
2020-12-31 21:35:54 Author: medium.com(查看原文) 阅读量:270 收藏

Hi my fellow hackers, my buddies! Welcome to my new blog! We are here, ending the year which we badly wanted. Yes!! We survived 2k20!!xD I hope you all are doing great and putting your efforts into whatever you are doing. I thought to end this year by giving back something to the community and here we go! With this note, let's move forward.
So, as the title says, this blog will be based on my Shodan hacks and in case if you are new to it, “Shodan is a search engine that lets the user find specific types of computers connected to the internet using a variety of filter.”, as per the Google. But as for me, it holds a much bigger place in your bounties when it comes to recon. You can read more about it on their official website, here.
The question is, why and how do we use it? Well, tbh, I use it for CVEs and open ports but you can use it for a ton of things i.e server enumeration, filtering the targets, etc. Not putting many words on WHY, since it is a personal choice. You can just Google it and find some very cool stuff out there. So I will be talking about HOW and that is my way of work in everything. Once you work on how things work, you automatically know the answer to WHY :)
Well, suppose you have to find a famous CVE on your target which is obviously a big org(Sadly you can't find much on a small target :|), let's assume Google. So, we have some Shodan dorks to find them. I found this dork very useful:-“set-cookie: webvpn;” and I reported a lot of P1s on bugcrowd (except Dell). However, someone was already hunting on that target and it came as a dupe in many cases. But this is not the point here whether it is valid or duplicate, what matters is if you find something with it. If you do, GZ, you won! Here is an example of how you put this dork in Shodan: -
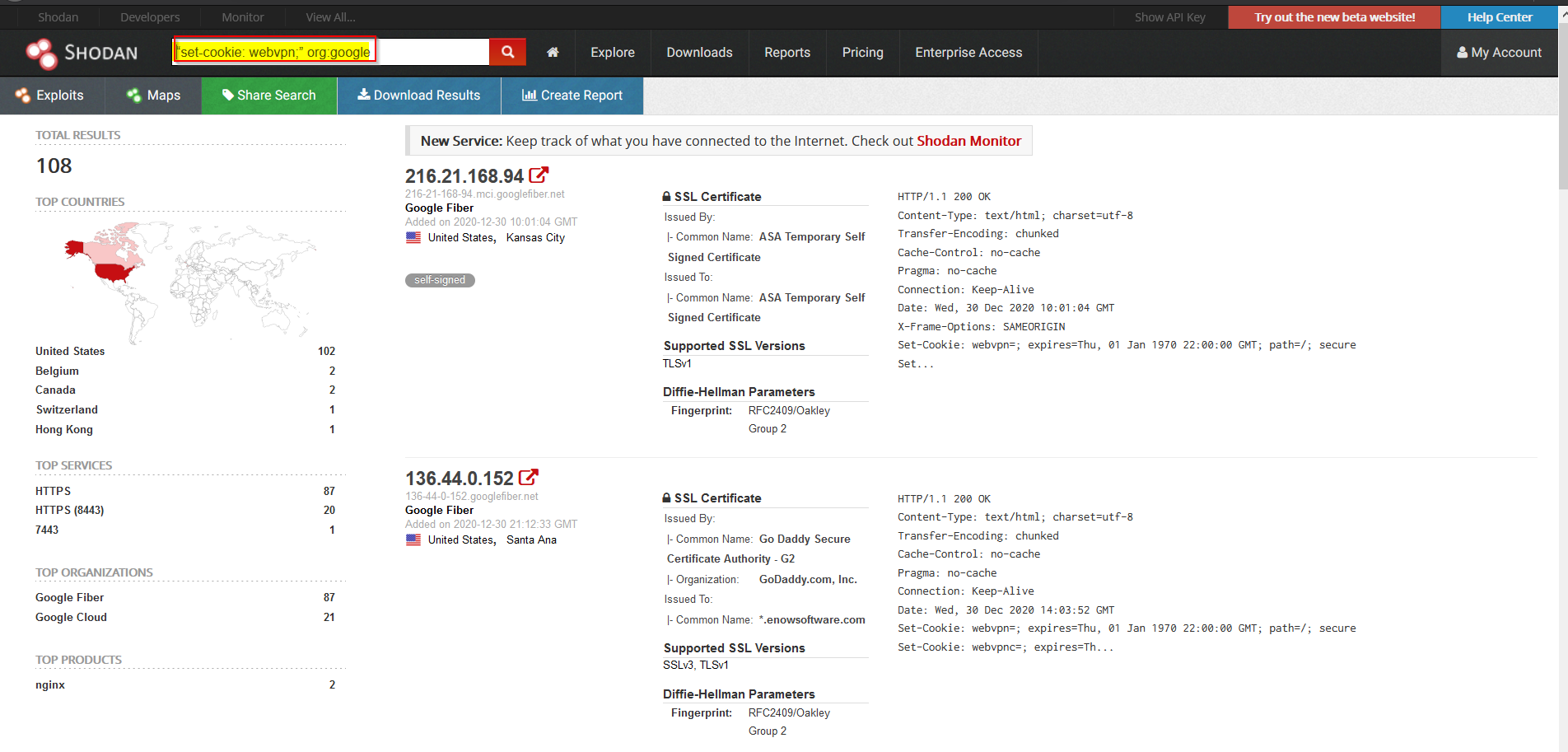
This doesn’t mean if you can report everything which you found here. There are two things to check: 1. If the target really belongs to the Organization or it is just a user who is using the IP address in the name of the Org. 2. If you can exploit it. Well, you will find the exploits related to it on Twitter once you search the keywords and I leave this as homework for you.
Another example of searching for something interesting would be, let’s assume we are searching for something related to Kibana. Kibana is an open-source data visualization dashboard for Elasticsearch. It provides visualization capabilities on top of the content indexed on an Elasticsearch cluster. Users can create bar, line, and scatter plots, or pie charts and maps on top of large volumes of data. So sometimes you will find their log instances open with this dork: title:”kibana” port:”443". Again, check if the target related to the organization and then only move forward. Here is a Screenshot for the same:)
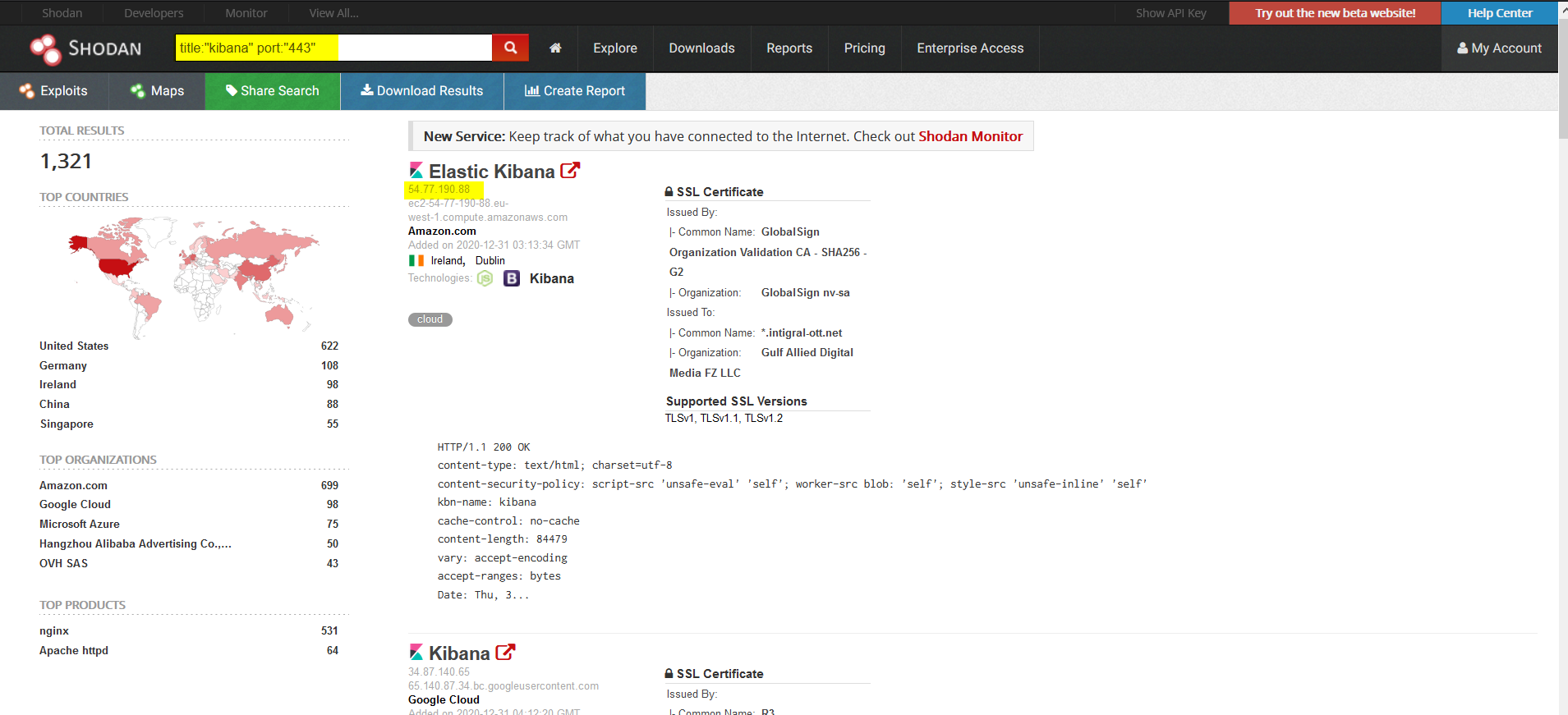
Also, make sure you have a Shodan paid membership and that really helps in your bounty stuff otherwise you will not be able to do a lot on it. However, you can always learn more about it on their website. Here are some more interesting dorks:-
“230 login successful” port:”21"
vsftpd 2.3.4 port:21
230 ‘anonymous@’ login ok
These were some dorks just to let you know how you can use it in web application hunts. You can always scrap a lot from Google. There are a ton of dorks and you just need to put them in a manner where you get results. Again, things like Dorking take a lot of time and if you are going to get something, you might need a lot of time to put in. Whether it is Google Dorking, GitHub, or Shodan, you have to have that patience. I can promise you all findings with this will be P1s or P2s and we love that right?
With this, I would like to wrap up this year here. I hope you got something from it and if you did, give me a clap down below. Also, you can follow me with this username on twitter:- @manasH4rsh.
I wish you all a Happy New Year 2k21! Grab some awesome bounties this year and I see you in the hall of fame!
Happy hunting, take care!
Adios ❤
如有侵权请联系:admin#unsafe.sh