
2020-12-10 03:35:02 Author: medium.com(查看原文) 阅读量:205 收藏

Hello my hacker buddies, I hope you all are doing great. Keep finding bugs and even if you are not finding them, keep putting effort in it:) In recent days, I have focused less on bounties since I was doing office stuff and many other things. Anyways, I fell in love with it again last week or so, and results have been quite nice. We will talk here about a bug which I found recently with GitHub Dorks and in case if you are new to this, follow this video by Bugcrowd university to understand how GitHub dorks work. Basically we put a combination of dorks to find desired results i.e sensitive data.
Let’s come to the bug. So recently I started a program let’s call it hack.com and the first thing I do in big scope program is dorking. Let me tell you clearly, it does take time. Dorking takes time! If you are expecting a P1/P2 in an hour or so, probability is you will end up scratching your head almost every time. I was looking with some common dorks like “password=”, “token=” etc. I found some of them and since those were not related to the organization, I didn’t move ahead. Admit it or not, we all have done this mistake. We have submitted ANYTHING FOUND WITH PASSWORD OR SECRET to programs xD. Anyways, I kept checking the repos and after 2 breaks and almost 4–5 hours, I ended up with 3 critical repositories. Here is a glimpse of one of them:-
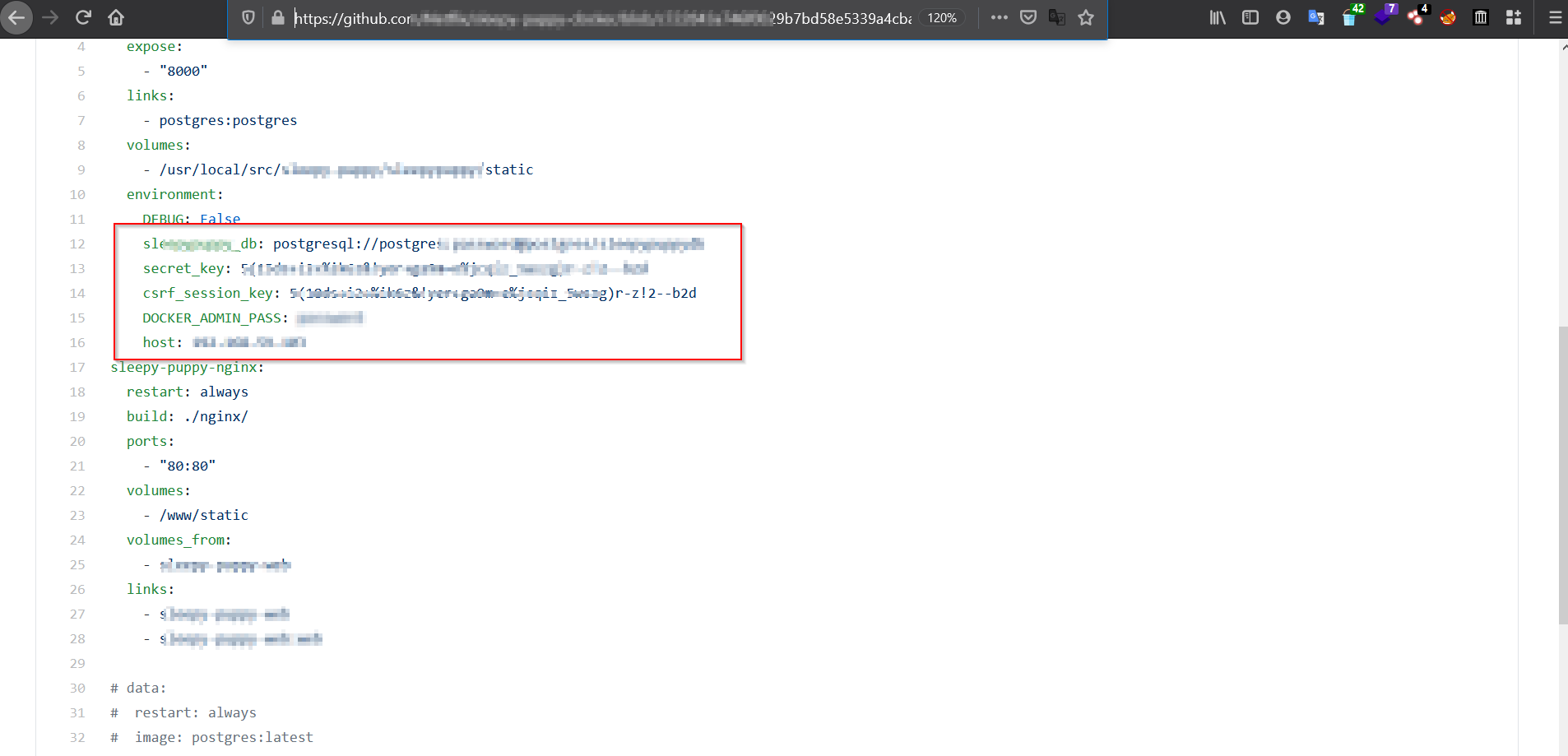
These were the dorks which led me to success. Even though these are classic ones, it makes sense to check these out in your search:-
Secret_key=
User_secret=
admin_passwd=
Once you go for GitHub dorking, keep in mind you can’t report every repository which contains a lot of data but doesn’t belong to the organization. Yes, if you found a repo with admin credentials, report as soon as you see it. The best way is to use “org:” in your dork and it will show you only those repositories which are contained by an organization. For example. org:Tesla will show you all the repository associated to Tesla and then you start your hack with a dork list:)
Well, this was all for this article and I hope it helps you to keep your hopes high in GitHub dorking. See, you get results with time. Yeah if you are lucky enough, you might find one within 5 mins. But make sure your data affects the organization. I wish you good luck ahead!
If you liked this article, give me a clap down below. Got doubts? Follow me on twitter with this username: @ManasH4rsh. Shoot me a DM with your query and I will be answering you for sure.
Happy hacking! Take care:)
Adios❤
Twitter:- https://twitter.com/ManasH4rsh
Linkedin:- https://www.linkedin.com/in/manasharsh/
如有侵权请联系:admin#unsafe.sh