionals working in cyber security to analyze the DevSecOps practices used to address open source vulnerability management.
This week Synopsys released the “DevSecOps Practices and Open Source Management in 2020” report, findings from a survey of 1,500 IT professionals working in cyber security, software development, software engineering, and web development. The report explores the strategies that organizations around the world are using to address open source vulnerability management, as well as the problem of outdated or abandoned open source components in commercial code. Survey participants came from the United States, the United Kingdom, Finland, Germany, China, Singapore, and Japan, with at least 50 respondents from each country. Here are six key findings from the report.
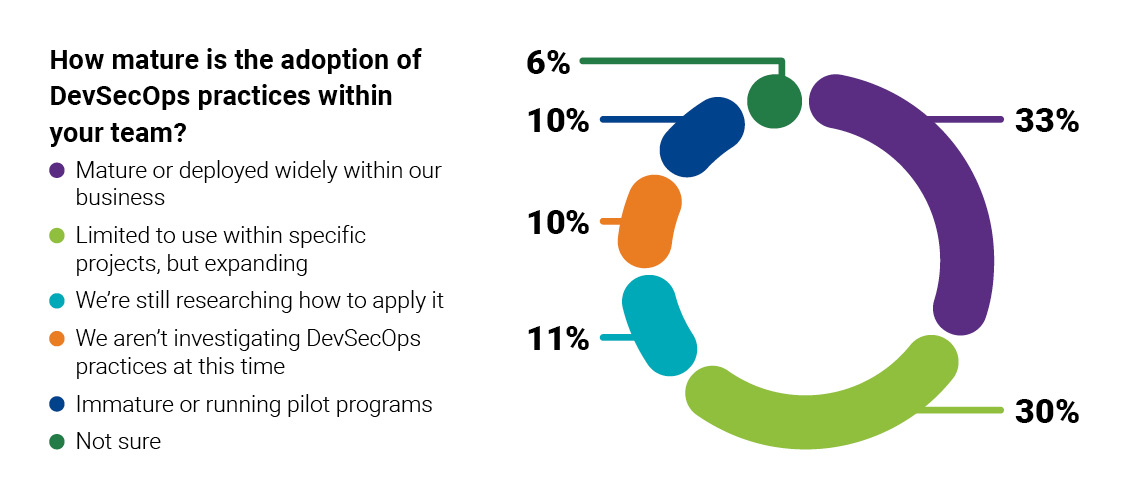
1. DevSecOps is growing rapidly worldwide
DevSecOps is the practice of integrating security into every stage of the DevOps pipeline. The “DevSecOps Practices and Open Source Management in 2020” report indicates that the DevSecOps methodology is an important, rapidly growing trend worldwide. A combined 63% of survey respondents reported that they are incorporating some DevSecOps activities into their software development pipelines.
2. There is no one universally adopted application security tool
The responses to the survey indicate that there is no shortage of application security testing (AST) tools and techniques used among the respondents. But for many teams, each tool represents a pain point within their development workflow that can slow development efforts. To ease some of that pain, vendors have focused on integrating their tools within CI/CD pipelines. But while integration can help with tool deployment, it doesn’t necessarily address perception of development teams that too many AST tools slow down or generate additional work for them.
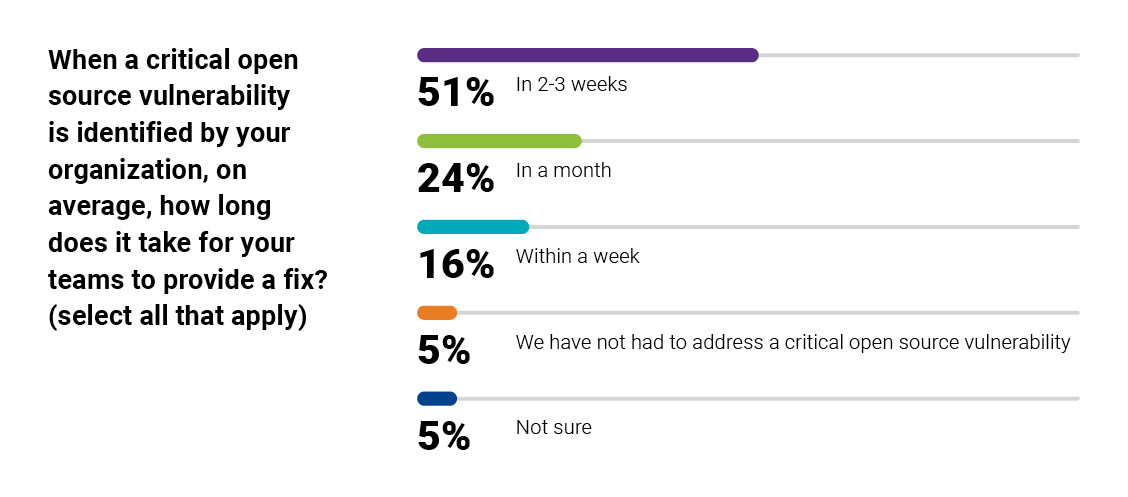
3. Unpatched open source vulnerabilities are a major source of developer pain
The “DevSecOps Practices and Open Source Management in 2020” report reflects that security and a component’s vulnerability to exploit were top-of-mind to respondents; that was cited as the number one selection criterion when vetting a new open source component. It’s also clear from the survey findings that unpatched vulnerabilities are a major source of developer pain. Over half—51%—of respondents said it takes two to three weeks for them to apply an open source patch. And over 50% of U.S. respondents (40% worldwide) also reported that they had delivery schedules disrupted to address open source vulnerabilities.
As noted in those findings, many organizations—especially in the United States—should accelerate their time-to-patch schedules. A production-grade software composition analysis (SCA) solution is key to reducing patching timelines from weeks to days by providing continuous monitoring for new vulnerabilities and giving guidance on mitigation.
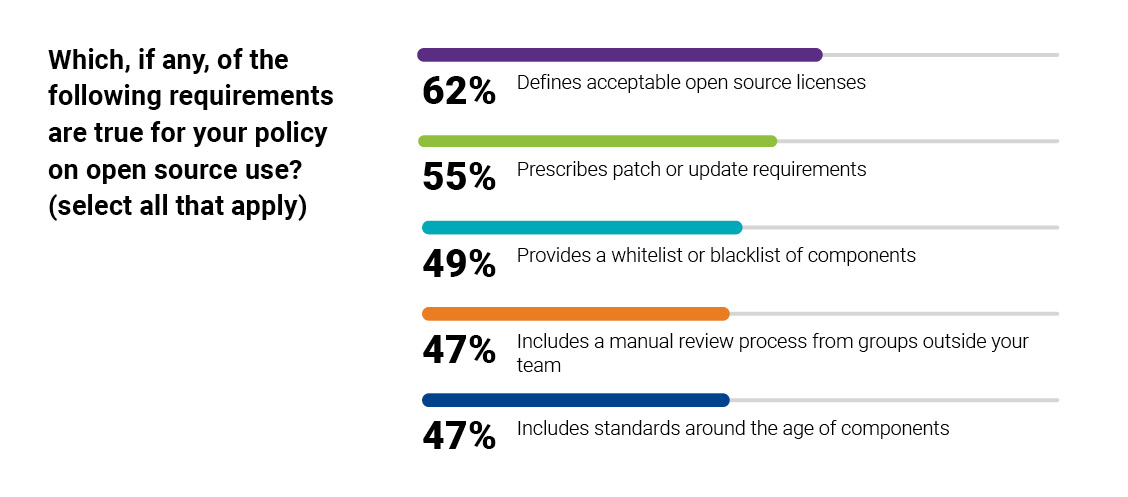
4. Organizations need to increase their investments in software composition analysis
Only 38% of respondents said their organizations are using an SCA tool to address open source security issues early in the software development life cycle. Automated SCA solutions allow development teams to identify and track open source in their code, mitigate security and license compliance risks, and automatically enforce open source policies using existing DevOps tools and processes. Organizations not using SCA tools are probably still employing manual processes to identify and manage open source—processes that can slow down developers and force them to play catch-up on security.
5. Media coverage plays a big role in how organizations respond to open source risk
The media comes under regular—sometimes deserved— criticism from the open source community for exaggerating security incidents and the risk of open source use. However, most responsible reporting notes that the risk comes from the unmanaged use of open source, with reported incidents usually involving unpatched or outdated components, or the lack of an up-to-date software inventory that includes all open source components as well as the versions used, the download locations for each project and all dependencies, the libraries the code calls to, and the libraries those dependencies link to.
The survey results also demonstrate that media coverage of open source issues definitely affects how organizations manage their open source use. Forty-six percent of respondents noted that a story in the media had prompted their organization to apply more stringent controls on open source usage.
6. Many organizations are defining standards around the age of the open source components they use
A growing issue in the open source community is project sustainability. A 2020 Synopsys study showed that 91% of codebases audited in 2019 contained open source components that either were more than four years out of date or had no development activity in the past two years.
Security risks increase when obsolete code is deployed, including the threat of an open source component being hijacked. In 2018, an attacker took over a piece of open source code that was not being actively maintained and rewrote it to try to steal cryptocurrency. The malicious code was downloaded over 8.5 million times before being discovered.
How does your organization compare to your peers?
![]()
如有侵权请联系:admin#unsafe.sh